This post is also available in: 日本語 (Japanese)
Executive Summary
In early August, GTSC discovered a new Microsoft Exchange zero-day remote code execution (RCE) that was very similar to ProxyShell (CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207).
The exploit was discovered in the wild in what appeared to be a SOC investigation into suspicious activity of one of GTSC’s customers. Once they determined the scope of the vulnerabilities, GTSC reported the vulnerability to the Zero-day Initiative (ZDI) to enable further coordination with Microsoft. The vulnerabilities were assigned CVE-2022-41040 and CVE-2022-41082 and rated with severities of critical and important respectively. The first one, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, while the second one, identified as CVE-2022-41082, allows remote code execution (RCE) when Exchange PowerShell is accessible to the attacker.
The exploit does require authentication; however, the authentication required is that of a standard user and, based on how easy it is to collect user credentials these days, this is not a high bar to overcome. Microsoft has yet to release a patch for these vulnerabilities. In the meantime, they provided mitigations in a blog responding to GTSC’s disclosure of these vulnerabilities.
Palo Alto Networks customers receive protections from and mitigations for ProxyNotShell in the following ways:
- Next-Generation Firewalls or Prisma Access with a Threat Prevention security subscription can block sessions related to CVE-2022-41040.
- A Cortex XSOAR response pack and playbook can automate the mitigation process.
- Cortex Xpanse can help identify and detect Microsoft Exchange servers that may be a part of your attack surface.
- Cortex XDR will report related exploitation attempts.
- XQL queries provided below can be used with Cortex XDR to help track attempts to exploit these CVEs.
- Malicious URLs and IPs have been added to Advanced URL Filtering.
- The Unit 42 Incident Response team can provide personalized assistance.
For more details, please see the conclusion.
| Vulnerabilities Discussed | CVE-2022-41040, CVE-2022-41082 |
Details of the Vulnerabilities
GTSC’s SOC discovered the following URL requests in a customer’s Microsoft Internet Information Services (IIS) logs:

The URL requests appear to be identical to the ProxyShell requests seen last year. Compare the above request with the following excerpt from Mandiant’s blog reporting on the discovery of ProxyShell last year, and you’d think this must be an unpatched server exploited by ProxyShell.
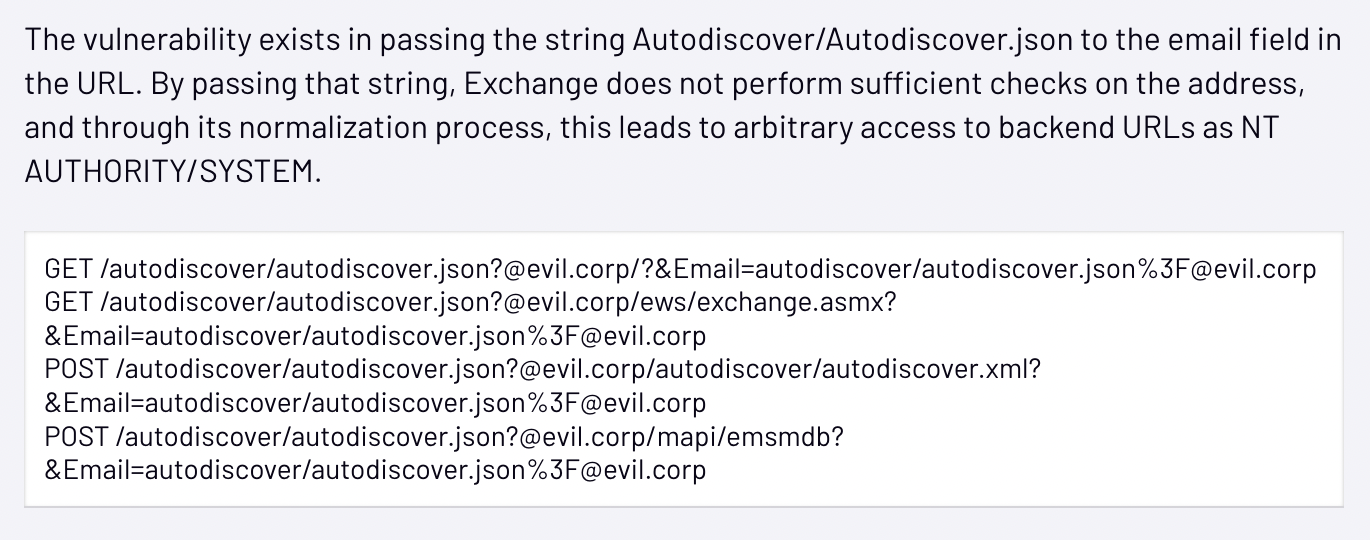
GTSC reviewed the Exchange server version and confirmed the Exchange servers were up to date and the vulnerabilities were indeed new zero days. GTSC also confirmed the attackers were able to get PowerShell execution during the attack. This also resembles ProxyShell. Once attackers gained access to the server, they installed webshells to obtain persistent access to the network. GTSC reported the vulnerability to the Zero-day Initiative (ZDI) to enable further coordination with Microsoft. The vulnerabilities were assigned CVE-2022-41040 and CVE-2022-41082 and rated with severities of critical and important respectively. The first one, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, while the second one, identified as CVE-2022-41082, allows remote code execution (RCE) when Exchange PowerShell is accessible to the attacker.
