Executive Summary
For Microsoft’s Patch Tuesday for February 2021, the company released patches for 56 disclosed vulnerabilities, which include:
- CVE-2021-24086 and CVE-2021-24094: Two denial-of-service (DoS) vulnerabilities in the Windows IPv6 stack.
- CVE-2021-24074: Remote code execution (RCE) vulnerability in the Windows IPv4 stack.
CVE-2021-24086 was given the Common Vulnerability Scoring System (CVSS) score of 7.5/6.5 and an "Important" security rating from Microsoft.
CVE-2021-24094 and CVE-2021-24074 were given the CVSS score of 9.8/8.4 and a "Critical" security rating from Microsoft.
CVE-2021-24086 and CVE-2021-24094 Overview
An attacker could send a number of crafted IPv6 packets (multiple headers, invalid header, multiple fragment headers, etc.), which would cause a DoS error. Palo Alto Networks Next-Generation Firewall customers with PAN-OS are able to block such malicious packets to mitigate the attacks.
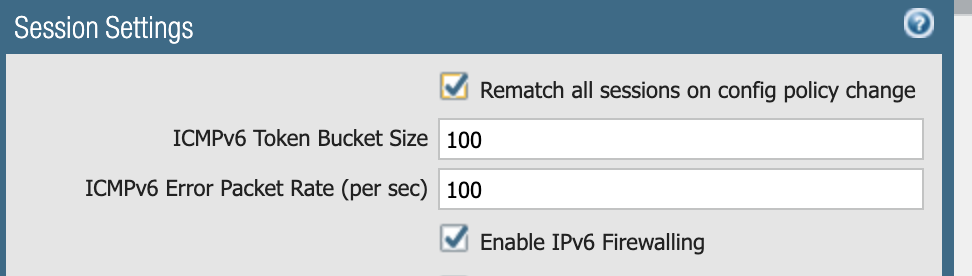
Palo Alto Networks Next-Generation Firewall customers with IPv6 Firewalling enabled already receive protections for these two vulnerabilities. IPv6 firewalling can be enabled in the user interface (UI) under Device > Setup > Session: Check the “Enable IPv6 Firewalling” checkbox and Commit the Firewall. More details about IPv6 Firewalling can be found in the Knowledge Base article, “How to Enable and Disable IPv6 Firewalling.”
Palo Alto Networks Next-Generation Firewall customers can check the details for the packet drops during a DoS attack using the command show counter global filter delta yes | match flow_parse_ip6, which allows viewing IPv6 packets dropped since the last time the command was issued.
For example, the following is the output of the command after running a DoS attack with crafted IPv6 packets against the firewall, which shows 90 IPv6 packets dropped due to truncated packets, six packets dropped due to invalid header position and one packet dropped due to multiple fragment headers present in the IPv6 packet.
admin@PA-3020> show counter global filter delta yes | match flow_parse_ip6
flow_parse_ip6_truncated 90 4 drop flow parse Packets dropped: IPv6 packet truncated
flow_parse_ip6_invalid_routing_ext_hdr 6 0 drop flow parse Packets dropped: invalid routing header position in IPv6 packet
flow_parse_ip6_frag_nested 1 0 drop flow parse Packets dropped: multiple fragment header in IPv6 packet
CVE-2021-24074 Overview
An attacker can leverage this vulnerability by sending maliciously crafted IPv4 packets to a victim, potentially causing a RCE on the system.
This vulnerability occurs due to confusing IPv4 options fields between two fragments. The scenario pointed out by Microsoft shows two IPv4 fragments, the first of which has the Security Options (Type 130) field, followed by a second fragment with either the Loose Source and Record Route (LSRR) option (Type 131) or the Strict Source and Record Route (SSRR) option (Type 137). The fragment offsets, confusing the options and the header data together, cause an out-of-bound read and write during reassembly of the IP fragments, which introduces the potential for RCE on a Windows machine.
Next-Generation Firewall Mitigations for CVE-2021-24074
Palo Alto Networks Next-Generation Firewall customers running PAN-OS 8.1 or higher can configure their Network Zone Protection Profile settings to protect themselves from attacks related to CVE-2021-24074 by enabling IP Drop for Malformed, Strict and Loose Source Routing IP Options.
Note that as a best practice for IP protocol, Palo Alto Networks recommends enabling packet drop for dropping packets with Malformed, Strict and Loose Source Routing options because allowing these options allows adversaries to bypass security policy rules that use the destination IP address as the matching criteria. More details of these options can be found in the TechDocs article, “Packet-Based Attack Protection.”
