Executive Summary
This article reviews nine vulnerabilities we recently discovered in two utilities called cuobjdump and nvdisasm, both from NVIDIA's Compute Unified Device Architecture (CUDA) Toolkit. We have coordinated with NVIDIA, and the company has released an update in February 2025 to address these issues.
The vulnerabilities are tracked as the following Common Vulnerabilities and Exposures (CVEs):
- CVE-2024-53870
- CVE-2024-53871
- CVE-2024-53872
- CVE-2024-53873
- CVE-2024-53874
- CVE-2024-53875
- CVE-2024-53876
- CVE-2024-53877
- CVE-2024-53878
Introduced in 2006, CUDA is a parallel computing platform and programming model. As part of NVIDIA's CUDA Toolkit, developers use the cuobjdump and nvdisasm tools to analyze CUDA binary files used in programs to run on NVIDIA graphics processing unit (GPU) hardware.
While these two tools don't directly execute CUDA code, they are essential for developers to inspect and optimize CUDA-based programs for NVIDIA GPUs. Successfully exploiting the associated vulnerabilities might lead to limited denial of service or limited information disclosure. Potential attackers could impact organizations through vulnerable versions of cuobjdump and nvdisasm in targeted developer environments.
Palo Alto Networks customers are better protected from the potential impact of these vulnerabilities through our Next-Generation Firewall (NGFW) with Cloud-Delivered Security Services that include Advanced Threat Prevention.
We also recommend using the most recent CUDA Toolkit release to avoid vulnerable versions of cuobjdump and nvdisasm.
The Unit 42 Incident Response Team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Related Unit 42 Topics | Vulnerabilities |
NVIDIA CUDA Toolkit
Launched in 2006, CUDA is a parallel computing platform and programming model developed by NVIDIA. Developers use this platform to create software that harnesses the computing power of NVIDIA GPUs for various computing tasks that require significant parallel processing power. These tasks include artificial intelligence (AI), scientific research and multimedia processing.
