Executive Summary
Organizations are facing an increase in obfuscation behavior from on-site and remote employees attempting to bypass proxy servers to hide their online activities or exfiltrate data without detection. For example, an employee might use the “incognito” mode, download a personal virtual private network (VPN) or the Tor browser, or bypass the corporate VPN. In those cases, the information security team (InfoSec) needs complete network visibility to determine if that employee is solely guarding their own privacy, masking behavior that breaks organization policies or attempting to cover an attack.
Personal VPN services promise to enable secure, encrypted tunnels for user traffic. They provide services that prevent others from seeing through these tunnels by encrypting the internet connection and keeping users' application usage and browsing history private. VPNs may be used to bypass internet censorship and traffic policy enforcement. However, in practice, they obscure organizations’ visibility into networks.
Network visibility is important for a variety of reasons, including improved security by policy enforcement, a decrease in shadow IT, and speedy detection of malicious or suspicious activities. It can enhance application profiling for organizations and aid in well-informed decision-making.
Organizations often use tools such as Palo Alto Networks Next-Generation Firewalls to gain immense visibility into network traffic. Enterprises may attempt to obtain visibility down to the packet, application and user level.
Here, we assess personal VPN applications and their risk and threats to network visibility within organizations. We will touch on how these applications and services evade firewalls to bypass security and policy enforcement mechanisms.
Palo Alto Networks customers can maintain complete network visibility through the use of the Next-Generation Firewall App-ID, which assists in the identification and sanitization of personal VPNs in networks.
Using Personal VPN on Corporate Networks: Key Risks
VPNs enable users to access network resources that may remain inaccessible otherwise. VPNs were developed to allow companies in different locations to connect their internal networks via encrypted channels through the internet. They are commonly used in workplaces to provide access to assets and devices for users who are not physically connected to a corporate network, such as remote workers. However, VPNs are now readily available to everyone – in some cases, free of charge. Nonetheless, average users often don't consider the risks of using personal VPNs on company devices.
Concerning data security and privacy with VPNs, in most cases, users have to simply trust their VPN providers, since providers operate the network tunnel. Moreover, providers can see which websites the user visits, including non-encrypted data, and the frequency of their visits. This data can be stored; some of it is valuable to advertising and marketing firms that use surfing behaviour to deliver ads to the right target audience. VPN providers could double-dip users and businesses by taking subscription money from users and selling users' web consumption data to the advertising industry. In more extreme cases, they might even supply user data to government authorities.
Using personal VPNs can introduce risks to networks. These risks involve threats that InfoSec teams mitigate in corporate environments via a defense-in-depth strategy to protect endpoints and prevent users from performing specific unauthorized tasks, either deliberately or accidentally.
Attackers constantly scan for vulnerable networks to compromise. If attackers succeed at compromising even one computer from an organization, the entire network could be at risk. Organizations use their domain name systems (DNS), enterprise data loss prevention (DLP), and proxy servers as countermeasures, each of which plays an important role in protecting users, data and communications. Circumventing any of those decreases network visibility and endangers the organization.
One of the primary uses of proxy servers is to prevent employees' access to browsing inappropriate and unsafe sites and monitor traffic. In addition, proxy servers protect corporate endpoints from communication with malicious command and control (C2) servers. However, through VPNs, users can bypass this protection. For example, if an employee's computer gets infected while using a VPN, the data sent to the C2 server will not be visible to the InfoSec team.
Insider threats pose almost as significant a risk to enterprise security as external intruders. Private or personal VPNs allow employees to bypass security measures and permissions that the InfoSec team put in place. VPNs can leave online activities vulnerable to hackers. In addition, the IT team loses its complete visibility into users' activities – for example, they hide when users browse unsafe or forbidden sites.
Known VPN Vulnerabilities
Not only does the underlying functionality of VPN products bring risks to the organization, but also, these products are often targeted by advanced persistent threats (APTs) due to their vulnerabilities. Unfortunately, cybercriminals all too often find ways to exploit known and patched vulnerabilities, banking on not all users having kept their patches up to date.
