This post is also available in: 日本語 (Japanese)
Executive Summary
When Unit 42 first introduced the concept of Adversary Playbooks, we used a sports analogy to describe how playbooks about specific threats could provide a picture of the adversarial opposition. The concept was straightforward. Threat actors used a playbook to launch attacks against your infrastructure, and network defenders utilized a playbook to defend it. The Adversary Playbook organizes the tactics, techniques and procedures (TTPs) of a particular adversary in a structured format, which can be shared with others and built upon. To accomplish this, we adopted the MITRE ATT&CK Framework and utilized the Structured Threat Information Expression (STIX) language and serialization format for structured information sharing. For several years, we have been releasing Adversary Playbooks derived from our internal intelligence analysis and research, so that anyone could utilize them to defend their networks better, learn about threat actor groups and gain a clearer understanding of the threats we all are facing. This allows you to make better strategic decisions around defense.
However, after a long thought process, we’ve decided to rename our Adversary Playbooks. Adversary Playbooks will now be called Actionable Threat Objects and Mitigations or ATOMs. This change is partly to acknowledge that not every threat we see is always about one specific adversary or threat group. We can develop a detailed picture of actions taken during threat activities, whether we have full campaign visibility or a unique malware set, even when a particular adversary is unknown.
In addition, almost every threat briefing we have ever given has led down a path toward conversations around security posture improvement and threat mitigation. We kept thinking to ourselves: Wouldn’t it be nice to take the intelligence we have of adversary activities and transform that into intelligence-driven security policy recommendations that customers could evaluate and use to improve their security posture? Organizations need a way to quickly diagnose if they are impacted by threats, find out what we are doing to protect them against new threats and determine what they must do to ensure they are protected. ATOMs can assist these customers in utilizing our products within their full capacity.
As such, Unit 42 has decided to introduce intelligence-driven Courses of Action (COA) into every ATOM package, allowing customers to see specific actions that can be used to address and mitigate the threat. With this strategic change, we felt that a nomenclature change was necessary and that the name ATOMs more appropriately represents the information provided. We have also moved the ATOM viewer directly into the Unit 42 website for added convenience.
Intelligence-Driven Courses of Action
Whenever we share our research, whether through a blog post, at a security conference or through direct conversations, we are often asked for more information. While these questions are primarily threat- or industry vertical-focused, the conversation’s main crux boils down to “How do I know that I’m protected?”
As a threat intelligence team, we know that in order to provide that answer, we have to break down the threat into the observed behaviors utilized by the adversary during their attempt to exploit or compromise. These behaviors are currently represented in our ATOMs by using the MITRE ATT&CK framework, which maps out a particular threat’s activities and stores those threat objects in STIX 2.0 format for ease of information sharing. This allows us to provide examples of high-level tactics used during attempts to exploit or compromise and the techniques they’ve used to achieve success.
Once these TTPs are broken down, we can translate these behaviors into security policy recommendations as a built-in security mapping solution depicted as a COA. This will help guide security teams with updating security configurations regarding whichever threat they are specifically concerned about.
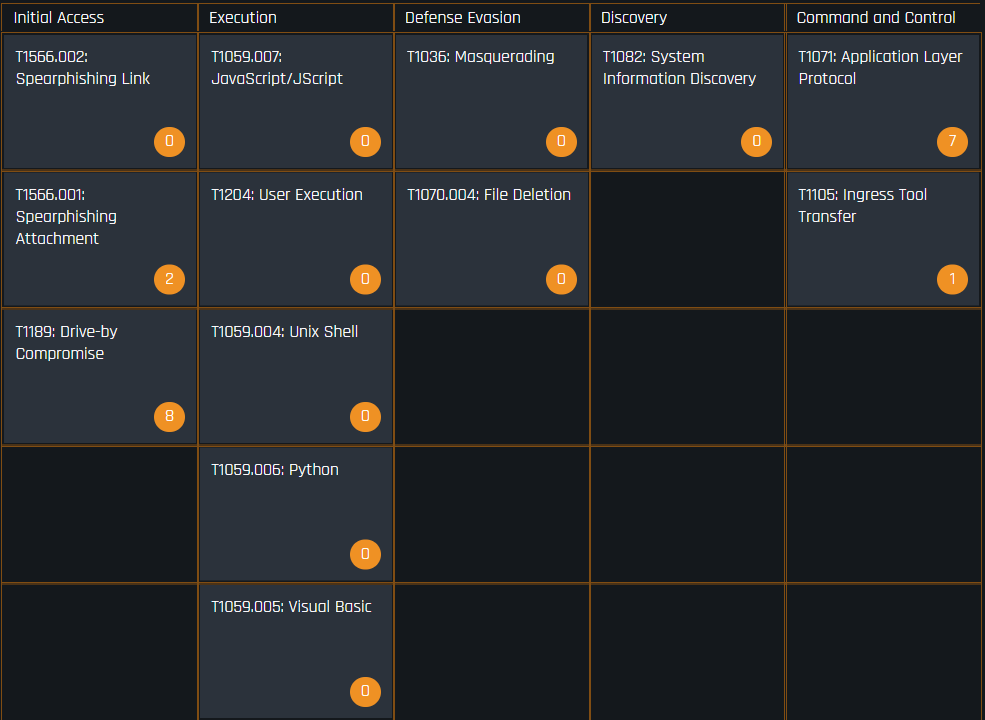
As an example, as shown in Figure 1, you can view all of the associated ATT&CK techniques that we have mapped out to any given threat. However, with the introduction of COA, you can now see security recommendations by clicking directly on the behavior you are interested in hardening against.
