
This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers analyzed 1.2 million newly observed hostnames (NOH) containing keywords related to the COVID-19 pandemic from March 9, 2020 to April 26, 2020 (7 weeks). 86,600+ fully qualified domain names are classified as “high-risk” or “malicious” (C2, malware, or phishing), spread across various regions , as shown in Figure 1. The United States has the highest number of malicious domain names (29,007), followed by Italy (2,877), Germany (2,564), and Russia (2,456).
Unit 42 researchers found 56,200+ of the NOHs are hosted in one of the top four popular cloud service providers (CSPs), such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and Alibaba:
-
- 70.1% in AWS
- 24.6% in GCP
- 5.3% in Azure
- <.1% in Alibaba
During our research, we noticed that some malicious domains resolve to multiple IP addresses, and some IP addresses are associated with multiple domains. This many-to-many mapping often occurs in cloud environments due to the use of content delivery networks (CDNs) and can make IP-based firewalls ineffective. Some important findings in this research are:
-
- On average, 1,767 high-risk or malicious COVID-19 themed domain names are created every day.
- Of the 86,600+ domain names, 2,829 domain names hosted in public clouds are found as high-risk or malicious
- 79.2% in AWS
- 14.6% in GCP
- 5.9% in Azure
- .3% in Alibaba
- Adversaries are disguising malicious activities such as phishing and malware delivery in the cloud.
- The higher price and more rigorous screening/monitoring process is likely making malicious actors less willing to host malicious domain names in public clouds.
Threats originating from the cloud can be more difficult to defend because malicious actors leverage the cloud resources to evade detection and amplify the attack. Organizations need to have a cloud-native security platform and a more advanced application-aware firewall to secure their environments. Palo Alto Networks continuously monitor the malicious newly observed hostnames. Prisma Cloud and VM-Series both provide layer-7 firewall capabilities in cloud environments to prevent malicious activities from these domain names.

COVID-19 Themed Domain Names
The COVID-19 related domain names studied in this research were obtained from the RiskIQ dataset. The dataset keeps track of the newly observed domain names that contain keywords related to COVID-19, including “coronav”, “covid”, “ncov”, “pandemic”, “vaccine,” and “virus.” Between March 9th to April 19th, 1.2M domain names were observed with one of these keywords. 86,607 domain names are categorized as high-risk or malicious by Palo Alto Networks URL Filtering. A site is classified as malicious if command and control (C2), malware distribution, or phishing are observed. A site is classified as high-risk if it was previously confirmed to be malicious, hosted on bulletproof ISPs, or shares domains with other malicious sites. We enriched the dataset using the Palo Alto Networks URL Filtering, AutoFocus, WHOIS database, and IP geolocation. Note that due to the size of the dataset, we were unable to individually verify the relationship between each domain name and the COVID-19 pandemic.
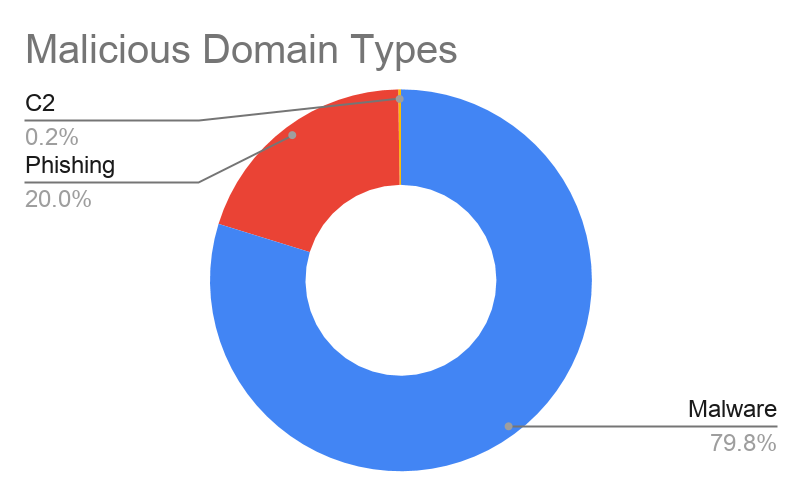
Figure 2 describes the number of NOHs containing each keyword and the number of these NOHs observed every week. Figure 3 illustrates the types of malicious domain names identified in the dataset. On average, 1,767 high-risk or malicious COVID-19 related domain names are created every day. Figure 1 visualizes where the malicious domain names are hosted. The United States has the highest number of high-risk or malicious domain names (29,007), followed by Italy (2,877), Germany (2,564), and Russia (2,456).
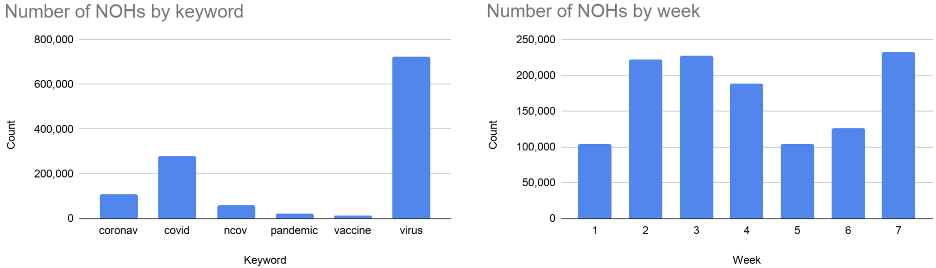 Figure 2. Newly observed hostnames containing COVID-19 related keywords from March 9, 2020 to April 26, 2020.
