Executive Summary
For the Unit 42 Cloud Threat Report, 2H 2020, Unit 42 researchers used data from the major cloud service providers (CSPs) – Amazon Web Services (AWS), Microsoft Azure and Google Cloud – to unearth the most common types of alerts globally. Policy violations fell into four categories:
- Identity and Access Management (IAM).
- Logging, Versioning and Tracing.
- Encryption.
- Exposed Systems and Services.
IAM alert data, along with original research into IAM misconfigurations, can be found in the full report. This blog examines the latter three categories of logging, encryption and exposed services. All research took place from May to August 2020 and included the Americas; Europe, the Middle East and Africa (EMEA); and Japan and Asia-Pacific (JAPAC) regions. These findings may not be representative of the entire base of CSP customers.
Analysis of the findings points to a general trend of weak security best practice globally. For instance, researchers found that 73% and 71% of global organizations using Azure Storage containers and AWS S3 buckets, respectively, are not enabling logging functionality. 63% of global organizations using AWS are not tracking changes to their S3 buckets and only 33% of global organizations are enabling encryption within their S3 buckets. This lays the foundation for an organization that is unable to monitor the access and manipulation of data within S3 buckets and cannot guarantee the confidentiality of data within those same S3 buckets to unauthorized users.
Logging, Versioning and Tracing
Unit 42 researchers have expounded at length on cloud environments that do not have logging enabled for storage resources. Here, researchers isolate key metrics within each CSP and region that highlight this ongoing security concern.
| AWS Logging, Versioning and Tracing Violations | Americas | EMEA | JAPAC | Global Average |
| AWS S3 buckets with logging not enabled | 70% | 77% | 74% | 71% |
| AWS S3 Object Versioning is disabled | 62% | 70% | 68% | 63% |
| AWS Lambda functions with tracing not enabled | 53% | 56% | 62% | 54% |
| Azure Logging Violations | Americas | EMEA | JAPAC | Global Average |
| Azure Blob Storage with logging not enabled | 74% | 74% | 67% | 73% |
While some regions performed better than others, Unit 42 researchers feel it is important to point out that no region has reached what should be considered the benchmark for acceptable logging performance. The Center for Internet Security (CIS) has established benchmarks for each cloud service provider as well as for individual applications, which address the requirements for providing logging, version control and serverless tracing functionality.
- Organizations in EMEA struggled the most in terms of failing to enable logging (77%) and versioning (70%) within AWS S3 buckets. JAPAC organizations were close behind at 74% and 68%, respectively. By failing to enable logging within storage resources like S3 buckets, these organizations would be unable to identify authorized, let alone unauthorized, access to these resources.
- Organizations had similar struggles with Azure Blob Storage logging. Organizations in EMEA and the Americas did not fare well implementing best practices for Azure Blob Storage – 74% of both regions’ organizations are not enabling storage account logging. JAPAC performed slightly better with only 67% of organizations not enabling logging for Azure Blob Storage.
- 63% of global organizations are not tracking any changes to the data within AWS S3 buckets. This is what the industry calls versioning. As such, these organizations would be unable to prove the integrity of data stored within these resources. A worst-case scenario for not enabling logging and versioning would be if a malicious actor entered the storage resource, located production source code and infected that code with malicious remote access trojan (RAT) code. This would manifest in any future usage of the source code. The malicious actor could successfully gain access to any production system which uses the code, either in-house or within a client environment, thus resulting in a successful supply-chain attack. Additionally, with the proper enablement of logging, it is highly likely this scenario could have been detected and avoided.
- 62% of JAPAC organizations did not enable tracing functionality for AWS Lambda serverless functions. Tracing is the process of monitoring serverless function operations. With tracing disabled, if these serverless functions became compromised, security teams would be unable to determine what actions were taken following the compromise, or what additional operations the functions performed.
Encryption
Cloud platforms offer encryption features for both virtual machine (VM) instances and storage services. While all CSPs provide encryption functionality for their storage resources, it is important to note that both Google Cloud and Azure enable encryption by default for storage resources. AWS requires users to enable and configure encryption for each of the storage resources deployed.
| Encryption Violations | Americas | EMEA | JAPAC | Global Average |
| AWS S3 buckets do not have server side encryption | 66% | 73% | 72% | 67% |
| AWS Elastic Block Store (EBS) volumes are not encrypted | 63% | 67% | 74% | 65% |
EMEA organizations had the highest percentage of unencrypted S3 buckets at 73%; JAPAC and the Americas had 72% and 66% respectively.