The “Configure Packet Based Attack Protection” page contains the steps to configure the Zone Protection Profile to drop the specific packets with IP options.
For configuring Zone Protection to drop IP packets with these options:
Step 1: Create a Zone Protection profile and configure Packet-Based Attack Protection settings.
- Select Network > Network Profiles > Zone Protection and Add a new profile.
- Enter a Name for the profile and an optional Description.
- Select Packet-Based Attack Protection.
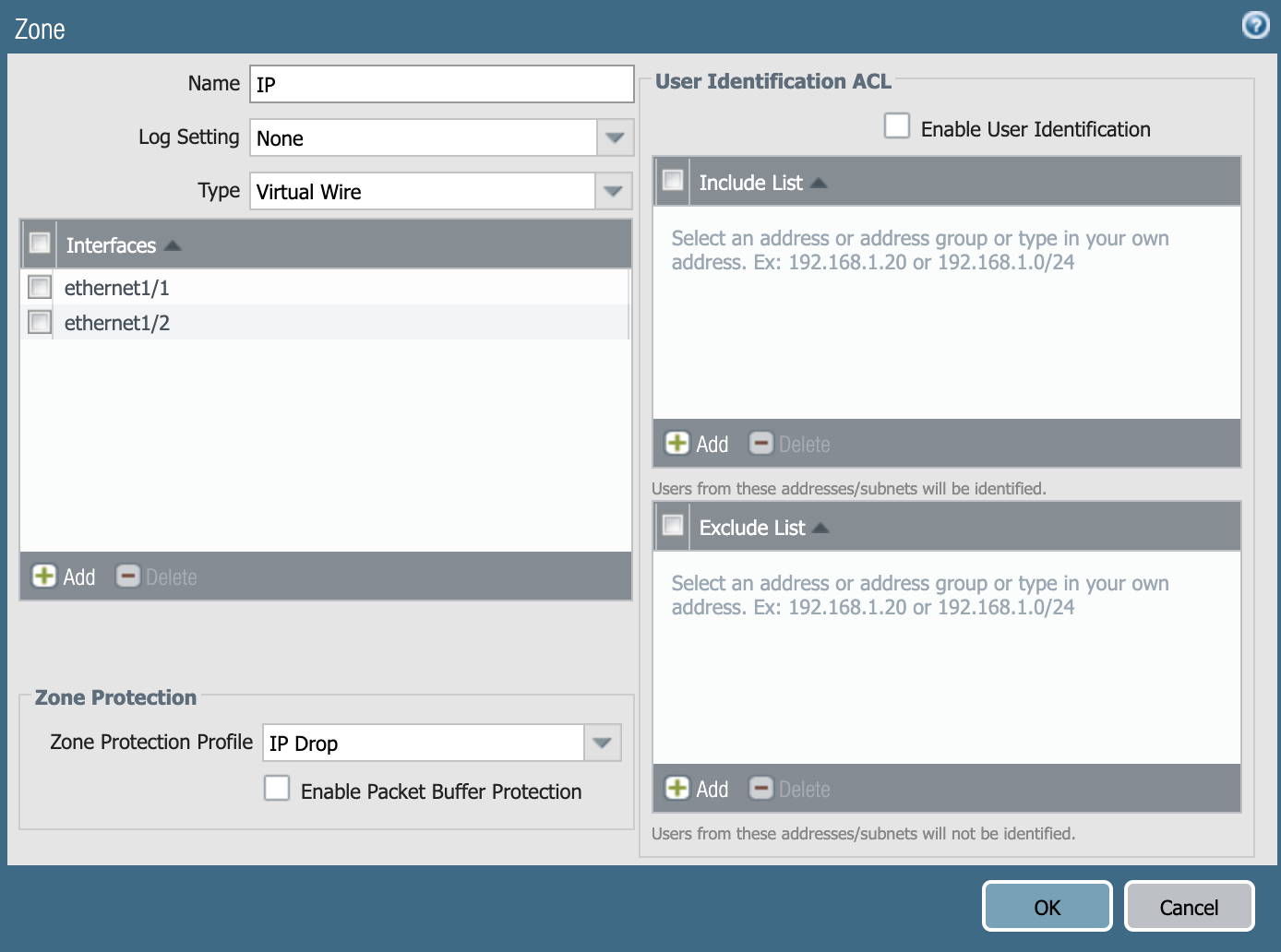