We took a list of the best VPN products of 2021 according to PC Magazine and checked the number of known vulnerabilities they have had in the past few years, as seen in Table 1.
| Name | Number of Vulnerabilities | Vuln ID | Highest CVSS Severity |
| Private Internet Access VPN | 12 | CVE-2020-15590
CVE-2019-12579 CVE-2019-12578 CVE-2019-12577 CVE-2019-12576 CVE-2019-12575 CVE-2019-12574 CVE-2019-12573 CVE-2019-12571 CVE-2019-12572 CVE-2018-10190 CVE-2017-15882 |
V3.0: 7.8 HIGH
V2.0: 9.3 HIGH |
| NordVPN | 3 | CVE-2018-3952
CVE-2018-10170 CVE-2018-9105 |
V3.0: 9.8 CRITICAL
V2.0: 10.0 HIGH |
| IVPN | 3 | CVE-2020-7043
CVE-2020-7042 CVE-2020-7041 |
V3.1: 9.1 CRITICAL
V2.0: 6.4 MEDIUM |
| ExpressVPN | 2 | CVE-2020-29238
CVE-2018-15490 |
V3.1: 7.5 HIGH
V2.0: 5.0 MEDIUM |
| ProtonVPN | 2 | CVE-2018-4010
CVE-2018-10169 |
V3.0: 9.8 CRITICAL
V2.0: 10.0 HIGH |
| Hotspot Shield VPN | 2 | CVE-2020-17365
CVE-2018-6460 |
V3.1: 7.8 HIGH
V2.0: 7.2 HIGH |
| CyberGhost VPN | 1 | CVE-2018-10646 | V3.0: 7.8 HIGH
V2.0: 7.2 HIGH |
| TunnelBear VPN | 1 | CVE-2018-10381 | V3.0: 9.8 CRITICAL
V2.0: 10.0 HIGH |
Table 1. Best VPN products of 2021 according to PC magazine, the number of known vulnerabilities in those services, and information on CVEs and severity.
How Do VPN Applications Try to Evade Firewalls?
Given that they can introduce vulnerabilities into an organization's network, it's concerning that the function of VPN applications includes trying to evade firewalls. VPNs cannot make online connections completely anonymous; however, VPNs typically tunnel into other protocols and use encryption techniques. VPN service providers can use secure VPN protocols such as Internet Protocol Security (IPsec), Transport Layer Security (SSL/TLS), Datagram Transport Layer Security (DTLS), Microsoft Point-to-Point Encryption (MPPE), Microsoft Secure Socket Tunneling Protocol (SSTP), Secure Shell VPN (SSH/OpenSSH), OpenVPN and WireGuard. However, these are all secure and well-defined protocols for legitimate use of VPNs, which comes with a disadvantage for personal VPN service providers. Because these are all known protocols, they can easily be blocked by organizations or governments. This poses a contradiction with the VPN provider's promise to their customer, which is 100% secure connectivity and availability.
VPN providers do their best to remain undetectable in the network, leveraging methods such as switching ports or servers or hopping from protocols. For example, VPN services that are based on OpenVPN give their users the option to change the transport protocol to Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). However, the demand for remaining undetected while maintaining full availability to serve customers goes further than that. Some VPN companies design their proprietary protocols precisely for circumventing organization or government blocks.
In this section, we review the evasion techniques that are used by some VPN products.
Self-Signed Certificate
Figure 1 illustrates how Hotspot Shield uses a bogus self-signed certificate to evade firewalls with its traffic. However, It can be identified with methods such as examining TLS Cipher Suite information, port number and observation of a pattern that is different from the genuine certificate.
