Unit 42 recently identified a variant of MNKit-weaponized documents being used to deliver LURK0 Gh0st, NetTraveler, and Saker payloads. The documents were delivered to targets involved with universities, NGOs, and political/human rights groups concerning Islam and South Asia. Reuse of this MNKit variant, sender email addresses, email subject lines, attachment filenames, command and control domains, XOR keys, and targeted recipients show a connection between the different payload families delivered.
MNKit is the name given to a builder that generates CVE-2012-0158 exploit documents. The documents are in MHTML format and install a malicious payload on the compromised host. We believe MNKit is privately shared between multiple attack groups, but is not widely available.
Information about previous attack campaigns using MNKit is available in the following reports:
- Cmstar Downloader: Lurid and Enfal’s New Cousin
- NetTraveler Spear-Phishing Email Targets Diplomat of Uzbekistan
- Scarlet Mimic: Years-Long Espionage Campaign Targets Minority Activists
For more details on MNKit, see the Sophos publication, Office exploit generators.
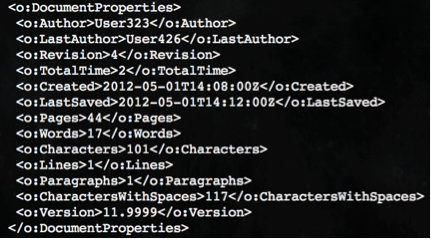
Typical MNKit MHTML files have used User123 or User323 as the Author and LastAuthor element values within their DocumentProperties sections and C:/2673C891/Doc1.files/ as a file directory location. The samples discussed in this blog use User323 and User426 as Author and LastAuthor element values and C:/23456789/Doc1.files/ as a file directory location.
LURK0 Delivery
LURK0 is a family of remote access trojans derived from Gh0st RAT. It has been used by attack groups for years, as discussed by CitizenLab in a publication from 2012 on Tibet-related information operations and has been fairly well analyzed in publicly available reporting. Contained within a subset of the MNKit exploit documents were malicious SFX PE files that delivered LURK0 implants. These PE files were encoded using a decrementing XOR function with the key beginning at 127. Within each SFX are five files:
|
1 2 3 4 5 |
RasTls.exe RasTls.dll MemoryLoad.dump BTFly.dump IconConfigBt.DAT or IconConfigBty.DAT |
The execution of the self-extracting zips side-loading of LURK0 payloads is identifiable by the registry key they create
|
1 |
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\DbxUpdateET\ |
The hashes and compile times of the malicious RasTls.dll files follow:
|
1 2 3 4 5 6 |
838d893581666a2d62bc41497c2214b04b39d0d8e869bcc9bdef7e0e67e1c6a8 0x56E02E36 (Wed Mar 09 09:07:50 2016) 6833f160407175bdb77a6b6b8c9f90ac5c1a73e67b89df6469d12fd6dba54827 0x56F7DE4F (Sun Mar 27 08:21:19 2016) dde54ba5a79ed2c0eb1dad667926ac8ee91afea5540a5fe3c98f21610861accd 0x56B04040 (Tue Feb 02 00:36:00 2016) f2d37ca11fb1e3a900cb79f45a4d97ec770fddedf2f8fc3a5d55d945aa57da40 0x56F7DE4F (Sun Mar 27 08:21:19 2016) f241bdf8dcd4b5c5d15ba5f984b76b9c2a524fd6ad6b8197089723ce3b672505 0x56E02E36 (Wed Mar 09 09:07:50 2016) a1b7ae7d2591b6055dfbf561d4e4527ba2eb18cffba9b50096460618b3972220 0x57315827 (Mon May 09 23:40:23 2016) |
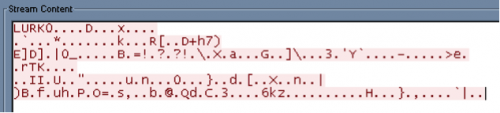
www.amerikauyghur[.]top and dge.123nat[.]com are two command and control domains resolved by the malware. The first domain was previously mentioned by Arbor Networks in a report detailing the targeting of Tibetan, Hong Kong, and Taiwanese interests in their report, The Four-Element Sword Engagement. A subdomain of 123nat[.]com, manhaton.123nat[.]com, was also referenced in Arbor’s report as a LURK0 command and control domain. Below shows the LURK0 string used in the first five bytes of an implant beacon.
Saker Delivery
Saker, often also called ‘Xbox’ and ‘Mongall’, is a malware family used by targeted attack groups who have also deployed NetTraveler and Gh0stRAT.