Please refer to GTSC’s excellent blog for details on the webshells, malware analysis, indicators of compromise (IoCs) and commands discovered during their investigation. Microsoft has stated that the vulnerabilities affect Microsoft Exchange Server 2013, Exchange Server 2016 and Exchange Server 2019. They also state that “Exchange Online has detections and mitigations to protect customers. As always, Microsoft is monitoring these detections for malicious activity and we’ll respond accordingly if necessary to protect customers.”
Current Scope of the Attack
It does appear there are multiple victims of this attack. However, from what has been publicly reported, the attacks still seem to remain isolated. GTSC stated in their blog, “GTSC's direct incident response process recorded more than one organization being the victims of an attack campaign exploiting this 0-day vulnerability.”
Microsoft, in a blog response to GTSC’s, stated “MSTIC observed activity related to a single activity group in August 2022 that achieved initial access and compromised Exchange servers by chaining CVE-2022-41040 and CVE-2022-41082 in a small number of targeted attacks.”
Both GTSC and Microsoft’s observed attacks used the China Chopper webshell and Microsoft’s MSTIC attributes the attacks, with medium confidence, to one attack group. Although the attacks still appear to be isolated, based on the history of ProxyShell and the difficulty of patching Exchange servers, we believe this vulnerability will garner widespread attention from threat groups. Therefore, we expect working exploits and proofs of concept (PoCs) will soon be available to aid in the exploitation of these vulnerabilities. That being said, Unit 42 has not yet seen any evidence of attempted exploitation within our customer telemetry.
Interim Guidance
Microsoft has yet to release a patch for these vulnerabilities. In the meantime, they provided mitigations that rely on the usage of a URL Rewrite rule to identify and block exploitation attempts as well as disabling remote PowerShell access for non-admins.
GTSC provided the same guidance in their blog as well. If you feel you may have been targeted and keep IIS logs, GTSC recommends running the following PowerShell command to search for evidence of attempted exploitation of your Exchange servers:
|
1 |
Get-ChildItem -Recurse -Path <Path_IIS_Logs> -Filter "*.log" | Select-String -Pattern 'powershell.*autodiscover\.json.*\@.*200'. |
Cortex XDR customers can search for signs of exploitation by employing the queries included in the following section of this brief. The queries include evidence of certutil connections to public IPs, evidence of DLL and EXE writes to C:\Users\Public\, evidence of China Chopper webshell activity, and the addition of suspicious files to Exchange directories.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit these CVEs across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