For AWS EBS instances, JAPAC organizations had the highest percentage of encryption violations at 74%, followed by 67% for EMEA and the Americas at 63%.
Encryption allows organizations to ensure the confidentiality of their data by preventing unauthorized users from viewing highly sensitive internal data. Encryption may have helped prevent the exposure of 3.1 million medical patient records as well as the 5.5 million files recently leaked from cybersecurity firms, universities and insurance companies.
In addition to the default encryption options available through CSPs, Unit 42 researchers highly recommend that organizations consider using their own private encryption keys for workloads with elevated data security requirements.
Exposed Systems and Services
Access to cloud environments is critical to digital transformation. As such, security controls need to be put into place to ensure that only essential network connectivity pathways are exposed, while unnecessary services or systems are unavailable to the internet at large. Unit 42 researchers have been tracking the exposure of SSH (port 22) and RDP (port 3389) in recent CTRs.
| Exposed Systems or Services Violations | Americas | EMEA | JAPAC | Global Average |
| AWS Security Groups allow internet traffic to SSH port (22) | 54% | 57% | 52% | 55% |
| Azure Network Security Group (NSG) allows internet traffic to SSH port (22) | 49% | 55% | 28% | 48% |
| Google Cloud firewall rule allows internet traffic to SSH port (22) | 39% | 52% | 45% | 41% |
| Exposed Systems and Services Violations | Americas | EMEA | JAPAC | Global Average |
| AWS Security Groups allow traffic from internet to RDP port (3389) | 36% | 36% | 32% | 36% |
| Azure Network Security Group (NSG) allows traffic from internet to RDP port (3389) | 46% | 46% | 42% | 45% |
| Google Cloud firewall rule allows internet traffic to RDP port (3389) | 32% | 38% | 35% | 34% |
The current trend of exposure for SSH and RDP is going down globally, meaning that more organizations are blocking or at least limiting their exposure to the internet than in previous CTRs. However, analysis shows that EMEA organizations expose SSH and RDP services more frequently than either Americas or JAPAC organizations. In O’Reilly’s Evolving Data Infrastructure report in 2018, the survey found that only 24% of European organizations felt they were “sophisticated cloud users.” The lack of skills and talent among the workforce was pointed to as the leading contributor for this sentiment:
- 57% of EMEA organizations using AWS are exposing SSH, and 55% and 52% of EMEA organizations using Azure and Google Cloud respectively are doing the same.
- 46% of EMEA organizations using Azure environments are exposing RDP, and 38% and 36% of EMEA organizations using Google Cloud and AWS respectively are doing the same.
| Network Traffic Restrictions | Americas | EMEA | JAPAC | Global Average |
| Unrestricted inbound network traffic into cloud environments | 38% | 39% | 37% | 38% |
Additionally, Unit 42 researchers found that 39% of EMEA organizations allow unrestricted inbound network traffic into their cloud environments, while the Americas and JAPAC were found to allow this traffic in 38% and 37% of organizations respectively. Without limiting the type of traffic allowed into an environment, the security landscape of an organization is needlessly expanded, allowing for the exposure of services and systems.
SSH is often targeted by attackers when configured to use password authentication. This can provide a low barrier to entry, as it is the same tool legitimate administrators use to control systems. In order to safeguard SSH connections, DevOps teams should use public key authentication functionality (RSA, ECDSA or Ed25519 key pairs) for all SSH-enabled systems. Network-based protections should also be utilized to block known SSH attack techniques.
RDP operates over port 3389 and, similar to SSH, is used to remotely administer Windows environments. Unit 42 researchers strongly recommend against directly exposing RDP to the public internet. Many alternatives now exist, such as Azure Bastion, which is a platform as a service (PaaS) offered by Microsoft. It provides connectivity to Azure VMs without directly exposing the public IP address of VMs.
