This post is also available in: 日本語 (Japanese)
Shade ransomware is a long-established family of ransomware first spotted in late 2014 targeting hosts running Microsoft Windows. It is also known as Troldesh. Shade has been distributed through malicious spam (malspam) and exploit kits. A recent report focused on Russian language emails that deliver Shade, but this ransomware is also distributed through English-language malspam.
Where is Shade currently appearing? To answer this question, we reviewed recent trends in Shade ransomware among our customer base. Our results indicate the majority of recent Shade ransomware executables have also targeted users outside of Russia.
In fact, our research shows that the top five countries affected by Shade ransomware are not Russia or nations of the former Soviet Union, they are the United States, Japan, India, Thailand, and Canada, Russia only occurs at number seven and the only other country we found in the top ten where Russian is an official language is Kazakhstan at number ten. The top industries attacked in these countries were High-Tech, Wholesale, and Education.
Very Little Change Since 2016
The Shade ransomware executable (EXE) has been remarkably consistent. All EXE samples we have analyzed since 2016 use the same Tor address at cryptsen7f043rr6.onion as a decryptor page. The desktop background that appears during an infection has been the same since Shade was first reported as Troldesh in late 2014.
Shade ransomware infections may include other activity like click fraud traffic as noted here.
Russian and English Language Distribution
Recent reports of malspam pushing Shade ransomware have focused on distribution through Russian language emails. However, Shade decryption instructions have always included English as well as Russian text. English language waves of malspam have been noted pushing Shade ransomware, like this wave of IRS notifications targeting recipients in the United States in 2017.
What does a Shade infection look like?
When a Windows host is infected with Shade ransomware, its desktop background announces the infection, and ten text files appear on the desktop named README1.txt through README10.txt as shown in Figure 1.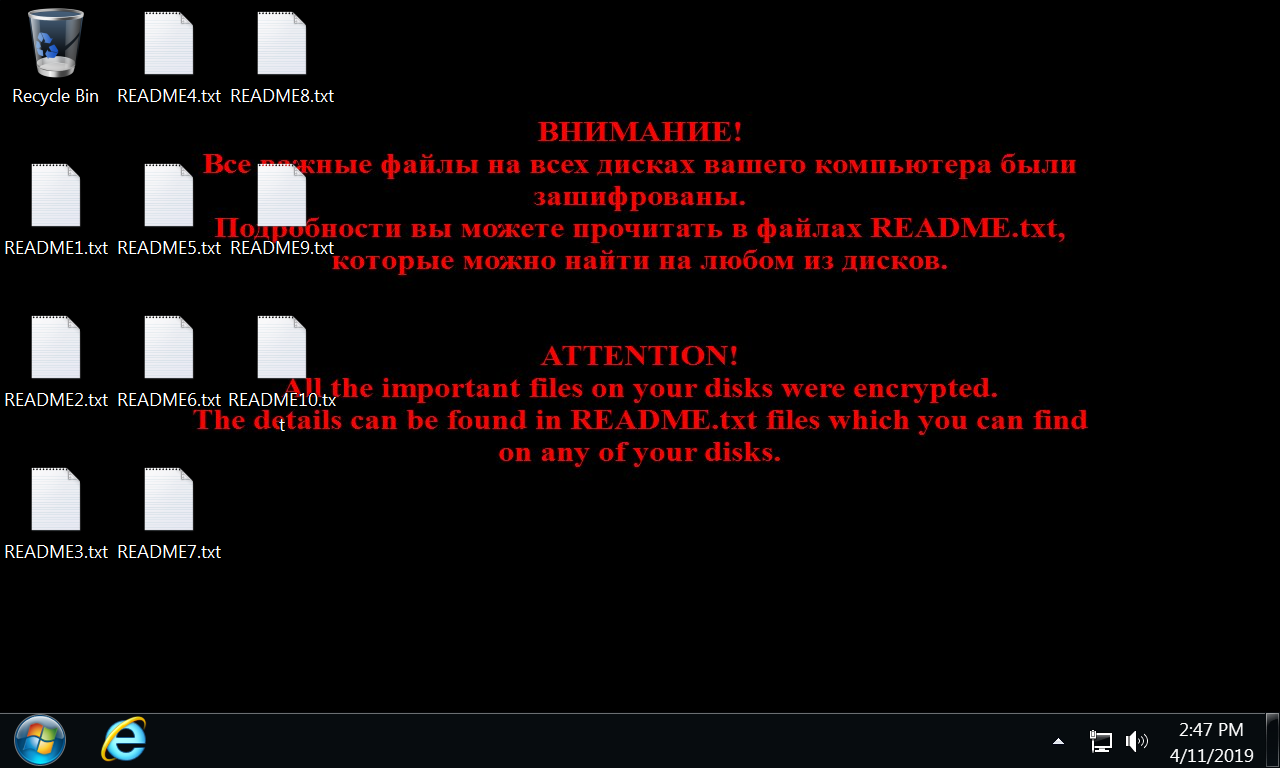
Figure 1. Desktop of a Windows host infected with Shade ransomware.