Two of the sending addresses used to distribute the above LURK0 samples, dolkun2015@gmail[.]com and duqdiniishlari@gmail[.]com, were also used to distributed other types of malware. By observing overlaps in the sending and receiving email addresses as well as the filenames of attachments, we were able to identify additional MNKit exploit documents that also included self-extracting PE files. These PE files were again XOR encoded in the attached documents using the same decrementing key (beginning with 127). These additional SFX PE files are password protected using one of the following passwords:
|
1 2 3 |
aurhuhkdsf!.xlas ^elqwiajdsfile! Ieafsdisdlflei!dsa |
Instead of including RasTls.exe to sideload payloads (as the LURK0 payloads did), within each of the embedded PEs is a single DLL file named msdis.dll which exports a function named JustTempFun. The recently compiled and deployed msdis.dll files' SHA256 hashes and compile timestamps follow:
|
1 2 3 4 5 6 |
5bbe82e975ef161d562cab2fe640f11b576964ad9fc6c3150cfaa43f073d4e01 0x56D7DFB0 (Thu Mar 03 01:54:40 2016) 445a4d12f012c69acaf40011daf5a14f1b7832a9fcd0f3451a773e0f084b44ac 0x56D7DFB0 (Thu Mar 03 01:54:40 2016) 60891bab7fe0baecc9038e194ab6a9222b9f0a7b814eacbd9d20b8c4fe63796c 0x570B5D12 (Mon Apr 11 04:15:14 2016) 74074a1b1b77f7922cafed5437fa0be012275a63c57aa10626fad77f3c85d8e9 0x56D7DFB0 (Thu Mar 03 01:54:40 2016) 68261823356d3471a7794a3cb5cd208101f5660b4928206a22c01df5ed0b4b52 0x56D55EC9 (Tue Mar 01 04:20:09 2016) ec341eebee6c08daf153675698404c9c6805049c31027490432e08c783edfd2c 0x572B0294 (Thu May 05 04:21:40 2016) |
Saker samples construct strings during execution. One such string is the origin of the malware’s name.
The Saker PEs also contain a user agent strings (also constructed manually during execution) of Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; .NET CLR 1.1.4531) and Mozilla/6.0 (compatible; MSIE 9.0; Wis NT 8.1; .NET CLR 2.13431). This second user agent is similar to the user agent, <code>Mozilla/4.0 (compatible; MSIE 6.0; Wis NT 5.0; .NET CLR 1.1.4322), as outlined by FireEye in 2014.
The command and control locations for the Saker samples delivered via MNKit follow:
|
1 2 3 |
bsnl[.]wang www.amerikauyghur[.]top www.onebook[.]top |
amerikauyghur[.]top overlaps with the LURK0 samples previously mentioned. Both onebook[.]top (registered with a registrant email address of interestbook@sina.com and bsnl.wang (registered with a registrant email address of jgjop@yahoo.com) have resolved previously to 103.232.222[.]20.
Using AutoFocus, we were able to locate additional samples that resolved to these domains. The samples are a mix of LURK0, Saker, and PlugX. Their hashes follow:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
02b9681c6b9b56ce6778dd360e38ffb9bd932c4e78256bc082d405b5ac2752bf 0c35a508ece0c9269e176b6b278a96f7ca29e04a2ca2319a91b585f27abfe2f6 0dc315e0b3d9f4098ea5cac977b9814e3c6e9116cf296c1bbfcb3ab95c72ca99 2368f620e812e6adbb9e502a26930922b940a87c488132f2960b4bd97b94f8cc 2a791ef693d410c22ecd6bdbb2855d29816c089d914a4c30ae37df9ff2d66850 343b5b27ebe615f5b97613aa6834740bdae3a90805b6f075d39cc173783aa631 3bbf0f821c89ba03d30deb63eec59c8e9e76c20578ad805de9971bdbcd2855d2 3f3d0a5aa2799d6afe74c5cb6e077e375078b173263c5ca887ffe2e22164b10f 45e39db2a877ff2663efc4d66ed4084ffdb6ddb4926112b7c471872208b96767 4ab388b1310918144ad95e418ebe12251a97cb69fbed3f0dd9f04d780ddd132d 4e749de65f1bb48ec647c5bdf4dd3357f9a1b1970bf2c9e486378e5a2c99f7be 5e818eeb0cffeb6f65f611a17f522560912ae19372e7f734be6df5e35ba82337 6e10e572cecf5b473ea0d75c02d1f7756a08ae0b5c294dee44d9b40f405bae95 81f7e37e6f07dea702e2fd69fc522dc756180f6b79c90e6646e719afd82d1d61 8f0f49e76275c8c129b0ad9b6c2556b0e8d678b4e7cbb20fec64346e135ca04c 940d0770e644c152d60a13f9d40015a1089419361de33fe127e032f4bb446c69 