Executive Summary
Unit 42 researchers discovered a campaign distributing thousands of fraudulent cryptocurrency investment platforms via websites and mobile applications. This article describes how threat actors systematically create, promote and potentially profit from these scams, highlighting the techniques used to deceive victims and the potential scale of the operation.
The campaign impersonates well-known brands, cryptocurrency platforms and popular organizations to lure victims. The consistent design of the websites and mobile apps suggests the use of a standardized toolkit for developing these platforms at scale.
There are several additional indicators attributing these activities to a single threat actor. This is underscored by the consistent registration of domains primarily in Singapore, predominantly using registrars with lenient policies and repeated patterns of fake registrant names. These domains also employ free HTTPS certificates and domain fronting via a popular public cloud service to obscure their true locations.
This campaign primarily targets users in East African and Asian countries, with scammers hosting large Telegram channels and groups to engage with victims. The scammers lure users with promises of unrealistically high investment returns and operate similar to Ponzi schemes by encouraging users to recruit others through multi-level affiliate programs.
Palo Alto Networks customers are better protected from the threats discussed in this article through our Next-Generation Firewall's Advanced WildFire, Advanced URL Filtering and Advanced DNS Security subscriptions.
| Related Unit 42 Topics | Cryptocurrency, Phishing |
Scam Crypto Investment Platforms
Unit 42 researchers uncovered a campaign responsible for creating a large number of scam crypto investment platforms, distributed via both websites and mobile apps. This article describes how threat actors systematically create, promote and potentially monetize this campaign of investment scams.
Distribution via Websites and Mobile Apps
Each scam crypto investment platform can be accessed through a website and an Android-based mobile application. A link to the mobile application is posted on the platform's website. Notably, these mobile applications are not published on the mobile app store, likely to evade enforcement and takedown operations.
Fraudulent Impersonation
Each scam crypto investment platform uses a popular theme that could be a well-known brand, organization, location or even a trending event. This tactic lures victims into signing up and investing, ultimately leading to fraud.
Our analysis revealed threat actors mimicking a wide range of brands, including:
- Well-known banks
- Retail stores
- Technology companies
- Luxury brands
- E-commerce stores
- Cryptocurrency exchanges
