Executive Summary
Update: As of August 23, over the last three weeks this incident has developed with three additional vulnerabilities discovered in Ivanti products. The first in MobileIron Core (CVE-2023-35082; the main topic of this threat brief post when first published in July), a second vulnerability discovered in the Ivanti Avalanche product (CVE-2023-32560), and the third in the Ivanti Sentry product (CVE-2023-38035).
On July 24, 2023, Ivanti Endpoint Manager Mobile (EPMM), previously known as MobileIron Core, publicly disclosed details about an unauthenticated API access zero-day vulnerability. CVE-2023-35078 affects versions 11.10, 11.9 and 11.8, but older versions are also at risk of possible exploitation.
At the time of writing, the only confirmed victims have been Norwegian government agencies. They confirmed their government ministries had been targeted in a cyberattack exploiting this vulnerability, but given the number of potentially vulnerable servers on the internet running this software, it's highly likely that other organizations will or already have fallen victim. Open source reporting indicates that these attacks most likely occurred prior to Ivanti knowing about the vulnerability.
As of July 24, data from our active attack surface management solution, Cortex Xpanse discovered over 5,500 Ivanti Endpoint Manager Mobile servers, spanning multiple versions, were publicly exposed on the internet. The highest number of these exposures were found in Germany, the United States and the United Kingdom.
The regional statistics from this scanning indicate over 80% of these servers reside in western countries and span multiple industry sectors including the following among many others:
- Local and national government departments
- Healthcare organizations
- Law firms and other legal entities
- Universities
- Banks and financial institutions
- Charities
- Retail
Update: As of August 23, Unit 42 Xpanse data indicates a fairly consistent total number of Ivanti MobileIron servers on the internet compared to the same analysis three weeks ago. Also noted are hundreds of IP addresses previously showing older, vulnerable versions now with updated versions that should mitigate the known vulnerabilities. However, we also note many internet IP addresses today still serving Ivanti MobileIron and related services reporting potentially vulnerable, not to mention unsupported, versions.
This vulnerability allows unauthenticated users full API access through specific API endpoints. According to the CISA advisory, with this access malicious actors can extract personally identifiable information (PII) and perform administrative actions, like creating new accounts and making configuration changes, without needing any credentials.
Given the global reach of this incident, and the fact that the vulnerability has already been exploited in the wild, organizations should investigate exposures on their network, and remediate as quickly as possible, using the Ivanti-provided product upgrades.
Since the discovery of the Critical vulnerability CVE-2023-35078, another vulnerability with a High CVSS classification has also been reported within the Ivanti Endpoint Manager Mobile application. CVE-2023-35081 is a remote file write vulnerability that requires an authenticated administrator to write files to the compromised server, which could include additional payloads providing further access.
Update: As of August 23, in the past three weeks three additional vulnerabilities in Ivanti products have been announced, as follows:
- CVE-2023-35082 allows an attacker remote, unauthenticated API access in MobileIron Core 11.2 and older. This is similar to the original vulnerability in the set – CVE-2023-35078 – but covers some of the older versions of the product.
- CVE-2023-32560 allows an attacker to remotely exploit the Ivanti Avalanche software without authentication which could lead to execution of arbitrary code on the vulnerable system.
- CVE-2023-38035 is currently being exploited in the wild allowing attackers, via an API authentication bypass vulnerability in the Ivanti Sentry product, to gain access to sensitive admin portal configuration APIs.
Unit 42 recommends that users of the affected software upgrade to the latest versions that include fixes for the vulnerability. It’s especially important to review your network topology to ensure that any public-facing Ivanti Endpoint Manager Mobile services are up-to-date with the latest patch.
For those who can’t upgrade to fixed versions of the software, we also recommend taking precautionary measures to control access to vulnerable servers, and considering restricting access to the public until they can be patched.