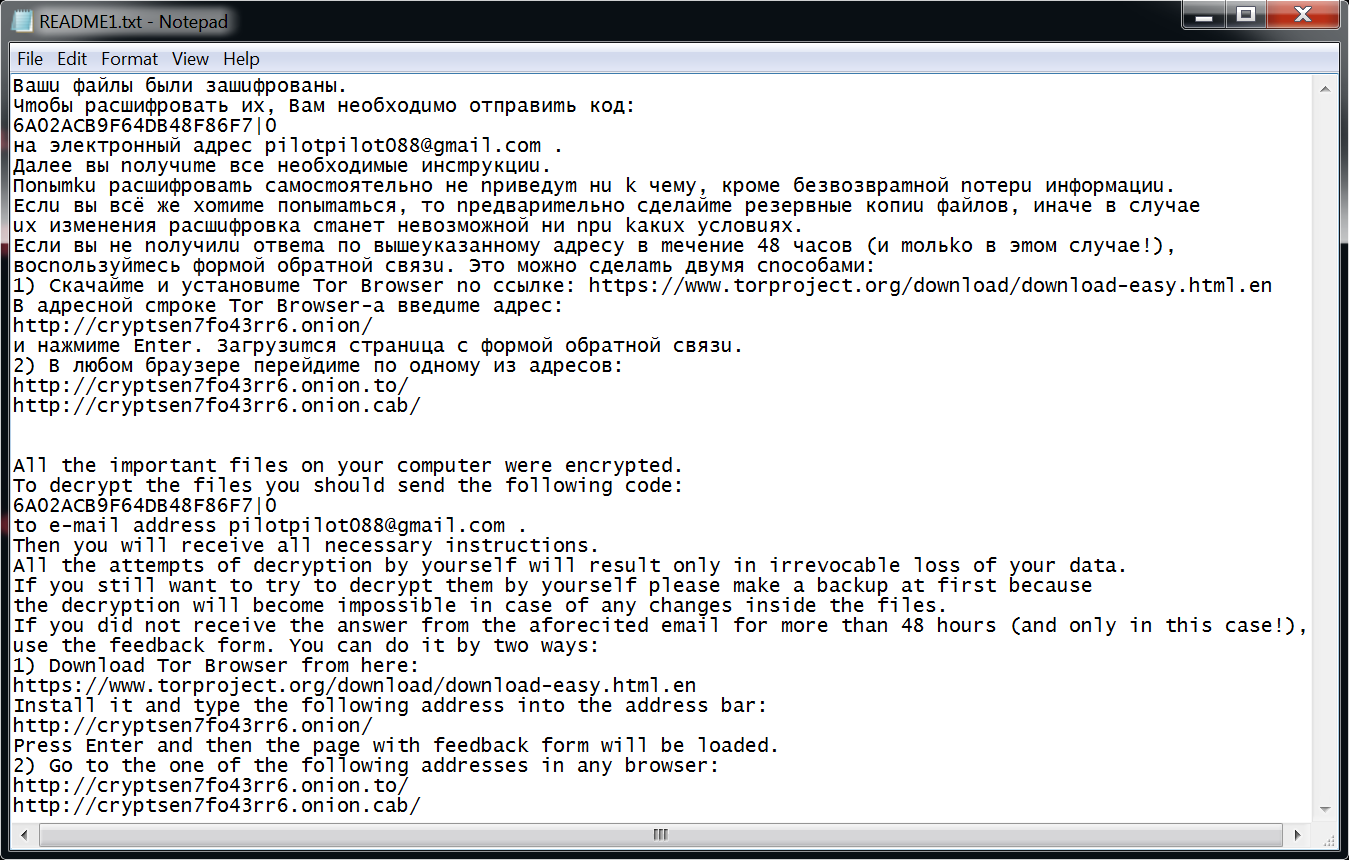
The ten README files all contain the same instructions as shown in Figure 2.