We identified over 50 impersonated themes across these websites. See Figure 1 for examples. The platforms also leverage major sporting events, like the Paris 2024 Olympics, to attract users. A list of website hostnames is available in the Indicators of Compromise (IoC) section at the end of the article.
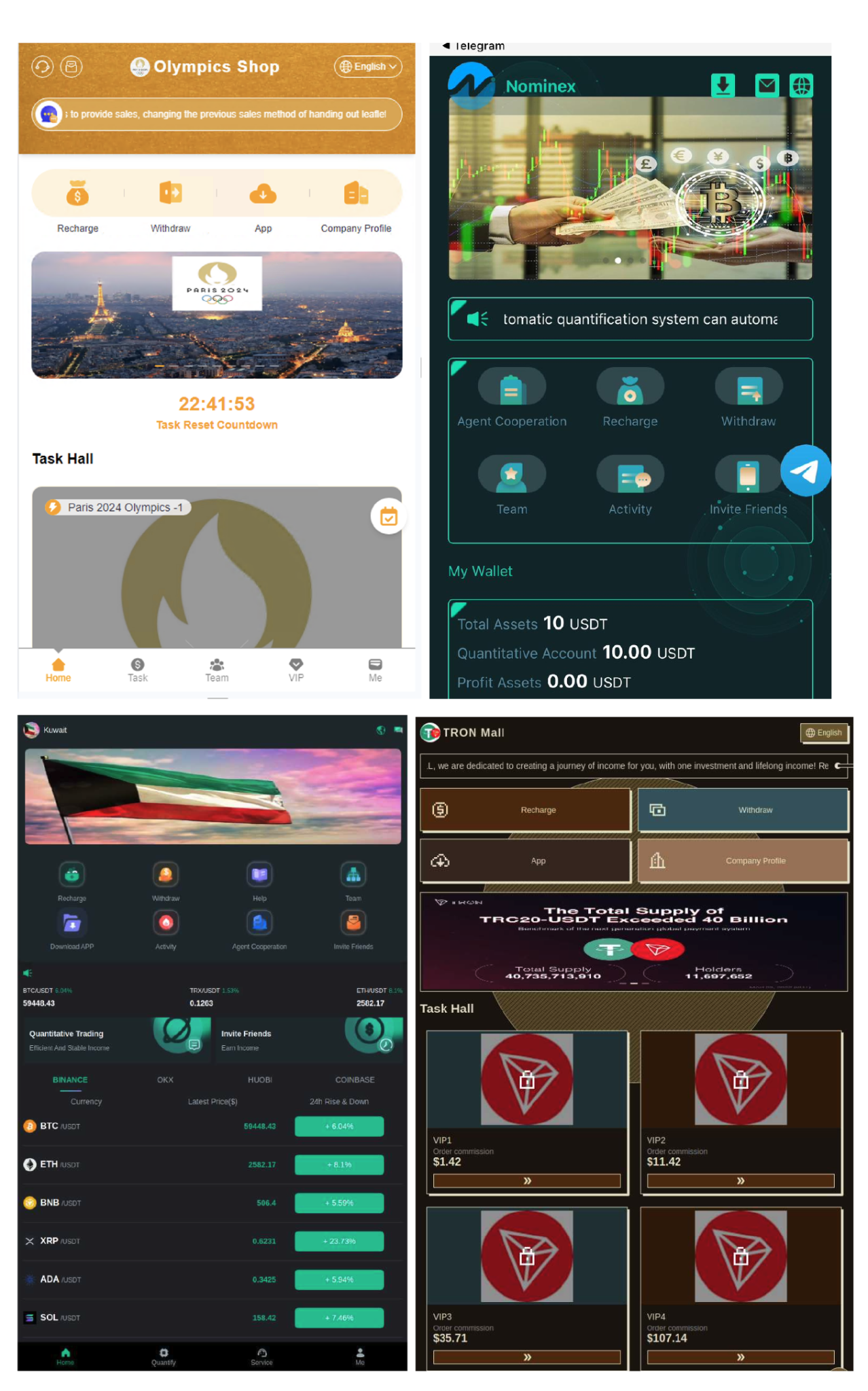
Unrealistic Claims of Returns on Principal Investment
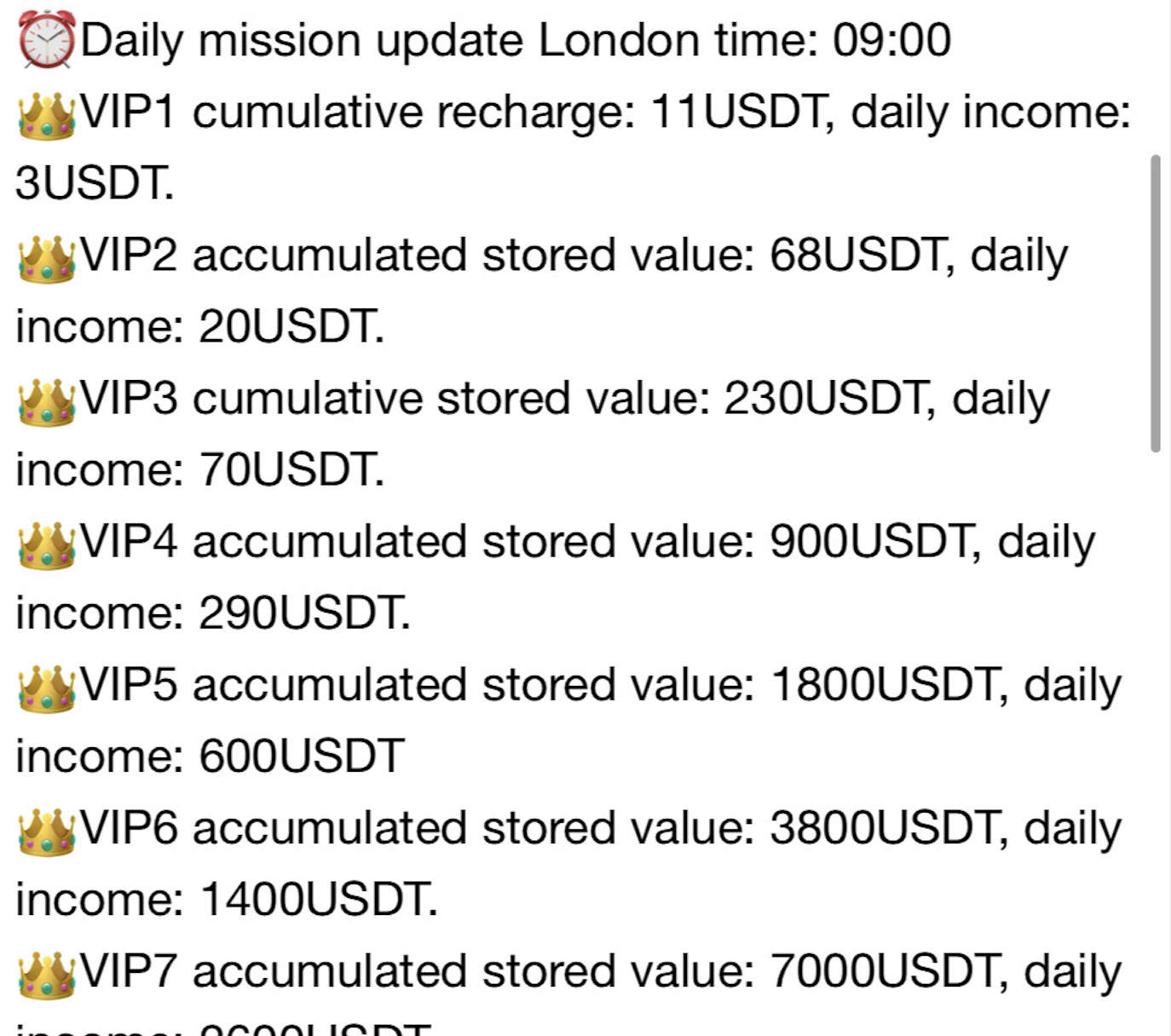
Platforms lure users with promises of unrealistically high returns on principal investments. Figure 2 shows a screenshot from a platform outlining daily returns on investment. For instance, the “VIP1” package claims to yield a daily return of $3 on an $11 principal investment. This represents a daily return on investment (ROI) of 27% that, when compounded, will yield an annual ROI of at least 2,650%. Such figures are unrealistic and should raise immediate red flags.
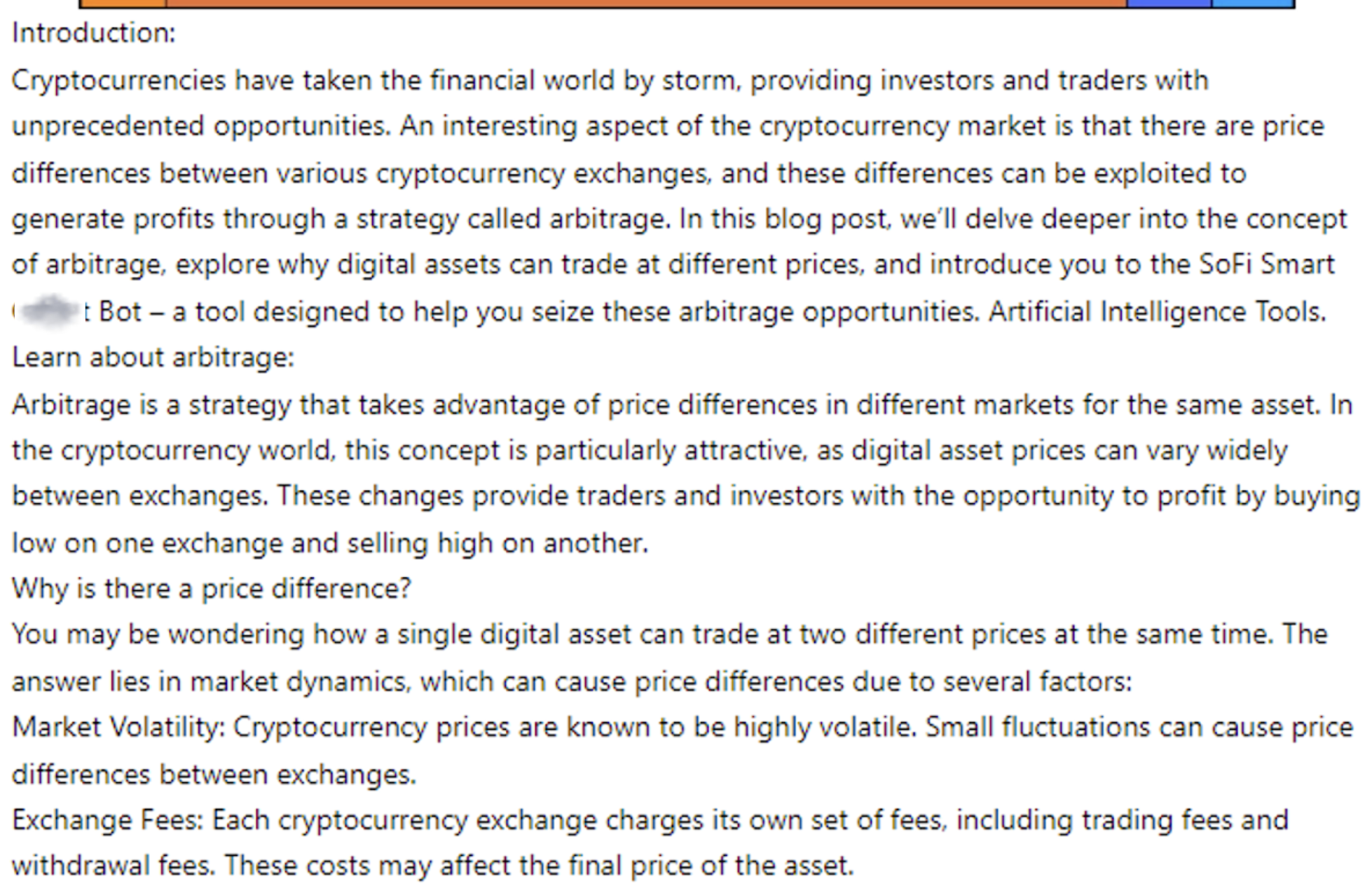
Some platforms fabricate explanations of how they generate profits to make these high-return claims appear legitimate. Figure 3 shows an example of a note claiming the creation of an AI-powered smart bot that leverages arbitrage to make money by trading on different crypto marketplaces.
Signs of a Ponzi Scheme
Each platform employs a multi-level affiliate program where affiliates earn commissions for signing up new members through an invitation link or code. Figure 4 illustrates an example of this multi-level affiliate program.