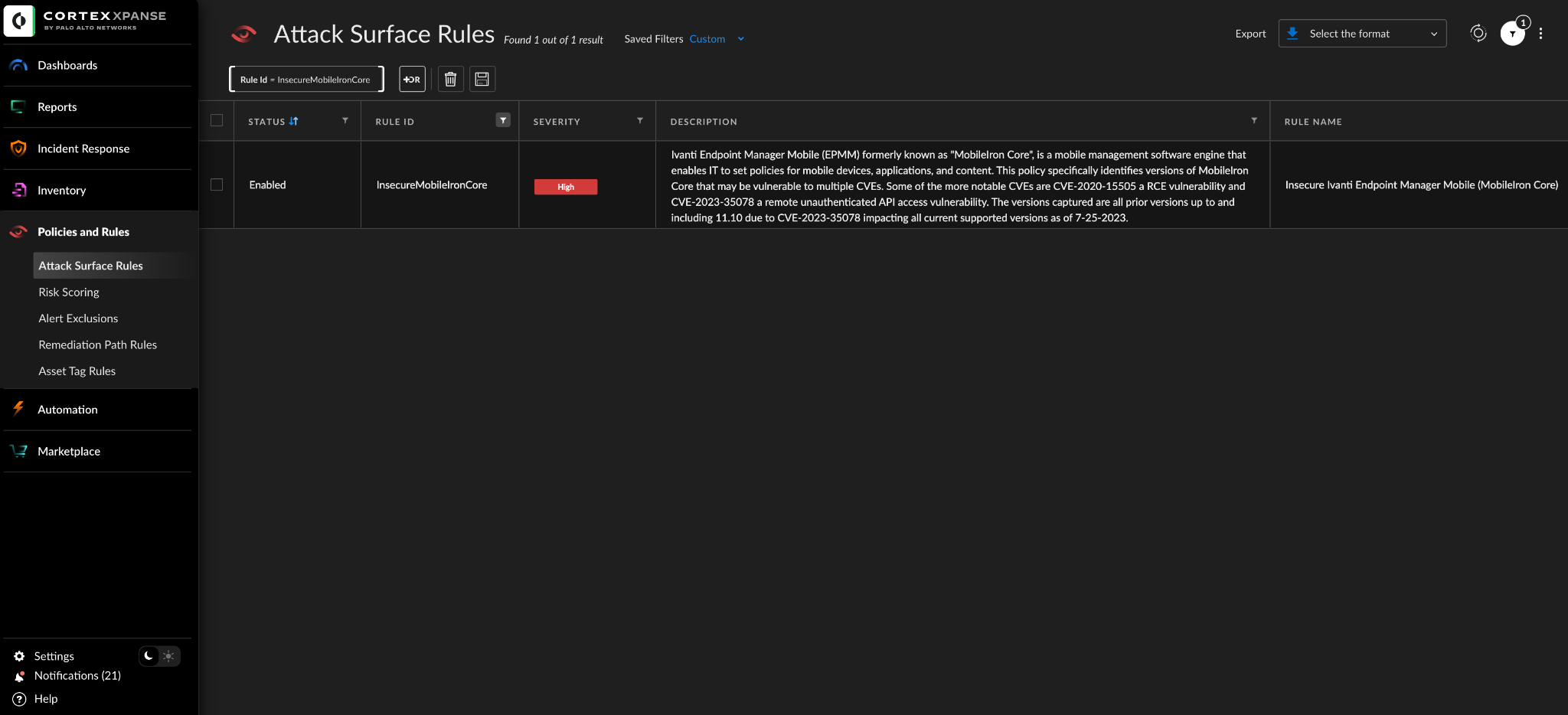
Cortex Xpanse customers can identify external facing instances of the application through the “Insecure Ivanti Endpoint Manager Mobile (MobileIron Core)” attack surface rule.
The timeline below provides an overview of the situation to-date.
| Event | Public announcement (discovery or disclosure) | Details |
| CVE-2023-35078 | July 24 | Allows unauthorized users to access restricted functionality or resources of the application without proper authentication |
| CVE-2023-35081 | July 28 | Attacker can write arbitrary files onto the appliance |
| CVE-2023-35082 | August 2 | Unauthorized users could access restricted functionality or resources of application without proper authentication |
| CVE-2023-32560 | August 16 | Unauthenticated stack-based buffer overflows |
| CVE-2023-38035 | August 21 | Enables an unauthenticated actor to access some sensitive APIs that are used to configure Ivanti Sentry on the administrator portal (commonly, MICS) |
Table 1. Timeline of discovery of CVEs. Source of details column: Ivanti.
