This post is also available in: 日本語 (Japanese)
Executive Summary
On Sept. 24, 2020, the source code for Windows XP and Windows Server 2003 was leaked and posted on several file-sharing sites such as Mega and 4Chan. Microsoft ended support for Windows XP when it reached its end-of-support date in 2014 and for Windows Server 2003 in 2015. Therefore, any vulnerabilities discovered since then remain unaddressed (with the exception of a patch in 2017 for the WannaCry attack). Although the leaked Windows XP source code might have circulated privately even earlier, the recent leak makes it broadly available for the first time. As a result, more hackers can easily identify potential vulnerabilities for which there are no software fixes.
This blog is a follow-up to the 2020 Unit 42 IoT Threat Report with a focus on the issue of devices running on an end-of-life (EOL) version of Windows and their impact on an organization. We review the data challenges this brings up for organizations and provide information about the best solutions to address the problem. We also provide a list of detailed recommendations to mitigate the impact of this specific incident around the source code leak for Windows XP and Windows Server 2003.
Palo Alto Networks Next-Generation Firewall customers with the Threat Prevention security subscription can protect legacy devices running Windows XP, Windows Server 2003 and other versions of Windows.
The Facts and Challenges
Windows End of Life – Does It Mean End of Use?
IoT devices running EOL Windows operating systems are commonplace in hospitals. This is a particularly big issue for imaging equipment. According to our IoT report, 83% of medical imaging devices run on operating systems that are no longer supported. This is based on an analysis of 1.2 million IoT devices in thousands of physical locations across enterprise IT and healthcare organizations in the United States in 2018 and 2019. Figure 1 shows the prevalence of unsupported operating systems in a typical hospital environment. Windows XP, which Microsoft stopped supporting in 2014, is still being used in 11% of imaging devices.
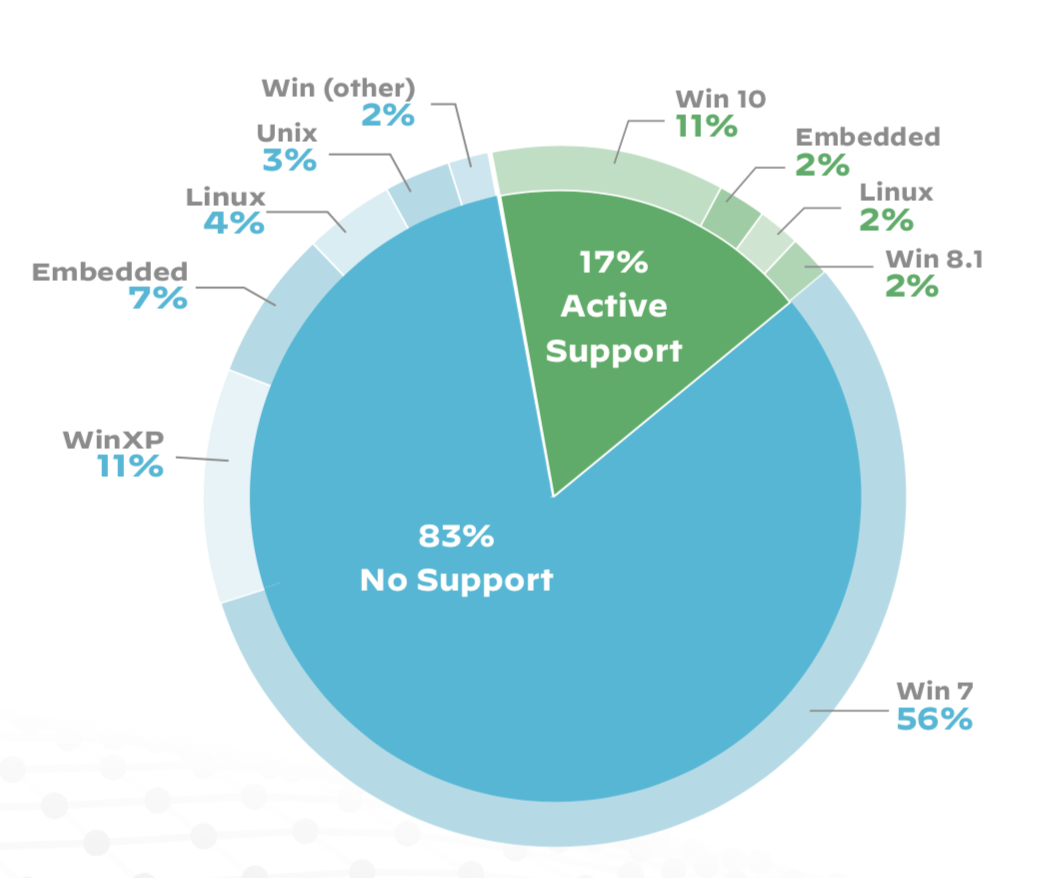
A typical mid-size hospital has, on average, 75 different types of medical imaging devices (such as X-Ray machines, MRI machines, CT scanners or ultrasounds) and approximately 100 imaging-related servers or workstations (such as PACS servers or DICOM image viewers). Among these devices, we observed a notable and discouraging trend of continued reliance on devices using Windows XP and Windows Server 2003.
