Executive Summary
On Mar. 2, 2021, Volexity reported in-the-wild-exploitation of four Microsoft Exchange Server vulnerabilities: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065.
As a result of these vulnerabilities being exploited, adversaries can access Microsoft Exchange Servers and allow installation of additional tools to facilitate long-term access into victims' environments. There has also been a report of multiple threat actors leveraging these zero-day vulnerabilities, meaning post-exploitation activity may vary depending on the purpose of the different threat actors.
These vulnerabilities affect the following Microsoft Exchange Server versions:
- Microsoft Exchange 2013.
- Microsoft Exchange 2016.
- Microsoft Exchange 2019.
Microsoft has released an emergency out-of-band security update to patch these vulnerabilities. We strongly advise immediately updating all Microsoft Exchange Servers to the latest available patched versions released by Microsoft.
Due to the surge of this malicious activity, we’ve created this threat assessment for overall threat awareness. Full visualization of the techniques observed and their relevant courses of action can be viewed in the Unit 42 ATOM Viewer.
If you think you may have been impacted, please email crypsis-investigations@paloaltonetworks.com or call 855.875.4631 to get in touch with the Crypsis Incident Response team.
Activity Overview: Exploits of Microsoft Exchange Server Vulnerabilities
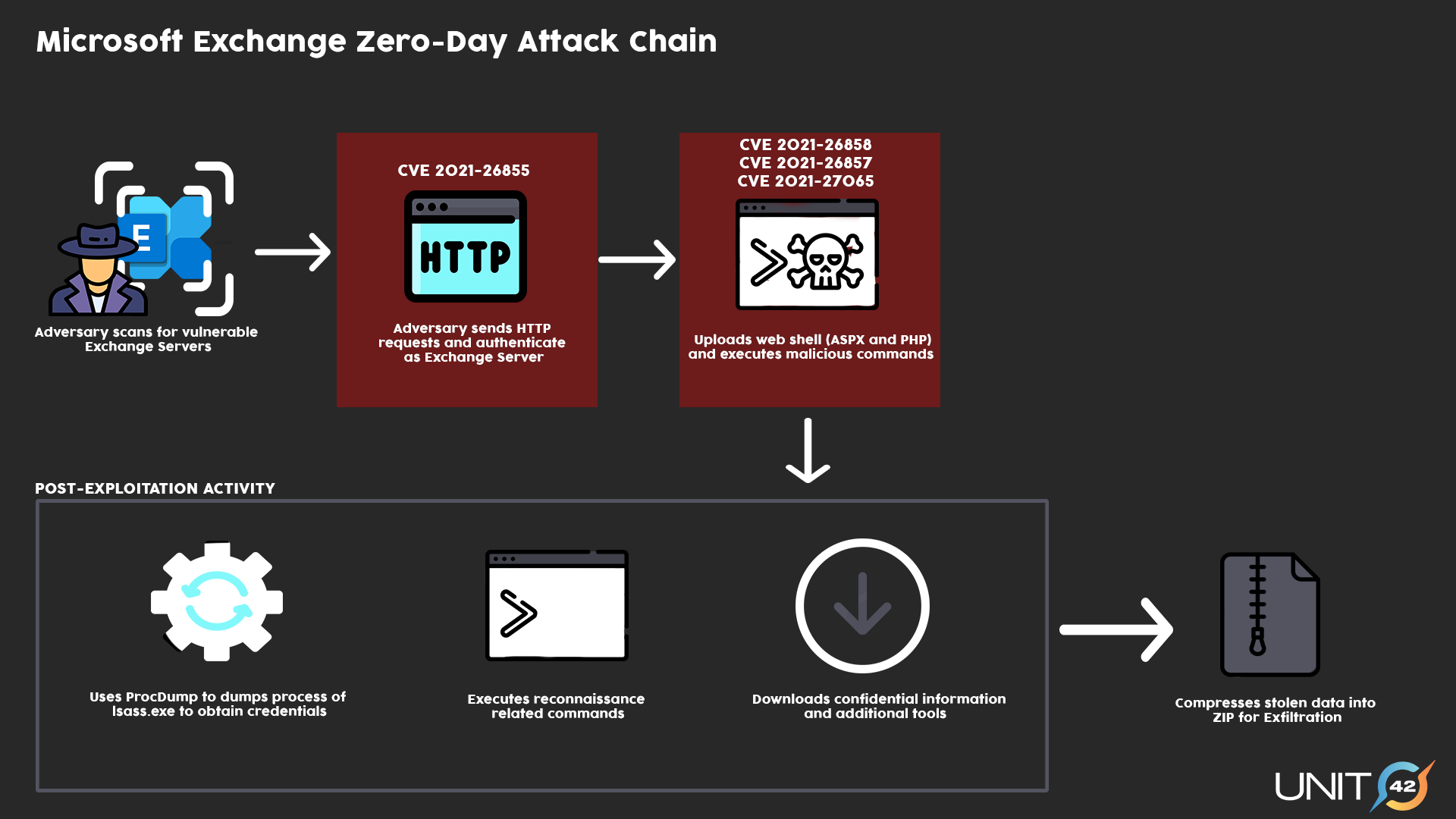
There have been reports of activity from several threat actors exploiting four zero-day vulnerabilities affecting Microsoft Exchange Servers. When these vulnerabilities are chained together, threat actors are able to exploit and gain access to Microsoft Exchange servers.
