This post is also available in: 日本語 (Japanese)
Ransomware attacks can cause victims to feel powerless. We’ve seen extortion demands rise dramatically over the past few years. They’re now regularly priced in the millions – and sometimes even tens of millions – of dollars. But the costs reach far beyond the extortion demands themselves.
Fallout can include operational downtime, brand damage, data discovery fees, litigation and impact on data privacy. We’re increasingly seeing cases where ransomware attacks cripple victim organizations with impact that affects their employees, customers and even commodity prices.
With so much at stake, it’s critical that organizations prepare themselves to reduce the risk of falling victim to a ransomware attack and minimize the impact if cyber extortionists do succeed in compromising their networks.
This blog explains what ransomware is and how attacks play out. Most importantly, it provides practical tips on how organizations can prevent these attacks, citing the lessons that our Unit 42 consultants have learned working hundreds of ransomware cases involving government agencies and businesses of all sizes in every industry. It concludes with 12 tips for fighting ransomware.
The Definition of Ransomware
Ransomware is a type of malware used by cybercriminals for financial gain. It takes over the victim’s files or systems, and the attacker demands a ransom be paid in exchange for a decryption key, which presumably will return the files to their original state. Since the end of 2019, the definition of ransomware has extended to also include data extortion, as threat actors have begun to exfiltrate data during a ransomware attack to blackmail victims into paying the ransom to avoid having their information posted on leak sites or put up for sale. This is commonly referred to as “double-extortion.” Also, we’re increasingly seeing attackers leverage a third approach to pressure victims into paying: launching DDoS attacks that shut down public websites.
The Numbers Behind Ransomware Attacks
The potential costs of a ransomware attack are too high to ignore:
- The average ransom paid in 2020 was more than $312,000, a 171% increase from 2019, According to the 2021 Unit 42 Ransomware Threat Report.
- So far this year, it’s nearly tripled to about $850,000. For a large enterprise, the average is nearly $3 million.
- The highest ransom paid by an organization doubled from 2019 to 2020, from $5 million to $10 million.
- The highest ransom demand last year doubled, from $15 million to $30 million. This year we’ve seen it as high as $50 million.
- Downtime associated with a ransomware attack averaged 16 days in Q2 of 2020.
To hear more about the financial impact of ransomware, check out this video.
How a Ransomware Attack Works
The most common type of ransomware circulating today is malware that scrambles the contents of files. It typically uses very strong – sometimes virtually uncrackable – encryption protocols that prevent the owner from accessing the files. The perpetrators demand a ransom in exchange for return of the files. Since the end of 2019, we have also observed an increasing trend where attackers behind ransomware variants such as Maze and LockBit exfiltrate data from the victim during the attack and post stolen data publicly to shame victims into paying their ransom. This places an even greater burden on the victim, as the exposed data could contain sensitive information, escalating costs and brand exposure.
Ransom requests are often presented in the form of a pop-up screen, which includes the ransom amount demanded, a desired payment method and a deadline. These days, criminals tend to favor cryptocurrency as a form of payment and will often request specific types (usually Bitcoin, but sometimes Dash or Monero).
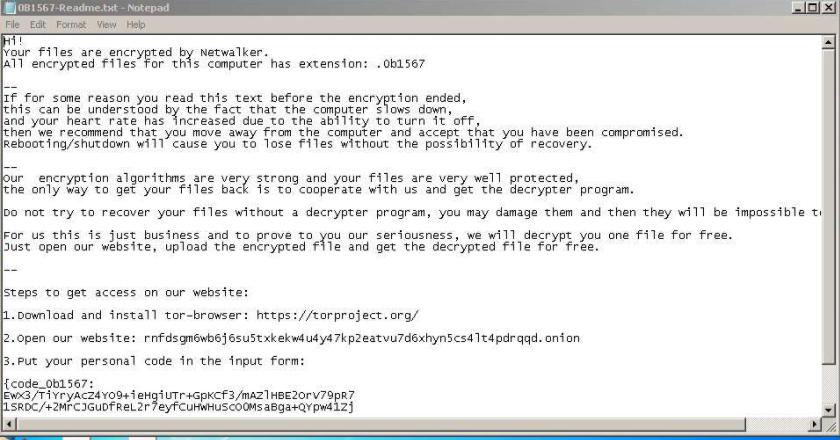
The attackers promise that the file or system will be returned to normal – once the ransom is paid. Usually, the attacker will send a decryption key that the victim can use to reverse the encryption applied to the files. In the cases where data exfiltration takes place, the attacker may also agree to not post any additional stolen data and may sometimes promise to show evidence it has been destroyed.