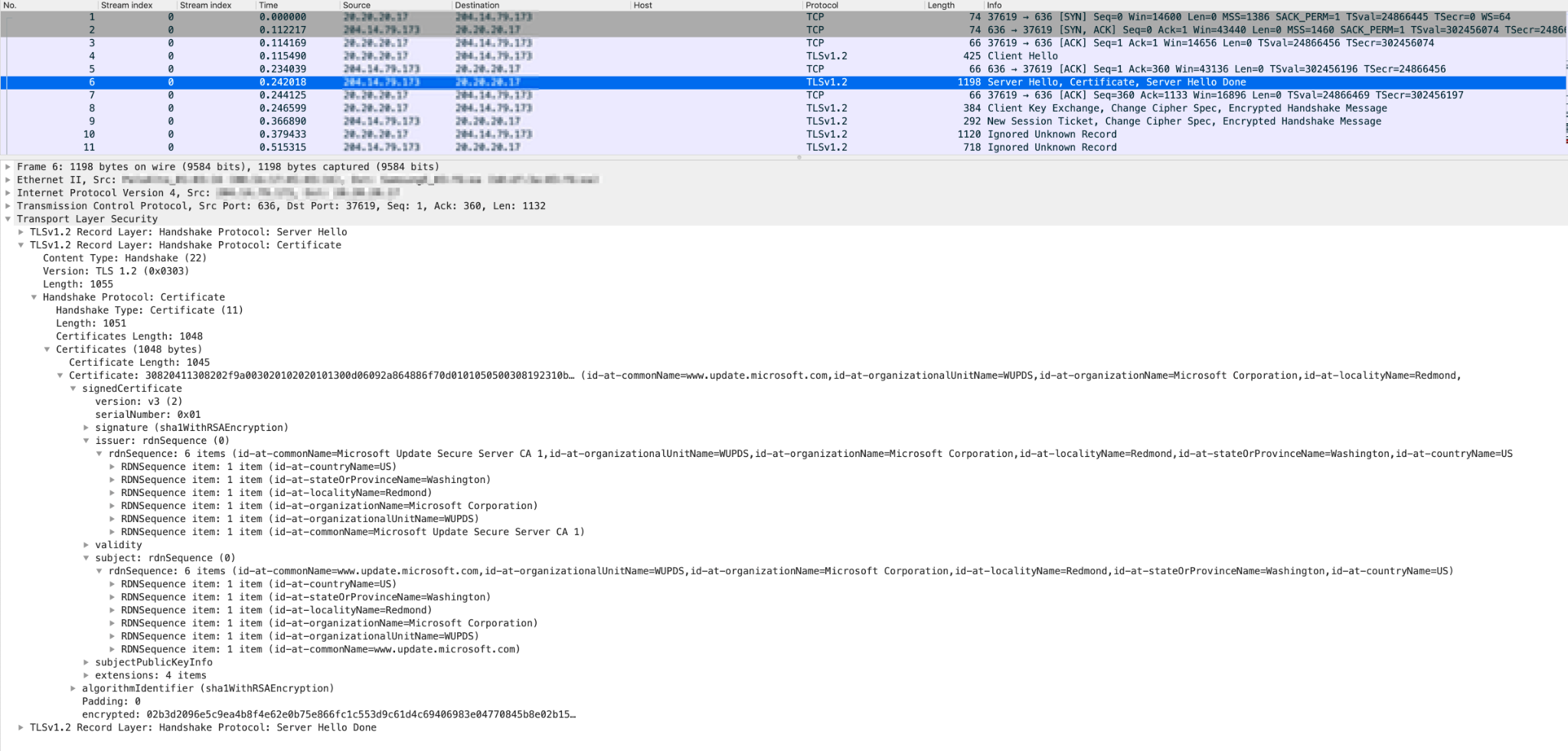
“Tunnel Into HTTP Traffic”
Some VPN applications try to traverse firewalls by sending traffic that appears to be simple HTTP traffic. However, with close inspection, their characteristics can be identified, such as authentication header or encoding, HTTP request method or port number, along with other distinct information in the request headers. These can be used to identify such applications.