| Medical Imaging Device Type | % of devices running Windows XP or Windows Server 2003 |
| X-Ray Machine | 21% |
| Ultrasound Machine | 20% |
| DICOM Imager | 15.3% |
| Medical Printer | 14% |
Table 1. Top medical imaging devices running on Windows XP and Windows Server 2003.
Continued use of unsupported software, though prevalent in hospitals, is not restricted to IoT devices in the healthcare industry. We see this issue impacting other industries, such as manufacturing.
Let’s Update! – Or Is It That Easy?
At a glance, this may seem like an easy problem to solve – update the operating system and run up-to-date, supported software on all systems. However, there are administrative and operational challenges that complicate the migration process.
Most organizations manage information technology (IT) and operational technology (OT) as separate teams with separate processes using separate tools. While IT focuses on the organization’s IT assets – such as computers, network equipment and printers – OT focuses on non-IT assets, such as medical devices, factory floor equipment and security cameras. For example, in the healthcare industry, biomedical engineers understand and maintain the medical devices. However, they don’t typically maintain the underlying operating systems that power the devices, nor do they manage the global security policies that govern these systems. The gaps between OT and IT security practices and operations result in ongoing use of devices that continue to run EOL operating systems. As a consequence, these devices are often prone to attacks that IT has been protected from for over a decade.
Updating the software in IoT devices is not as straightforward as updating a normal laptop or desktop, as certain functionalities of the IoT device only work with a specific Windows version. In healthcare specifically, biomedical engineers need to ensure that existing software running on the new versions of Windows complies with FDA regulations and does not introduce any new vulnerabilities for the medical devices.
Additionally, updating an unsupported operating system in healthcare IoT devices requires a certain amount of downtime that might not be feasible, given the nature of the operating environment. It might not be a realistic possibility for all medical facilities to devote the time to do such upgrades and testing, as the hospital may be unable to function at full capacity while devices are down for software maintenance. Lastly, there are cost and resource-allocation challenges to upgrading the entire medical device inventory to a certain operating system.
We observed similar trends when analyzing data from our healthcare customers. At the time of writing, 72% of IoT devices running unsupported versions of Windows were detected more than three months ago, while 30% of all legacy Windows devices were detected more than six months ago. The Palo Alto Networks IoT Security subscription raises an alert to Next-Generation Firewall customers when a device running an EOL Windows operating system is detected. Based on these statistics, we can assume that awareness of the presence of devices running unsupported versions of Windows is not reason enough to persuade customers to update to the latest Windows version. There must be other factors, similar to the ones listed above, that might delay a software update.
Attacks: How Vulnerable Are These Devices?