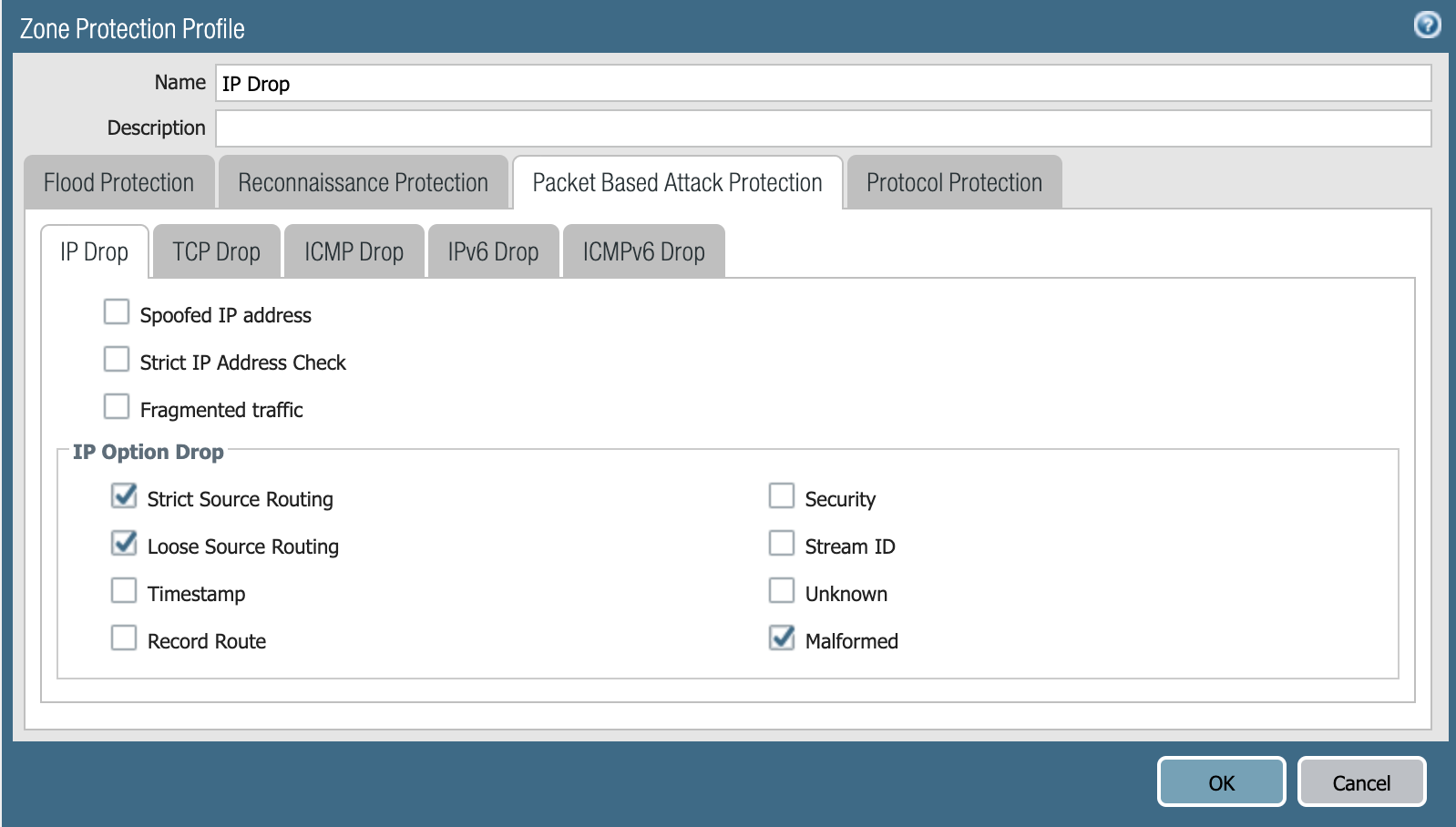
- On the IP Drop tab, select the Packet-Based Attack Protection settings tab and select the Malformed, Strict Source Routing and Loose Source Routing check boxes under IP Option Drop.
- Click OK.
![To mitigate CVE-2021-24074 with the Next-Generation Firewall, you can configure your Zone Protection Profile as shown in this screenshot. Note the selctions of IP Option Drops "Strict Source Routing," "Loose Source Routing" and "Malformed."]()
Figure 2. Configuring Zone Protection Profile with IP Drop options.