Figure 2. Decryption instructions from a recent Shade ransomware infection.
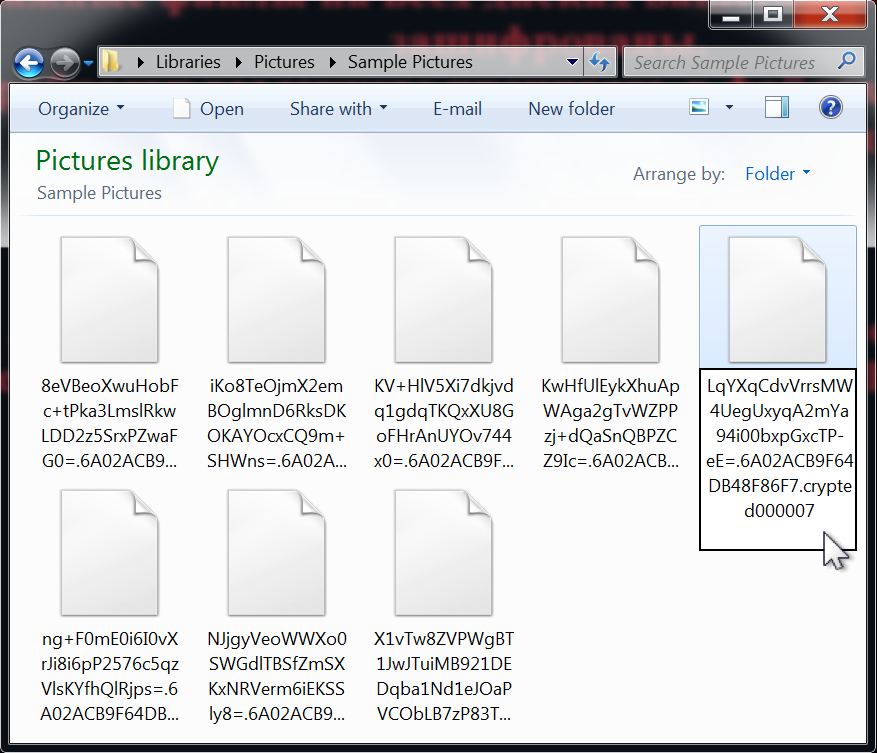
Since June 2016, file extensions for any encrypted files are .crypted000007 as shown in Figure 3.
Figure 3. Examples of encrypted files from a Shade ransomware infection.
Shade Distribution through Malspam
Malspam-based infections for Shade ransomware involve a JavaScript (.js) or other type of script-based file disguised as an invoice or bill. In some cases, Shade malspam has links for these script-based files. In other cases, the files are directly attached to the emails within a zip file or other type of archive. In February 2019, waves of Russian-language malspam used attached PDF files with links to download zip archives containing these script-based files.
In all cases we have reviewed, a .js or other script-based file was involved as indicated in Figure 4. These script-based files are designed to retrieve executable files for Shade ransomware.
