This post is also available in: 日本語 (Japanese)
Over the past month, Palo Alto Networks has observed two spam campaigns targeting users residing in Italy. The spam emails attempt to install the pervasive Andromeda malware onto victim machines. This malware has been around since 2011 and shows no signs of stopping. Compromised hosts cause a victim’s machine to be attached to the Andromeda botnet, giving attackers the ability to push plugins or additional malware onto these machines.
Overview
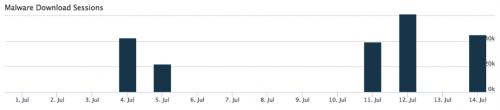
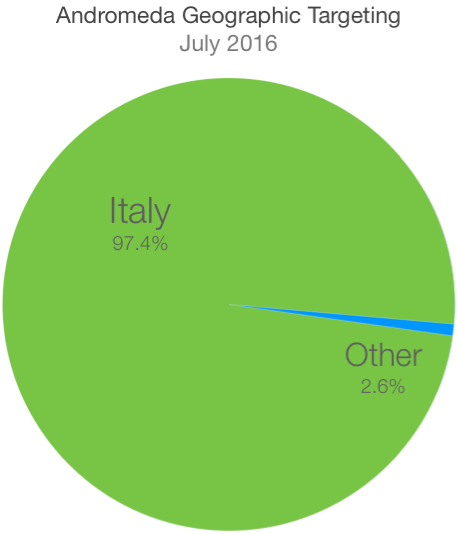
Palo Alto Networks has observed two distinct campaigns that have resulted in approximately 210,000 emails. Of those 210,000 emails, 97% were sent to users in Italy. As shown in Figure 1, AutoFocus has tracked two distinct spam campaigns delivering Andromeda in the month of July.
Figure 1 Andromeda spam emails in July 2016
The geographic distribution of countries targeted during these campaigns is visualized below:
Figure 2 Geographic distribution of Andromeda spam campaigns in July
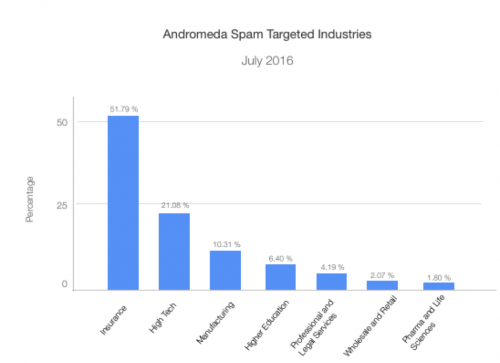
These particular campaigns have primarily targeted the insurance and high tech industries, as shown in Figure 3.
Figure 3 Industries targeted by Andromeda spam campaigns in July
Palo Alto Networks observed the following filenames and email subjects most frequently:
Top Email Subjects
- DOCUMENTO [18.15%]
- invio fattura Noleggio stampante [8.66%]
- Invio Estratto Conto [6.15%]
- Documento aruba.it [4.08%]
- Copia bollettino [4.06%]
- copia del bollettino [4.01%]
- bolla di accompagnamento [3.00%]
- lettera di vettura [2.98%]
- bolletta di carico [2.96%]
- distinta di spedizione [2.94%]
Top Filenames
- 201607051045678890.pdf.exe [18.02%]
- Fattura N 305 Del 04-07-2016.xls.exe [17.30%]
- ft_12072016003.pdf.exe [14.14%]
- 20164805931 aruba.it.pdf.exe [11.74%]
- img-849903872011973.pdf.exe [10.91%]
- 19047-450N-M01-01pdf.PDF.exe [8.37%]
- FAT-E,FAT-B_2016_07.PDF.exe [5.57%]
- -Trasport 904821.pdf.exe [4.65%]
- DOC 2016 ordine.doc.exe [4.43%]
- progetto_85009400941750019201.pdf.exe [3.16%]
Not surprisingly, the majority of the email subjects and filenames observed are in Italian. An Italian-based hosting provider, Aruba, is referenced both in email subjects as well as filenames. When viewing the top email senders, we see further evidence that spammers are most likely posing as Aruba in an attempt to entice victims into opening up the attached files. The emails below are almost certainly spoofed, and it’s highly unlikely that Aruba is sending out these emails.
Top Email Senders
- comunicazioni.it@staff.aruba.it [6.11%]
- comunicazioni_aruba@staff.aruba.it [6.06%]
- prolines@proline.aruba.it [2.21%]
- prolines@aruba.it [2.17%]
- prolinearuba_proline@proline.aruba.it [2.15%]
- prolinearuba_proline@aruba.it [2.14%]
- info@alice.it [1.10%]
- info@tiscali.it [1.10%]
- info@libero.it [1.05%]
- info@virgilio.it [1.04%]
The abundance of Italian-based domain names witnessed are as expected due to the high volume of spam emails being sent to Italy.