Figure 2 shows that SetupVPN, which has over two million users, uses the HTTP proxy-authorization header to authenticate users to its server. Deciphering the header presents helpful information about the SetupVPN application.
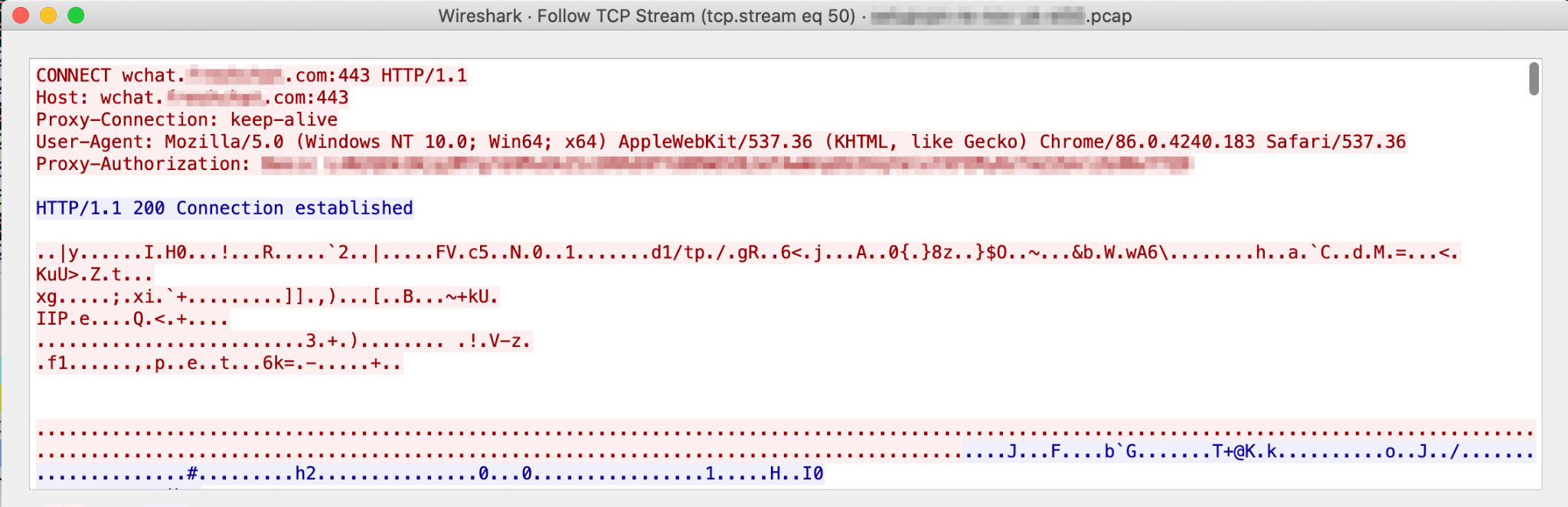
Mimicking Common Protocols
VPN applications send traffic using well-known ports for their communication to evade firewalls and cause misidentification of the firewall implementation to pass through firewalls. For instance, with over 10 million users, Thunder VPN uses UDP port 53, known for its use for DNS, and TCP port 443, known for its use for the HTTP protocol over TLS/SSL.