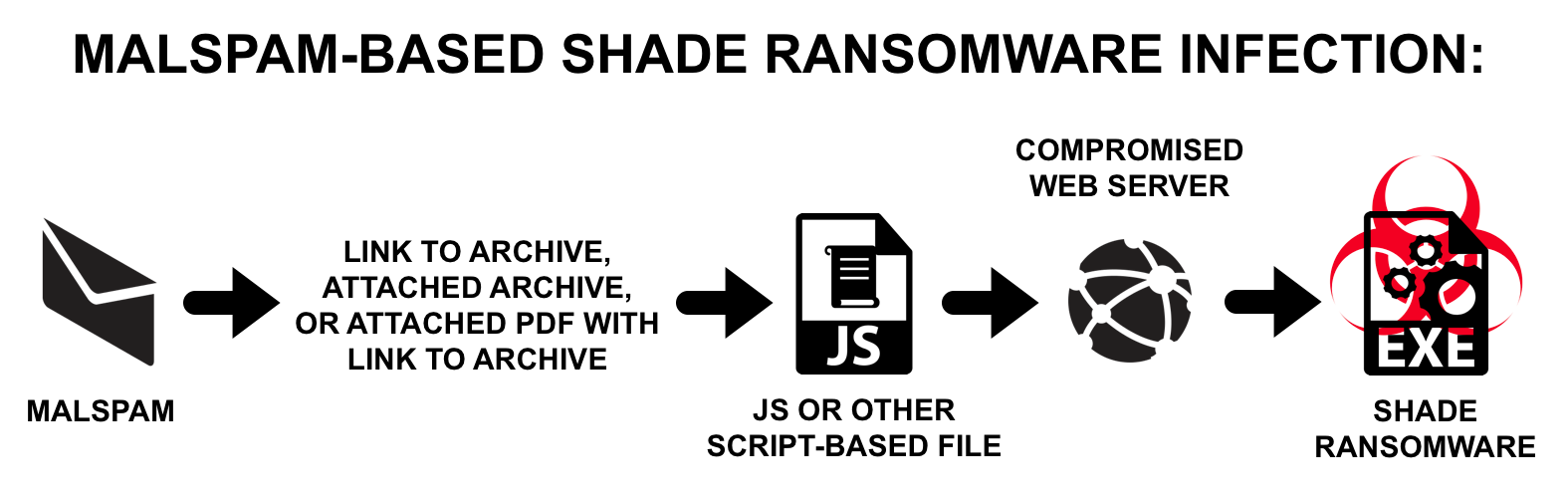 Figure 4. Flow chart for malspam-based Shade ransomware infections.
Figure 4. Flow chart for malspam-based Shade ransomware infections.
Executable delivery during the infection chain
Malspam-based Shade infection chains have one thing in common. They all involve retrieving an executable file from a compromised server. By focusing on the executable in this chain of events, we can determine where Shade ransomware infection attempts have occurred.
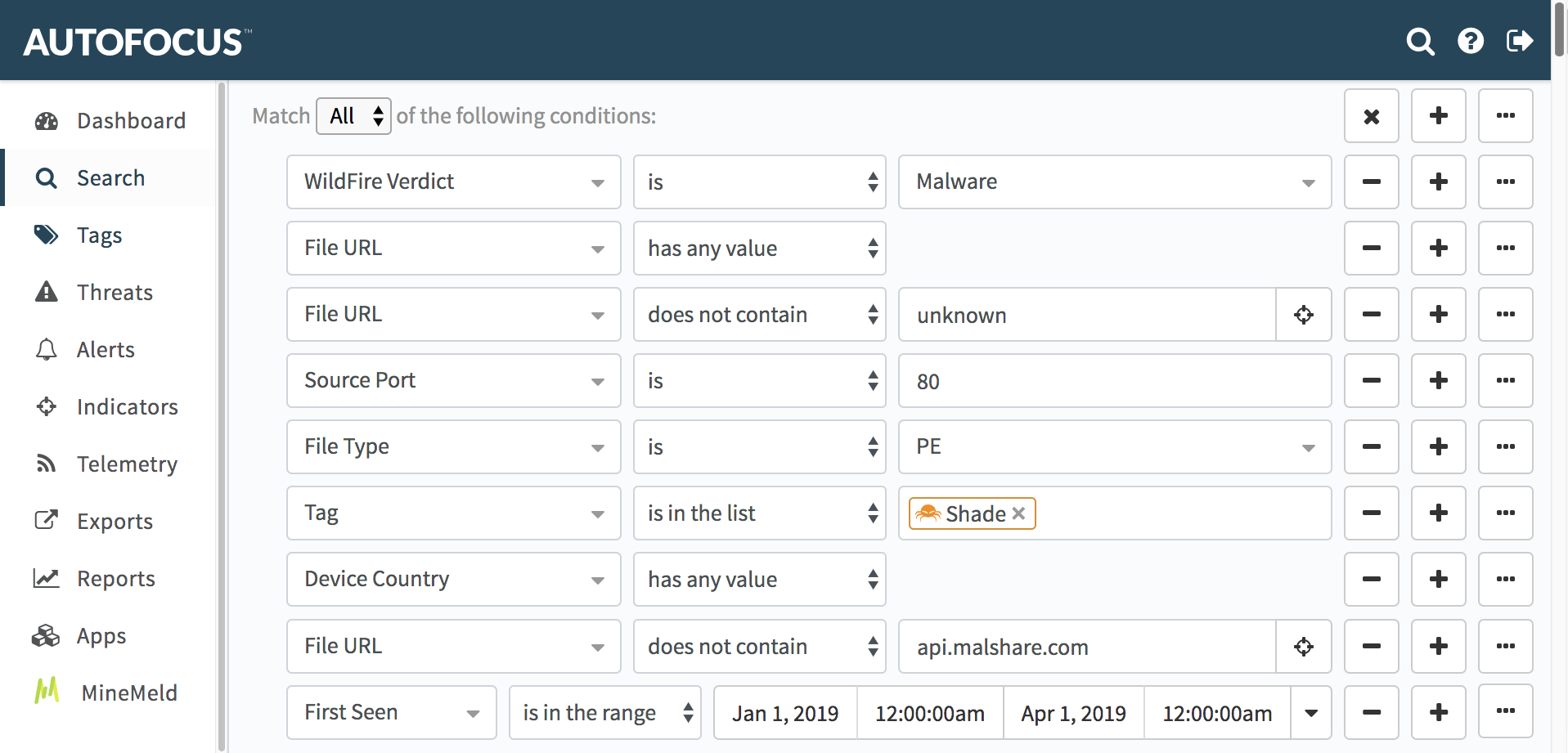
AutoFocus search parameters
AutoFocus has a Shade ransomware tag that identifies any items associated with Shade ransomware. We searched on attempted deliveries of a Shade ransomware executable during an infection chain, and we focused our search on packed executable (PE) files sent through a URL over TCP port 80.
Since we're trying to determine geographic locations among our customer base where Shade ransomware attempts have happened, we looked for the country of Palo Alto Networks devices that discovered these attempts.
This search is for the first quarter of 2019.
Finally, our query eliminated any obvious malware submissions to online sandboxes and online sharing services. Our search parameters from the AutoFocus database were:
- Date is in the range from January 1st through March 31st
- Unit 42 tag is for Shade ransomware
- File type is PE
- File URL has any value but is not unknown
- Source port (the TCP port the file came from) is 80
- Device Country has any value (is not blank or unidentified)
- File URL does not contain the string /malware/