Developers use the CUDA Toolkit for a development environment to create these GPU-accelerated applications. The CUDA Toolkit can be used in Windows or Linux environments. In either operating system, the developed code is stored in CUDA binary files.
CUDA Binary (Cubin) Files
A CUDA binary is a type of executable file that stores CUDA code, including instructions designed for NVIDIA GPUs. CUDA binaries use a .cubin file extension in their file names, so we commonly refer to these as "cubin" files.
Cubin follows a standardized ELF format [PDF] found in Linux and Unix. Cubin files include sections for the actual executable code, alongside additional information like symbols, relocation data and debugging details for CUDA code to run on NVIDIA GPUs.
A cubin file typically consists of code for both the host (CPU) and device (GPU) portions of a program. Cubin files are produced by compiling the source code written in CUDA C/C++.
Cubin files are easily identifiable through common utilities like the file command. Figure 1 shows the results from running a file command on a cubin file named normal.cubin in a terminal from a Linux environment. The results indicate it is a 64-bit ELF using the NVIDIA CUDA architecture.
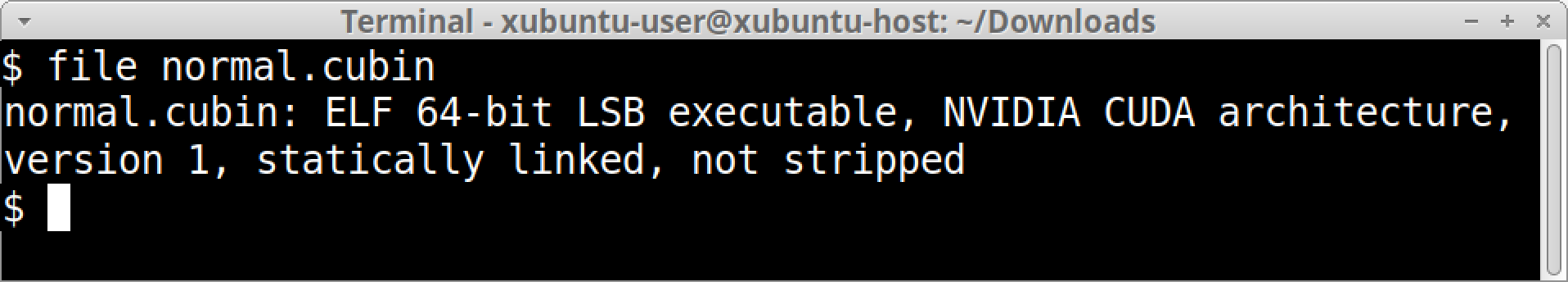
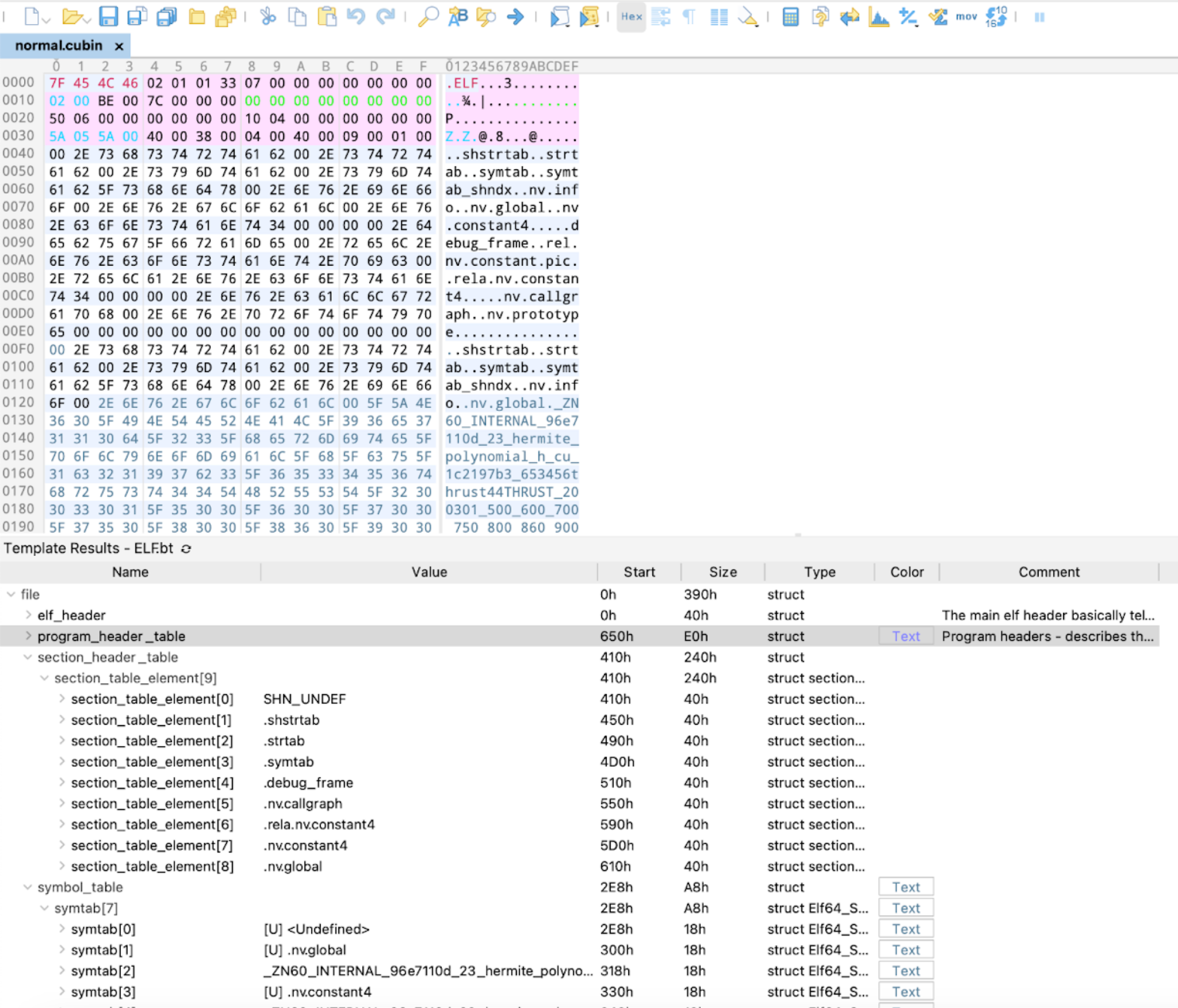
We can further confirm that the cubin file used in Figure 1 follows the ELF format by using tools like 010 Editor. Figure 2 shows the contents of normal.cubin in 010 Editor running an ELF binary template (ELF.bt) to parse and interpret the structure of the binary. The results in the lower half of the image further confirm normal.cubin follows the ELF format.
Cuobjdump and Nvdisasm
We discovered vulnerabilities in two tools from the CUDA Toolkit used to inspect and analyze cubin files. These tools are command-line utilities named cuobjdump and nvdisasm. Before examining the associated vulnerabilities, we should understand how these two tools work.
