Introduction
High-profile software supply chain attacks such as SolarWinds and Kaseya VSA have shed a glaring light on the disparity between organizations’ perceptions of security within their cloud infrastructure, and the reality of threats in their supply chains that can impact business catastrophically.
In the Unit 42 Cloud Threat Report, 2H 2021, our researchers dive deep into the full scope of supply chain attacks in the cloud and explain often misunderstood details about how they occur. We also provide actionable recommendations any organization can adopt immediately to begin protecting their software supply chains in the cloud.
How the Research Was Conducted
We analyzed data from a variety of public data sources around the world in order to draw conclusions about the growing threats organizations face today in their software supply chains. In our analysis, we found:
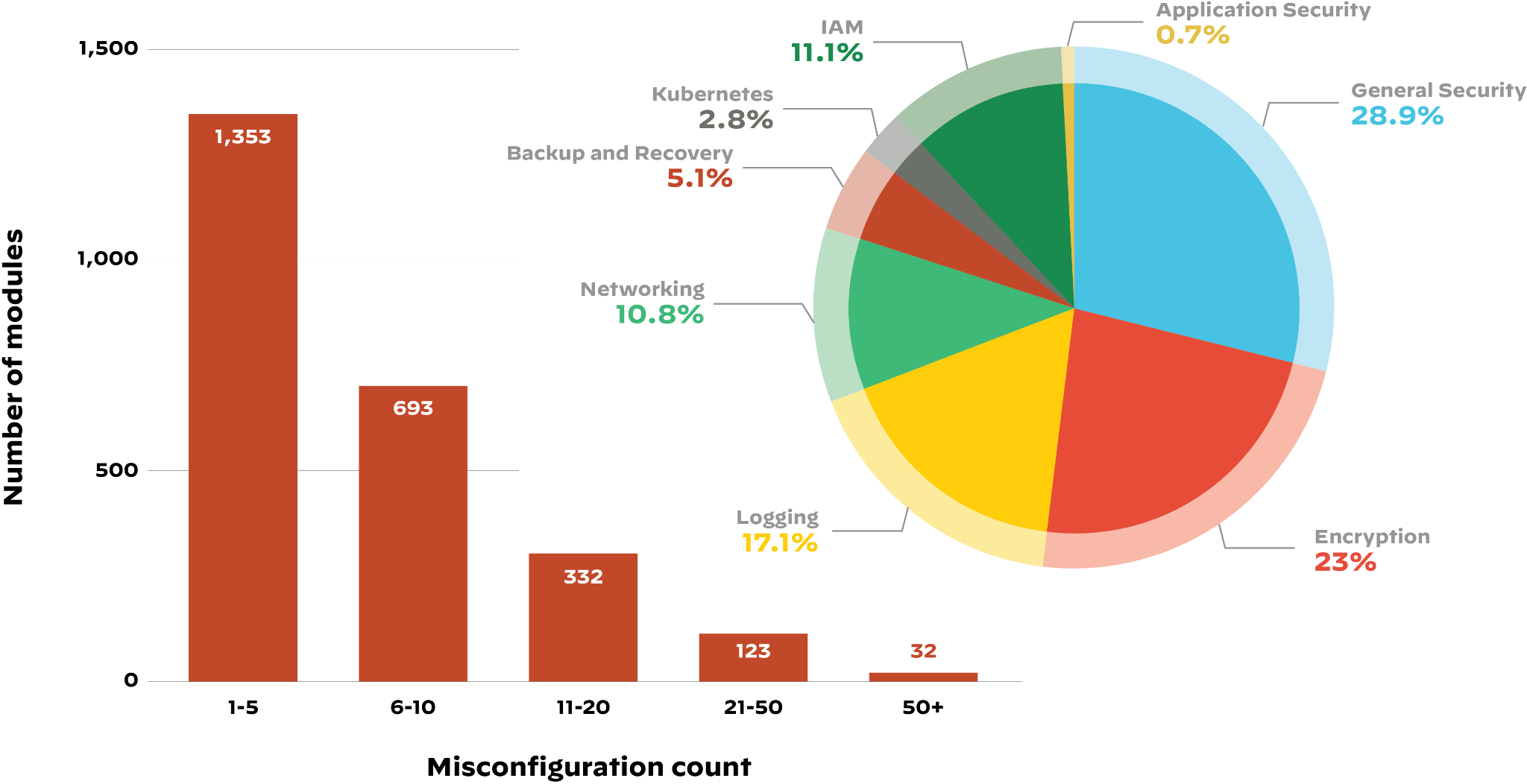
- 63% of third-party code templates used in building cloud infrastructure contained insecure configurations.
- 96% of third-party container applications deployed in cloud infrastructure contain known vulnerabilities.
In addition to analyzing data, our researchers were commissioned by a large SaaS provider (a customer of Palo Alto Networks) to run a red team exercise against their software development environment. In just three days, a single Unit 42 researcher discovered critical software development flaws that left the customer vulnerable to an attack similar to those on SolarWinds and Kaseya VSA.
Key Findings
Poor Supply Chain Hygiene Impacts Cloud Infrastructure
The customer whose development environment was tested in the red team exercise has what most would consider a mature cloud security posture. However, their development environment contained several critical misconfigurations and vulnerabilities, enabling the Unit 42 team to take over the customer’s cloud infrastructure in a matter of days.
Third-Party Code != Secure Code
In most supply chain attacks, an attacker compromises a vendor and inserts malicious code in software used by customers. Cloud infrastructure can fall prey to a similar approach in which unvetted third-party code could introduce security flaws and give attackers access to sensitive data in the cloud environment. Additionally, unless organizations verify sources, third-party code can come from anyone, including an Advanced Persistent Threat (APT).
Organizations Need to Shift Security Left
Teams continue to neglect DevOps security, due in part to lack of attention to supply chain threats. Cloud native applications have a long chain of dependencies, and those dependencies have dependences of their own. DevOps and security teams need to gain visibility into the bill of materials in every cloud workload in order to evaluate risk at every stage of the dependency chain and establish guardrails.
Secure Your Software Supply Chain in the Cloud
While the report provides key knowledge about software supply chain attacks themselves, the main focus is on how you can protect your organization from this growing threat starting immediately.
Download your free copy of the Unit 42 Cloud Threat Report, 2H 2021, today to learn how common supply chain issues undermine security in the cloud and what you can do to gain confidence in your supply chain.
Additional Resources
- Unit 42 Cloud Threat Report Update: Cloud Security Weakens as More Organizations Fail to Secure IAM
- Unit 42 Cloud Threat Report, 2H 2020 (Identity and access management security)
- Unit 42 Cloud Threat Report, 1H 2021 (COVID-19’s impact on cloud security)
- Infographic: Software Supply Chain Threats in the Cloud
- Unit 42 Security Consulting












 Get updates from Unit 42
Get updates from Unit 42