For this attack to be successful, the adversary would first need to identify an on-premises Microsoft Exchange Server that is able to receive untrusted connections from an external source on port 443. If an adversary is successful in securing a connection, they can then exploit CVE-2021-26855 to authenticate themselves as a Microsoft Exchange server. This can be followed by the exploitation of CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065 post-authentication, allowing the adversary to gain remote access.
If access is achieved, the exploited vulnerabilities will allow threat actors to execute commands remotely, which can include uploading a China Chopper webshell to establish persistence in the compromised system. The webshell would then allow the adversary to steal data and execute additional malicious actions, such as downloading remote files or network service scanning.
When the webshell is deployed, post-exploitation activity typically occurs in the system, most commonly the use of Procdump to dump Local Security Authority Subsystem Service (LSASS) process memory to obtain credentials. There have also been instances in which threat actors downloaded additional tools, such as Nishang and Powercat, to support their actions. Following the extraction of credentials and data from the compromised system, threat actors often use compression utilities such as 7zip or Winrar to compress and stage the stolen data for exfiltration. It’s worth noting that since different groups have leveraged these vulnerabilities, post-exploitation activities may vary depending on the actor behind the attack.
Microsoft has shared ways to determine whether your system has been compromised by this activity. There is also an emergency out-of-band security update to patch these vulnerabilities.
Courses of Action
This section documents the relevant tactics, techniques and procedures (TTPs) observed being used by adversaries leveraging CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065, and maps them directly to Palo Alto Networks product(s) and service(s) which can protect against them. It also further instructs customers on how to ensure their devices are configured correctly.
| Product / Service | Course of Action |
| Initial Access, Persistence, Command and Control, Exfiltration | |
| Exploit Public-Facing Application [T1190], Web Shell [T1505.003], Web Protocols [T1071.001], Ingress Tool Transfer [T1105], Exfiltration Over C2 Channel [T1041], Domain Account [T1136.002] | |
| NGFW | Ensure application security policies exist when allowing traffic from an untrusted zone to a more trusted zone |
| Ensure 'Service setting of ANY' in a security policy allowing traffic does not exist | |
| Ensure 'Security Policy' denying any/all traffic to/from IP addresses on Trusted Threat Intelligence Sources Exists | |
| Ensure 'SSL Forward Proxy Policy' for traffic destined to the internet is configured | |
| Ensure 'SSL Inbound Inspection' is required for all untrusted traffic destined for servers using SSL or TLS | |
| Ensure that the Certificate used for Decryption is Trusted | |
| Set up File Blocking | |
| Ensure that User-ID is only enabled for internal trusted interfaces | |
| Ensure that 'Include/Exclude Networks' is used if User-ID is enabled | |
| Ensure that the User-ID Agent has minimal permissions if User-ID is enabled | |
| Ensure that the User-ID service account does not have interactive logon rights | |
| Ensure remote access capabilities for the User-ID service account are forbidden. | |
| Define at least one 'Include Network'. | |
| Threat Prevention† | Ensure a Vulnerability Protection Profile is set to block attacks against critical and high vulnerabilities, and set to default on medium, low and informational vulnerabilities |
| Ensure a secure Vulnerability Protection Profile is applied to all security rules allowing traffic | |
| Ensure an anti-spyware profile is configured to block on all spyware severity levels, categories and threats | |
| Ensure DNS sinkholing is configured on all anti-spyware profiles in use | |
| Ensure passive DNS monitoring is set to enabled on all anti-spyware profiles in use | |
| Ensure a secure anti-spyware profile is applied to all security policies permitting traffic to the internet | |
| Ensure that antivirus profiles are set to block on all decoders except 'imap' and 'pop3' | |
| Ensure a secure antivirus profile is applied to all relevant security policies | |
| DNS Security† | Enable DNS Security in anti-spyware profile |
