Executive Summary
Researchers with Palo Alto Networks Unit 42 investigated the tunneling software X-VPN, which uses various evasion techniques to bypass security and policy enforcement mechanisms. X-VPN is a type of Virtual Private Network (VPN) that can be used to bypass internet censorship and traffic policy enforcement points, which poses a great risk to network operators as well as VPN users.
X-VPN is currently one of the most evasive VPN clients, mimicking various popular protocols and services to bypass security policies. As a consequence, protection systems are not able to inspect the data packets, which can allow malicious traffic to enter the network or sensitive information to leave network.
Risks of Evasive VPN Connections
Using VPN clients such as X-VPN will put the user of such software as well as the network operator at risk. Users have to consider the following risks when they decide to use a VPN client:
- Can the VPN provider be trusted? – When using a VPN, all data from a client is sent to a third party who is able to perform various analysis and logging on the data.
- Jurisdiction of host-country – Depending where the VPN provider is located, the host country might require the VPN provider to share certain user data with the government. During our analysis of X-VPN we found that many exit nodes are located in different countries, which are often automatically selected by the VPN client.
- Restricting traffic – Since a VPN provider has complete control over the data from its users, it can throttle or even block connections to various services or favor certain content providers over others.
- Risks of malware and spyware – VPN clients often access third-party sources and can infect the host with malware or spyware programs. Especially if VPNs use custom encryption, security monitors won’t be able to identify malicious payloads of incoming traffic.
- Using the client as an exit node – VPN clients may allow its users to connect through an installed client of another end-user. In such a case the end-user who is used as an exit node may be held responsible for any illegal activities other VPN users perform.
Considering the risks associated with VPNs, it is critical that network operators are able to monitor and control the usage of VPNs in their networks. The following section discusses evasion techniques found during our deep analysis of X-VPN.
X-VPN Evasion Techniques
X-VPN’s evasion techniques are based on using custom encryption of TCP and UDP payloads as well as mimicking other application layer protocols such as HTTP, SSL, FTP, NTP, and SMTP. Based on our research, X-VPN uses an estimated 10,000 server instances hosted by public cloud providers and replaces 300-500 server instances with new public IP addresses every day.
To hide the actual payload of data packets, X-VPN mimics connections to popular services such as www.google.com or www.bing.com:
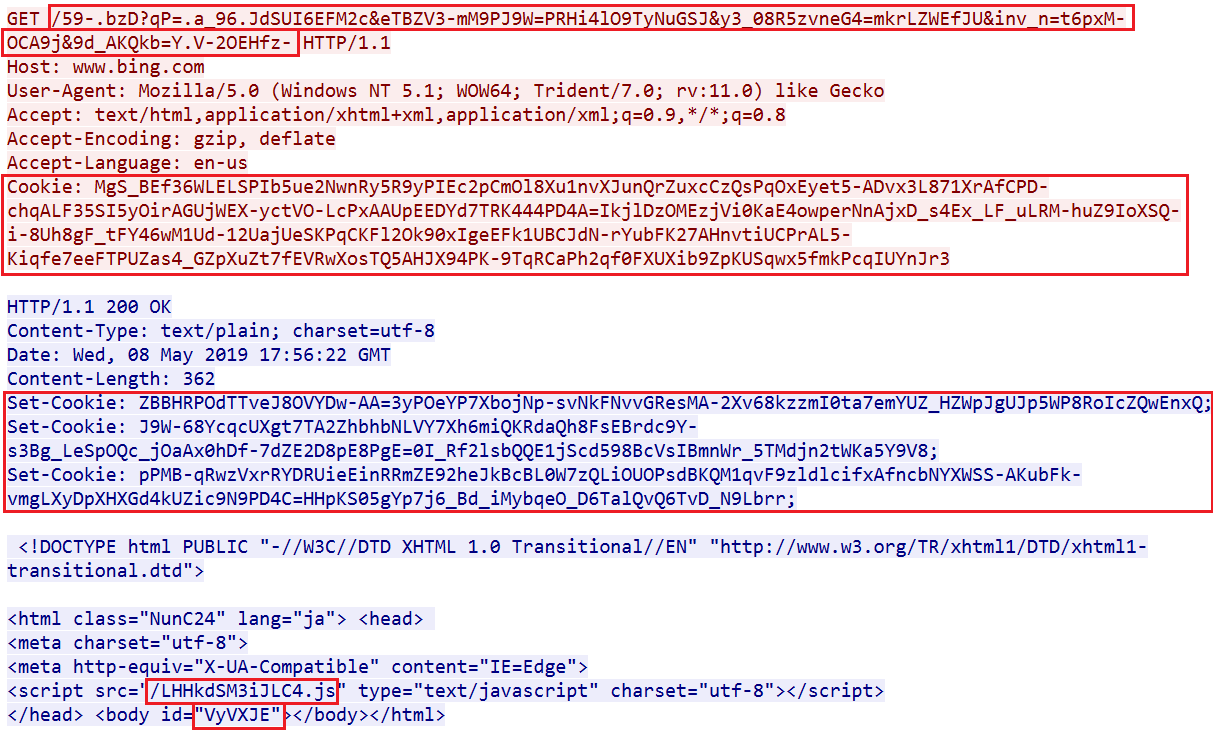 Figure 1. X-VPN traffic mimicking web browsing to www.bing.com
Figure 1. X-VPN traffic mimicking web browsing to www.bing.com
As shown in Figure 1, X-VPN mimics HTTP traffic which appears to be web browsing traffic to Bing. The highlighted fields are custom encrypted and either used as command and control traffic or to transmit data between the client software and one of X-VPN’s server instances.