9b3d54069c052a28c8edfedd9acb0a29c550e0594921c96b2d0f179ddd3dc442 9feee2a3fe49fe774d414999ac393655255e7c035ffc93bbd031a2331fd89dc8 aee15bbea68236cbcc622be63fa90134e5da1e7b9af5d87b99b25005a3322976 b625e605932196efbc6c80a18f61a71d27d82935209a1abde2ec591973fed31e b94f87c0afa49526e807a39259552c2176c5aa26ec79896b264b676e531839fd ba9f756ab3e7313388192547e1884eaf3f574c3256b03ac96db829dac90f8653 c39e0fc30c2604b3eb9694591789a8e3d4cee7bcc4f9b03349e10c45304aef59 cb0a6704f39d89e64220be531c09d17af0232f5a2665346aace4fa4930ad6c25 cbb3b49d743c1a463b675f9b369ee8363a8c6ab211cb14df333656bad4af1e25 cf394e482e63803dea495316615d2f63fe610790cbb4fb0d967c91c569dc0be7 d90e40837ef510cd29f28ccd8caa343e22438b792c086e2a6df626948d3a3ab8 dfdbf86793cd212f8073c1531fc0b9de86df3809cee97a69c1b1b4060297ead4 dfe7dcb54842bbb9af8defd4dfeca945ca9a1d7205ad8bebdd53e471f3337b69 e20adee61a6dd2a5fbe39abc94ae4b800e69bee8955042e942ebcf1d66398154 e55912a134902ab73c52cb42f32051745214275b59a95d565cfcb7560d32f601 f4fd8554710017caa042b52122d7985c7f510df8e2c26f1ffa6e27233bfe9b54 |
Pivoting from the first rather unique user agent string we located the following Saker samples on totalhash:
|
1 2 |
331594c845fc7b906d8f9bbac7ad0f46a563d86ba6fa12b5d72a9fed7f23cc3d e4a8996d3cfd9146c8a2c8eaedae655f006c26999e561731c449662bce1f7223 |
These samples beacon to www.togolaga[.]com (103.246.246[.]221) and unisers[.]com (123.254.104[.]32) which respectively were mentioned by the Sophos Rotten Tomatoes publication.
Within AutoFocus the user-agent string was also seen being used by the following Saker sample hashes:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
01a661ee0473efdd5502ac109180bc3eb45ffd5d76a433d248099f1c03bf2a01 0d2600d978f5c1042e93b701654db080aac144dfa2877844334b1d4cd78f4a1d 1a36de918338df965edc2405cedd3a2cc0fce7078805e6430c0f1515ef4770db 23c5832325da3f243db7775688582c9e6e9b21edf276ba2ebfec45eae5952cbe 25339bfd0befe9f493a6b120755e5e87b47df4aeaf4ba9f1157ff1215f37db97 343b5b27ebe615f5b97613aa6834740bdae3a90805b6f075d39cc173783aa631 3677534e326febb704b344dc151c9d0cfd931a72ad625b944614265b12a2677b 5236f08f8a4097c5a7bb854be22a18672e7feacb7ff4e10c502aec518cff5b8e 5d97ec30c481e00d4285246b528745f331be905f453e062bd9c2d506e9386f0e 77ecd4e442d8ef7cf273cadadd6d822206e482c64e43de6298941c4c6ec8eb94 841db1850dc2df1d62c647fd6707a24d2eb4f2e14cce6a4f46bb2a1d5e09aaa4 89adc12913232995e2565c03f4c876953937a6b84102c15170a1034eeb3fad0f 9a45850d4963bfe065ce979ce9e35d9b03ba6f1f065daf34819e04e775841443 9c7959c83f1d37d38dc2db3815d78805ea7f7c49b375738576ae3800bc42324f 9e7e88b3ada8ca3a9484aac3d3abf2fd967d5230695a66241e6101b9593ebd2a c4799e8a8b260b13bd7eae170e2a49459629b9d049f2a704114cd4f8a340f519 c7d7211d1fea69ea6a9697a8f8d21ac40f6d7dc6863708b9a98930271a156c86 d2a5cf434e8a0c63c23e6a3e5cf8a60f259099a706d2d243ffa5c7dbd46fd9d4 dff2e340c2b66847aa7cef8a211102798d46d2bf568c9fd186522db22972f5d2 e4a8996d3cfd9146c8a2c8eaedae655f006c26999e561731c449662bce1f7223 |
These resolve and connect to the following domain names:
|
1 2 3 4 5 |
onebook[.]top (103.232.222[.]20) www.dicemention[.]com (123.108.111[.]228) www.updatenewes[.]com (103.246.246[.]221) softinc[.]pw (210.209.118[.]87) www.notebookhk[.]net (123.254.104[.]50) |
notebookhk[.]net, also mentioned in the Rotten Tomatoes report, was at one point a known PlugX command and control domain. This domain as well as www.dicemention[.]com are noted Korplug (often used to load PlugX) domains outlined by ESET in a blog post here. These domains as well as other overlapping indicators, such as the export function name JustTempFun, were discussed by ProofPoint in a 2015 publication on PlugX targeting Russian military and telecom organizations and by Kaspersky in part 1 of their publication on NetTraveler.
