The holiday season is a time for friends and family, as well as for heightened levels of consumer shopping. It’s also a time of year when threat actors get especially opportunistic, and the 2015 holiday season was no different.
Let’s take a closer look at recent holiday season-themed attacks.
Happy Festivus!
Unit 42 examined the time period from November 25, 2015 through December 29, 2015 and identified nearly 4 million phishing attacks containing malicious attachments using AutoFocus. Out of these phishing email messages, we then searched specifically for holiday-themes, using keywords such as “Christmas,” “holiday,” “Santa,” etc. Amongst the results, 92 percent of the attacks identified to be holiday themed were already found to have a Unit 42 tag associated with it, providing additional context around the malware family in use, indicator sets, and any references that may be of use.
It’s important to note that we did not include keywords related to “package delivery notification” themes in this analysis. While these can certainly be characterized as holiday-related, we find these themes are abused year-round by attackers and no longer specific to the holiday season.
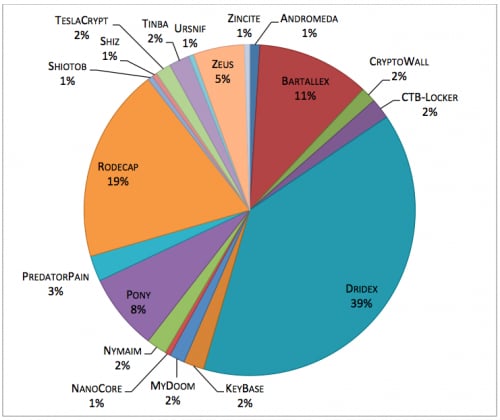
Among the observed sessions positively identified as holiday-themed, a single organization in higher education generated the significant majority, roughly 80 percent of those sessions, primarily containing the Bartallex/Dridex macro malware families delivering payloads containing Pony, Rodecap, and Zeus.
This data seems to indicate that a significant campaign was put in place at the affected organization, and the adversaries specifically leveraged holiday themes in an attempt to attack as many victims as possible. Subject lines for the phishing lures were made up of mostly shopping-related topics, such as advertisements for sales or giveaways. Other lures included invitations to holiday festivities; simple greetings or well wishes; and, strangely, alcohol addiction-themed lures.
Other industries did experience similarly themed attacks, but not in nearly as high volume as higher education due to the one largely affected organization.
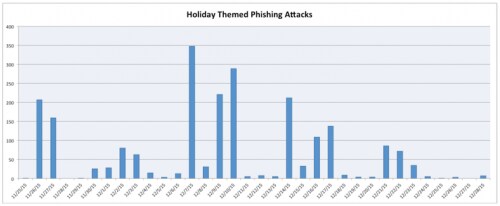
Figure 1 Holiday-Themed Phishing Attacks by Date
Figure 1 shows the general trend of holiday-themed phishing attacks, which loosely corresponds to work weeks (little to no activity on Friday, Saturday, and Sunday), as well as the tapering off in activity as workers began to take days off for the holidays.
Examining the possible motivations by the adversaries involved in holiday-themed attacks, the vast majority appear to be motivated by profit – cybercriminals seeking to generate revenue using malware, such as banking Trojans designed to steal credentials, botnet malware that causes the victim to unwittingly join a botnet often put up for sale, and ransomware that can encrypt a victim’s data and hold it hostage.
The most common delivery methods used a weaponized Microsoft Office document using a macro, or macro malware, to retrieve additional malware once launched on the victim host. These generally fell under the Dridex or Bartallex families and made up 50 percent of all holiday-themed malware. Other delivery mechanisms were generally much simpler, arriving in the form of a portable executable attachment in a holiday-themed email message with the hope that a victim would launch it.
Figure 2 Breakdown of malware families
“WISH U A MERRY CHRITMAS DAY”
Although most of the activity of holiday-themed attacks appeared to be for-profit, at least one targeted attack was observed during the season. The attack used a malicious RTF file exploiting an older, but well-known vulnerability in Microsoft Word, CVE-2012-0158. This vulnerability has been exploited in multiple cyber espionage operations, including Lotus Blossom, but does not indicate an attack by any particular group. The malicious document contained a Christmas-themed graphic (Figure 3) and used a Christmas-themed filename, “Christmas Letter&sponsors.doc.”
Once executed, the file would drop a self-extracting RAR file containing a legitimate executable that would then be used to sideload malicious DLLs. The malware ultimately installed onto the victim host has been identified as LURK0, a variant of the well-known Gh0st RAT. Gh0st RAT is a fairly old, but effective remote access Trojan, and the source code is freely available on the Internet. Because of this, it is quite popular and has been observed in use by multiple nation-state groups as well as cybercriminals. Additionally, the variants and modifications to the original source code are numerous. The one constant of Gh0st and its variants is their network communications – they always begin with a “magic word,” using “Gh0st” in the default configuration. Roughly 50 or so magic words have been discovered, with each variant being named after that magic word. This particular sample uses “LURK0” as the magic word, hence the name.
Figure 3 Image from Weaponized RTF
Conclusion
As we have indicated in multiple previous blog articles, staying situationally aware of ongoing events in our everyday lives is vital in effective defense against the adversary. For specifically holiday-themed attacks, the motivations appear primarily profit-driven. The holiday season can be a high-stress time, and consumers may be more likely to pay an adversary if, for example, their data was encrypted by ransomware. There may also be a higher level of banking activity as funds are transferred and exchanged at a higher volume due to the additional shopping that occurs. Of course, that does not mean targeted attacks leveraging this seasonal event do not occur, as described previously.
Ultimately, the overall trend continues: our end users are constantly faced with a barrage of attacks on both their personal and professional resources. Taking a prevention-first approach to security is crucial in reducing the attack surface to more effectively defend ourselves and our organizations from all adversaries.













 Get updates from Unit 42
Get updates from Unit 42