This post is also available in: 日本語 (Japanese)
Executive Summary
Today, INTERPOL and The Nigeria Police Force announced the arrest of a prominent business email compromise (BEC) actor who has been active since 2015. His apprehension marks the latest success for Operation Delilah - a counter-BEC operation that began in May 2021 and has involved international law enforcement and industry cooperation across four continents.
BEC remains the most common and most costly threat facing organizations globally. This threat held the top spot for the sixth year in a row on the 2021 FBI Internet Crime Complaint Center (IC3) report. Over half a decade, global losses have ballooned from $360 million in 2016 to a staggering $2.3 billion in 2021. Despite these massive loss amounts, industry and global law enforcement continue to make considerable strides toward thwarting this activity.
Unit 42 tracks Nigerian BEC actors under the name SilverTerrier. Following the arrest of 11 BEC actors as part of Operation Falcon II in December 2021, this recent operation is significant in that it demonstrates the resolve of global law enforcement to hold BEC actors accountable despite temporary setbacks. Specifically, in this case, the SilverTerrier actor fled Nigeria in 2021 when authorities initially attempted to apprehend him. Months later, in March 2022, he attempted to return home and was quickly identified and detained as he attempted to re-enter Nigeria. This level of international cooperation, tracking of actors as they travel internationally and subsequent apprehension of actors upon returning to their home countries represents a laudable advancement in the ability of global law enforcement organizations to combat these types of crimes.
Palo Alto Networks Unit 42 was thanked for its collaboration with INTERPOL in Operation Delilah. The team provided telemetry and other insights about BEC actors.
This blog provides a brief overview of the actor’s activities and provides recommendations to help organizations protect against these threats.
Palo Alto Networks customers are protected against the types of BEC threats discussed in this blog by products including Cortex XDR and the WildFire, Threat Prevention, AutoFocus and Advanced URL Filtering subscription services for the Next-Generation Firewall.
| Related Unit 42 topics | SilverTerrier, Cybercrime, Business Email Compromise |
SilverTerrier Actor

Domains: We have identified over 240 domains that were registered using this actor's aliases. Of that number, over 50 were used to provide command and control for malware. Most notably, this actor falsely provided a street address in New York city associated with a major financial institution when registering his malicious domains. Examples of domains registered by this actor include: goldmedal-inlt[.]com,gulfmedlcal[.]com, magen-ecoenregy[.]com, nauticelegal[.]com, sanof1[.]com and scbc-uk[.]com.
Malware: ISRStealer, Pony, LokiBot
Oldest Activity: 2015
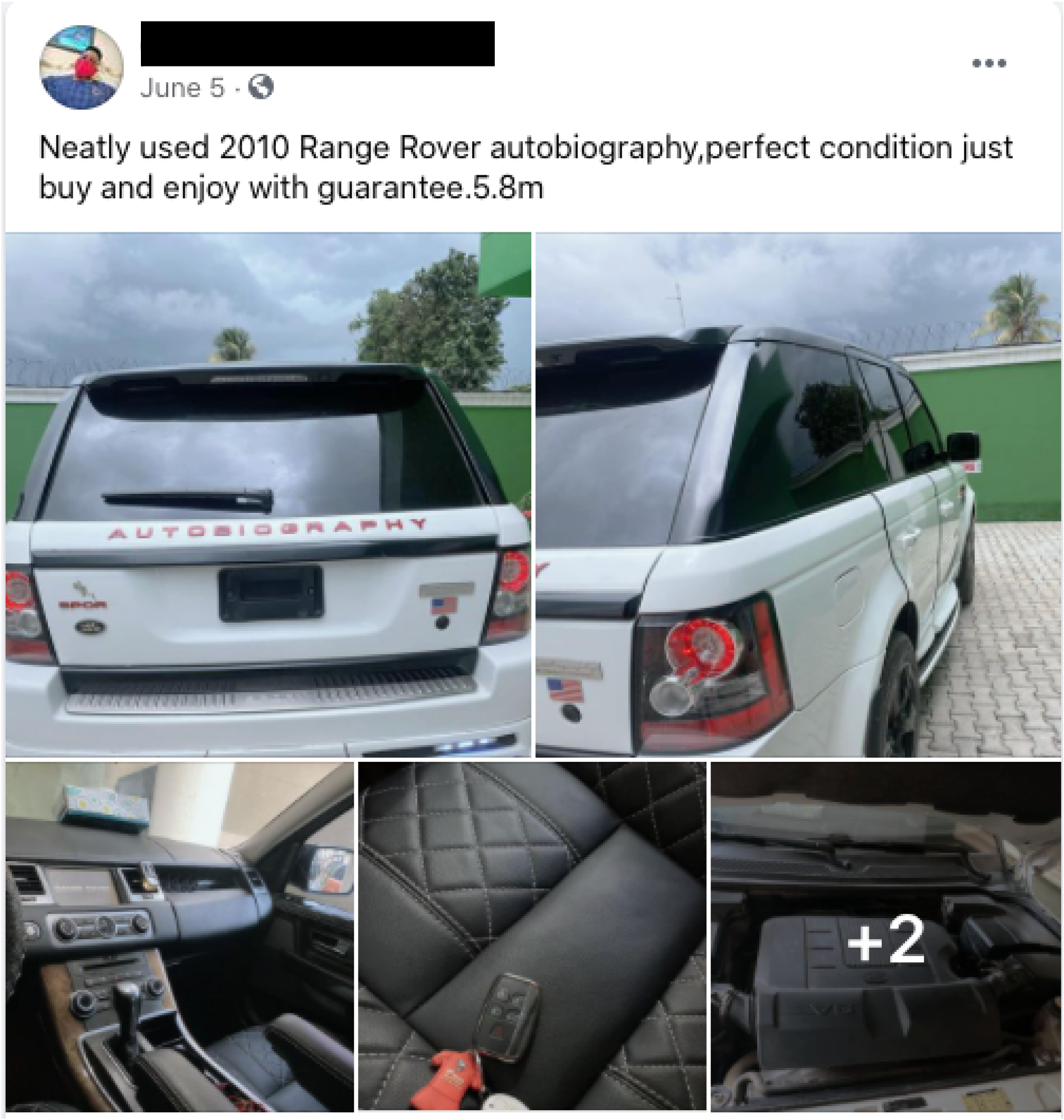
Departing Nigeria: Upon fleeing Nigeria in June 2021, this actor was observed attempting to sell his Autobiography Special Edition Range Rover for 5.8 million Naira.