NetTraveler Delivery
NetTraveler is a backdoor used to install other malware, steal information, and provide remote control of a compromised system. The targets previously mentioned by Kaspersky Lab of the NetTraveler operators aligns closely with the recipients of a new set of samples.
Three additional MNKit documents were located as MNKit exploit attachments. Unfortunately, we were unable to locate emails the attachments were sent with. These three samples also included SFX PE files encoded using the same decrementing XOR. Within each PE are three files which side-load NetTraveler. The files are named:
|
1 2 3 |
fsguidll.exe fslapi.dll fslapi.dll.gui |
The hashes and compile timestamps for each fslapi.dll follow:
|
1 2 3 |
8d03cead273180baaae19aca5dd84ea4b7a8c88375c5eba3c3d4b69fce563506 0x574D3F35 (Tue May 31 03:37:25 2016) 682638c3fa5447da1af53b8dd60ee9fdd8489dd5dd4606e8d06082a6a363d362 0x57513FF6 (Fri Jun 03 04:29:42 2016) d953cd81ef92c301ad9c3f43dd183aac65719c729cdf55341954acd6da08bb23 0x571177B8 (Fri Apr 15 19:22:32 2016) |
The fslapi.dll files load their accompanying fslapi.dll.gui files that are XOR encoded. The decoded fslap.dll.gui DLLs include the following embedded URLs, the first of which was previously documented by Unit 42 as a red herring within NetTraveler samples.
|
1 2 |
http://192.168.3[.]201/downloader2013/asp/downloader.asp http://www.duiod[.]com/acid/allebid.asp |
The fslapi.dll files contain an overlay that is used to decode the real C2 as documented in the same Unit 42 NetTraveler blog. The decoded command and control URLs include:
|
1 2 |
http://www.riaru[.]net/revenge/dk/downloader.asp http://www.interfaxru[.]com/dk/dk/downloader.asp |
Both domains have previously resolved to 103.231.184[.]163 which has also hosted www.tassnews[.]net www.info-spb[.]com, both of which have also been used as NetTraveler command and control domains. www.tassnews.net is also the resolved by
|
1 |
ed0caf7ce1fe3b13cef5606515543536e078022c486f0266e02f2f42bd72a128 |
the SFX PE (encoding using the same decrementing XOR) decoded from
|
1 |
80ba8997067025dd830d49d09c57c0dcb1e2f303fa0e093069bd9cff29420692 |
another sample of this MNKit variant.
Tassnews[.]net was registered with a registrant email address of ghjksd@gmail[.]com and info-spb[.]com was registered with a registrant email address of kefj0943@yahoo[.]com. Riaru[.]net was registered with a registrant email address of fjknge@yahoo[.]com on 29 March 2016, which also registered one other domain name, yandax[.]net, on 16 June 2016 using the same authoritative DNS servers and registrar. Interfaxru[.]com was registered with a registrant email address of ganh@gmail[.]com on 18 April 2016 using the same registrar and authoritative DNS servers as riaru[.]net and yandax[.]net. Only one domain name is currently registered by ganh@gmail[.]com, however it would be no surprise if an additional domain is registered by this registrant in the near future.
Putting it All Together
While MNKit has been associated with multiple different groups the reuse of domain names, IPv4 addresses, phishing themes, XOR schemes, and email accounts are strong evidence for linkage between these new attacks and the previously documented ones. The change in PE SFX contents over the three sets of SFX PE files between February 2016 to March 2016, March 2016 to April 2016, and April 2016 to June 2016 time frames show a slight deviation is payload but consistencies in delivery methods. The best defense against MNKit is to ensure your systems are patched for CVE-2012-0158, but in situations where this isn’t possible, exploit mitigation technology like Traps is warranted.
While attribution is a challenging art, it's likely whoever is behind these recent attacks is, through infrastructure, malware families and delivery techniques, somehow related to the previously reported attacks. The attackers have been active for years, will likely continue to be active, and seem to prefer to change tactics only subtly.
