Summary
In July 2016 Unit 42 analyzed the LuminosityLink Remote Access Tool (RAT) which first appeared in April 2015. LuminosityLink was once a popular, cheap, full-featured commodity RAT. Now, however, LuminosityLink appears to have died – or been killed off – over half a year ago.
We recently noticed that the sites luminosity[.]link and luminosityvpn[.]com had been taken down and were looking into the possibility that it was indeed “dead”, when we saw on February 5, 2018 Europol published a press release that stated “A hacking tool allowing cybercriminals to remotely and surreptitiously gain complete control over a victim’s computer is no longer available as a result of an UK-led operation targeting hackers linked to the Remote Access Trojan (RAT) Luminosity Link.”.
In this blog we look at how LuminosityLink indeed appears to have died, go into some details on LuminosityLink’s prevalence, and discuss LuminosityLink’s capabilities and how they belie claims sometimes made that it was a legitimate tool.
M.I.A.
Up until July 2017, the LuminosityLink RAT software was sold at the website luminosity[.]link (Figure 1).
Figure 1 - luminosity[.]link website
Customers complained that their licensing systems were no longer working (Figure 2).
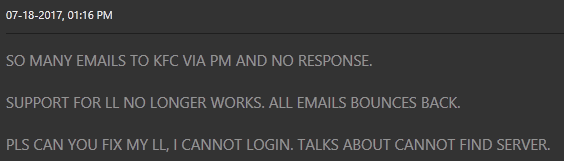
Figure 2 - Customers noticing licensing down
The author of LuminosityLink, “KFC Watermelon”, was indeed keeping a low profile – closing his forum thread selling the software (Figure 3).
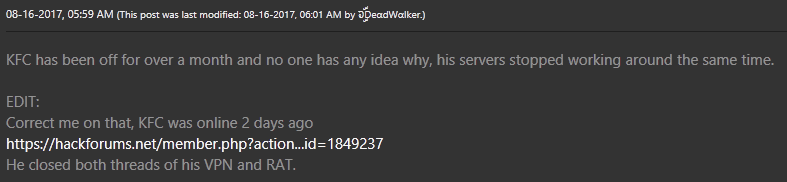
Figure 3 - KFC Watermelon MIA
As shown in Figures 4 and 5, although unrelated to LuminosityLink, the arrest of the author of the Nanocore RAT earlier in 2017 fueled speculation on forums that the LuminosityLink author had also been arrested and may have handed over his customer list.
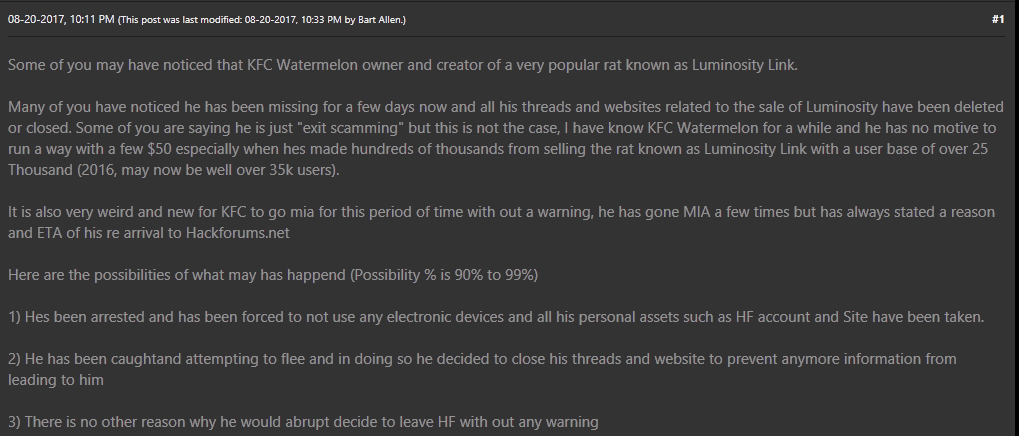
Figure 4 - Speculation
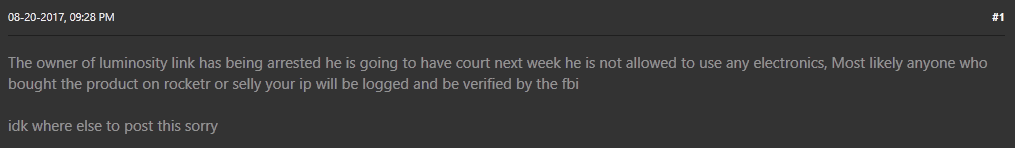
Figure 5 - Arrest
However, even though sales and licensing of LuminosityLink have ceased, despite the rumors, there has been no report of an arrest in the case of the LuminosityLink author to date.