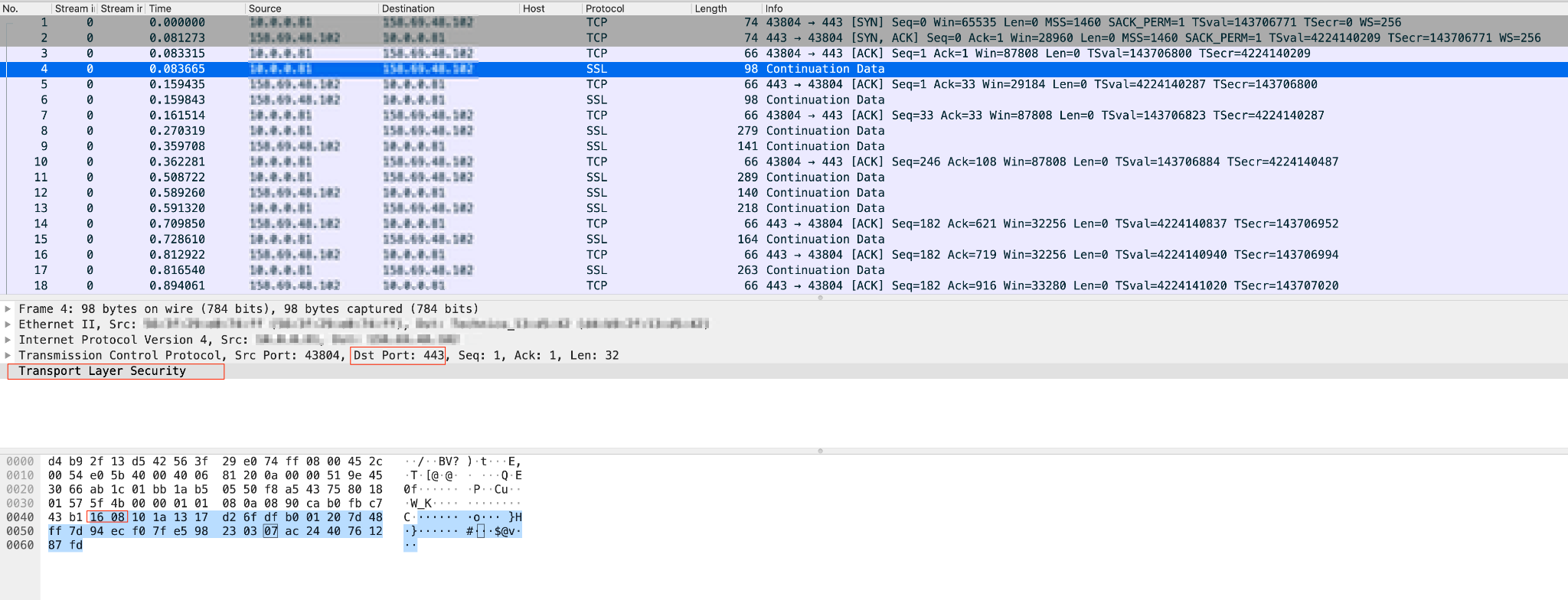
The above figure shows that the traffic on port 443 sent by Thunder VPN was misidentified as SSL in Wireshark. Thunder VPN mimics SSL traffic by utilizing the same port and handshake type.
Thunder VPN also uses port 53 to evade traffic using default DNS ports that are generally allowed in all networks. In addition, the DNS reserved flag Z is set to 1, which must be zero in all DNS queries and responses in the traffic originated by this application. The UDP traffic on port 53 sent by Thunder VPN is as shown in Figure 4.