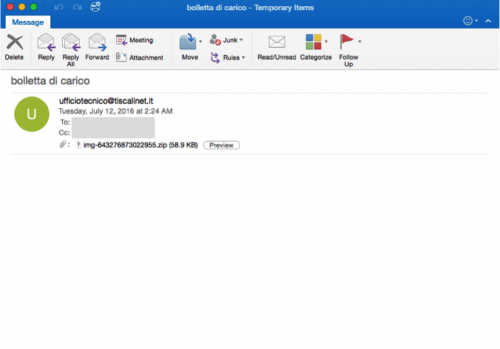
The example email in Figure 4 was obtained via a third party, and demonstrates what an email from this campaign may look like. As we can see, this specific email has no message body.
Figure 4 Example email from Andromeda spam campaign
Andromeda
The Andromeda botnet, which surfaced in 2011, has been discussed at great length by other researchers. Readers are encouraged to reference the following articles to better understand the inner workings of this malware family and its infrastructure.
- Andromeda under the microscope
- The Andromeda/Gamarue botnet is on the rise again
- Andromeda Botnet Hides Behind AutoIT
- Andromeda – An attack kill chain analysis
Overall, Andromeda is very modular, and has been responsible for deploying other popular malware families in the past. In previous years, Andromeda was responsible for delivering a number of point of sale (POS) malware families, such as GamaPOS. Additionally, some of the modules loaded by Andromeda perform the following functionality:
- Keylogging
- Rootkit
- Browser Formgrabber
- Hidden Remote Access
Conclusion
All users should be aware of the Andromeda threat and take the necessary actions to stay protected, especially users in Italy. Users are encouraged to be suspicious of unsolicited emails, and look to ensure that the message sender is legitimate. Additionally, executables provided in email attachments should rarely, if ever, be opened, including those wrapped within a compressed ZIP file.
Palo Alto Networks customers are protected against this threat in the following ways:
An AutoFocus tag exists for the tracking and identification of this malware family.
- All samples encountered within this campaign are correctly identified as malicious by WildFire.
- An IPS rule (Andromeda.Gen Command and Control Traffic) identifies Andromeda-related network traffic.
Appendix
SHA256 Hashes
e3eeccbb66a7aedc7bfc9006d8a42a4b79ce0677d6be2d2e6bd480dea2d26852
1f4295448d294cf2a154e9df31d5ce1f9bde8a9aa560fe33396c5a66beb0da87
5f344ae4e45a61a3b9f22a5019fd0a0df4b6388a5aadaa18dbe7e576a9212ef5
f144e5a238964c803719aa7928fa86958d94bab5a6be3777ac068d6d872c3ffb
4c519dc75e7f12cdbd7b2a9a378a4a370ade42dd34e2b4d57c72ba9c7c8ee80a
7904410713542907d98409a64778d98db3c195ee1a4c712a136211c1c02a27ec
be89fbbcbc98cb7cf54223c1a06bc59134e5f82e83fc577618fc6c6fdcf3129c
6afafa23a357226c7c87854eefe03d82556944ef7319aac0897cca1e9bad4f86
bd2b323b2ec26be8936839b6b8e2b0874d28e2370371f415a6e8559bfa236dc0
490d3160da50f61a150365bb0719dfb36f1c1c13ab7b80d783d7611450478505
f7a07211fb96425d9cc74eed1e673918177ed155cd9118fcad132d5c994e0c54
6439ca529257f15450606dbd80847cb6f6c4024c2447510bc30e7d29a333355e
833b280f48809d15c81309915399c5325dd68bf83ebc9924aa68c96ec9345e4f
6001bcae5a14acf20e246bf9973af47dfd144c9a27ebc7ed0311b68c2e782cd7
a8620a774c7a22e37a02c5caff85fe2e8f9dcf3b49dd105fcdefc153d4a2828c
ed096a3bdb59308343da3a599d55a593568b86cd88389f9fc054aa009c15a9fd
24f78fb42db6184a9919a66afa59ecb12705b4bf32c97d23b9fa46ff969f3697
47c41b0e320df279f25858c74770182eaccb4126b21147dc2605a3f3505a6e6f
5ab435aff9015ecd2e5f111ff64f6e28ed2f0473322f607a20d851e6413ba43e
9e8b1f4e53d545858709c7a10ca70e766474cc168640bada1c6fb14f38d80e42
c85e6c218e4591d48d19fae9b12db30856da245a28bafc9735e4404b794ca263
f237a91297ac3f1cc730c77edc1090f7b1c8c1d5da0bf4a44411c88e3cbba6db











 Get updates from Unit 42
Get updates from Unit 42