Executive Summary
Palo Alto Networks has been actively researching and developing security capabilities using AI. In an effort to audit web applications for Broken Object-Level Authorization (BOLA) vulnerabilities, Unit 42 researchers developed an automated BOLA detection tool leveraging GenAI.
In 2023, we used our tool to test an open-source project, Easy!Appointments, and found 15 BOLA vulnerabilities. We notified the vendor, who has since patched the vulnerabilities. The number of issues we found highlights the prevalence of BOLA vulnerabilities in API applications and underscores the importance of continuously scrutinizing software for these potentially severe issues.
Easy!Appointments is a popular tool used for scheduling and managing appointments, as well as synchronizing data with widely used calendar services. The vulnerabilities we discovered allow low-privileged and logged in users (such as customers) to view and manipulate appointments created by more privileged users (such as providers and admins).
The vulnerabilities we discovered, tracked as CVE-2023-3285 to CVE-2023-3290 and CVE-2023-38047 to CVE-2023-38055, all affect different API endpoints. They have been assigned CVSS scores ranging from 5 to 9.9, with seven vulnerabilities scoring 9.9.
Upon discovering these vulnerabilities, we collaborated closely with the maintainers to patch all the issues in the latest version 1.5.0. To mitigate the risks, organizations are advised to upgrade to Easy!Appointments version 1.5.0 or later immediately. Please reach out to info@easyappointments.org for more information on updating to the latest version.
Cortex Xpanse and Cortex XSIAM customers with the ASM module are able to detect all exposed Easy!Appointments instances as well as known insecure instances via targeted attack surface rules.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | API Attacks, BOLA |
Broken Object-Level Authorization (BOLA)
Broken object-level authorization (BOLA), also known as insecure direct object references (IDOR), is a prevalent type of vulnerability in modern APIs and web applications. It is ranked as the top risk in the OWASP API top 10 and the fourth most reported vulnerability type in the HackerOne Global Top 10.
As explained in another recent article on a BOLA vulnerability, BOLA occurs when an application fails to properly check if a user has the necessary permissions to access, modify or delete an object. The term object in this context refers to various types of data within a system, examples of which include messages, photos, trips, user profiles and invoices.
Attackers can exploit BOLA vulnerabilities in API endpoints by altering object identifiers within requests. Such manipulations can lead to unauthorized access to user data, resulting in data leaks, manipulation of data or even complete account takeovers.
BOLA Detection
While manually looking for BOLAs is generally straightforward, automating this process is challenging. Testing for BOLA has historically been performed manually due to the complexity of web applications' workflow and business logic, along with the stateful nature of modern web applications.
Researchers at Palo Alto Networks are actively developing new technology that leverages AI to automate the detection of BOLA vulnerabilities. We're internally using these AI detection operations to allow us to test new advancements daily.
Our most recent disclosed vulnerability was CVE-2024-1313, a BOLA vulnerability in Grafana, an open-source project with over 20 million users.
Overview of Easy!Appointments
Easy!Appointments is an open-source web application designed for scheduling appointments. It is highly customizable, allowing integration with existing websites and synchronization with Google Calendar and CalDAV servers.
The software is free and supports commercial use, targeting professional users through premium services. It is popular among large organizations and a committed developer community maintains it.
Easy!Appointments features a permissions system for different user roles. Every role except admin is considered low-privileged.
- Customer: This role can only access the booking page to manage their appointments.
- Provider: This role manages appointments and customer information but cannot handle administrative tasks like managing services or system settings.
- Secretary: This role is similar to providers but doesn't serve appointments directly. It manages schedules for assigned providers without accessing administrative settings.
- Admin: This role has full access to all system resources and actions, including service definitions, user management and system settings.
Explanation of Vulnerabilities
This section outlines the 15 vulnerable API paths uncovered in our research. Most of these vulnerabilities are exploitable through APIs, not UI consoles. Each path may be vulnerable to one or multiple HTTP methods, such as GET, POST, PUT and DELETE.
The lack of sufficient checking and validation of caller identities at the backend makes most API endpoints vulnerable to BOLA. Among the 15 CVEs identified, nine are rated as Critical severity (CVSS 9.0 or higher), five as High severity (CVSS between 7.0-9.0), and one as Medium severity (CVSS between 4.0-6.9).
- CVE-2023-3287 (CVSS=9.9): A BOLA vulnerability in POST /admins allows a low-privileged user to create a high-privileged user (admin) in the system. This results in privilege escalation.
