This post is also available in: 日本語 (Japanese)
In 2015, Sucuri published two blog posts, one in March describing a pseudo-Darkleech campaign targeting WordPress sites, and another about its evolution the following December. Sites compromised by this campaign redirected unsuspecting users to an exploit kit (EK). The Sucuri posts describe patterns in the injected script related to this campaign. Since December 2015, patterns associated with pseudo-Darkleech have continued to evolve. Our blog post today will examine these changes.
However, before we look at the recent developments, we should understand how EKs fit into the overall picture and review the history of Darkleech.
Path to an Exploit Kit
An EK is used by criminals to infect unsuspecting users while they are browsing the web. EKs are hosted on servers dedicated to the EK. The EK will check if a user's computer is vulnerable and send the appropriate exploit. That exploit is used by the EK to send malware, execute it as a background process, and infect the user's computer.
This malware is the EK payload. Most payloads are designed to infect computers running Microsoft Windows. Different EKs are available to criminals for this purpose. Notable EKs in recent months include Angler, Neutrino, Nuclear, and Rig.
How are web browsers directed to these EK severs? Since users won’t intentionally view an EK, criminals must establish a path behind-the-scenes. The first step in this process is a compromised website. These compromised websites are legitimate pages with hidden script that initiates a network connection to the EK. This is the most direct path to an EK.
Criminals sometimes use another server as a gate between the compromised website and the EK server. In some cases, you’ll find more than one gate in this path. However, pseudo-Darkleech traffic doesn't appear to rely on gates. From what we can tell, the injected script most often points directly to an EK's landing page.
Enter Darkleech
Darkleech is the name of a campaign that infected thousands of Apache servers starting in 2012. More specifically, Darkleech refers to an Apache module available on the black market that was used for malware distribution. In 2013, many organizations had reported on Darkleech. At the time, servers infected with Darkleech led to Blackhole EK.
Below are examples of injected script from compromised websites running the Darkleech module in July and August 2012.
![]()
Figure 1: Example of injected script from July 2012.
![]()
Figure 2: Example of injected script from August 2012.
Patterns for this injected script remained relatively consistent throughout 2013. But changes were coming. By October 2013, Russian authorities had arrested Paunch, who allegedly created the Blackhole EK. Within a few months, Blackhole EK disappeared from the scene. By early 2014, the same Darkleech pattern was pointing to No-IP.com domains (hopto.org, ddns.net, myftp.biz, serveftp.com, etc). These No-IP domains were either gates to an EK, or they directly hosted EKs like Fiesta.
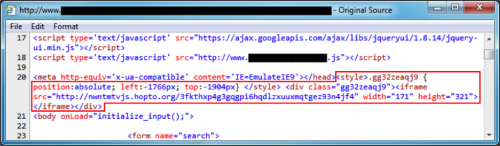
Figure 3: Injected script from March 2014 pointing to Fiesta EK.
![]()
Figure 4: Another example of injected script from November 2014.
Enter Pseudo-Darkleech
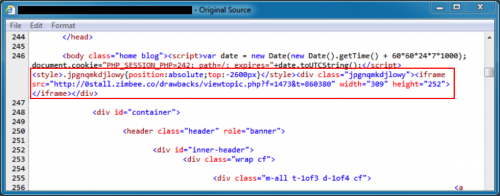
In March of 2015, Sucuri published a blog identifying these newer patterns of injected script from early 2014 as "pseudo-Darkleech." Why use "pseudo" to describe this campaign, especially if the injected script looked the same as before? Because the injected script was now seen from IIS sites, where previously it had only been noticed on Apache servers. As the year progressed, pseudo-Darkleech script was found pointing to Angler EK and delivering ransomware like CryptoWall].
Figure 5: Injected script pointing to an Angler EK landing page in July 2015.
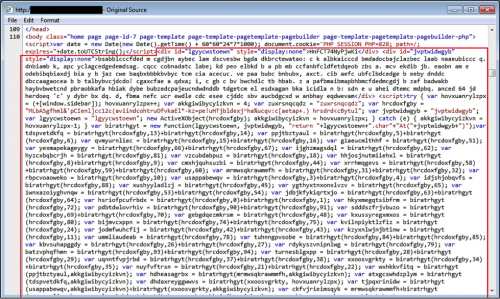
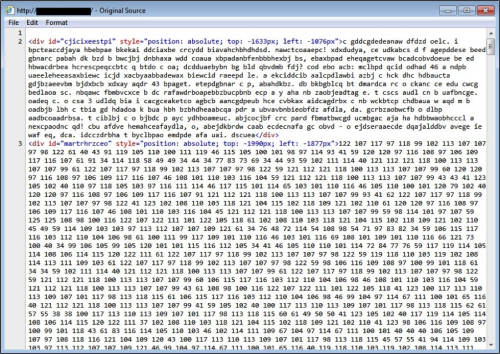
These patterns remained consistent until late September 2015. At that time, injected script caused by pseudo-Darkleech dramatically changed. The script became highly-obfuscated. It looked nothing like previous Darkleech patterns, and you couldn’t easily determine the URL it would generate.