Trend Data from Past Reports
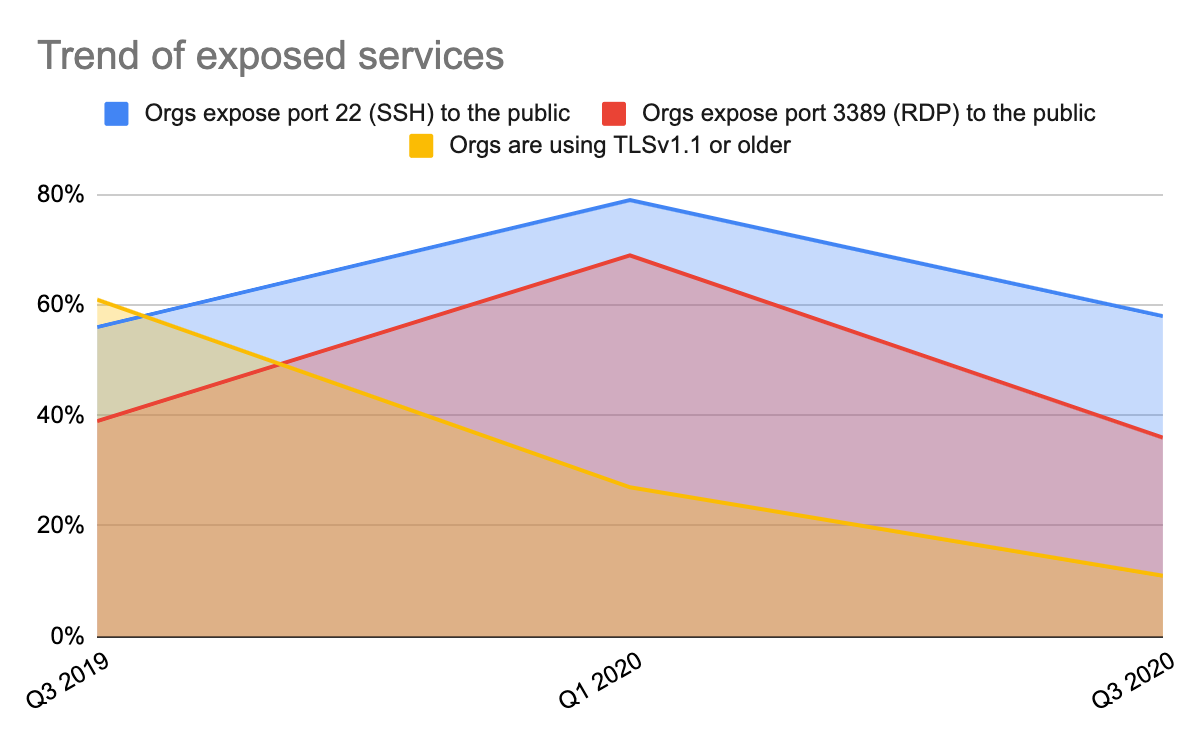
In the Unit 42 Cloud Threat Report: Spring 2020, Unit 42 researchers began noting trends in the percentage of organizations that exposed SSH and RDP services, and those that were still using TLS v1.1 for their network traffic requirements. The graph below demonstrates that each of these areas saw a marked decrease in occurrences since February 2020. While TLS v1.1 has seen a consistent decline in usage since we started tracking this metric, the exposure of SSH and RDP services appears to be overall flat, with just under 60% of organizations exposing SSH and just under 39% exposing RDP.
Conclusion
This data derived from logging, versioning and tracing operations gives security professionals the information they need to monitor and defend their networks from cyberattacks. CIS addressed logging by stating, “Without protected and complete logging records, an attack may go unnoticed indefinitely and the particular damages done may be irreversible.”
In order to minimize the attackable surface area of a cloud environment, organizations should take several actions:
- Ensure logging operations follow CIS guidelines.
- Require data processing or data storage resource encryption mechanisms.
- Limit the number of systems and services exposed to the internet.
Following these recommendations will result in a more manageable and defensible cloud environment.
Prisma Cloud provides a comprehensive solution to protect cloud environments from deploying misconfigured, vulnerable or overly exposed cloud resources. By drawing on a robust suite of security protection mechanisms and intelligence, Palo Alto Networks provides organizations that operate in the cloud a unique lens into their environments.
Download the Unit 42 Cloud Threat Report, 2H 2020 for more research and best practices to implement in your organization.












 Get updates from Unit 42
Get updates from Unit 42