In comparison, Figure 2 shows the HTTP header of real web browsing traffic to www.bing.com
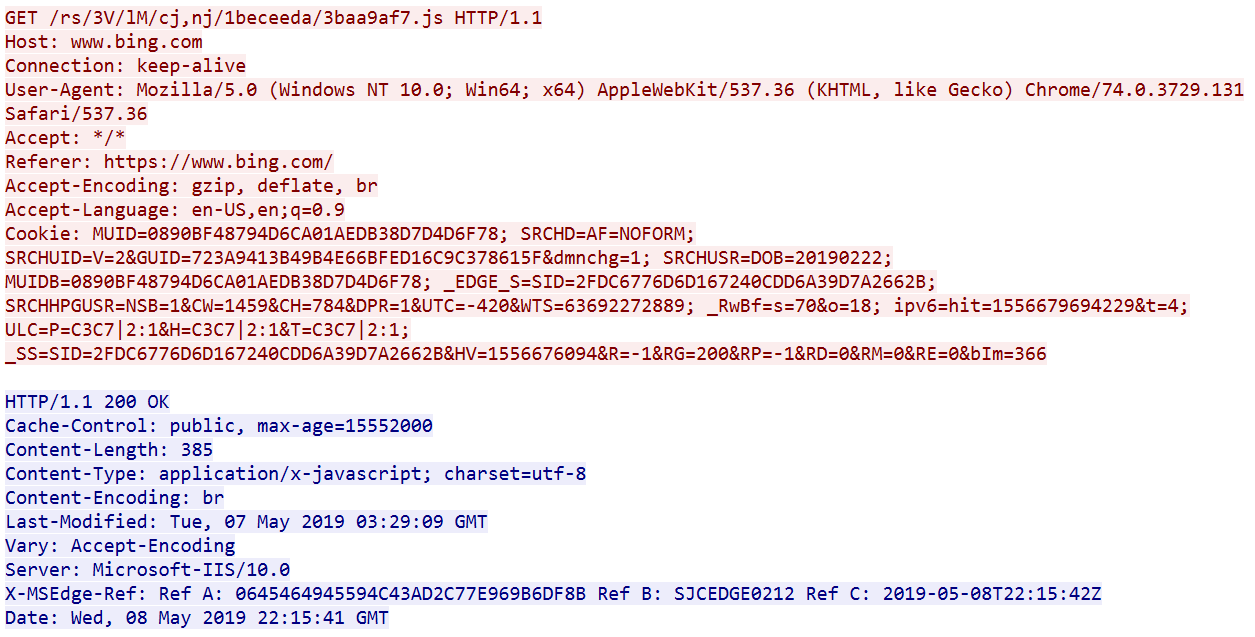 Figure 2. Real traffic to www.bing.com
Figure 2. Real traffic to www.bing.com
The same techniques can be observed with SSL traffic, where X-VPN mimics the SSL handshake, e.g. to google.com, as we show in Figure 3.