Step 2: Apply the Zone Protection profile to a security zone that is assigned to interfaces you want to protect.
- Select Network > Zones and select the zone where you want to assign the Zone Protection profile.
- Add the Interfaces belonging to the zone.
- For Zone Protection Profile, select the profile you just created.
- Click OK.
Step 3: Commit your changes.
Step 4: (PAN-OS 8.1.2 or higher) Enable the firewall to generate threat logs for the attack, and also generate threat logs for the types of packets listed above if you enable the corresponding packet-based attack protection (in Step 1). For example, if you enable packet-based attack protection for Loose Source Routing, using the following command line interface (CLI) causes the firewall to generate a threat log when the firewall receives and drops a packet with an LSRR option. Customers can leverage this option for troubleshooting purposes.
- Access the CLI.
- Use the operational CLI command set system setting additional-threat-log on. Default is off.
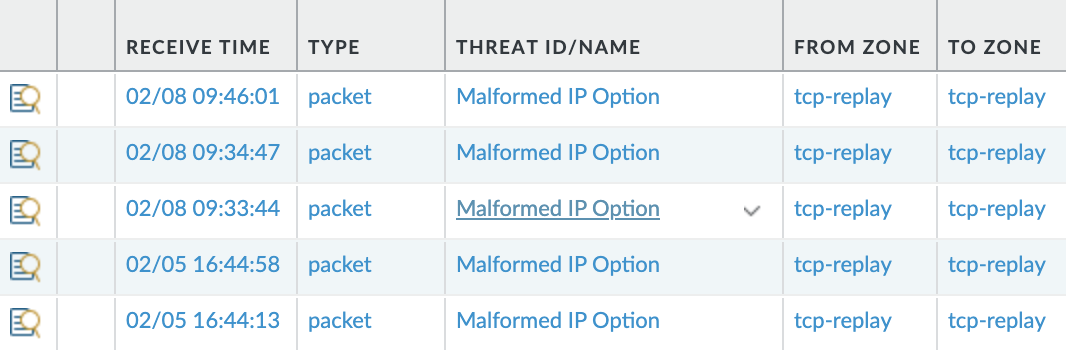
Additionally, the threat logs can be seen in the UI as shown in Figure 4.
As an alternative, Palo Alto Networks Next-Generation Firewall customers can also check the details for the IPv4 packet drops due to Zone Protection using the flow_dos_pf_badoption, flow_dos_pf_strictsource and flow_dos_pf_strictsource flow counters.
For example, the command show counter global filter delta yes | match flow_dos_pf_badoption allows viewing IPv4 packets dropped since the last time the command was issued.
admin@PA-5250> show counter global filter delta yes | match flow_dos_pf_badoption
flow_dos_pf_badoption 1 0 drop flow dos Packets dropped: Zone protection option 'discard-malformed-option'
For CVE-2021-24074, malformed packets which cause bad loose/strict source options to the subsequent packet get dropped when the “Malformed” Zone Protection IP Drop Option is enabled. The subsequent IP packet with bad loose/strict source does not get transmitted to the firewall due to internal firewall packet filtering. Since IPv4 Source routing is considered insecure, other IPv4 packets with source routing would get dropped when the “Loose Source Routing” and “Strict Source Routing” Zone Protection IP Drop Options are enabled.
Cortex XDR Mitigations for CVE-2021-24074, CVE-2021-24086 and CVE-2021-24094
If you’re a Palo Alto Networks Cortex XDR Agent customer version 7.1 or higher, you can leverage your agents starting Feb. 10 to modify system settings to protect unpatched endpoints from these vulnerabilities until a Windows update is installed.
The workaround is managed through the Endpoint Exploit Security Profile and requires the latest content update. You can edit any of your existing profiles or create a new profile to include the workaround as needed.
