This post is also available in: 日本語 (Japanese)
On January 31 the Korean CERT published a security advisory regarding a new Adobe Flash Player zero-day vulnerability (CVE-2018-4878) which was observed being exploited in the wild. Adobe released a patch and security bulletin on February 6th to address this vulnerability. The vulnerability is a Use-After-Free (UAF) bug in Adobe tvsdk. The final goal is allegedly to download and execute a malware known as DogCall (aka ROKRAT) – an information stealing backdoor. DogCall is often delivered via malicious Hangul Word Processor (HWP) files, which is a popular application used in South Korea.
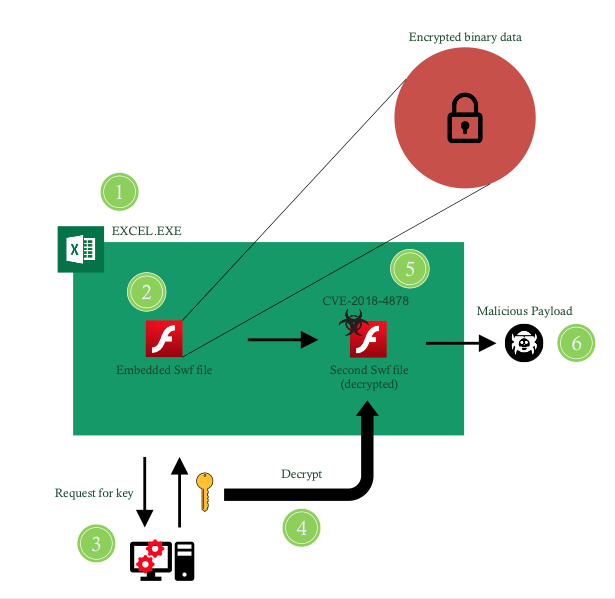
Figure 1 – The attack flow as observed in the malicious sample
In Figure 1 we show the attack flow as observed in the malicious sample. First, the malicious XLS spreadsheet file is opened by the victim. Then, the document executes an embedded Adobe Flash file which contains an encrypted binary data blob. Next, the Adobe Flash file connects to a remote server and requests a decryption key for the binary blob. The binary blob is then decrypted and loaded as a second Adobe Flash file dynamically. This Adobe Flash file is in fact the one that contains the zero-day exploit for CVE-2018-4878. Upon successful exploitation, a shellcode is executed which retrieves and runs the malicious payload.
How Traps prevents this threat
Palo Alto Networks Traps advanced endpoint protection offers multiple methods of malware and exploit prevention to protect against such complex threats. For this threat, Traps prevents the malicious shellcode running in Excel.exe using Traps exploit prevention capabilities. In addition, Traps local analysis via machine learning prevents the malicious payload from executing.
AutoFocus customers can track this activity via the DogCall tag.











 Get updates from Unit 42
Get updates from Unit 42