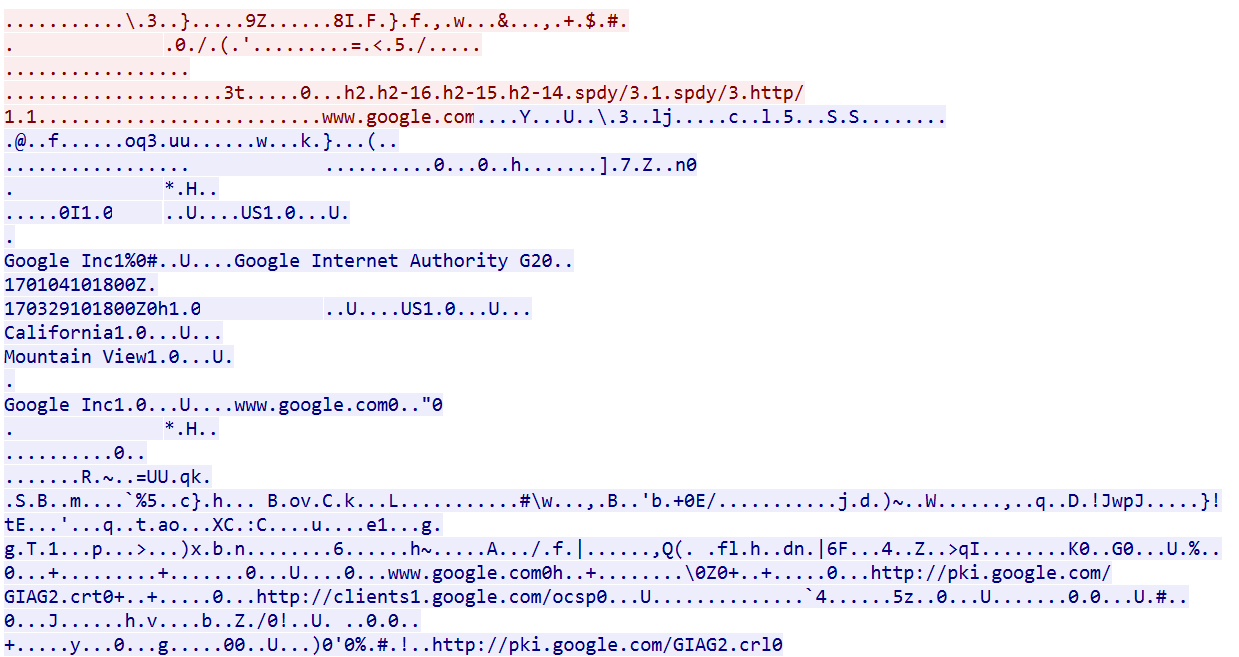 Figure 3. X-VPN mimicking SSL handshake to www.google.com
Figure 3. X-VPN mimicking SSL handshake to www.google.com
Besides the usage of popular services as domain names, we also observed that X-VPN uses generated domains such as 8v9m.com.
In addition to using deceptive HTTP and SSL packets to tunnel data through policy enforcement systems, X-VPN applies the same principle to FTP, SMTP and NTP traffic and hides custom encoded data within fields embedded in packets that appear as benign protocols.
In Figure 4, such an example is shown where the structure of a Simple Mail Transfer Protocol (SMTP) packet which appears to communicate with icloud.com is used by X-VPN to transmit data. The ‘FROM’ and ‘TO’ mail addresses in the SMTP packet stream appear as custom encrypted values. This traffic is assumed to be used by X-VPN for command and control communication.
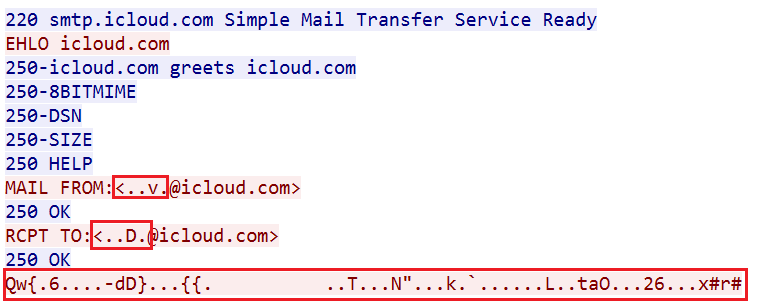 Figure 4. X-VPN mimicking SMTP traffic
Figure 4. X-VPN mimicking SMTP traffic
A similar method is used by X-VPN to utilize FTP (File Transfer Protocol) traffic where the username and password are custom encrypted to communicate information between client and server in an evasive way as we show in Figure 5.
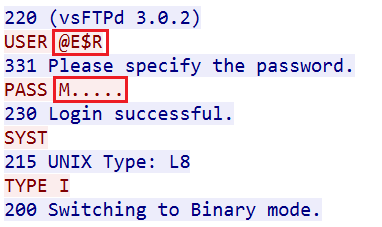 Figure 5. X-VPN mimicking FTP traffic
Figure 5. X-VPN mimicking FTP traffic
Conclusion and Mitigation
Palo Alto Networks can help customers and enterprises by blocking X-VPN and other proxies by a combination of different best practice recommendations. A detailed description on how to configure Palo Alto Networks Firewall to block X-VPN can be found here: Configure Palo Alto Networks Firewall To Block X-VPN












 Get updates from Unit 42
Get updates from Unit 42