Interestingly, the Europol press release seems to focus upon the users of LuminosityLink, and noticeably omits any mention of the author. Our own investigation into the LuminosityLink author suggests that the individual behind LuminosityLink RAT (and previously Plasma RAT) lives in Kentucky. In light of the fact that “KFC” originally stood for “Kentucky Fried Chicken”, the “KFC” in “KFC Watermelon” may have a deeper significance and not be a random handle.
Prevalence of LuminosityLink
Our oldest sample of this malware dates to mid-April 2015, very shortly after the domain luminosity[.]link was registered. In the just-over two years that this RAT was sold, Palo Alto Networks collected over 43,000 unique LuminosityLink samples through various methods. In total, Palo Alto Networks observed over 72,000 submissions to Wildfire (Figure 6), of over 6000 unique samples, by almost 2500 Palo Alto Networks customers. The most prolific of these individual samples were observed in over 2000 attacks each.
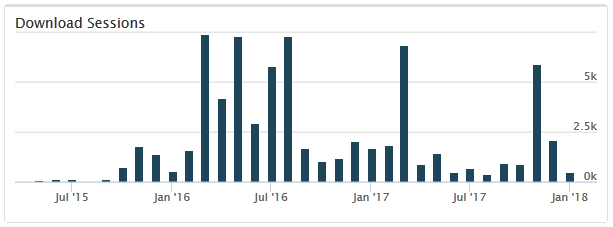
Figure 6 - LuminosityLink Attack Observations
LuminosityLink Command and Control (C2) servers contact the author’s licensing server to verify their legitimacy. We note a sharp drop after July 2017, with the licensing server down, though samples continue to be observed. Although we note a couple of noticeable spikes, the observation of new LuminosityLink samples is on a steady decline. Based on other examples, we believe the continued presence LuminosityLink in the wild, even though it’s no longer under development, may be due to cracked versions of it being in use.
Malware, or legitimate tool?
Customers of these services, users on underground forums, have expressed concern that arrests of RAT authors might lead law enforcement to their own doors (we see similar sentiments echoed by the customers of DDoS “booter” / “stresser” services).
RAT authors and customers alike claim that RATs represent legitimate “administration tools” – despite the fact that the support thread itself is in under “Hacks, Exploits, and Various Discussions » Hacking Tools and Programs”, on a hacking forum (Figure 7).
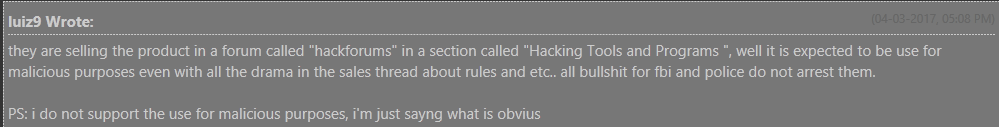
Figure 7 - What is obvious
Further undermining these claims, the help forum on the luminosity[.]link site included an article (Figure 8) about “support regarding a third-party product (VPN, Crypter, etc)” – suggesting that the use of such detection avoidance techniques was in the front of the mind of the author.
“KFC Watermelon” even states as much on forums “I do cater to crypter coders now and are in contact with numerous developers to ensure Luminosity works great while crypted. 1.3.1 is further proof of this.”.
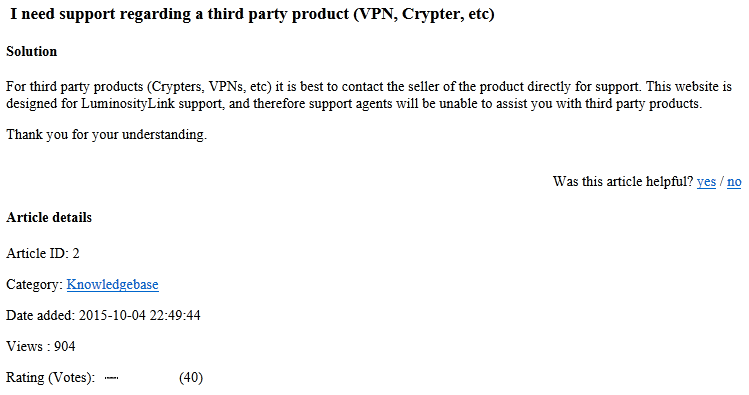
Figure 8 - luminosity[.]link support article
Even more to the point, LuminosityLink boasted feature sets such as “Surveillance: Remote Desktop, Remote Webcam, Remote Microphone”, “Smart Keylogger: Records all Keystrokes, Specify Websites and Programs to Record Separately, Keylogger Viewer, Organized and easy-to-use, Search Keylogs Easily”. These all heavily suggest a purpose other than legitimate remote administration. And other features would seem to have no legitimate purpose at all: “Crypto Currency Miner: Supports Scrypt, SHA256 and More, Custom Miner Support (For Alt Coins), Set amount of CPU to use, Supports CPU and GPU Mining, Proxy Support, Update mining config at anytime” (Figure 9).