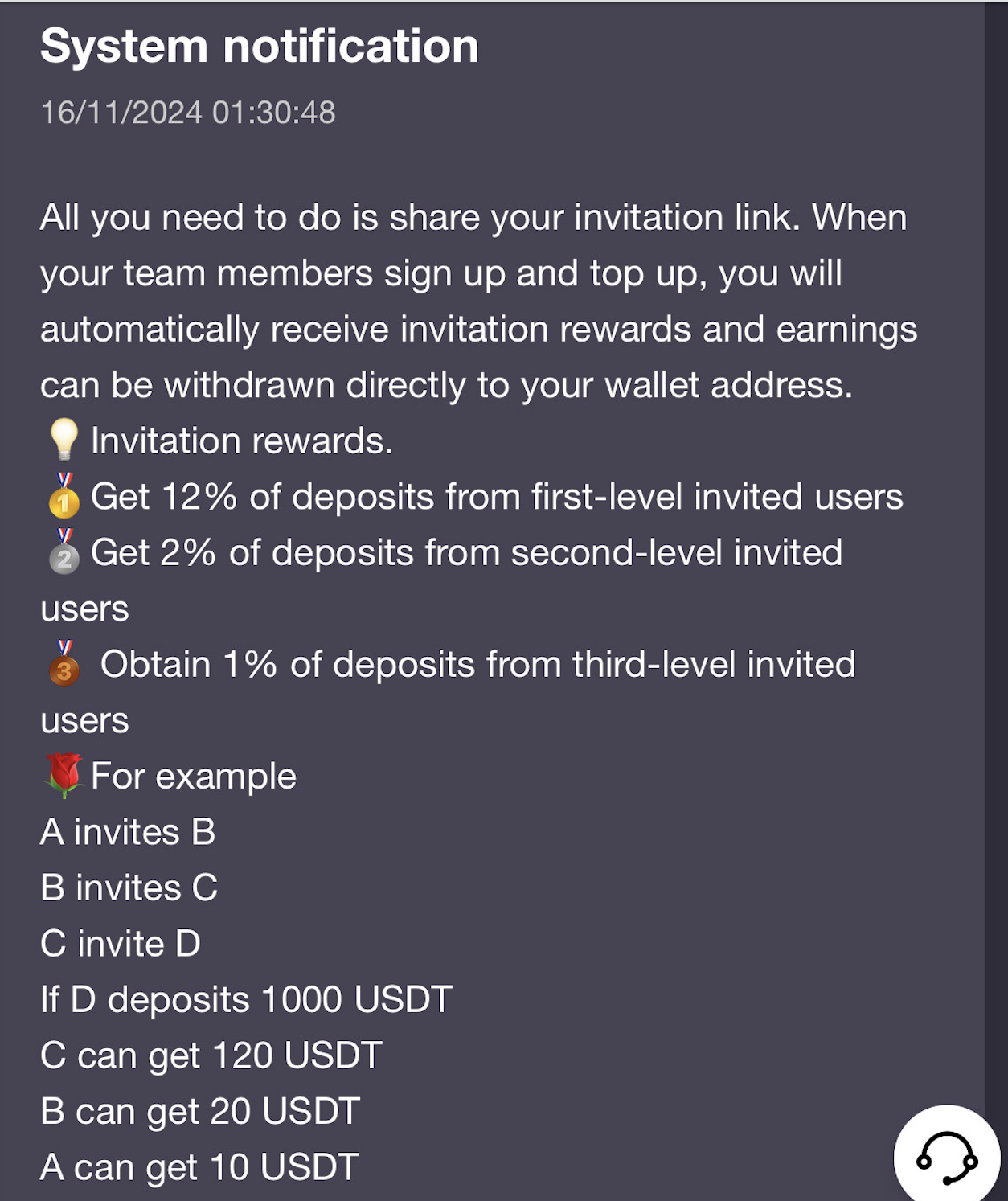
Their commission structure is tiered. It offers the highest commission for first-level recruits, whom the affiliate signs up directly. The commission decreases for subsequent levels, where the recruited members become affiliates and sign up more members.
These characteristics are telltale signs of a pyramid scheme, where members primarily earn money by recruiting others rather than through genuine investments or business activities. We believe that the affiliates leverage social media platforms to promote these schemes, as described next.
Promotions and Distribution Through a Popular Video Sharing Platform
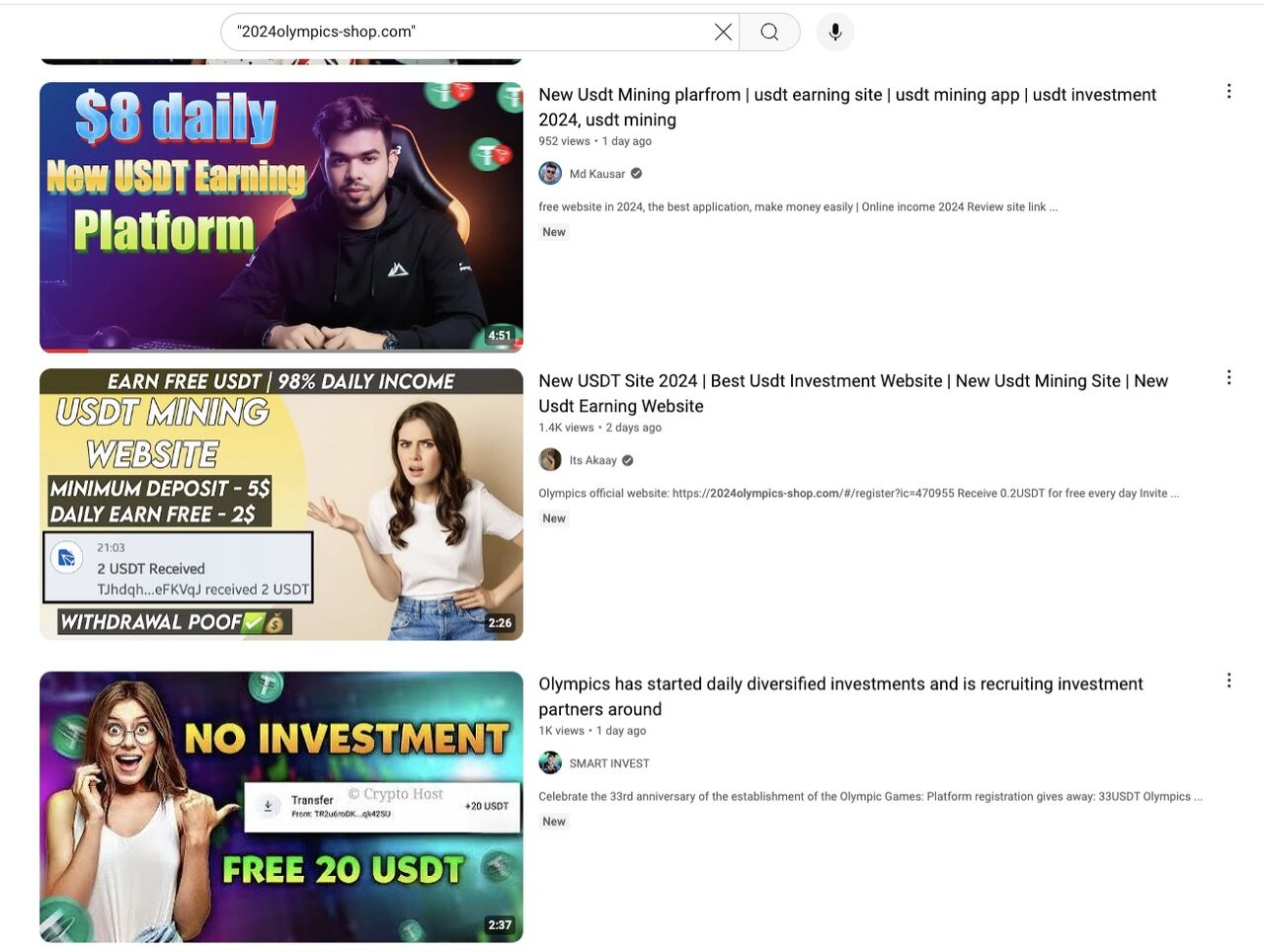
These scam platforms are promoted on popular video sharing platforms. Figure 5 shows examples of videos promoting a platform 2024olympics-shop[.]com. Each video includes an invitation link or an affiliate code, strongly suggesting the vloggers are top-level affiliates earning commissions through recruitment.
Large User Base
Each scam investment platform has a potentially large reach. The popularity of these platforms can be gauged by the membership numbers in their associated Telegram channels, many of which boast tens of thousands of members.