Interesting Notes: This actor shares social media connections with Onuegbu Ifeanyi Ephraim, Darlington Ndukwu, and Onukwubiri Ifeanyi Kingsley, all of whom were arrested in 2021 as part of Operation Falcon II. He is also considered to be well connected with other known BEC actors.
Protections and Mitigations
The best defense against BEC campaigns is a security posture that favors prevention. Please see our full list of recommendations for a prevention-focused approach to BEC.
Finally, for Palo Alto Networks customers, our products and services provide several capabilities designed to thwart BEC attempts, including:
 |
Cortex XDR protects endpoints from all malware, exploits and fileless attacks associated with SilverTerrier actors. |
 |
WildFire® cloud-based threat analysis service accurately identifies samples associated with information stealers, RATs and document packaging techniques used by these actors. |
 |
Threat Prevention provides protection against the known client and server-side vulnerability exploits, malware and command and control infrastructure used by these actors. |
 |
Advanced URL Filtering identifies all phishing and malware domains associated with these actors and proactively flags new infrastructure associated with these actors before it is weaponized. |
 |
Users of AutoFocus™ contextual threat intelligence service can view malware associated with these attacks using the SilverTerrier tag. |
Conclusion
While BEC schemes remain the most profitable and widespread form of cybercrime on the internet, private/public collaborative efforts continue to make tremendous strides in combating these threats on a global scale. The success of this most recent joint operation highlights the expanding capability of global law enforcement to coordinate and track actors as they travel abroad, ultimately leading to apprehension of BEC actors when they return to their home countries.
Palo Alto Networks was the first cybersecurity company to sign a partnership agreement with INTERPOL in 2017. This agreement served as the foundation for our collaborative efforts in combating criminal trends in cyberspace and other cyberthreats globally. Since then the partnership has continued to evolve, and today Palo Alto Networks remains a proud contributing member of INTERPOL's Gateway program.
Additional Resources
2022 - Operation Falcon II: Unit 42 Helps INTERPOL Identify Nigerian Business Email Compromise Ring Members
2021 - Interpol Operation Falcon II
2021 – Credential Harvesting at Scale Without Malware
Mitre: SilverTerrier Group
2020 - Interpol Operation Falcon
2020 – SilverTerrier: New COVID-19 Themed Business Email Compromise Schemes
2019 – SilverTerrier: 2019 Nigerian Business Email Compromise Update
2018 – SilverTerrier: 2018 Nigerian Business Email Compromise Update
2017 – SilverTerrier: The Rise of Nigerian Business Email Compromise
2016 – SilverTerrier: The Next Evolution in Nigerian Cybercrime
2014 – 419 Evolution
Unit 42 - Business Email Compromise - Response Services
Unit 42 - Business Email Compromise - Readiness Assessment











 Get updates from Unit 42
Get updates from Unit 42