The Windows XP and Windows Server 2003 operating systems, in addition to no longer being supported by Microsoft, come with a host of vulnerabilities and security threats. Table 2 includes the number of National Institute of Standards and Technology (NIST) vulnerabilities reported for these operating systems. Most common vulnerabilities can allow an attacker to run remote code, cause memory overflow issues or restrict usage of devices by performing a Denial of Service (DoS) attack.
| Vulnerability Breakdown | Windows XP | Windows Server 2003 |
| Total CVEs | 741 | 436 |
| Critical CVEs (CVSS Score > 9.0) |
239 | 127 |
| Denial of Service | 144 | 89 |
| Code Execution | 325 | 190 |
| Overflow | 206 | 133 |
| Memory Corruption | 68 | 44 |
| Cross-Site Scripting | 6 | 7 |
| Gaining Privileges | 228 | 132 |
| Gaining Information | 17 | 14 |
| Directory Traversal | 1 | 1 |
| Bypass | 22 | 9 |
Table 2. A breakdown of CVEs on Windows XP and Windows Server 2003.
The simplest IoT risk remediation practice is network segmentation. However, due to a large number of medical IoT devices running EOL operating systems, even subnetworks with proper network segmentation are at risk. Based on data collected from about 100 hospital customers, we determined that 12% of all segments with medical devices include at least one device running an outdated Windows version. In such segments, if an attacker can gain access to a Windows XP device, all the other devices in that segment, including critical medical devices, are at risk. Having a vulnerable Windows XP or Windows Server 2003 device increases the attack surface. Moreover, an attacker can move laterally across a network to infect other devices.
In one example, we encountered a healthcare customer with a specific VLAN segment that has only medical and imaging devices. This segment includes devices such as CT scanners, MRI machines, medical dispensing equipment, PACS servers, medical printers, ultrasound machines and X-Ray machines. From the point of view of a security analyst, this VLAN is ideally segmented with no mixing of medical and non-medical devices. However, we determined that a particular CT scanner was running Windows XP. Thus an attacker, by exploiting knowledge from the leaked source code, can attack the device and expose all the other devices in the segment.
The Solution
Palo Alto Networks data shows that Windows XP and other EOL Windows versions are still popular in older IoT and OT devices. Many of these devices are mission-critical and yet difficult to manage. It is often a daunting task to upgrade them without the risk of introducing a network-wide interruption to business operations. As a result, most businesses choose not to do so. This is especially true in the healthcare industry. In a typical hospital, Windows XP can still be found running on various types of devices such as CT scanners, X-Ray machines, nuclear medicine imagers, patient monitors, DICOM viewers, medical workstations and even some older printers. What makes things difficult is that the majority of IoT and OT devices frequently use customized software, configurations and limited hardware resources, such as memory or CPU power. As a result, an endpoint security solution is unlikely to sufficiently protect against vulnerabilities.
As a consequence of these obstacles, IoT and OT devices can essentially be rendered un-upgradable, and with viable endpoint solutions often out of the question, how can organizations stay protected from the threats that rely on exploits collected over hundreds of existing vulnerabilities? The answer lies in network behavior monitoring and network traffic analytics powered by artificial intelligence and machine learning.
Figure 2 illustrates the network behavior of a healthcare customer’s nuclear medicine imager that is operating within normal parameters and another with suspicious traffic patterns that is running on Windows 2000 (as an aside, this particular device is still being used in a hospital at the time of writing). In this case, network behavior refers to how various applications running on the device connect to remote destinations to provide or acquire network-based services. When the device is infected by malware, its network behavior becomes anomalous compared to its normal operating state. In Figure 2, in its normal state, the nuclear medicine imager only has a regular connection to a PAC server using the DICOM application. But when the imager is infected by malware, the malware takes control on the device and starts making dozens of network connections in order to find more nearby devices that are also vulnerable, allowing it to move laterally on the network.