When you click on the first technique shown in Figure 1 under “Initial Access,” T1566.002: Spearphishing Link, you are presented with the recommended COA, organized by Palo Alto Networks product.
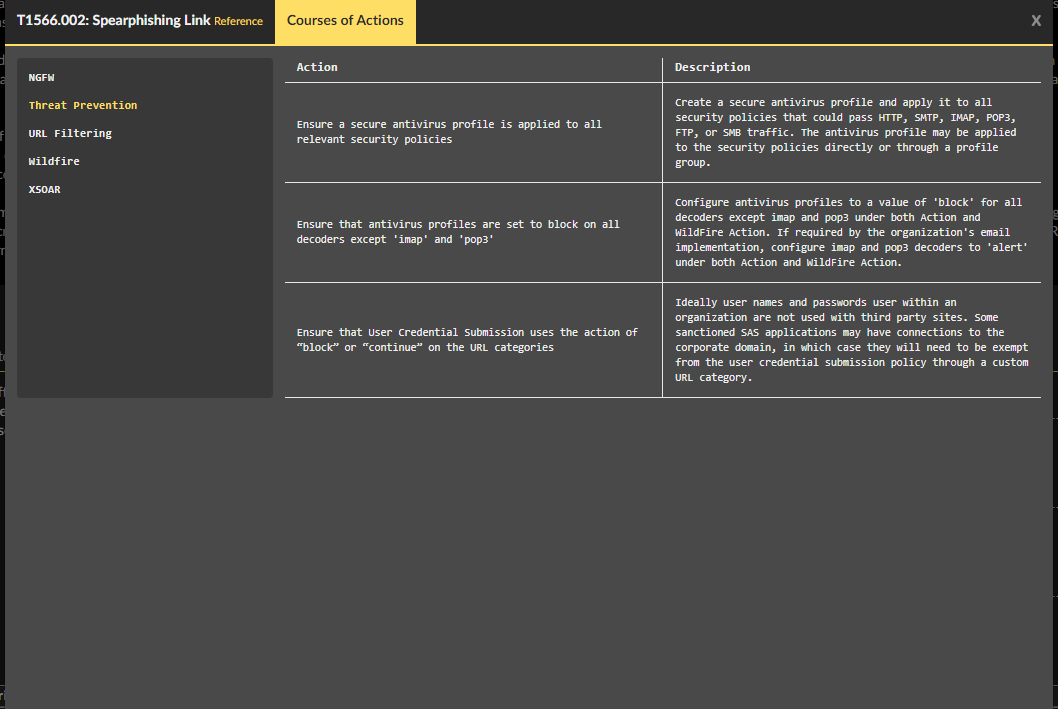
The COA help users understand how to utilize various Palo Alto Networks products to mitigate specific attack techniques. They are driven by threat intelligence and deep knowledge of best practices. These recommendations are available to review whenever Palo Alto Networks customers need to assess what to do next after hearing about new threats targeting their environment.
Threat Assessments and Actionable Threat Objects and Mitigations (ATOMs)
With these announced changes, we will be focusing more on generating Threat Assessments and publishing them on the Unit 42 website. For organizations to benefit from the latest research and the most up to date best practices and mitigation recommendations, we need to deliver timely, relevant and actionable intelligence that our customers and others can consume. We expect ATOMs and Threat Assessments to be vehicles everyone can use to identify and understand information about new threats and, at the same time, provide our customers with mitigation recommendations to simplify the hardening of their infrastructures on top of the protections and general best practices we currently offer.
The following Threat Assessments have been published to our website and linked to ATOM STIX 2.0 objects complete with COA:
- Threat Assessment: WastedLocker Ransomware Activities
- Threat Assessment: EKANS Ransomware
- Threat Assessment: Hangover Threat Group
Conclusion
Unit 42 has renamed the Adversary Playbooks to Actionable Threat Objects and Mitigations (ATOMs) and has directly relocated the ATOM viewer into the Unit 42 website. Furthermore, Unit 42 has enhanced the ATOM packages, introducing intelligence-driven security best practices and mitigation recommendations, mapped to MITRE ATT&CK techniques and presented as Courses of Action (COA), which allow consumers to understand more about the threat and how to mitigate it.
Each ATOM campaign provides indicators of compromise, the ATT&CK techniques utilized and COA for Palo Alto Networks products in one STIX 2.0 object deliverable that can easily be ingested for various purposes, whether for tactical defense, longer-term defense planning or simulating attacks.
The first part of our COA work identified the vehicle to get security best practices for specific threats delivered to the customer. We are currently working with our product teams to integrate the COA directly into our product environment, so that they are available within the interfaces that our customers now use and see.
In the future, we expect to be able to take newly identified threats, utilize the COA we align to that threat and report back to the customer. We can describe the potential impact of the threat, whether the customer is protected and through which products or services, and provide recommendations that can be used to address any weaknesses directly within each given product.











 Get updates from Unit 42
Get updates from Unit 42