This post is also available in: 日本語 (Japanese)
Unit 42 has recently discovered a new variant of PowerWare, also known as PoshCoder, imitating the popular Locky ransomware family. PoshCoder has been encrypting files with PowerShell since 2014, and the new variant named PowerWare was reported in March 2016. The malware is responsible for encrypting files on a victim’s machine and demanding a ransom via the Bitcoin cryptocurrency.
In addition to using the ‘.locky’ filename extension on encrypted files, this PowerWare variant also uses the same ransom note as the Locky malware family. This is not the first time PowerWare has imitated other malware families, as earlier versions have been known to use the CryptoWall ransom note. Other instances of ransomware have also been known to borrow code from others, such as the TeslaCrypt ransomware family.
Unit 42 has written a Python script that will recursively seek out .locky files on a victim machine and restore them to their original state. The decrypter can be found here.
Analysis
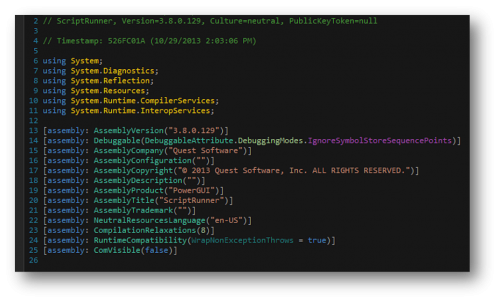
Initial analysis of PowerWare showed that this sample is a .NET executable. After careful inspection of the malware using a .NET decompilation program named dnSpy, we witnessed the word “PowerGUI” from Quest Software. This allowed us to immediately know that the malware was using the PowerShell script editor that converts PowerShell scripts to Microsoft executable files.
Figure 1 PowerGUI referenced within the decompiled malware variant
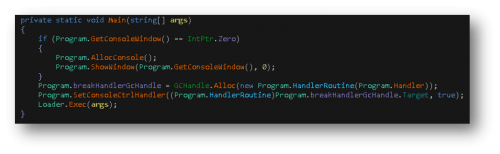
Figure 2 Decompiled Main() function
Upon closer inspection of the .NET executable file, we discovered that it’s using ScriptRunner.dll to unpack a PowerShell script, named fixed.ps1. This unpacked file is dropped to the following location:
%USERPROFILE%\AppData\Local\Temp\Quest Software\PowerGUI\51daca6d-6a9a-44c8-9717-f8cc5c68d10e\fixed.ps1
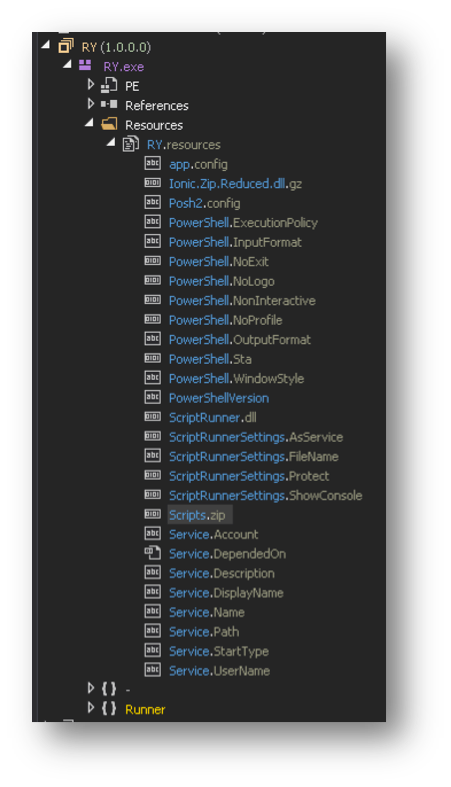
In reality, this .NET Microsoft Windows executable is only responsible for unpacking an embedded script and running it with PowerShell.exe. The script resides inside a ZIP file, named Scripts.zip. This file is located in the resources section of the file as shown in Figure 3.