Figure 2. Newly observed hostnames containing COVID-19 related keywords from March 9, 2020 to April 26, 2020.
COVID-19 NRDs in Public Clouds
When focusing on the cloud-hosted domain names, 56,212 of the NOHs are hosted in one of the top 4 cloud service providers, AWS, Azure, GCP, or Alibaba. 39,494 (70%) of these domain names are hosted in AWS and only 61 (0.1%) of the domain names are hosted in Alibaba. Palo Alto Networks identified 2,829 cloud-hosted NOHs classified as “high-risk” or “malicious.” Figure 4 shows the distribution of NOHs across the 4 CSPs. The left plot is the distribution of all cloud-hosted NOHs, and the right plot is the distribution of “malicious” NOHs in public clouds. Note that Alibaba does not appear in the plot due to its low percentage (< 0.5%). It is interesting to see that only 5% of the NOHs are found high-risk or malicious in public clouds, while 7.5% of NOHs are found high-risk or malicious in the entire internet. We speculate that the higher price and more rigorous screening/monitoring process may make malicious actors less willing to host malicious domain names in public clouds. Note that researchers did not investigate why a large volume of NOHs were hosted on AWS as compared to other prominent CSPs. Nothing discovered during the analysis indicated fundamental vulnerability.
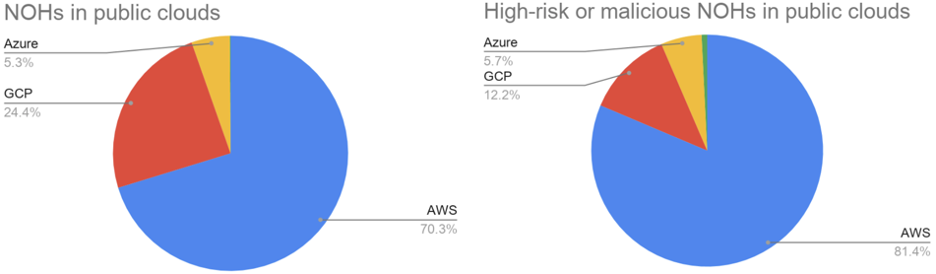 Figure 4. Distribution of NOHs in public clouds.
Figure 4. Distribution of NOHs in public clouds.
During the analysis on cloud-hosted malicious domains, we noticed that multiple domains may resolve to a single IP, and a single domain may be associated with multiple IPs. The first scenario often occurs when the domains are hosted in a CDN, such as Amazon Cloudfront or Cloudflare. In a CDN, hundreds or thousands of domains in the nearby geographical location may resolve to the same IP of an edge server. CDNs reduce network latency and improve service availability by caching the static web content on edge servers. However, because a malicious domain shares the same IPs as other benign domains in the same CDN, it also acts as a cover for malicious domains. In our analysis, a Cloudflare IP 23.227.38[.]64 is associated with more than 150 risky or malicious domains. E.g., covid-safe[.]shop, cubrebocascovid[.]com, www.covidkaukes[.]lt, protection-contre-le-coronavirus[.]com. In the same dataset, more than 2,000 other benign domains also resolve to the same IP.
In the second scenario, when a single domain name resolves to multiple IPs, the domain name may have a set of redundant hosts all serving the same content, or the domain name may again be hosted in a CDN. If a domain name has multiple redundant hosts, a DNS will hold multiple A records for this domain name. If a domain name is hosted in a CDN, the domain name can resolve to different IP addresses based on the client's location. The IP of the closest edge server is always returned when a client queries DNS servers for this domain name. In our analysis, the domain name covid19-fr.johanrin[.]com resolves to 28 different IPs where each IP belongs to an Amazon CloudFront edge server. E.g., 52.85.151[.]68, 99.84.191[.]82, 13.249.44[.]82, 54.192.30[.]118.
This many-to-many domain name to IP mapping makes it difficult to block malicious domain names by IP addresses. A denylisted IP in a layer-3 firewall may fail to block the traffic to/from a malicious domain while unintentionally making many other benign domain names unreachable. A more intelligent layer-7 firewall is necessary to inspect the domain names in the application layer and selectively pass or block sessions.
Conclusion
Cyber threats are evolving rapidly and leveraging real-world events to deceive victims. With COVID-19 driving a surge in cloud adoption, we see not only attacks targeting the cloud users but also threats originating from the cloud. With thousands of malicious domains coming online every day, it is imperative to protect every endpoint with continuous monitoring and automatic threat prevention tools because cloud-hosted applications and services are exposed to the same threats as non-cloud endpoints. The problem becomes even more complicated when working in a multi-cloud environment. Due to the complexity of cloud management, user-induced misconfigurations lead to the most security incidents. Cloud Native Security Platforms (CNSPs) help organizations monitor and secure resources across multiple cloud providers, workloads and hybrid cloud environments.
Palo Alto Networks customers are already protected from these threats by:
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