// Description: Detect certutil netcons to public IP addresses. May be observed // post-exploit in latest Exchange 0-day attacks for connection checks config case_sensitive = false | dataset = xdr_data | filter event_type = STORY and actor_process_image_name = "certutil.exe" and actor_process_image_command_line contains ":8080" | comp count() by agent_hostname, actor_process_image_name, action_external_hostname, action_remote_ip, action_remote_port, actor_process_command_line // Filter out connections to private IP addresses |alter rfc1918_172 = incidr(action_remote_ip, "172.16.0.0/12") |alter rfc1918_10 = incidr(action_remote_ip, "10.0.0.0/8") |alter rfc1918_192 = incidr(action_remote_ip, "192.168.0.0/16") |filter rfc1918_172 = false and rfc1918_10 = false and rfc1918_192 = false | fields - rfc1918_10, rfc1918_172, rfc1918_192 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
// Description: Detect DLL and EXE writes to Public folder (C:\Users\Public\) on possible // Exchange hosts. May be used post-exploit as part of latest Exchange 0-day attacks config case_sensitive = false | dataset = xdr_data | filter event_type = FILE and (event_sub_type = ENUM.FILE_WRITE or event_sub_type = ENUM.FILE_CREATE_NEW) and action_file_extension in ("exe", "dll") and action_file_path contains "C:\Users\Public" | fields event_type, event_sub_type, agent_hostname, actor_effective_username, action_file_path, action_file_extension, actor_process_image_name, causality_actor_process_image_name // Show only results on possible Exchange hosts (w3wp.exe process is present) | join conflict_strategy = right type=inner ( dataset = xdr_data | filter (event_type = PROCESS and actor_process_image_name = "w3wp.exe") | comp count(event_timestamp) as w3wp_event_count by actor_process_image_name, agent_hostname | fields agent_hostname ) as w3wp_list w3wp_list.agent_hostname = agent_hostname |
|
1 2 3 4 5 6 |
// Detection of China Chopper webshell activity config case_sensitive = false | dataset = xdr_data | filter event_type = ENUM.PROCESS and actor_process_image_name = "w3wp.exe" and (action_process_image_command_line contains "&ipconfig&echo" or action_process_image_command_line contains "&quesr&echo" or action_process_image_command_line contains "&whoami&echo" or action_process_image_command_line contains "&c:&echo" or action_process_image_command_line contains "&cd&echo" or action_process_image_command_line contains "&echo [E]" or action_process_image_command_line contains "&echo [S]") | fields action_process_image_command_line , actor_process_image_path , actor_effective_username , agent_hostname |
|
1 2 3 4 5 6 7 |
// Detection Suspicious files in Exchange directories config case_sensitive = false timeframe = 30d | dataset = xdr_data | filter event_type = ENUM.FILE and actor_process_image_name = "w3wp.exe" and action_file_path contains "FrontEnd\HttpProxy" and actor_process_command_line contains "MSExchange" | fields actor_effective_username , agent_hostname , actor_process_command_line, action_file_path , action_file_sha256 |
Conclusion
Based on the amount of publicly available information, the ease of use and the extreme effectiveness of this exploit, Palo Alto Networks highly recommends following Microsoft’s guidance to protect your organization until a patch is issued to fix the problem. Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information, release of proof-of-concept code and evidence of more widespread exploitation.
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
Next-Generation Firewalls (PA-Series, VM-Series and CN-Series) or Prisma Access with an Advanced Threat Prevention security subscription can automatically block sessions related to CVE-2022-41040 using Threat ID 91368 (Application and Threat content update 8624).