- CVE-2023-38048 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /providers/{providerId} allows a low-privileged user to fetch, modify or delete a privileged user (provider). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38049 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /appointments/{appointmentId} allows a low-privileged user to fetch, modify or delete an appointment of any user (including admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38050 (CVSS=9.1): A BOLA vulnerability in GET, PUT, DELETE /webhooks/{webhookId} allows a low-privileged user to fetch, modify or delete a webhook of any user (including admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38051 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /secretaries/{secretaryId} allows a low-privileged user to fetch, modify or delete a low-privileged user (secretary). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38052 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /admins/{adminId} allows a low-privileged user to fetch, modify or delete a high-privileged user (admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38053 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /settings/{settingName} allows a low-privileged user to fetch, modify or delete the settings of any user (including admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38054 (CVSS=9.9): A BOLA vulnerability in GET, PUT, DELETE /customers/{customerId} allows a low-privileged user to fetch, modify or delete a low-privileged user (customer). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-38055 (CVSS=9.6): A BOLA vulnerability in GET, PUT, DELETE /services/{serviceId} allows a low-privileged user to fetch, modify or delete the services of any user (including admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-3285 (CVSS=7.7): A BOLA vulnerability in POST /appointments allows a low-privileged user to create an appointment for any user in the system (including admin). This results in unauthorized data manipulation.
- CVE-2023-3286 (CVSS=7.7): A BOLA vulnerability in POST /secretaries allows a low-privileged user to create a low-privileged user (secretary) in the system. This results in unauthorized data manipulation.
- CVE-2023-3288 (CVSS=7.7): A BOLA vulnerability in POST /providers allows a low-privileged user to create a privileged user (provider) in the system. This results in privilege escalation.
- CVE-2023-3289 (CVSS=7.7): A BOLA vulnerability in POST /services allows a low-privileged user to create a service for any user in the system (including admin). This results in unauthorized data manipulation.
- CVE-2023-38047 (CVSS=8.5): A BOLA vulnerability in GET, PUT, DELETE /categories/{categoryId} allows a low-privileged user to fetch, modify or delete the category of any user (including admin). This results in unauthorized access and unauthorized data manipulation.
- CVE-2023-3290 (CVSS=5): A BOLA vulnerability in POST /customers allows a low-privileged user to create a low-privileged user (customer) in the system. This results in unauthorized data manipulation.
CVE-2023-38049
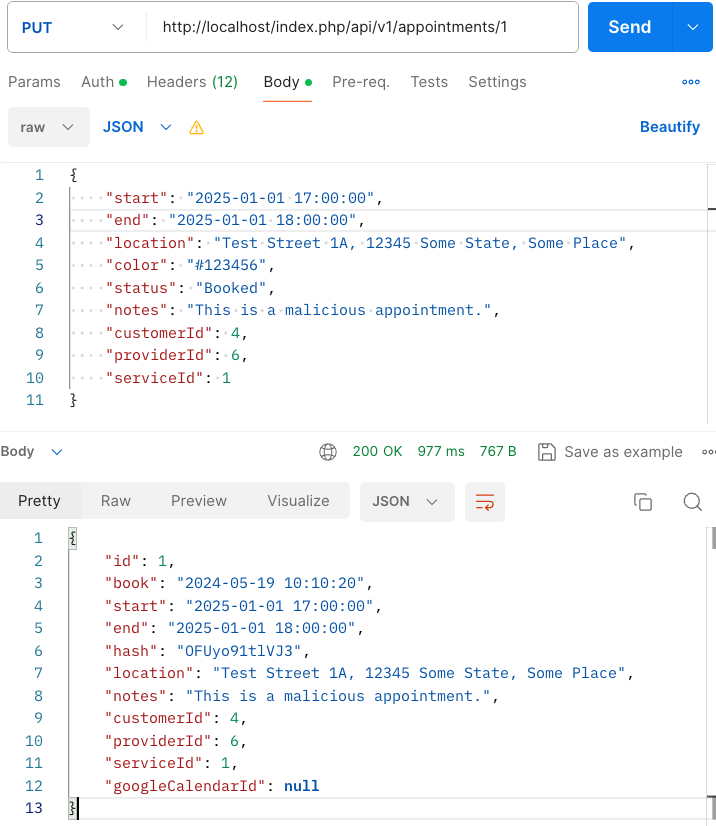
To illustrate the issue that underpins the vulnerabilities we identified, let’s look at CVE-2023-38049 as an example. A user with a secretary role could exploit the vulnerability to modify an arbitrary user's appointment. According to the official documentation, the secretary role is intended to perform organizational tasks only for their assigned providers.