For example, the Telegram channel shown in Figure 6 had over 29,000 members. This channel is associated with a scam crypto investment platform nmxquantify[.]com.

Our telemetry data indicates that these threat actors primarily target internet users in East African and Asian countries. We supported this with a manual review of videos, where most content creators appeared to target users in these regions.
Use of Scam ToolKit
Analysis of multiple websites reveals numerous similarities between these platforms, suggesting the use of a single scam toolkit to generate them at scale. This toolkit likely uses basic inputs, such as brand names and images, to produce both a website and a mobile application.
Common design elements: The websites share similar layouts. They share several design elements in their placement. For example, each website’s homepage typically features a slideshow at the top, an investment opportunities section and a standard set of buttons linking to company profiles, mobile apps, wallet recharges and money withdrawals.
Use of a front-end web design framework: Our analysis revealed structural similarities in the websites’ HTML, specifically the common Document Object Model (DOM) element (data-v-*). A known front-end JavaScript framework, Vue.js (discussed in a Stack Overflow thread) commonly uses this element.
Mobile applications: All reviewed mobile applications are Android-based. These apps integrate the original website via a web view, likely to reduce development overhead for the scam toolkit creators.
The rationale behind distributing mobile apps remains unclear. These apps, however, require sensitive permissions such as android.permission.READ_EXTERNAL_STORAGE and android.permission.CAMERA. The necessity of these permissions for web view apps is questionable, and while attackers could potentially be misusing them, we found no evidence of such misuse.
Location of mobile applications on the website: The mobile applications follow a specific naming convention based on the platform’s website name. For all reviewed platforms, the app’s location follows a specific pattern: api.[name].[tld]/[name].apk.
For example, the application for the platform teslamall66[.]vip is hosted at hxxps[:]//api.teslamall66[.]vip/teslamall66.apk.
These striking similarities in the design of scam crypto websites and their associated mobile apps strongly indicate the use of a toolkit to generate these websites at scale. The next section explores the likelihood of a single threat actor behind these platforms.
Is There a Single Threat Actor Behind This Campaign?
Figure 7 shows increased activity in new domain registrations since June 2024. We estimated the domain registration date based on the first seen passive DNS (historical DNS records), as the WHOIS records for most domains were unavailable at the time of the investigation.