| Vulnerabilities Discussed | CVE-2023-35078, CVE-2023-35081, CVE-2023-35082, CVE-2023-32560, CVE-2023-38035 |
Details of the Vulnerability: CVE-2023-35078
Of the 5,500 Ivanti Endpoint Manager Mobile servers discovered through Palo Alto Networks Cortex Xpanse data, Figure 1 below shows a subset of those servers that we were able to obtain a product version for, and the count of said version. The Ivanti-supported version numbers are mentioned above. However, as you can see in the figure below, there are many other, older, unsupported versions still publicly exposed on the internet.
Just under a quarter of the servers we could obtain version information for were supported and, despite the partial information, that pattern is quite concerning. This is an important point to make: Software, especially when it’s internet-facing, should be protected and kept up to date.
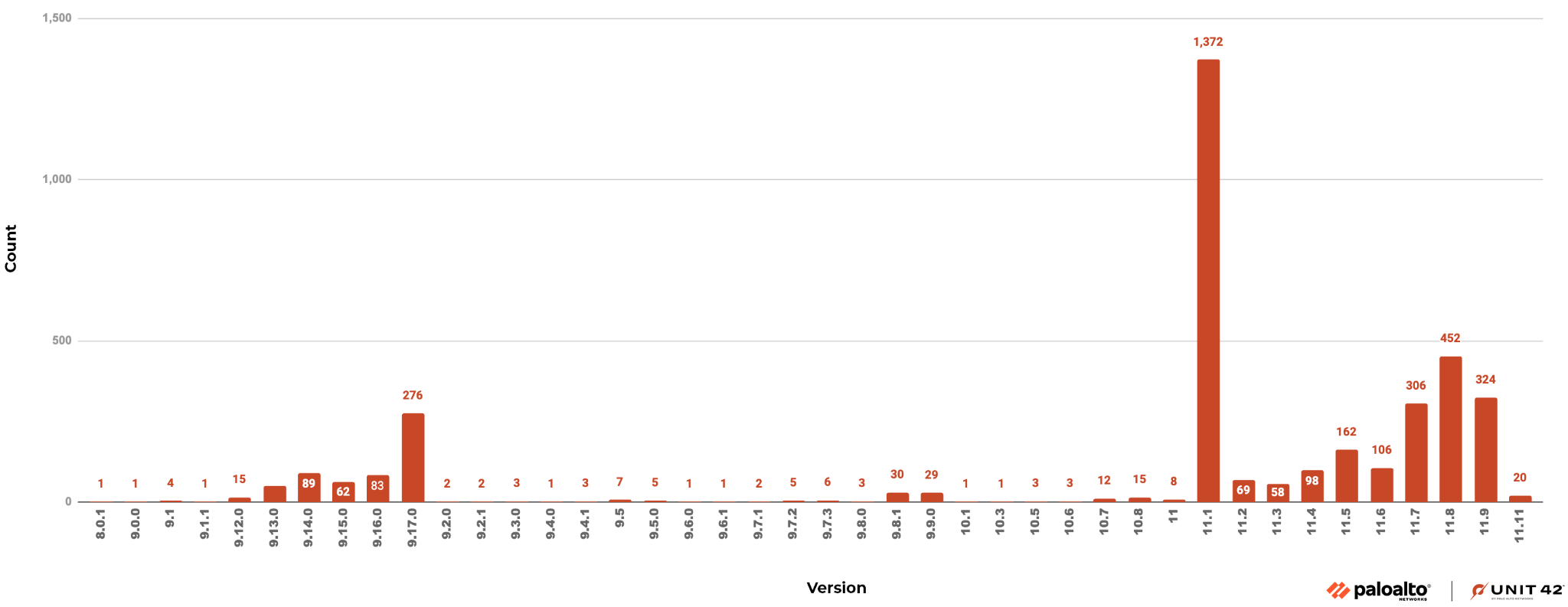
The vulnerability has received a CVSS v.3.0 base score of 10.0, the highest rating possible, and a severity of Critical.