In particular, a malicious secretary could perform GET, PUT and DELETE operations on the API path /appointments/{appointmentId} to modify another user's appointment. It is important to note that these operations cannot be performed by a secretary through the user interface. They can only be executed via API calls. This results in a discrepancy between the API and UI behavior.
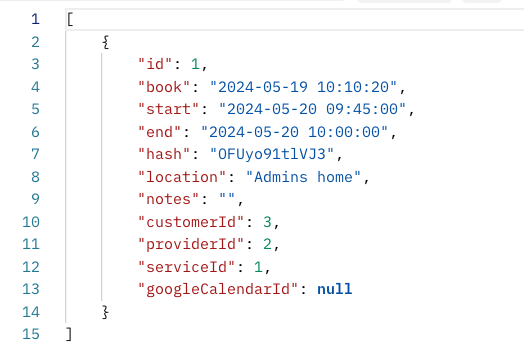
We created an admin user and used it to create an appointment with appointment_id equal to 1. Figure 1 shows the response of GET /appointments/1 request. The response includes information such as the following:
- Appointment ID
- Start and end times
- Location
- Customer
- Provider
- Service
- Hash
This data is sensitive and should only be accessible to the user who created the meeting.
We then used a low-privileged secretary user to manipulate the appointment created by the admin user through the vulnerable endpoint, PUT /appointments/{appointmentId}. Figure 2 shows the HTTP requests sent with the secretary user.
Vulnerability Impact
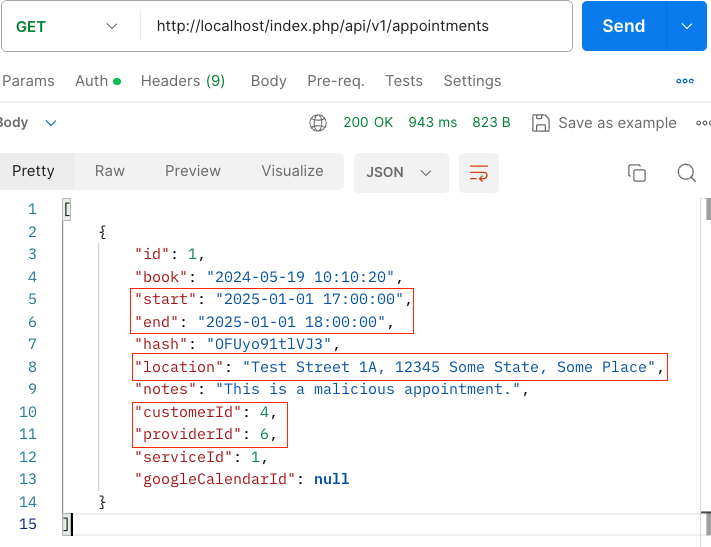
Figure 3 shows the appointment being modified with different start and end times, location, and identities of the provider and customer. Despite these changes, the appointment hash remained unchanged, giving the false impression that the original appointment was not altered.
Disclosure Process
- Aug. 23, 2023: We reported the vulnerabilities to Easy!Appointments’ maintainers through email
- Oct. 9, 2023: Easy!Appointments’ maintainer confirmed the vulnerabilities
- April 24, 2024: Unit 42 researchers sent a follow-up email to the maintainer to inquire about the patch release timeline
- May 6, 2024: 15 CVEs were reserved
- May 14, 2024: Easy!Appointments released version 1.5.0-alpha.1 (develop) that patched all the vulnerabilities
- July 1, 2024: Easy!Appointments released version 1.5.0-beta.1 (develop) that patched all the vulnerabilities
- July 7, 2024: Easy!Appointments released version 1.5.0 (production) that patched all the vulnerabilities
Conclusion
As the use of APIs is increasing exponentially, so is the prevalence of API vulnerabilities and BOLA vulnerabilities in particular. This article details the 15 BOLA vulnerabilities Unit 42 researchers discovered in Easy!Appointments using a new automatic methodology that leverages AI. Due to the ease of exploitation and potential impacts of these vulnerabilities, we encourage affected organizations to update to the patched version as soon as possible.
Researchers at Unit 42 are committed to fortifying open-source software and innovating technology to discover new vulnerabilities more efficiently and effectively. Palo Alto Networks customers are better protected by our latest research findings and insights.
Cortex Xpanse and Cortex XSIAM customers with the ASM module are able to detect all exposed Easy!Appointments instances as well as known insecure instances via targeted attack surface rules.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200












 Get updates from Unit 42
Get updates from Unit 42