However, even if you pay the ransom, there’s no guarantee that the cybercriminal will follow through on their end of the bargain. Even if your files are restored to their original state, it’s possible that the perpetrator will maintain a copy of the stolen data and could potentially sell it on the dark web or use it against you in future attacks. We have observed attackers sending non-functioning or only partially functioning decryption keys. In some cases, we have even seen them send keys that contain additional malicious files or backdoors to give threat actors access to the environment in the future, which is why we are always careful to reverse engineer any key to ensure it is safe for our clients.
How Ransomware Infects Networks
A ransomware attack consists of two main steps. Initially, the malware has to find its way onto a device. Then comes the encryption stage: The ransomware must find and encrypt files and communicate the ransom terms to the victim. Some types of ransomware don’t stop there and can spread from device to device, affecting all computers in a network.
So how does the ransomware find its way into a network in the first place?
These are the three main methods our incident responders have observed in the hundreds of cases we’ve worked over the past year:
- Email links or attachments: The user is sent a phishing email with a malicious link or attachment, which leads to the downloading of the ransomware. File extensions to watch out for are .exe and .zip as these are commonly used to distribute ransomware.
- Remote Desk Protocol (RDP) attacks: Use of this method is growing, given its ease of use and the high level of access it gives to attackers. Cybercriminals exploit publicly available or weak credentials and brute-force via the RDP protocol to gain access to a victim’s environment before remotely deploying and executing the ransomware. The ransomware gang CrySIS/Dharma is known to push ransomware via RDP attacks.
- Virtual Private Network (VPN) attacks: Cybercriminals identify and exploit unsecured and unpatched remote access VPN servers to gain access to a network, then distribute malware. For example, the threat actors responsible for the ransomware variant Sodinokibi have been known to leverage this trend.
Once on a device, ransomware typically searches for specific types of files to encrypt. It might also encrypt shadow files, backups and filenames, making recovery more difficult.
Want to learn more? Here's a quick video on techniques we've observed in ransomware attacks.
12 Tips for Fighting Ransomware Attacks
- Keep your software up to date with the latest version as updates often patch security vulnerabilities. This includes patching VPN servers and upgrading from Server Message Block Version 1 (SMBv1) to limit adversaries from using the file sharing protocol to move laterally within the systems.
- Maintain regular backups of your files and systems and ensure the backups are stored off network. By doing this, threat actors cannot gain access to disable or delete backups to prevent recovery.
- Conduct comprehensive, rigorous end user training on standard and advanced phishing and social engineering techniques. It is important to tailor the education to fit your organization and employee roles.
- Leverage log aggregation systems to increase log retention, integrity and availability.
- Understand where sensitive data lives and implement strong access controls to protect that data. Monitor and audit access regularly.
- Invest in a trusted endpoint detection and response platform to help with ransomware detection, and employ the use of firewalls to block malicious traffic.
- Implement strict policies surrounding the use of employee-owned devices for work-related activities and limit user privileges whenever possible.
- Integrate multi-factor authentication (MFA) for all remote access, internet accessible and business email accounts.
- Disable any direct external RDP access and ensure all external remote administration is conducted through an enterprise-grade MFA VPN.
- Adopt account administration best practices across the organization, including requiring unique and complex passwords that are at least 15 characters in length so they cannot be easily brute forced.
- Limit the use of privileged accounts, and do not reuse local administrator account passwords to prevent initial access by attackers, privilege escalation and lateral movement across the network.
- Create and maintain an asset inventory.
For more tips, check out this video on lessons learned.
Conclusion
Ransomware continues to be a pervasive and dangerous threat to organizations. With the total cost of a ransomware attack continuing to rise, organizations should embrace best practices to protect themselves and arm themselves with a strong understanding of the ransomware threat landscape.
Organizations should also make sure to have an incident response plan in place in case of an attack. Unit 42 offers a Ransomware Readiness Assessment to help organizations get started on bolstering defenses.
Palo Alto Networks customers are protected from many ransomware threats by:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- Indicators for known ransomware.
- Anti-Ransomware Module.
- Local Analysis detection.
- Cortex XSOAR: Cortex XSOAR’s ransomware content pack can immediately help incident response, threat intelligence and SecOps teams to standardize and speed-up post-intrusion response processes. This content pack automates most of the ransomware response steps, allowing the incident response and SecOps teams to add their guidance and input.
- Next-Generation Firewalls: DNS Signatures detect known command and control (C2) domains, which are also categorized as malware in URL Filtering.
- AutoFocus: Tracking related activity using relevant tags.
Learn more about ransomware and see the steps your business should initiate immediately if you find yourself under attack.









 Get updates from Unit 42
Get updates from Unit 42