AutoFocus users can track the malware discussed above using the following tags:
Examined MNKit Samples and Payloads
MNKit MIME attachments carrying LURK0 payloads:
|
1 2 3 4 5 6 |
d90e40837ef510cd29f28ccd8caa343e22438b792c086e2a6df626948d3a3ab8 0dc315e0b3d9f4098ea5cac977b9814e3c6e9116cf296c1bbfcb3ab95c72ca99 192fc3ed6259e1b226b713829dc101542b9248a686284b71eda285630b6394bc 9feee2a3fe49fe774d414999ac393655255e7c035ffc93bbd031a2331fd89dc8 0c35a508ece0c9269e176b6b278a96f7ca29e04a2ca2319a91b585f27abfe2f6 3a32d88cef7bb8b013e48a77c2845eed344ad317d28a4a45dfe33d5e7b9661c6 |
LURK0 payload files contained within MNKit documents:
|
1 2 3 4 5 6 |
e20adee61a6dd2a5fbe39abc94ae4b800e69bee8955042e942ebcf1d66398154 9b3d54069c052a28c8edfedd9acb0a29c550e0594921c96b2d0f179ddd3dc442 29cfd443459d7a6e4974e780447f60e8f4e251f2a57afeba573086260c6af69b 2a791ef693d410c22ecd6bdbb2855d29816c089d914a4c30ae37df9ff2d66850 6f302dca845c679c7b243ca0b17b568d1d651770f9025874f38bbd1beb1508fe 28fbd4373ddd0714846aeae5a6000da2233eafe4b7eb1505e83b8904525b3f28 |
MNKit MIME attachments carrying Saker payloads:
|
1 2 3 4 5 6 7 8 |
8f0f49e76275c8c129b0ad9b6c2556b0e8d678b4e7cbb20fec64346e135ca04c cf394e482e63803dea495316615d2f63fe610790cbb4fb0d967c91c569dc0be7 45e39db2a877ff2663efc4d66ed4084ffdb6ddb4926112b7c471872208b96767 940d0770e644c152d60a13f9d40015a1089419361de33fe127e032f4bb446c69 dfe7dcb54842bbb9af8defd4dfeca945ca9a1d7205ad8bebdd53e471f3337b69 f4fd8554710017caa042b52122d7985c7f510df8e2c26f1ffa6e27233bfe9b54 343b5b27ebe615f5b97613aa6834740bdae3a90805b6f075d39cc173783aa631 5e818eeb0cffeb6f65f611a17f522560912ae19372e7f734be6df5e35ba82337 |
Saker payload files contained within MNKit documents:
|
1 2 3 4 5 6 7 8 |
4bf5c328915537fbfa46d198373875c7098a719953bcdd1260704d7d40d33ff4 ac12f86ea8f9c195bcd84f4f8cd35876d9df9bdc34d430a31e30bae410d8164f 8ed28bdd1b95022eca20637d3a8d358c6e619a8502104f1ce9d0cf616830d93f 97669b680a0175cc59bb82953b8d4c62f5418020fe008bfd60541375740453cd f942c6b977fbe009ca7d4372930eaa49961c20a1d3c03c31ebc3e5841816c082 856a4a3abe97a4b9c10ae92d9f1d0a565893cfd2bfa934a1127f14baa6413721 94e522b1194c3c4845436a0f0b6657beb832b469823835b1b0e81cf93d42983e 96b4dacef4d6ca5d7ad951014f30148fa8ecc5295cf4c1fadc2d69552e2505d3 |
MNKit MIME attachments carrying NetTraveler payloads:
|
1 2 3 4 |
59933209d3774e501f2384a2591db2d8ab048a3cccf3d7c028f838981a120648 c3c453c43be714ec26ffe23626df9851efdcf65af42d4b6475f7890e96859679 60386112fc4b0ddb833fc9a877a9a4f0fe76828ebab4457637b0827106b269fe 80ba8997067025dd830d49d09c57c0dcb1e2f303fa0e093069bd9cff29420692 |
NetTraveler payload files contained within MNKit documents:
|
1 2 3 4 |
f0911c03276b13019cc32751efcd4e79cb89848721a14fbda8892cb2183c85b9 cc1ffa59fc1033a7d56cd858de44153b6826493af25d7b5fab351de0c1a29ce2 97e2ec38e310e612d2a4118ecf4e513687eb47c0eff196bc4854119148e938e4 ed0caf7ce1fe3b13cef5606515543536e078022c486f0266e02f2f42bd72a128 |













 Get updates from Unit 42
Get updates from Unit 42