Given the ease of exploitation to the internet-facing application's API, provided as default by each organization running the affected software, there is no so-called proof of concept code required to exploit the vulnerability. It is, unfortunately, as simple as interacting with the system's API using commands (many of which are documented and publically available) to perform various actions within the victim's environment. As described by CISA, such commands can extract PII and perform administrative actions, like creating new accounts and making configuration changes, without needing any credentials.
Details of the Vulnerability: CVE-2023-35081
On July 28, 2023, another vulnerability with a High CVSS classification was reported within the Ivanti Endpoint Manager Mobile application. CVE-2023-35081 is a remote file write vulnerability that requires an authenticated administrator to write files to the compromised server, which could include additional payloads providing further access.
According to Ivanti, there are reports of victims impacted by the new vulnerability used in conjunction with the original vulnerability. The original provides unauthenticated access while the second provides additional capabilities.
This news is somewhat reminiscent of the recent MOVEit vulnerability where, in the weeks following the discovery, both the vendor and security researchers had uncovered additional vulnerabilities perhaps due to the focus drawn by the initial findings.
Current Scope of the Attack: CVE-2023-35078
As Ivanti's public notification about CVE-2023-35078 in their forums states, "If exploited, this vulnerability enables an unauthorized, remote (internet-facing) actor to potentially access users’ personally identifiable information and make limited changes to the server." Furthermore, Ivanti stated they were aware of a very limited number of customers that have been impacted.
Our research shows that a total of 85 countries hosted the 5,500 Ivanti Endpoint Manager Mobile servers on the internet. A dozen or so countries had a single server present at the time of our scan, but many countries had dozens each, if not hundreds. Germany and the United States both had over 1,000 servers.
Figure 2 shows the breakdown of the top 10 countries hosting the highest number of servers.
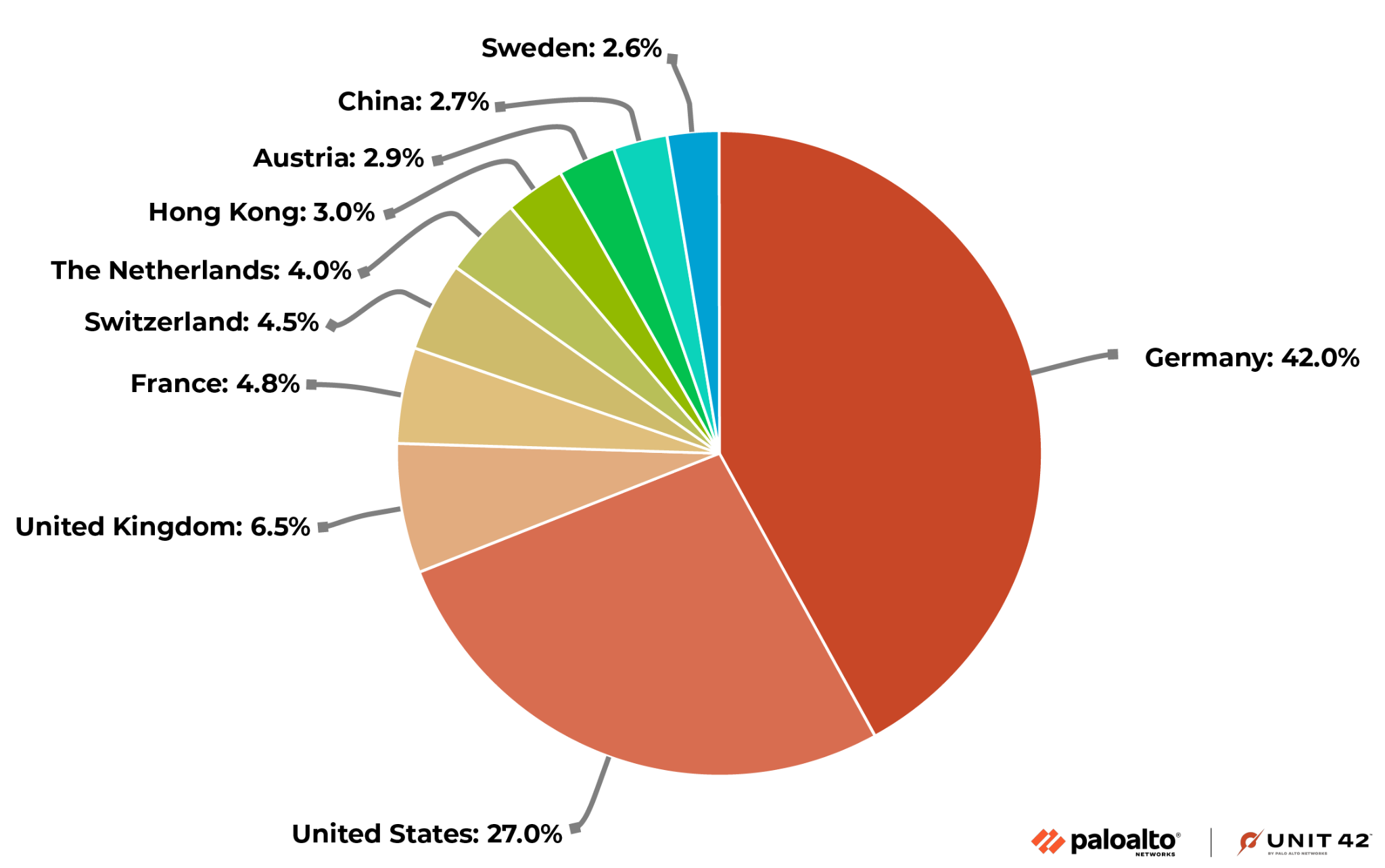