Figure 6: Injected script from September 2015.
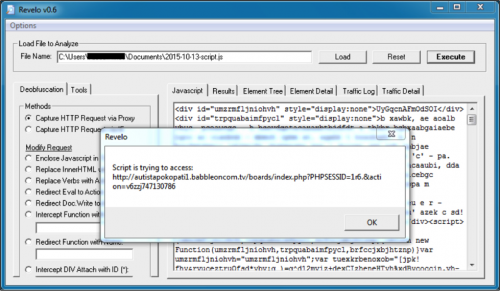
An example of this injected script from October 2015 has been isolated and posted to Pastebin. Using a tool named Revelo from Kahu Security, you can quickly see what the script does. As shown below, the script tries to access a URL, and the URL matches patterns for Angler EK.
Figure 7: Injected script from October 2015 run through Revelo.
Later in 2015, pseudo-Darkleech injected script occasionally switched between Angler EK or Neutrino EK as it delivered ransomware like CryptoWall or TeslaCrypt. By December 2015, Sucuri published a new blog post covering these most recent updates on pseudo-Darkleech injected script. Even with the injected script’s new patterns, Sucuri reported that server-side indicators remained the same as it had reported in March 2015. This activity was still pseudo-Darkleech.
Recent Developments
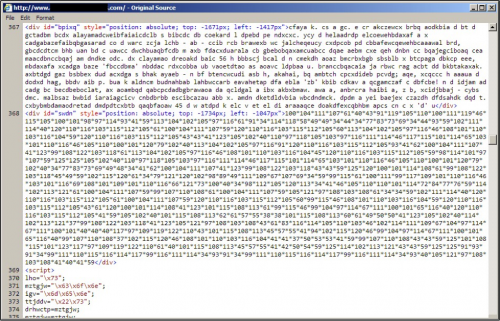
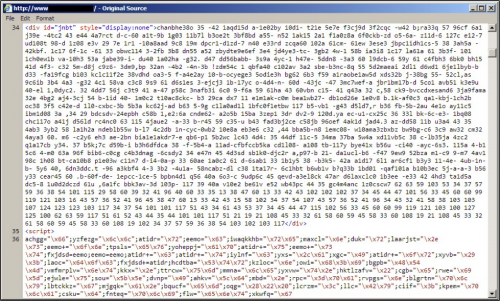
Since September 2015, patterns associated with pseudo-Darkleech have evolved. Any changes were minor until early February 2016, when we saw the addition of a sizable block containing numeric characters in the injected script.
Figure 8: Start of pseudo-Darkleech injected script from early February 2016.
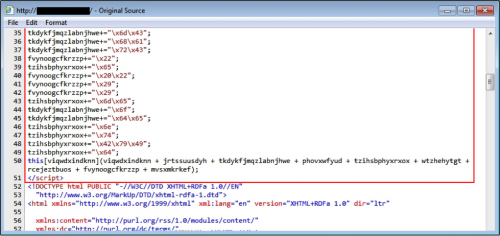
Figure 9: End of pseudo-Darkleech injected script from early February 2016.
Since that time, the characters separating the numbers in that large block of numeric characters have changed. For example, on 2016-02-24 they switched from spaces to commas. By 2016-02-29, pseudo-Darkleech had switched to semicolons. By 2016-03-07, we saw asterisks. On 2016-03-14, the patterns had changed yet again.
Figure 10: Start of pseudo-Darkleech injected script from 2016-03-07.
Figure 11: Start of pseudo-Darkleech injected script from 2016-03-14.
Conclusion
Since it was first called pseudo-Darkleech by Sucuri in March 2015, members of the security community have found websites compromised through this campaign on a daily basis. With tens of thousands of compromised sites reported in 2013 under the original Darkleech banner, pseudo-Darkleech continues the onslaught with no signs of slowing down.
In recent weeks, this campaign has led to Angler EK delivering a ransomware payload, especially TeslaCrypt. Pseudo-Darkleech and the associated Angler EK traffic remain a persistent and evolving threat. Both Darkleech and Angler frequently change patterns to avoid detection. Palo Alto Networks researchers have already examined Angler EK and published an in-depth report containing indicators in January 2016. We continue to investigate pseudo-Darkleech and Angler EK for applicable indicators to inform the community and further enhance our threat prevention platform.
Indicators of Compromise
Domains and IP addresses from websites compromised through this campaign are continually changing. Below are recent examples of the injected script caused by pseudo-Darkleech that have been isolated and posted to Pastebin:
- 2015-10-13 - http://pastebin.com/XCe7ZHz8
- 2015-12-16 - http://pastebin.com/DrUtXgxM
- 2016-02-05 - http://pastebin.com/Knz2bYR0
- 2016-02-24 - http://pastebin.com/K053dSti
- 2016-02-29 - http://pastebin.com/EcHHmu0p
- 2016-03-07 - http://pastebin.com/zmjRguGW
- 2016-03-14 - http://pastebin.com/QWb09vJJ









 Get updates from Unit 42
Get updates from Unit 42