Cuobjdump
Developers use the CUDA Toolkit command-line utility cuobjdump to inspect and analyze cubin files. Output from cuobjdump presents cubin data in a human-readable format. This tool has several command-line options that developers can use to return information on different aspects of a cubin file.
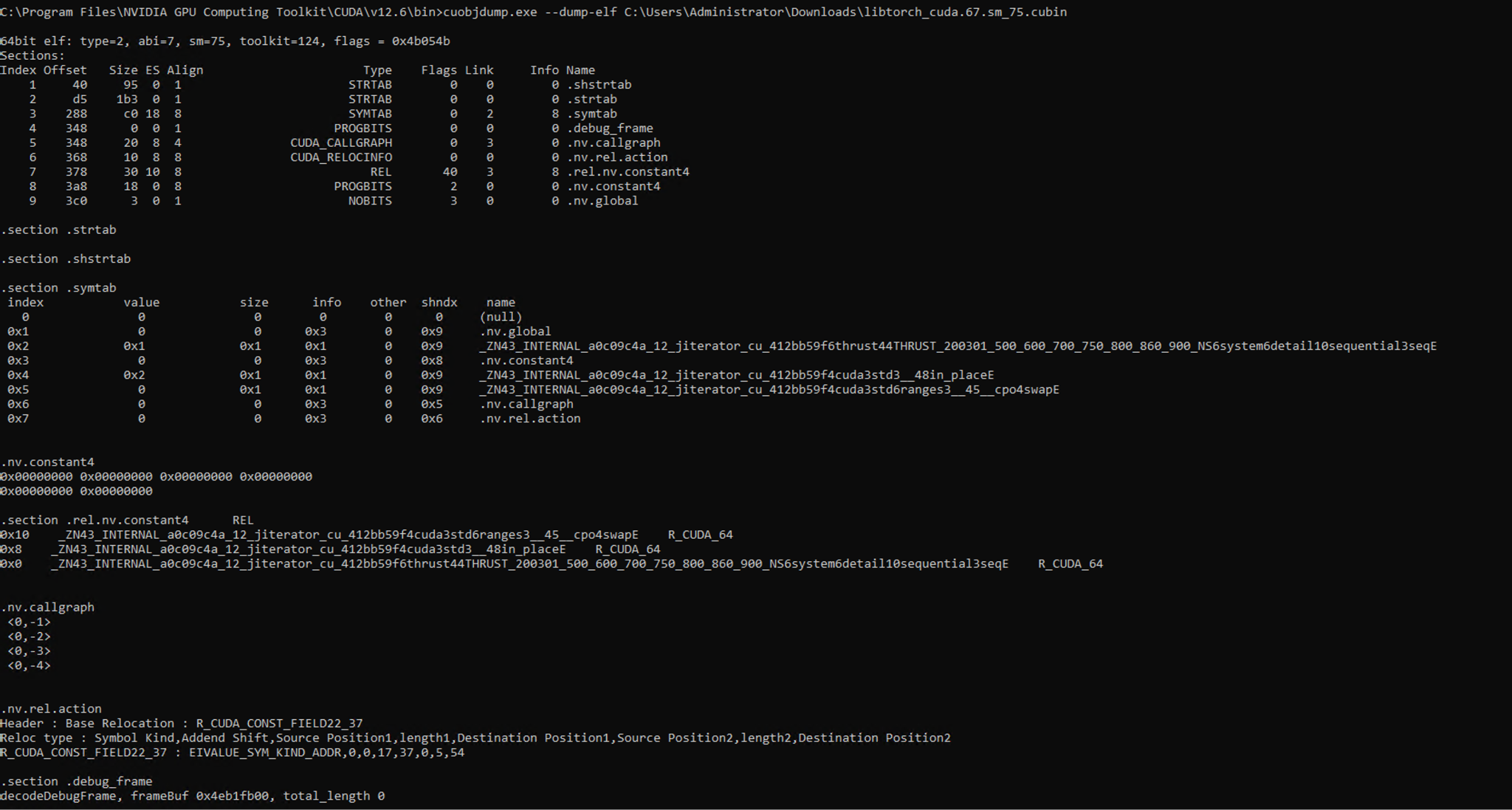
For example, the --dump-elf option returns an information dump on a cubin file's ELF Object sections, which can give a general overview of a cubin file. Figure 3 displays the output of cuobjdump on a cubin file using the --dump-elf option.
