This post is also available in: 日本語 (Japanese)
Situation Summary
This Unit 42 blog provides an update on the threat situation surrounding the WanaCrypt0r ransomware attacks and how the attack propagates.
Initial reports said that the WanaCrypt0r attack began as part of a spam/phishing campaign. Unit 42 and other researchers have concluded that these reports are not substantiated. While the initial attack vector for these attacks is unknown, it is certain that the spread of the ransomware occurs through active exploitation of the ETERNALBLUE vulnerability (CVE-2017-0144) in Microsoft Windows. Patches for this vulnerability for all supported versions of Windows have been available since March 2017. On Friday May 12, 2017, Microsoft took the extraordinary step of releasing patches for out-of-support versions of Windows to help protect against these attacks.
As the attack leverages this Microsoft vulnerability, the most appropriate first step to take against the attack is to apply the patches. Unit 42 researchers have confirmed that the patch is effective against the WanaCrypt0r Ransomware attacks.
In addition, Palo Alto Networks, and other vendors, including our fellow members of the Cyber Threat Alliance, have released additional protections that help prevent the spread of the WanaCrypt0r ransomware. For information on Palo Alto Networks protections, please see our posting Palo Alto Networks Protections Against WanaCrypt0r Ransomware Attacks.
As with all ransomware attacks, Palo Alto Networks and Unit 42 recommends that anyone affected NOT pay the ransom. Unit 42 is not aware of any reports where paying the ransom to the WanaCrypt0r attackers has resulted in the recovery of data. In addition, Unit 42 research has shown that very few have attempted to pay the ransom.
Unit 42 is following this situation very closely and will update this blog with any new information as it becomes available.
Overview
WanaCrypt0r is a global ransomware attack that emerged on Friday, May 12, 2017. It immediately gained broad media attention, due to its destructive nature, how widespread it was, and multiple high profile victims. This attack uses the version 2.0 of this ransomware. WanaCrypt0r v 1.0 was first reported a few months ago but did not include the worm capability associated with this attack.
Reports quickly emerged that this attack was effective due to the presence of code exploiting a vulnerability (CVE-2017-0144) in Microsoft Windows (code named: ETERNALBLUE) that was released as part of the Equation Group dump by the Shadow Brokers in their fifth leak on April 14, 2017. Microsoft patched this vulnerability as part of the March 2017 Monthly Security Update Release by Microsoft Security Bulletin MS17-010. This is a SYSTEM-level remote code execution (RCE) in the handling of the Server Message Block (SMB) protocol in Microsoft Windows.
The attack uses this vulnerability to spread the WanaCrypt0r ransomware on the network. This is a classic network worm-class vulnerability like MS-Blaster and Conficker.
Early reports indicated that the initial attack vector was via spam and/or phishing email. However, this has not been confirmed and is unlikely to account for the global spread of the malware.
When the WanaCrypt0r ransomware executes successfully, it will encrypt key files on the system and display a ransom note as shown below (SOURCE: Microsoft).
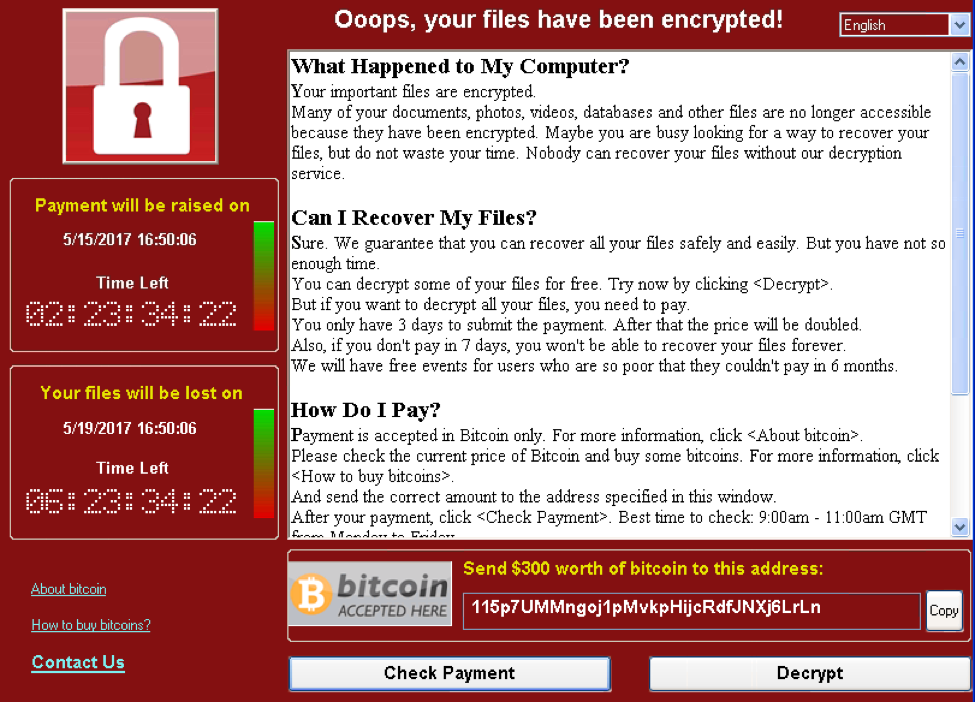
Figure 1 Ransom note for WanaCrypt0r
One thing reports have indicated that make this attack unique is a “killswitch” capability built into the malware. This “killswitch” will prevent the WanaCrypt0r ransomware from executing. The “killswitch” is code which will attempt to connect to an extremely long domain that should not resolve. The initial variant of WanaCrypt0r uses hxxp://iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, however, there are reports of newer variants using different domains. If it was successful in connecting to the domain, the ransomware would not execute. However, it was easily subverted to work against the malware. A security researcher in the United Kingdom initially registered this domain in order to track this threat, and soon discovered that in doing so, he had enabled this “killswitch”, causing a number of instances of WanaCrypt0r to not execute for a large number of infected systems.