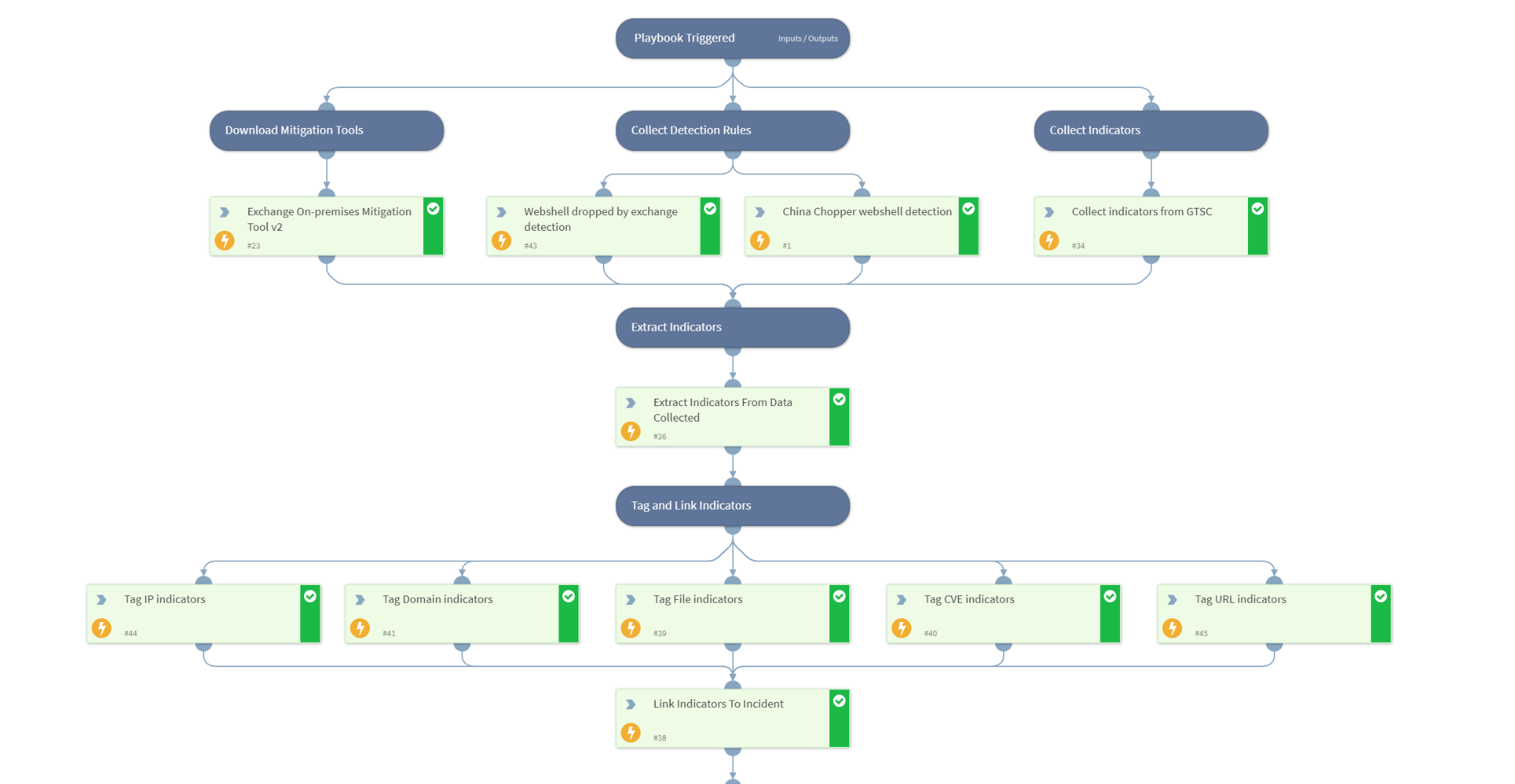
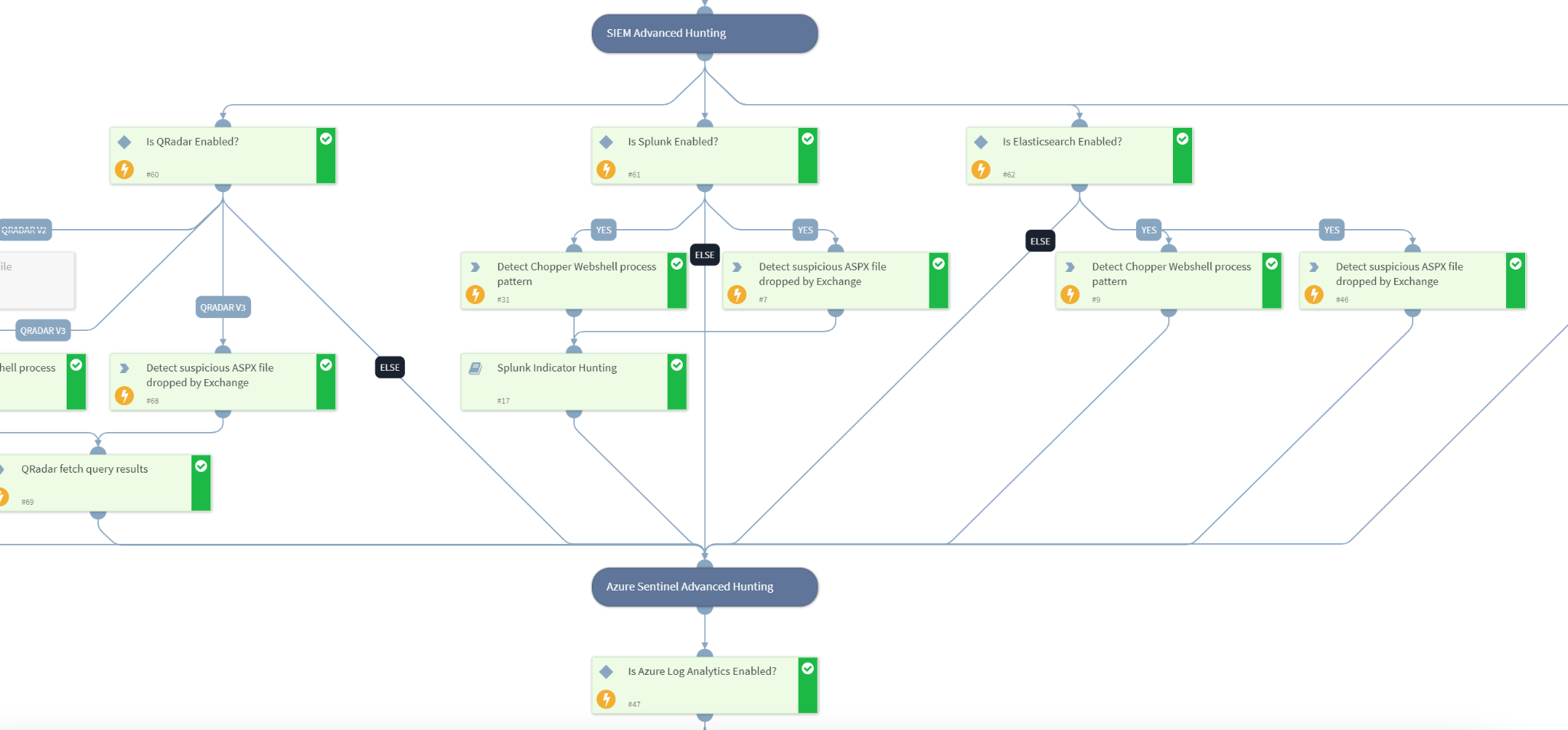
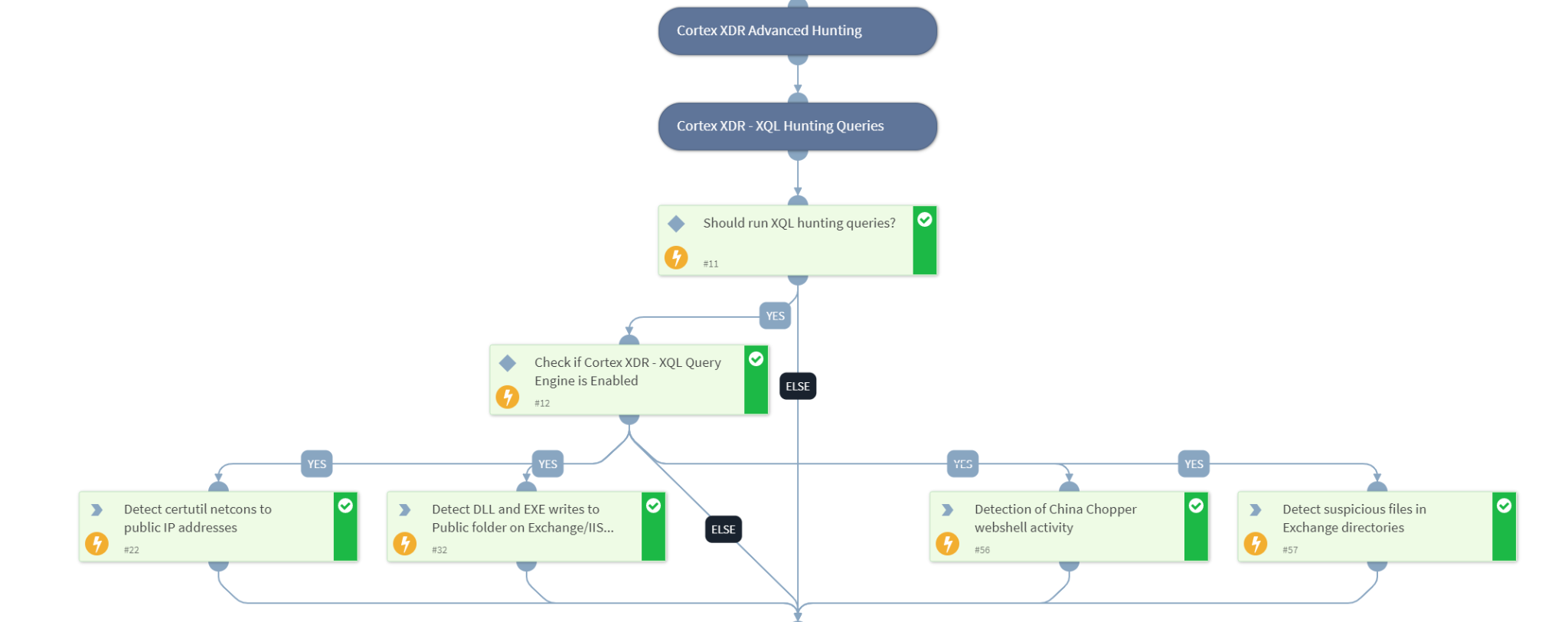
Cortex XSOAR has released a response pack and playbook for the ProxyNotShell CVEs to help automate and speed the mitigation process.
This playbook automates the following tasks:
- Collection of Microsoft mitigation tools, detection rules and Microsoft Global Technical Support Center (GTSC) indicators
- Extraction of these indicators and tagging to incidents
- Hunting for exploitation patterns using Cortex XDR-XQL queries
- Hunting for exploitation patterns using the following SIEM products:
- Azure Sentinel
- Splunk
- QRadar
- Elasticsearch
- Indicator hunting using PAN-OS, Splunk and QRadar
- Mitigation actions such as deploying detection rules and recommended workarounds
See the Cortex XSOAR page on CVE-2022-41040 & CVE-2022-41082 - ProxyNotShell for details on the pack. To find out about other Cortex XSOAR packs and playbooks, visit our Cortex XSOAR Developer Docs reference page.