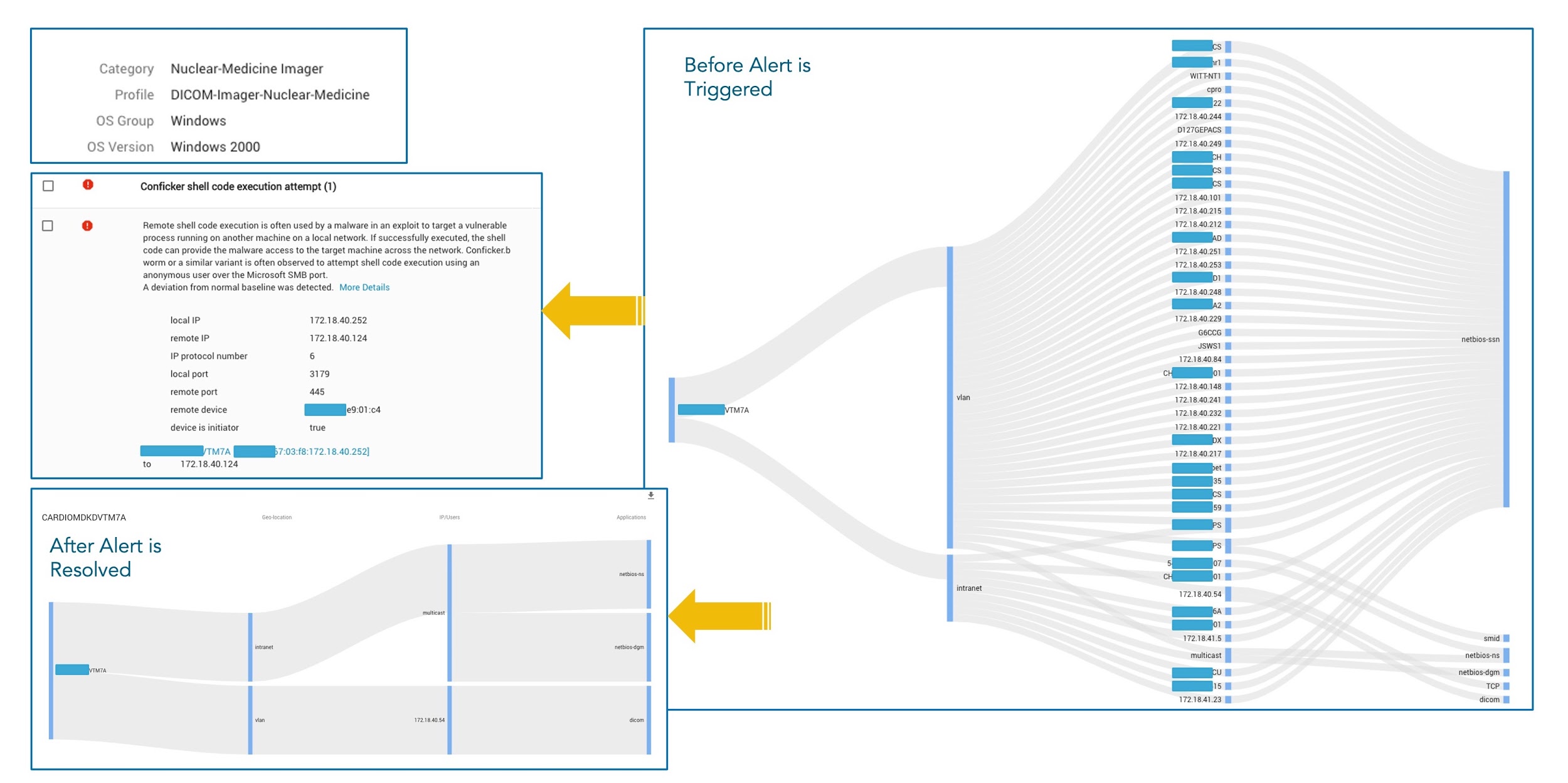
Traditionally, threat detection relies on deploying thousands of rules that look for predetermined byte patterns in the network payload. But it is not capable of detecting zero-day attacks or network behavior changes as a result of the attacks. To discover changes in network behavior and detect attacks like this, A machine learning based solution has been proved to be more effective. Machine learning algorithms can be used to inspect the network traffic, discover and learn the repeatable behavior patterns carried in the traffic and then build that into mathematical models that serve as the network behavior baseline for an IoT device. Corresponding detection algorithms can then be put in place using these models to predict attacks when a deviation from the device’s network behavior baseline is observed.