So far, the only publicly confirmed victims are Norwegian authorities and their government ministries. The attack against them was confirmed to be a zero day and later confirmed to be a vulnerability in Ivantis software. However, it's highly likely that other organizations will have fallen victim as well, given the number of potentially vulnerable servers on the internet running this software.
Interim Guidance
Ivanti recommends for users of their software to upgrade to the latest versions that include fixes for the vulnerability.
Unit 42 recommends reviewing your network topology to ensure that any public-facing Ivanti Endpoint Manager Mobile services are up-to-date with the latest patch. If not, consider restricting access to the public until they can be patched.
Conclusion
Based on the amount of publicly available information, the ease of use and the extreme effectiveness of the exploit for CVE-2023-35078, Palo Alto Networks highly recommends following Ivanti's guidance to protect your organization. Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information and provide evidence of more widespread exploitation, if and when that occurs.
Network-based, and especially internet-facing, services are popular targets for threat actors to exploit and leverage to gain access into an environment. This has happened in the past with MobileIron, as documented by the UK NCSC describing nation-state actors using CVE-2020-15505 to compromise the networks of UK organizations.
The recent news of another vulnerability — CVE-2023-35081 — in the Ivanti Endpoint Manager Mobile application, providing a remote file write capability to an authenticated administrator came quickly after the original vulnerability disclosure. As was seen with the MOVEit vulnerability over the last couple of months, once a significant vulnerability is identified within a piece of software, attention is drawn for security researchers, threat actors and the software vendor in an attempt to uncover additional issues for different motivations.
We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for CVE-2023-35078
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Cortex Xpanse
Cortex Xpanse customers can identify external facing instances of the application through the “Insecure Ivanti Endpoint Manager Mobile (MobileIron Core)” attack surface rule. The rule is available to all customers with a default state of “On.”