Cortex Xpanse has the ability to identify and detect Microsoft Exchange servers that may be a part of your attack surface or the attack surface of third-party partners connected to your organization.
Cortex XDR agent running on version 7.7 with content version 710-19877 and above will report the exploitation attempt of the exploitation chain that we have identified.
To ensure you are receiving alerts and monitoring any exploitation attempts:
- Verify that you are using Cortex XDR agent version 7.7 (or newer)
- Verify that your agent is on content update 710-19877 (or newer)
- Perform an agent heartbeat
- Restart Microsoft Internet Information Services (IIS) using the command: “iisreset”
A new Behavioral Threat Protection (BTP) rule has been added to notify XDR customers about exploitation attempts:
The alert can be displayed in two forms, depending on whether you enabled ‘Informative BTP Alerts’ in the agent configuration
| Alert name | Alert Description | |
| Informative BTP Alerts enabled | Webserver Exploitation - 286099623 | Exchange ProxyNotShell CVE-2022-41040 variant - Behavioral threat detected (rule: bioc.sync.exchange_proxynotshell_cve_2022_41040) |
| Informative BTP Alerts disabled | Behavioral Threat Detected | Behavioral threat detected (rule: bioc.sync.exchange_proxynotshell_cve_2022_41040) |
As part of the Cortex XDR multi-layer protection approach, additional already existing Behavioral Threat Protection rules are capable of detecting and preventing the dropping of malicious webshells from a Microsoft Exchange server; those will come into effect until the rule above goes into block mode in the near future.
The malicious URLs and IPs have been released to Advanced URL Filtering and Built-in External Dynamic Lists, respectively.
Prisma Cloud Web-Application and API Security (WAAS) customers receive protections from this threat through the ProxyShell custom rule.
If you think you may have been compromised or have an urgent matter, you can get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
As further information emerges or additional detections and protections are put into place, Palo Alto Networks will update this publication accordingly.
Updated Oct. 11, 2022, at 1:30 p.m. PT.












 Get updates from Unit 42
Get updates from Unit 42