Nvdisasm
The nvdisasm command-line tool is a disassembler for cubin files. Like cuobjdump, this tool takes content from a cubin file and converts it to a human-readable format. However, unlike cuobjdump, developers use nvdisasm to gain insight into the low-level operations of their code after it’s been compiled but before it runs on the GPU.
This tool has several command-line options that focus on the functionality of a cubin file's CUDA code. These options can provide different aspects and levels of detail on the disassembled code.
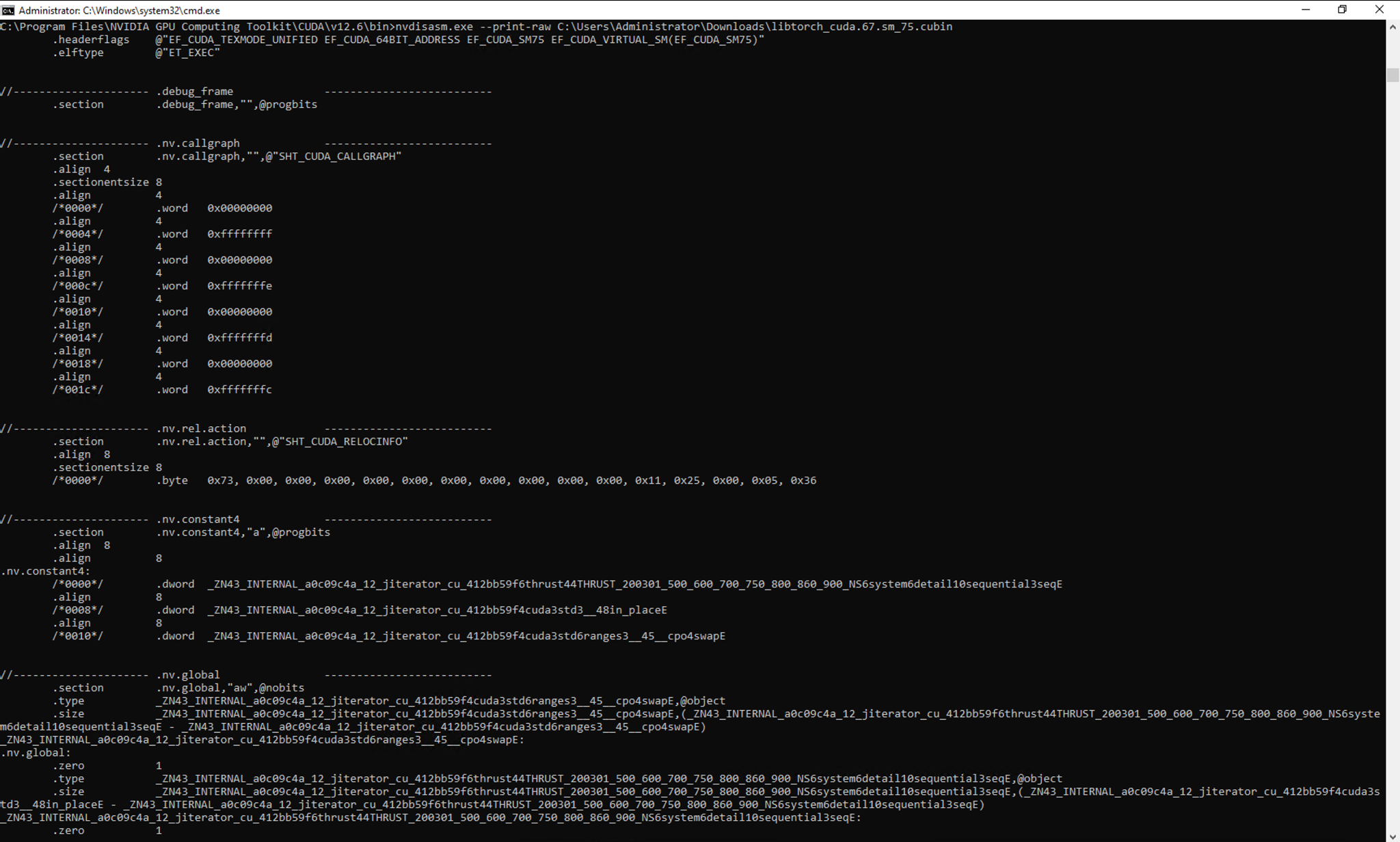
To see the resulting disassembly without any attempt to beautify it, we can use the --print-raw option. Figure 4 shows the output of nvdisasm on a cubin file using the --print-raw option.