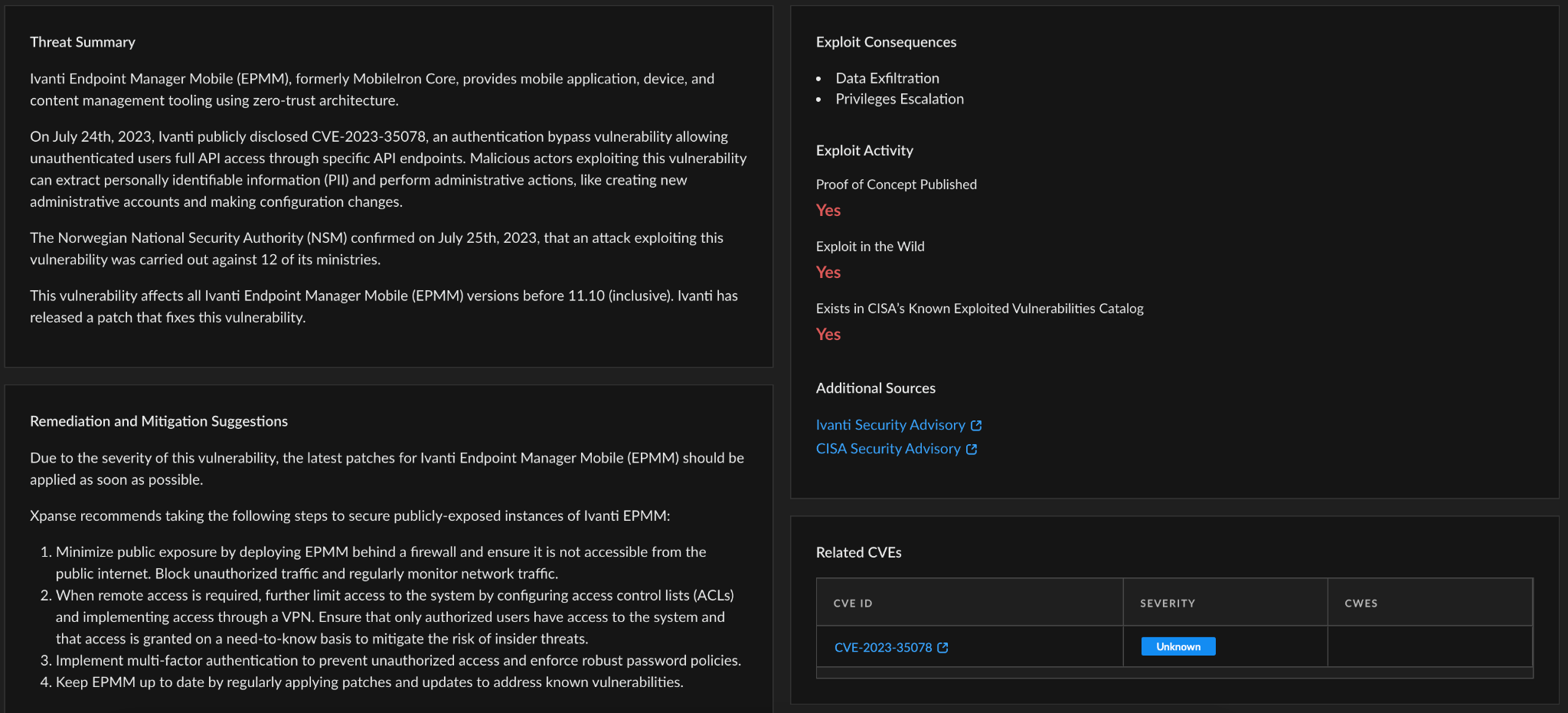
Within Cortex Xpanse’s Threat Response Center, organizations can also find curated threat intel summaries, exploit consequences, previous exploit activity and links to other sources for additional information. This allows you to see how risk is distributed across your organization and build a remediation plan based on the guidance provided. Cortex Xpanse identifies service owners automatically, so organizations can easily assign a ticket to the right person.
Additional References
- Don’t Let Your Ivanti Exposures Go Unpatched Blog, Palo Alto Networks
- Nulldagssårbarhet i Ivanti Endpoint Manager (MobileIron Core) – NSM
- MobileIrony backdoor allows complete takeover of mobile security product and endpoints – Kevin Beaumont, DoublePulsar
- Norwegian government IT systems hacked using zero-day flaw – Bleeping Computer
- Ivanti patches MobileIron zero-day bug exploited in attacks – Bleeping Computer
- Ivanti Releases Security Updates for Endpoint Manager Mobile (EPMM) CVE-2023-35078 – CISA
- Exploit Public-Facing Application, Technique T1190 - Enterprise – MITRE ATT&CK
Previous vulnerability:
- Social Media: how to use it safely – NCSC
- Top 30 Critical Security Vulnerabilities Most Exploited by Hackers – The Hacker News
Updated August 23, 2023, at 11:21 a.m. PT to include three new CVEs affecting Ivanti and a timeline of their discovery.












 Get updates from Unit 42
Get updates from Unit 42