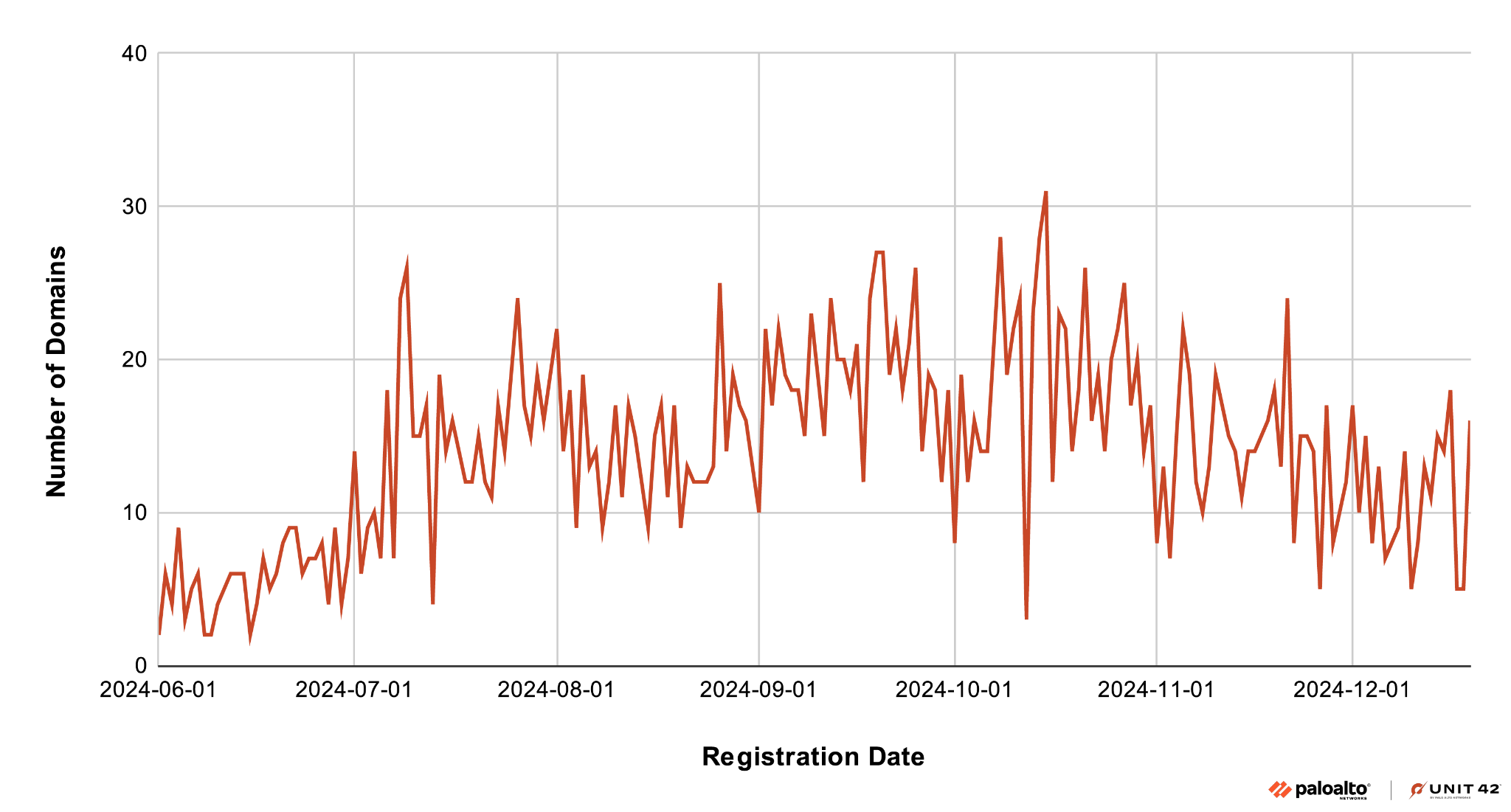
We observed that around 15 domains were created on average per day. Further, most of the domains (82%) were registered in Singapore using registrars with relaxed registration requirements. This is evident from the fake registrant names used for registration such as “Sophia” (14%), “Abe” (4%) and “Sophie” (3%). A steady influx of new domain registrations and repeated use of dummy names suggests automated domain creation.
The threat actor also registered a few domains through reputable, well-known registrars, using paid privacy services to mask the registrants’ names.