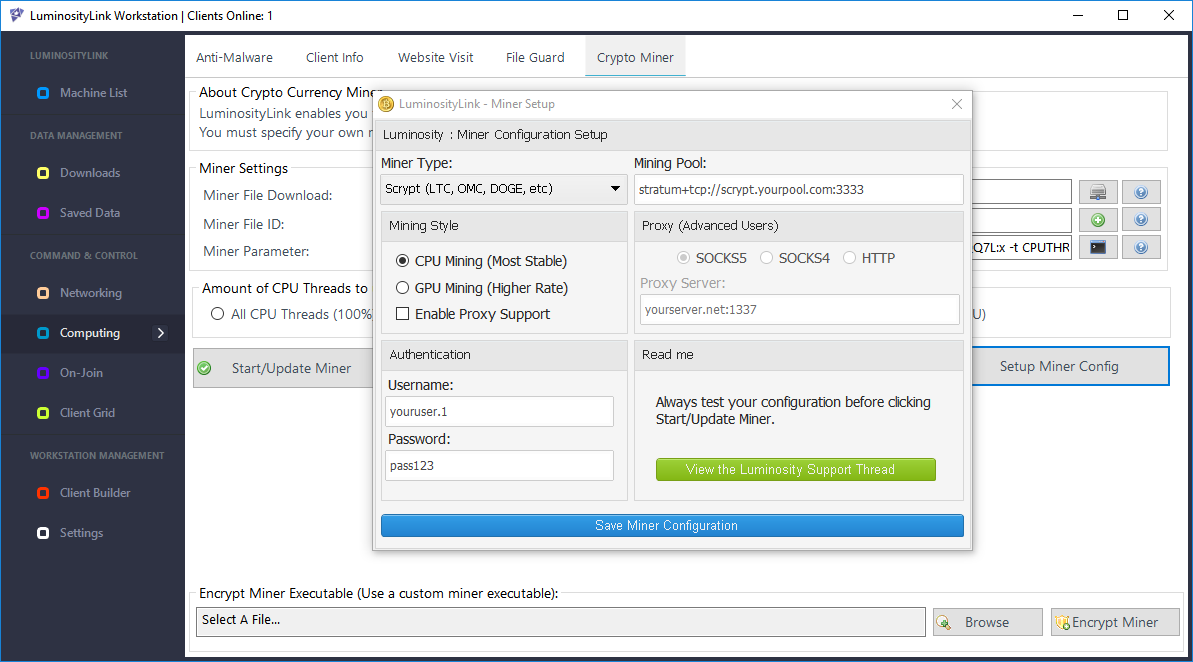
Figure 9 - Coin Miner
It’s also hard to imagine a legitimate-use scenario for launching a DDoS attack (Figure 10):
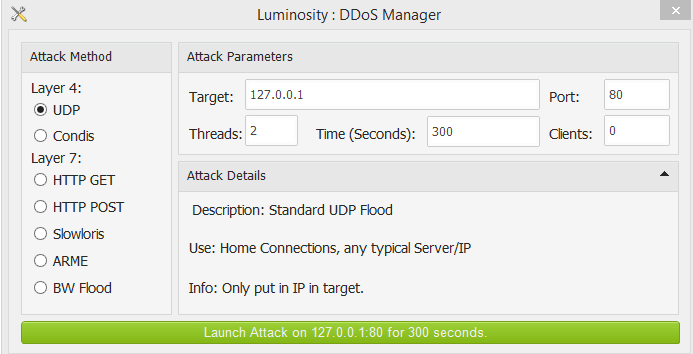
Figure 10 - DDoS feature
Per “KFC Watermelon” himself “I also re-coded the DDoS modules in 1.0.0.1 and made the Layer 7 attacks more effective.”.
