This post is also available in: 日本語 (Japanese)
Introduction
Cloud computing is now at the center of nearly every business strategy. But, as with the rapid adoption of any new technology, growing pains persist. To help organizations achieve secure cloud computing and innovation, the cloud-focused division of Unit 42 has released the Spring 2020 edition of the bi-annual Unit 42 Cloud Threat Report.
Based upon threat intelligence from multiple data sources, including publicly available data and proprietary data from Palo Alto Networks, the key findings shed light on security missteps that are actually in practice by organizations across the globe.
Zeroing in on the practices of DevOps, the research in this report indicates that while Infrastructure-as-Code (IaC) offers security teams a systematic way to enforce security standards, this powerful capability remains largely unharnessed, leading to a higher likelihood of exploitable cloud vulnerabilities.
Key Findings
In addition to the top-line findings highlighted in the executive summary, the following highlights dive into specific data points that reinforce the research and recommendations outlined in the report.
CloudFormation Configuration Files
-
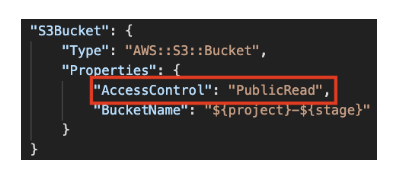
- Nearly 50% of every scanned CloudFormation template (CFT) contains a potentially vulnerable configuration. This makes the odds of deploying a vulnerable cloud template significant. The example to the right highlights an insecure CFT with an S3 bucket exposed to the entire internet.
-
- 42% of all CloudFormation configuration files contained at least one insecure configuration. Notably, templates tend to leave data storage services unencrypted and logging events within cloud environments appear to be weak.
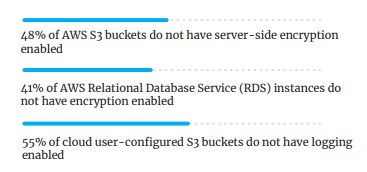
- 42% of all CloudFormation configuration files contained at least one insecure configuration. Notably, templates tend to leave data storage services unencrypted and logging events within cloud environments appear to be weak.
Terraform Configuration Files
-
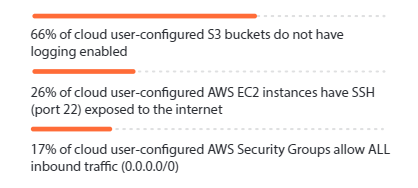
- 22% of all Terraform configuration files contained at least one insecure configuration. Unfortunately, a similar pattern emerged around cloud storage logging and network access control.
Putting the IaC Data Puzzle Pieces Together
DevOps teams are shortening the time to production using infrastructure as code (IaC) templates, but the IaC templates themselves are not the issue. It’s the flawed process by which they are being created. Most IaC templates are created through a simple three-step process: design, code, and deploy.
What’s getting many DevOps teams in trouble is the missing check on risk; scanning for security issues. Just like application code, IaC templates must be scanned for security issues every time they are created or updated. But as the report outlines, this step is currently overlooked.
Unit 42 researchers strongly recommend that every IaC template pulled from a public repository, such as GitHub, be thoroughly scanned for vulnerabilities as part of the CI/CD pipeline.
Three Distinct Goals to Empower Your Business
Shortening time to production using IaC templates can affect the risk profile of cloud infrastructure. The Unit 42 Cloud Threat Report can help your organization stay secure in the cloud in three distinct ways:
-
- Provide situational awareness of the latest adversary tactics that could cause significant security incidents unique to the cloud.
- Empower DevOps and security teams stay ahead of attackers with best practices.
- Instill the mindset that a secure cloud is not possible unless organizations shift left and fully embrace DevSecOps.
Get the full Unit 42 Cloud Threat Report: Spring 2020 for more research and best practices to implement in your organization.
Additional Resources











 Get updates from Unit 42
Get updates from Unit 42