Like many malicious websites, these scam crypto websites use free HTTPS certificates (digital credentials that encrypt website traffic).
The campaign heavily used domain fronting, a technique masking the true destination of web traffic, through public cloud services (97% of the hosting IP addresses belong to a single cloud service provider). In some cases, we identified the real hosting IP addresses for some of the domains. Even those real hosting IP addresses were abusing popular shared hosting platforms. This allows them to further camouflage their operations by being among unrelated benign domains hosted on these shared IP addresses. However, our analysis showed highly interconnected malicious domains and these shared hosting IP addresses, suggesting a coordinated attack.
The following points suggest that a single threat actor created the domains involved in this campaign:
- Similar registration records
- Consistent domain creation over time
- Similar TLS certificates
- Similar hosting infrastructure
Conclusion
This article detailed a widespread scam cryptocurrency investment campaign, which operates similarly to Ponzi schemes. They impersonate popular and reputable brands, organizations and events to lure victims. In 2024, we uncovered thousands of websites associated with this campaign.
We found strong evidence that suggests a single threat actor likely operates these websites, given the consistent registration patterns and the use of similar infrastructure. This actor may also be using a sophisticated toolkit to create these fraudulent sites at scale since both the websites and mobile apps involved share common design elements and functionalities.
We hope that the details of the scam crypto investment campaign described in our article can help readers identify similar fraudulent schemes. We strongly advise readers to always conduct thorough research before investing, to safeguard against such scams. Be particularly cautious of unrealistic promises of guaranteed returns, as these are often major red flags for scam investment schemes.
Palo Alto Networks customers are better protected from the threats discussed in this article through our Next-Generation Firewall's Advanced WildFire, Advanced URL Filtering and Advanced DNS Security subscriptions.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Scam Crypto Investment Websites
- 2024olympics-shop[.]com
- ai-doublemintvip[.]com
- ai-virtu[.]com
- aibotusdt[.]com
- aldmeha-aaaa[.]com
- beamusdt[.]top
- diorkks[.]com
- eni-vip[.]com
- gongtea66[.]com
- ibmquantify[.]com
- mudrexgpt[.]org
- nikemall[.]tw
- nmxquantify[.]com
- one-usdt[.]net
- pepsivip-usdt[.]com
- sc-tesla[.]com
- sofiusdt[.]com
- tapswapusdt[.]vip
- tesla-usdt[.]com
- teslabond[.]org
- teslaevcharging[.]com
- teslafund[.]org
- teslamall66[.]vip
- teslausdt[.]net
- teslausdt[.]org
- teslausdt[.]vip
- valero-vip[.]com
- vipoxy[.]top
- viprobot888[.]net
- xpusdt[.]com
Telegram Channels
- t[.]me/NMX_English
- t[.]me/SoFi_USDT
- t[.]me/AiTeslaRoBot
- t[.]me/Virtu_Financial_vip
- t[.]me/NMX_Quantify
- t[.]me/Mudrex_VIP
- t[.]me/youlemeivip
- t[.]me/Tapswap_678
- t[.]me/Alpha_USDT6
- t[.]me/PepsiCovip8
- t[.]me/supercharger_Ch
- t[.]me/Tesla_Supercharger_Mall
- t[.]me/teslavip88
Android Applications Hashes
- e3e4163263d65cd9de073cc564c4ab8be31c418c40eeb25af38fcfbfb063e6d9
- aae9b07dbf0c6205e80acd6a86c716fc46a0bf5fbfee1c1565b62d432c979647
- ebc120ac0608d4b43a23a84e7ebcf84aeee2fca96184928ee787b734d85b0f01
Android Application Download URLs
- hxxps[:]//api.nmxquantify[.]com/nmxquantify.apk
- hxxps[:]//api.teslamall66[.]vip/teslamall66.apk
- hxxps[:]//api.2024olympics-shop[.]com/Olympics.apk
Additional Resources
- Unit42-timely-threat-intel/2024-07-30-Olympics-themed-investment-scam.txt at main – Unit 42 GitHub
- Unit42-timely-threat-intel/2024-08-14-crytpo-investment-scams-impersonating-Tesla.txt at main – Unit 42 GitHub
- Unit42-timely-threat-intel/2024-08-09-scam-impersonating-legit-crypto-exchange.txt at main – Unit 42 GitHub












 Get updates from Unit 42
Get updates from Unit 42