Figure 3 Scripts.zip embedded within the malware's resource section
As the Scripts.zip file is embedded within the malware without any obfuscation, we can easily extract this ZIP file using dnSpy. This in turn allows us to obtain the compressed PowerShell script within.
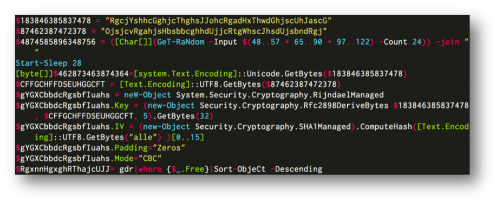
The PowerShell script is very similar to other PoshCoder/PowerWare variants. This sample uses AES-128 encryption with a hard-coded key, which would allow victims to decrypt files without paying, as seen in Figure 4. It doesn’t include a network beacon that tries to transmit randomly generated bytes for the key like some variants have been known to do.
Figure 4 Encryption setup for PowerWare variant
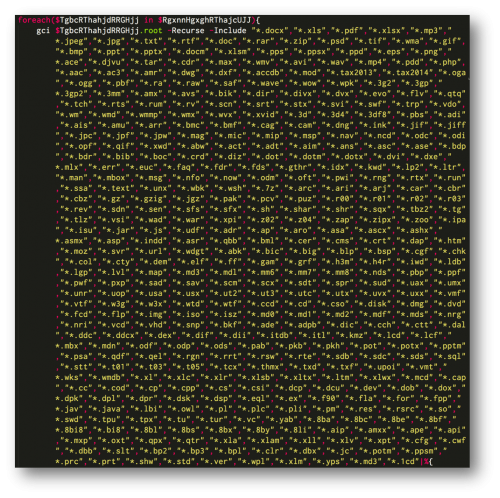
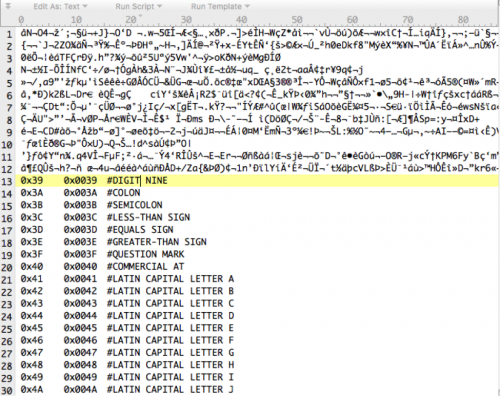
The PowerShell script automatically scans the victim’s machine for files with the extensions listed below and then proceeds to encrypt them.
Figure 5 List of file extensions encrypted by PowerWare
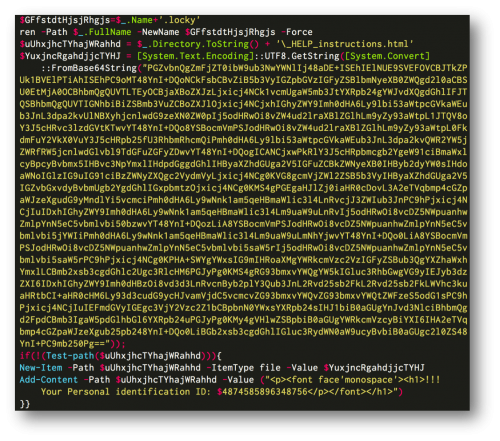
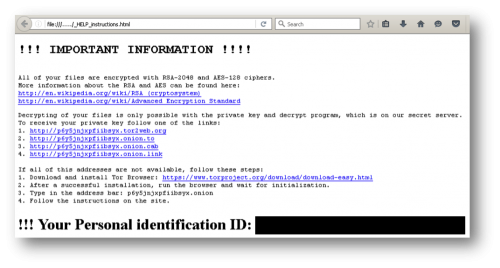
PowerWare then appends the .locky extension to the files it encrypts like the infamous Locky malware. It also writes a HTML file with the name ‘_HELP_instructions.html’, which is identical in wording to the Locky ransomware family. This ransom note is dropped into folders containing encrypted files.