Another forum was quite accurately prophetic about the risks the author of LuminosityLink was taking in April 2017, about three months before the site was parked (Figure 11).
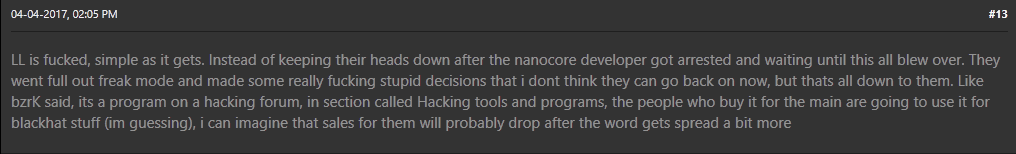
Figure 11 – Forum Comment on Risks LuminosityLink Author Was Taking
Conclusion
Based on our analysis and the recent Europol announcement, it does seem though that LuminosityLink is indeed dead, and we await news of what has indeed happened to the author of this malware. In support of this, we have seen LuminosityLink prevalence drop significantly and we believe any remaining observable instances are likely due to cracked versions.
Finally, a review of most recent feature sets and capabilities for LuminosityLink show that even if some of its capabilities could be put to legitimate purposes, taken as a whole, the preponderance of questionable or outright illegitimate features discredit any claims to legitimacy.
Coverage
Palo Alto Networks customers are protected from this threat in the following ways:
- WildFire accurately identifies LuminosityLink RAT samples as malicious.
- Traps prevents this threat on endpoints, based upon WildFire prevention.
AutoFocus users can view LuminosityLink RAT samples using the “LuminosityLinkRAT” tag.
IOCs can be found in the appendices of this report.
Appendix I – Top 20 samples
| 07b4b11940baa619c0c6ec91b1a73715f4a1ece29ad85287b7db97718a60aea5 | 2260 |
| efdf2238c091f4ff3fa9b2eea8cfa5c9edad70434fc81cba5a81d2b3fe188276 | 2142 |
| 73f7967d53fe124a028311db97b2b1c0a53acffe269c37d20e31f2a4a068ab28 | 1769 |
| 45657413799e9481eff4c83bf183b9343b3f7ed1ecde6724b1a7d2c2c6e4839c | 1260 |
| df5a90d5dac6c3a4286230e0b0d4835ec936b11bbacf6b031b25ff6545ed153e | 1007 |
| 8785ef18b75605bd659a346ec890b4888749c6015b729cd3363fd8289e55faf3 | 959 |
| f3aacd6a47fd6655408507446ff53b946108f29e2a3dc0bb2f496b8e36927ce7 | 890 |
| add98a6912601551634239a6867ea10136fd6cf770cd25eecde576a3853738d8 | 823 |
| c4eee35f0e51a04a7daca1431c4926d02720590ce62200c8362bacc66eb574b1 | 764 |
| 53d817e8a824488a622cf653c9d48164c3d741aa19f2e2d89a713005f81109ef | 751 |
| a3dd71e5bd2d9edad31252d3d6049b5ffb1d6bd11fe6215f9d2c8cf093ba8ab7 | 749 |
| 82151d68ae5ec5e00e81998785371ff694b37bfe6093fe3bd8c9932ed21651c7 | 731 |
| 68a599d2658096ff9c529c5aeb9644119c47e1c744b07323a3df8a8e5e94c4da | 725 |
| 1f79ac7f0201584d6ea7d6b0c96d2285572ed4a191e765a20f5ccae6ebb2f34d | 718 |
| 50349613c6fbac2b344f5b7753a165620be112a674763153a6de497df43589af | 712 |
| 79a6a3c5ae196a1874234f5870fc8c6d07059c85cb1fca73d21c8eb51c0d41b1 | 680 |
| 8329f8176e926053fc9a4db2f9eb09aff6fec31c197e919ae26cb9501926c516 | 674 |
| f8f58cc1095ea29e2c365fa64fdccdebce5113b44e3d7032e96f0ebb3dfd5e9c | 669 |
| 09681a9054f9f04e270b0ae390c7b697748405d4c29a589ff45a4b485baa18c4 | 652 |
| 0247b0ecbf6069e38e772ef546e63c46262cc77efe5d004a3ec516baf0e74d87 | 524 |
Appendix 2 – full sample hash list
A full list of SHA256 hashes for all known LuminosityLink samples, as of 1 February 2018, can be found here.












 Get updates from Unit 42
Get updates from Unit 42