Often, a single detection of a behavior pattern change might not provide enough information to draw a conclusion. Naturally, a sequence of anomalous events that match an attack scenario could become more definitive proof. Machine learning techniques are good at picking up time sequences automatically and correlating seemingly unrelated events based on what is learned and captured from massive amounts of data. When we put together all the data collected from thousands of hospitals of various sizes and in various environments, we can obtain an accurate picture of how a type of medical device behaves on the network under normal operating conditions, compared to when it is under attack. This type of approach would work well to address the challenges brought by EOL operating systems still running on these devices.
However, to truly secure IoT and OT devices, a solution can’t stop at monitoring and detecting behavioral anomalies or attempting to associate them with certain attack scenarios. The network behavior needs to be controlled with a good set of security policies, which can be effective at stopping the behavior before the attack is set in motion. This can be best achieved by integrating IoT monitoring with a next-generation firewall. When the user is allowed to create a policy based on the device identity and the operating system used, bad behaviors can be easily blocked and filtered out. Artificial intelligence and machine learning technologies excel at summarizing trends from trained models to make policy recommendations, which can then be converted into usable, real-world security policies. This feature is available for Palo Alto Networks Next-Generation Firewall customers through the IoT Security subscription.
With AI and ML-based network behavior baselining, combined with security policy recommendations, any risks and consequences from the Windows XP code leak can be contained and mitigated. When reviewing all the recommended actions, an IT security organization should prioritize having an effective IoT security solution whenever unsupported operating systems are present within the network.
Conclusion
One of the biggest challenges for securing IoT and OT devices comes from software upgrades. Many IoT and OT devices have long life cycles, but are nearly impossible to keep up to date with the latest software release. It is often a norm to find these devices running on outdated or EOL operating systems. EOL operating systems such as Windows XP and Windows Server 2003 have hundreds of known vulnerabilities. Malicious actors rely on these vulnerabilities to penetrate organizations’ OT networks. Many organizations will undoubtedly try hard to upgrade their traditional cyber defense in order to detect exploits on known vulnerabilities, in an attempt to maintain a balance in security when upgrading the device OS is not seen as an option. Unfortunately, this is often a losing battle.
The recent Windows XP and Windows Server 2003 code leak has finally pushed the delicate balance to a tipping point. The source code offers malicious actors infinite possibilities to discover new vulnerabilities and improve their techniques. IoT and OT devices running EOL operating systems could become the stepping stone to attackers breaching and defeating an organization’s cyber defense.
In the meantime, AI and ML-based security solutions that focus on network behavior analysis have been effective in dealing with advanced threats and zero-day attacks. They offer new hope for organizations to regain balance and control in their cyber defense.
The following are our recommendations:
- Restrict systems running Windows XP or Windows Server 2003 from browsing the internet and microsegment them from other network segments.
- Implement Zero Trust policies to allow only necessary applications, sources and destinations.
- Enforce strong password policies on systems running Windows XP and Windows Server 2003.
- Closely monitor incoming and outgoing traffic for unusual activity on ports for commonly used services that include but are not limited to the following:
- SMB on UDP 137 and 138, and TCP 139 and 445
- RDP on TCP 3389
- SQL Server on TCP 1433
- Note: Default port numbers are shown, but use the ports specific to your deployment if they’ve been changed.
- Enable threat prevention technologies such as the Palo Alto Networks Threat Prevention security subscription for Next-Generation Firewalls for legacy devices running Windows XP, Windows Server 2003 and other versions of Windows.
- Palo Alto Networks Threat Prevention can detect over 280 Windows XP CVEs and over 150 of the Windows Server 2003 CVEs. If a CVE exploit is detected in your system, drop or reset the connection to disable such attacks.
- Implement or enforce an incident response policy that quickly disconnects a suspicious or compromised machine from the network.
- Implement or enforce cloud or offline backups for machines running Windows XP or Windows Server 2003. Saving data to the cloud or an offline server is a safety precaution in case your organization ever gets hit with ransomware.
Additional Resources
- 2020 Unit 42 IoT Threat Report
- Risks in IoT Supply Chain
- Two New IoT Vulnerabilities Identified with Mirai Payloads












 Get updates from Unit 42
Get updates from Unit 42