| URL Filtering† | Ensure that PAN-DB URL Filtering is used |
| Ensure that URL Filtering uses the action of ‘block’ or ‘override’ on the <enterprise approved value> URL categories | |
| Ensure that access to every URL is logged | |
| Ensure all HTTP Header Logging options are enabled | |
| Ensure secure URL filtering is enabled for all security policies allowing traffic to the internet | |
| WildFire† | Ensure that WildFire file size upload limits are maximized |
| Ensure forwarding is enabled for all applications and file types in WildFire file blocking profiles | |
| Ensure a WildFire Analysis profile is enabled for all security policies | |
| Ensure forwarding of decrypted content to WildFire is enabled | |
| Ensure all WildFire session information settings are enabled | |
| Ensure alerts are enabled for malicious files detected by WildFire | |
| Ensure 'WildFire Update Schedule' is set to download and install updates every minute | |
| Cortex XSOAR | Deploy XSOAR Playbook “HAFNIUM - Exchange 0-day exploits” (Rapid Breach Response pack) |
| Deploy XSOAR Playbook Cortex XDR - Isolate Endpoint | |
| Deploy XSOAR Playbook - Block IP | |
| Deploy XSOAR Playbook - Block URL | |
| Deploy XSOAR Playbook - Hunting and Threat Detection Playbook | |
| Deploy XSOAR Playbook - PAN-OS Query Logs for Indicators | |
| Deploy XSOAR Playbook - Access Investigation Playbook | |
| Deploy XSOAR Playbook - Block Account Generic | |
| Execution, Credential Access, Collection, Lateral Movement | |
| Windows Command Shell [T1059.003], LSASS Memory [T1003.001], Archive via Utility [T1560.001], Web Protocols [T1070.001], Exploit Public-Facing Application [T1190], Remote System Discovery [T1018], System Information Discovery[T1082], System Network Configuration Discovery [T1016], System Service Discovery [T1007], Permission Groups Discovery [T1069], OS Credential Dumping [T1003], Remote Services [T1021], Account Discovery [T1087], Windows Remote Management [T1021.006], Windows Remote Management [T1047], Scripting [T1064], Powershell [T1059.001] | |
| Cortex XDR | Enable Anti-Exploit Protection |
| Enable Anti-Malware Protection | |
| Suspicious Process Creation | |
| Look for the following BIOCs alerts to detect activity*: Cortex XDR Analytics BIOC -Uncommon net group execution Cortex XDR Analytics - Multiple Discovery Commands Cortex XDR BIOC -Exchange process writing aspx files Cortex XDR Agent - Behavioral Threat Detected Cortex XDR Analytics BIOC - Uncommon remote service start via sc.exe Cortex XDR Analytics BIOC - Rare SSH Session Cortex XDR Analytics BIOC - Uncommon ARP cache listing via arp.exe Cortex XDR Analytics BIOC - Uncommon user management via net.exe Cortex XDR Analytics BIOC - WmiPrvSe.exe Rare Child Command Line Cortex XDR Analytics BIOC - Script Connecting to Rare External Host Cortex XDR BIOC - Remote process execution using WMI Cortex XDR BIOC - 64-bit PowerShell spawning a 32-bit PowerShell Cortex XDR BIOC - Suspicious PowerShell Command Line Cortex XDR BIOC - Dumping Registry hives with passwords |
|
Table 1. Courses of Action for observed techniques used by multiple threat actors leveraging zero-day Microsoft Exchange Server vulnerabilities.
†These capabilities are part of the NGFW security subscriptions service.
* These analytic detectors will trigger automatically for Cortex XDR Pro customers.
Conclusion
Due to the alarming activity of threat actors exploiting these zero-day vulnerabilities against vulnerable Microsoft Exchange Servers, we strongly advise immediately updating all Microsoft Exchange Servers to the latest available patched versions released by Microsoft.
As of the time of writing, based on signatures and indicators that have been observed, Palo Alto Networks customers are protected across our product ecosystem, with specific protections deployed in the following products and subscriptions:
- Next-Generation Firewall:
- Threat Prevention. (Deploy Content Pack 8380 which detects the four 0-day vulnerabilities)
- URL Filtering.
- Cortex XDR.
- Cortex XSOAR.
It is imperative for customers to employ best practices in order to ensure Palo Alto Networks products are configured in a manner best suited for your protection.
Additional Resources
- Hunting for the Recent Attacks Targeting Microsoft Exchange
- HAFNIUM targeting Exchange Servers with 0-day exploits
- Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
- Mass Exploitation of Exchange Server Zero-Day CVEs: What You Need to Know












 Get updates from Unit 42
Get updates from Unit 42