On Friday, May 12, 2017, Microsoft announced that they were making an emergency patch available for out-of-support versions of Windows (Windows XP, Windows 8 and Windows Server 2003).
As of this writing attacks appear to have subsided. This is likely due to increased uptake of the patch MS17-010 in light of the WanaCrypt0r attacks, as well as efforts made within the security community.
Unit 42 research shows there is likely very little actual payment of ransom. We analyzed our known WanaCrypt0r samples and extract the following Bitcoin (BTC) addresses likely associated with the attackers and associated totals:
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 - 12.42466618
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw - 11.83101346
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn - 8.74393075
- 1DefE3HEeBaR4EBbAajjHatFzMuPe885Hf - 3.12308549
This results in a total of 36 BTC, or roughly $63k based on the current price of BTC. Given that WanaCrypt0r requests $300 per infected machine, we can infer that approximately 210 victims have made payments to the attackers.
Reconnaissance
This attack does not appear to be targeted. Therefore, there appears to be little recon as part of this attack. There are some reports that there may be scanning of TCP port 445, which is one of the ports associated with SMB. But these reports haven’t been conclusively verified.
Delivery
There is no consensus in the industry on what the delivery method/initial infection vector is. There have been several theories:
- Spam/Phishing: Initial theories suggested that delivery occurred through a spam or phishing email with a link in the body or in an attached Adobe .PDF file and the user could click the link and execute the attacker’s code in their security context to initiate the attack which would then spread on the network by attacking the ETERNALBLUE vulnerability.
- Direct attack against MS17-010: This theory suggests that the attack would establish a beachhead by attacking the ETERNALBLUE vulnerability on Internet-exposed systems and the attack would then spread on the network by attacking the ETERNALBLUE vulnerability from these compromised systems.
- RDP: This theory suggests that the initial attack comes by attacking systems using the Remote Desktop Protocol (RDP) and then the attack which would then spread on the network by attacking the ETERNALBLUE vulnerability from these compromised systems. This theory suggests an attack pattern similar to what Unit 42 outlined in the Shamoon 2 attacks followed by using RDP as the initial delivery method and then attacking the internal network from the compromised RDP system. There are theories suggesting this could be due to brute force attacks against the RDP system, while other theories suggest this could be due to a successful attack against a vulnerability on these RDP systems (theories do not state what vulnerability this could be or where the vulnerability might occur).
Unit 42 believes the most likely delivery method is method #2. However, this is not conclusively provenLateral Movement
Lateral Movement
The WanaCrypt0r ransomware spreads itself by heavily scanning over TCP port 445 (associated with SMB) and attempting to exploit the ETERNALBLUE vulnerability on systems. A successful attack against this vulnerability will infect the target system with the WanaCrypt0r ransomware, which will encrypt data on the target system and attempt to spread itself once again.
Multiple vendors report that the malware includes the ability to spread via port 445 scans and attacks against the ETERNALBLUE vulnerability not only on internal networks but also across the Internet. These reports indicate that in addition to the internal lateral movement already outlined, the WanaCrypt0r ransomware will scan for port 445 on random external IP addresses and if it finds an IP address with an open port 445, it will then scan all devices on the same /24 IP range (i.e. that share the first three octets as that IP address with the open port 445).
Command and Control (C2)
In general, WanaCrypt0r does not have C2 capabilities but it does utilize the TOR network to communicate encryption keys for decryption upon payment of ransom. It has been reported that the DOUBLEPULSAR backdoor (also from the Equation Group leak by Shadow Brokers) is installed and used to execute the malware after successful exploitation of a host via ETERNALBLUE, but this warrants further analysis.
Conclusion
Overall, WanaCrypt0r has been a notable incident within the security community, as the threat couples a wormable vulnerability/exploit with a ransomware family. Users are urged to apply the necessary Microsoft patch to protect themselves against this threat.
For protections, customers are advised to view this blog post that outlines the various ways the Palo Alto Networks platform prevents this threat.
Cyber Threat Alliance member ElevenPaths has developed a tool which can be used to attempt to recover some files deleted by WanaCrypt0r. You can find more information on this tool here.
Register for Ignite ’17 Security Conference
Vancouver, BC June 12–15, 2017
Ignite ’17 Security Conference is a live, four-day conference designed for today’s security professionals. Hear from innovators and experts, gain real-world skills through hands-on sessions and interactive workshops, and find out how breach prevention is changing the security industry. Visit the Ignite website for more information on tracks, workshops and marquee sessions.









 Get updates from Unit 42
Get updates from Unit 42