- File URL does not contain the string malshare.com
- File URL does not contain the string paloaltonetworks
- File URL does not contain the string local
Figure 5. An AutoFocus query for Shade ransomware executables in the first quarter of 2019.
Results from January through March 2019
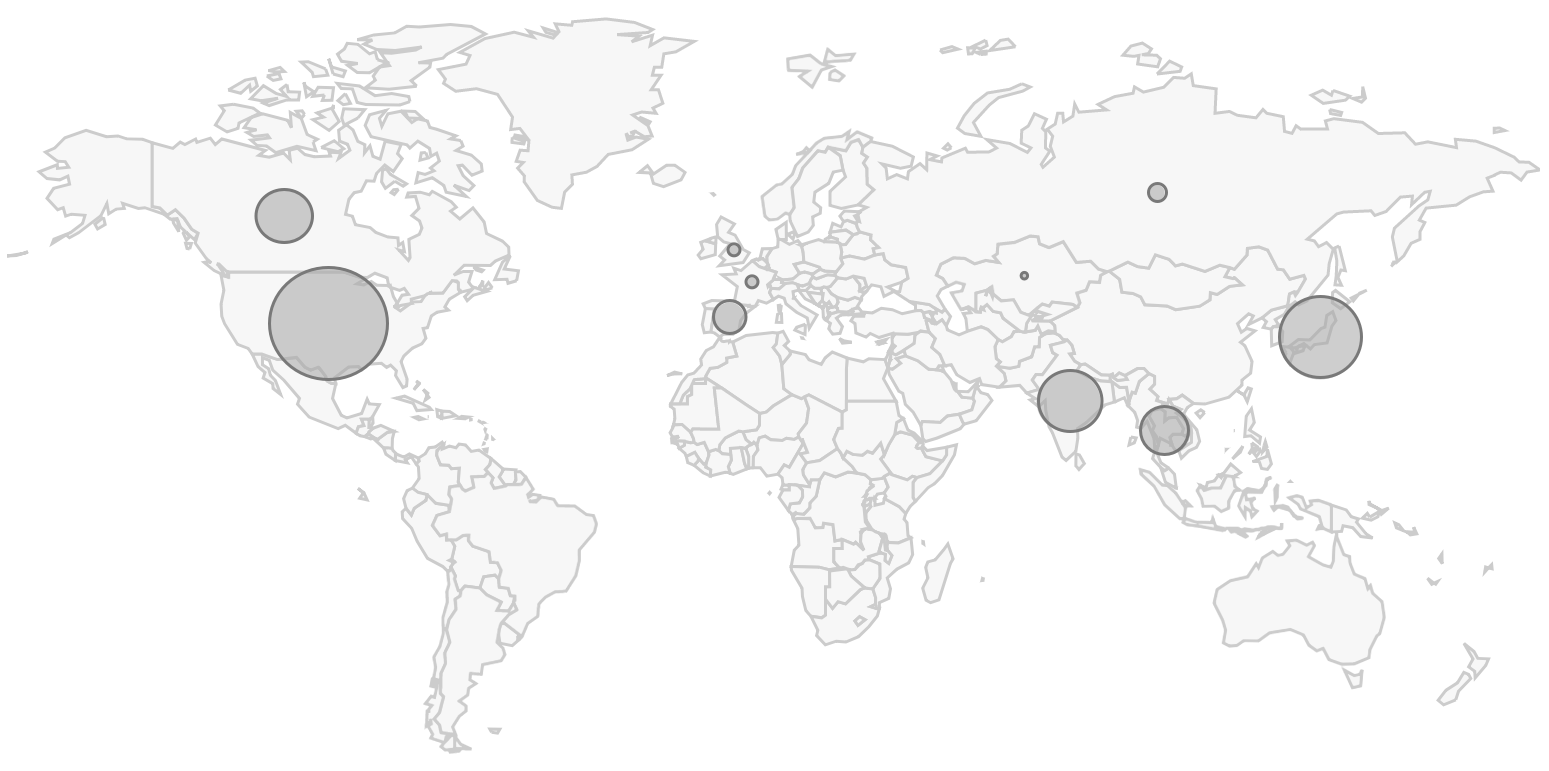
Our search results from January through March 2019 revealed 307 Shade ransomware samples over 6,536 sessions. Each session represents an HTTP request for a URL hosting a Shade ransomware executable. Many of these URLs were seen multiple times in separate sessions. Locations of our top ten results were:
- United States - 2,010 sessions
- Japan - 1,677 sessions
- India - 989 sessions
- Thailand - 723 sessions
- Canada - 712 sessions
- Spain - 505 sessions
- Russian Federation - 86 sessions
- France - 71 sessions
- United Kingdom - 67 sessions
- Kazakhstan - 21 sessions
Figure 6. Top ten countries from our AutoFocus search results as shown on a world map.
The top country with Shade ransomware infection attempts among our customer base was the United States. The vast majority of these for URLs hosting Shade ransomware executables were reported from customer devices outside of Russia and Russian language countries.
The top 10 verticals for this period were:
- High Tech: 5,009 sessions
- Wholesale and Retail: 722 sessions
- Education: 720 sessions
- Telecommunications: 311 sessions
- Finance: 51 sessions
- Transportation and Logistics: 24 sessions
- Manufacturing: 32 sessions
- Professional and Legal Services: 8 sessions