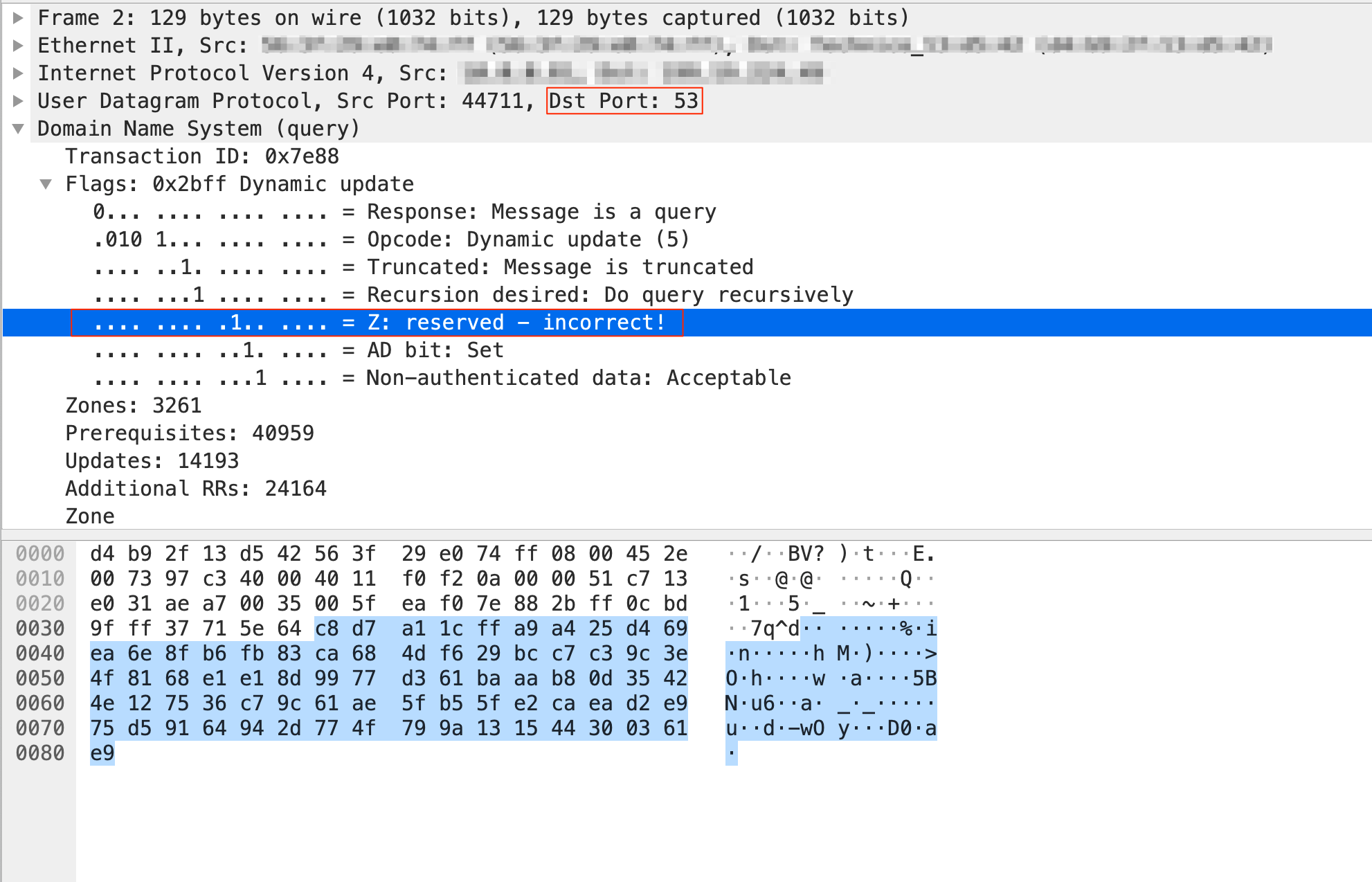
Conclusion
With the rise of remote work as adopted by most corporations these days, network security teams should recognize the potential threats presented by personal VPN usage and adjust security policies accordingly.
The Palo Alto Networks App-ID technology provides customers with the ability to control applications and protocols in their networks. It allows information and network security teams to securely enable applications through policies that allow or deny applications contextually. This helps keep the attack surface as small as possible.
App-ID, which is now running on the Palo Alto Networks Next-Generation Firewall, can grant visibility into VPN apps and their underlying protocols in your network, including all the protocols mentioned in this article. App-ID can help security teams see who uses VPN applications in your entire network – as well as when and where – and enforce policies chosen by your organization. Currently, App-ID covers more than 70 of the most popular VPN services.
The App-ID team constantly reviews and releases updates for the latest versions of VPN applications to its customers. Due to the nature of these applications, their traffic changes frequently to evade firewalls.
Additional Resources
File Transfer Threats: Risk Factors and How Network Traffic Visibility Can Help
Evasion of Security Policies by VPN Clients Poses Great Risk to Network Operators












 Get updates from Unit 42
Get updates from Unit 42