The cuobjdump tool works on both standalone cubin files (compiled CUDA binaries) and host binaries (executable files containing embedded CUDA code). In contrast, nvdisasm is more specialized, focusing solely on cubin files. However, nvdisasm offers more detailed and comprehensive output, making it a powerful tool for in-depth analysis. NVIDIA provides a comparison table that efficiently displays the differences between these two tools.
A basic understanding of these two tools allows us to better understand the associated vulnerabilities we discovered.
Review of the Vulnerabilities
During a security evaluation of the NVIDIA CUDA Toolkit, we conducted an extensive fuzz test on cuobjdump and nvdisasm. We ran a file fuzzer on both applications for a month. The results revealed six vulnerabilities in cuobjdump and three vulnerabilities in nvdisasm.
We were able to successfully identify and trigger these vulnerabilities during our testing. To mitigate the risk of these vulnerabilities being weaponized, we will not publicly share specific details.
Ultimately, older versions of cuobjdump and nvdisasm could potentially be exploited by using these tools to analyze a maliciously manipulated cubin file.
The vulnerabilities we discovered in cuobjdump and nvdisasm are classified as two types:
- Integer overflow: Code in a vulnerable application processes an integer value that is too large to store in the intended location
- Out-of-bounds read: Code in a vulnerable application reads data past the end or before the beginning of an intended buffer
Successfully exploiting these vulnerabilities could lead to:
- Limited denial of service
- Limited information disclosure
These vulnerabilities have been assigned Common Vulnerability Scoring System (CVSS) numbers ranging from 2.8 to 3.3 representing a Low level of impact.
Table 1 shows the vulnerabilities we discovered in cuobjdump.
| CVE Designator | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2024-53870 | Integer overflow vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53872 | Out-of-bounds read vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53873 | Integer overflow vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger a heap buffer overflow when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service, code execution and limited information disclosure. |
3.3 |
| CVE-2024-53874 | Out-of-bounds read vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53875 | Out-of-bounds read vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53878 | Out-of-bounds read vulnerability in cuobjdump. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs cuobjdump on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
2.8 |
Table 1. Breakdown of vulnerabilities in cuobjdump.
Table 2 shows the vulnerabilities we discovered in nvdisasm.
| CVE Designator | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2024-53871 | Out-of-bounds read vulnerability in nvdisasm. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when a user runs nvdisasm on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53876 | Out-of-bounds read vulnerability in nvdisasm. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when the user runs nvdisasm on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
| CVE-2024-53877 | Out-of-bounds read vulnerability in nvdisasm. By manipulating a cubin file, an attacker can potentially trigger an out-of-bounds read when the user runs nvdisasm on the file.
A successful exploit of this vulnerability may lead to limited denial of service and limited information disclosure. |
3.3 |
Table 2. Breakdown of vulnerabilities in nvdisasm.
Conclusion
NVIDIA's CUDA Toolkit is a fundamental component of the broader CUDA ecosystem, which supports the development, deployment and execution of CUDA programs.
While cuobjdump and nvdisasm are not directly involved in executing CUDA code, they are essential for developers looking to inspect and optimize their GPU programs.
Vulnerabilities in tools like cuobjdump and nvdisasm have wider implications, because they are part of the CUDA Toolkit. Attackers could possibly target organizations if these vulnerabilities exist in their development environments. CUDA is widely used in security-sensitive applications in generative AI, machine learning and scientific computing. We recommend that developers use the most up-to-date version of this and any other development platform.
NVIDIA released a security update to address these vulnerabilities in February 2025, so concerned parties can update to the latest version and avoid these vulnerabilities.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected by our products like Next-Generation Firewall (NGFW) with Cloud-Delivered Security Services that include Advanced Threat Prevention.
- NGFW with an Advanced Threat Prevention subscription can identify and block the command injection traffic, when following best practices, via the following Threat Prevention signatures: 95847, 95848, 95849, 95850, 95852, 95853, 95854, 95855, 95856
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Disclosure Timeline
- Report date: October 2024
- Confirmed date: Nov. 15, 2024
- CVEs assigned date: Jan. 7, 2025
- Release date: Feb. 18, 2025
Additional Resources
- NVIDIA Product Security – NVIDIA
- CUDA Toolkit - Free Tools and Training – NVIDIA Developer
- CUDA Binary Utilities – NVIDIA Docs












 Get updates from Unit 42
Get updates from Unit 42