- Utilities and Energy: 4 sessions
- State and Local Government: 1 session
Conclusion
The top country with Shade ransomware infection attempts among our customer base was the United States. The vast majority of these for URLs hosting Shade ransomware executables were reported from customer devices outside of Russia and Russian language countries.
The most common target for Shade ransomware infection attempts were organizations that fell under the High Tech category.
These results are likely skewed towards English due to our customer base. However, they indicate Shade ransomware is very active outside of Russia and possibly targeting more English-speaking victims than Russian.
Palo Alto Networks customers are protected from Shade ransomware by our threat prevention platform which easily detects these executables. AutoFocus users can track Shade ransomware attempts by using the Shade tag. See the appendices below for details on recent Shade ransomware samples we discovered in March and April 2019.
Appendix A
73 recent SHA256 file hashes for Shade ransomware executable files found in March and April 2019. Information is available at: https://github.com/pan-unit42/iocs/blob/master/Shade_ransomware/Shade-ransomware-SHA256-hashes-March-and-April-2019.txt
Appendix B
203 recent URLs that returned Shade ransomware executable files in March and April 2019. Information is available at: https://github.com/pan-unit42/iocs/blob/master/Shade_ransomware/Shade-ransomware-URLs-March-and-April-2019.txt









 Get updates from Unit 42
Get updates from Unit 42