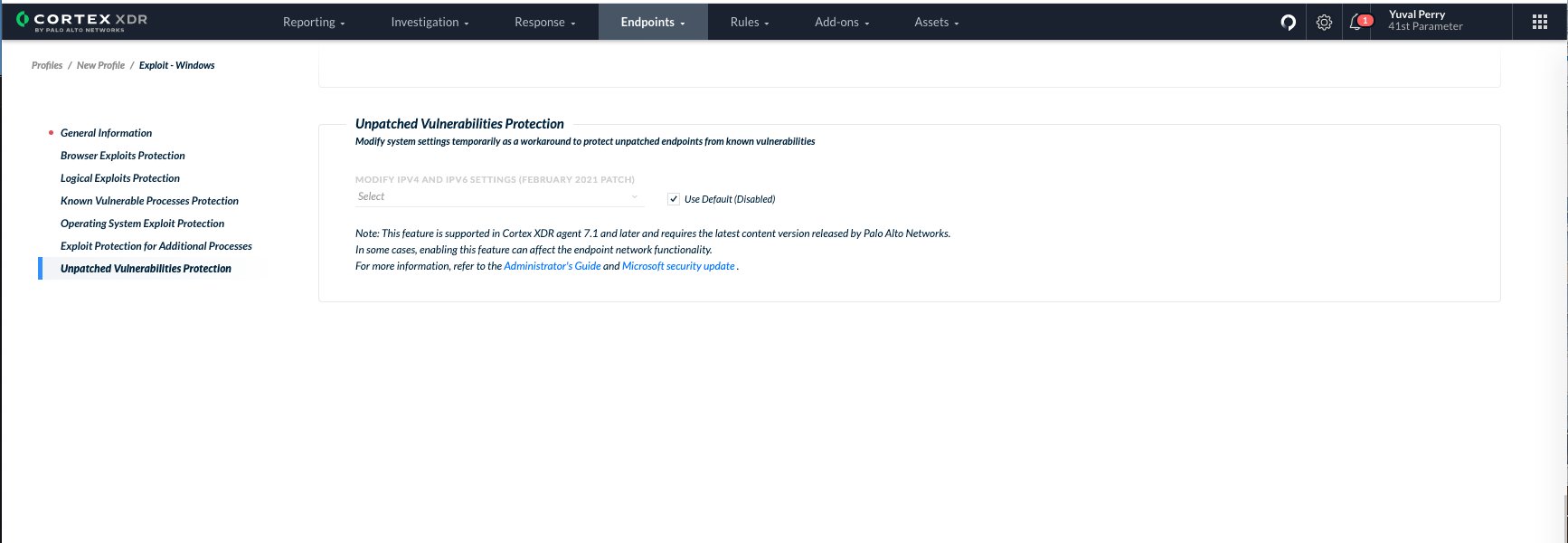
Under the “Unpatched Vulnerabilities Protection” section, define the workaround setting for CVE-2021-24074, CVE-2021-24086 and CVE-2021-24094 by selecting one of the options below:
- Do not modify system settings (default): Do not modify the IPv4 and IPv6 settings currently set on the endpoint, whether the current values are your original values or values that were modified as part of this workaround.
- Modify system settings until the endpoint is patched: The Cortex XDR agent runs the following commands on your endpoints to temporarily modify the IPv4 and IPv6 settings until the endpoint is patched. After the endpoint is patched, all modified Windows system settings are automatically reverted to their values before modification. Palo Alto Networks strongly recommends that you review these commands before applying this workaround in your network to ensure your business-critical components are not affected or harmed.
-
- To disable IPv6 fragmentation on the endpoint: netsh int ipv6 set global reassemblylimit=0
- To disable loose source routing for IPv4 : netsh int ipv4 set global sourceroutingbehavior=drop
- Revert system settings to your previous settings: Revert all Windows system settings to their values before modification as part of this workaround, regardless of whether the endpoint was patched or not.
BEST PRACTICE NOTE: For all Windows endpoints, Palo Alto Networks strongly recommends that you install the latest Windows Update that patches these vulnerabilities.
For more details, refer to the Cortex XDR Prevent Administrator’s guide.
Conclusion
As a member of the Microsoft Active Protections Program (MAPP) program, Palo Alto Networks received early details of the vulnerability, providing greater understanding of the threat, which helps us implement strong product coverage. As always, we recommend keeping your Microsoft products up to date with the latest patches to mitigate this vulnerability.
Palo Alto Networks will update this Threat Brief with new information and recommendations as they become available.
Additional Resources
Windows TCP/IP Remote Code Execution Vulnerability, CVE-2021-24074
Windows TCP/IP Denial of Service Vulnerability, CVE-2021-24086
Windows TCP/IP Remote Code Execution Vulnerability, CVE-2021-24094
February 2021 Security Updates from Microsoft
Packet-Based Attack Protection
Configure Packet Based Attack Protection












 Get updates from Unit 42
Get updates from Unit 42