Linking Vatet, PyXie and Defray777
While researching these malware families, we found that there were several consistencies between Vatet, PyXie and Defray777 that strongly suggest that all three malware families were created, and are currently maintained by, the same financially motivated threat group.
PDB Path Reuse
As we saw with the Defray777 decryptors, there are numerous victims that have been impacted by Defray777. However, these decryptors also show some overlap with PyXie. One of the decryptors we analyzed shares a common path with earlier versions of PyXie and its Cobalt Mode downloader.
| Defray777 Decryptor | Z:\coding\pyproject\compiled\ransom\ransom.pdb |
| PyXie | z:\coding\pyproject\python_static_2.7.15\ |
| Cobalt Mode | Z:\coding\pyproject\compiled\cobalt_mode\cobalt_mode.pdb |
Table 19. PDB paths shared between Defray777, PyXie and Cobalt Mode.
Additionally, some of the variants of Vatet we observed also have overlapping PDB paths.
| Tetris | C:\Users\1\Downloads\tetris-game-master\Release\TetrisGame_zjy.pdb |
| Notepad | C:\Users\1\Downloads\notepad-master\Debug\notepad.pdb |
| Rainmeter | C:\Users\1\Downloads\rainmeter-master\x32-Release\Obj\Library\Rainmeter.pdb |
| Rainmeter | C:\Users\1\Downloads\rainmeter-master\x32-Release\Obj\Application\Rainmeter.pdb |
| Notepad++ | C:\Users\1\Downloads\notepad-plus-plus-master\PowerEditor\bin\npp.pdb |
Table 20. PDB paths shared between Vatet variants.
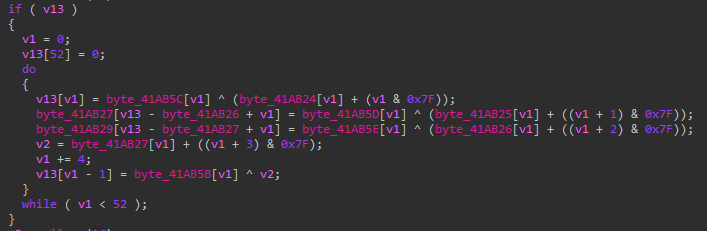
String Encryption
During our research, we observed that the method of string encryption in each of the variants was consistent. Defray777 uses the same string encryption that was used in PyXie. Additionally, the same string encryption methodology was observed in the Tetris variant of Vatet loader.
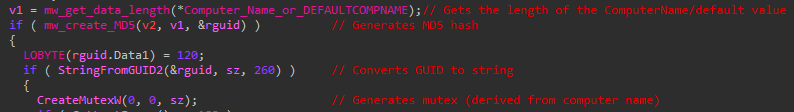
Creating Mutexes
Defray777 uses the same Mutex routine as the updated PyXie sample we analyzed, including the DEFAULTCOMPNAME fallback. One thing Defray777 does differently is that it omits the step where the computed MD5 hash is XOR’d with 0x2.
Conclusion
Since 2018, a financially-motivated threat group has been using a combination of Vatet loader, PyXie RAT and Defray777 ransomware to target organizations in the healthcare, education, government and technology industries without drawing attention to themselves. They’ve only been a blip on the radar.
We have exposed this group’s desire to use open source tools as a means for the Vatet loader. We have shown how PyXie is used to conduct reconnaissance and find and exfiltrate data. We have also uncovered how this group uses Cobalt Strike to deliver Defray777 into memory to encrypt files, causing catastrophic damage to their victims.
We hope that by shining more light on this group of threat actors, we can help disrupt their ability to conduct ransomware operations. Now that they are on the radar, we must aim to keep them there.
Palo Alto Networks customers are protected from this threat in the following ways:
- All samples in this report have a malicious verdict in WildFire.
- Cortex XDR detects these threats.
- Command and Control infrastructure has been classified as malicious in URL Filtering.
- AutoFocus tags are available for additional context:
Continue reading: Indicators of Compromise












 Get updates from Unit 42
Get updates from Unit 42