Figure 6 PowerShell code used to mimic the Locky malware family
Figure 7 PowerWare ransom note using same wording as Locky
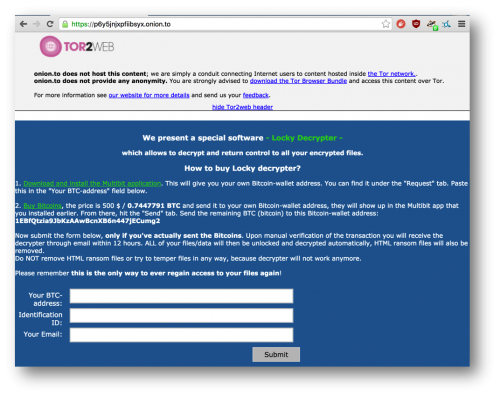
In the event users wish to pay the ransom, they may navigate to a provided website, such as the one below. The site provides instructions on how Bitcoin may be purchased, and once again we see references to the Locky ransomware family, which this variant is clearly mimicking.
Figure 8 Decryption website
Decryption
As mentioned previously, since the malware uses a static key, decryption of victim’s file is possible. The malware actually only encrypts the first 2048 bytes of the targeted files, as witnessed in Figure 9.
Figure 9 Example of a file encrypted with the PowerWare variant
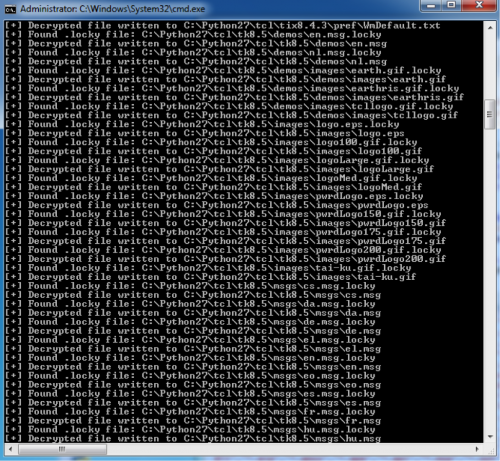
The following screenshot shows an example of the script running on an infected Windows machine.
Figure 10 Decrypter script being executed
It is our hope that this script will assist victims that have been affected by this variant of PowerWare.
Conclusion
While this sample may appear to be new, it is in fact a variant of the previously discovered PowerWare malware family. Unlike other variants, this sample purports to be the Locky malware family.
Palo Alto Networks customers are protected from this threat in the following ways:
- All domains and IP addresses associated with this malware are correctly flagged as malicious.
- All samples encountered within this campaign are correctly identified as malicious by WildFire.
- An AutoFocus tag exists for the tracking and identification of this malware family.
Indicators of Compromise
URLs
hxxp://bobbavice[.]top/RY.exe
hxxp://p6y5jnjxpfiibsyx.tor2web[.]org
hxxp://p6y5jnjxpfiibsyx.onion[.]to
hxxp://p6y5jnjxpfiibsyx.onion[.]cab
hxxp://p6y5jnjxpfiibsyx.onion[.]link
SHA256 Hashes
RY.exe -
7f1023a3d523ab15fe3cceb7fde8038199510703a65dd03d78b9548eb2596b51
Dropped PowerShell
fixed.ps1
cd7ca159f8e8dd057b0591abc2e773d5651a27718eb72e26623e64af859d2826
%USERPROFILE%\AppData\Local\Temp\Quest Software\PowerGUI\51daca6d-6a9a-44c8-9717-f8cc5c68d10e\fixed.ps1
Written Files
_HELP_instructions.html
.locky









 Get updates from Unit 42
Get updates from Unit 42