Recently, FireEye published a blog titled “Operation Poisoned Hurricane” which detailed the use of PlugX malware variants signed with legitimate certificates that used Google Code project pages for command and control (C2). We were able to uncover multiple additional samples exploiting the same technique as well as an additional Google Code account with multiple projects containing encoded commands.
The attacks against Palo Alto Networks customers, which took place between early June to early July, also targeted users in East Asia; in this case an international law firm’s regional office and a major university. All of the attacks were detected by our WildFire platform.
Of note, three of the Google Code projects associated with the newly uncovered account were added during the past few days, indicating it is still in active use.
Below is a current screenshot of the newly uncovered Google Code account’s projects.
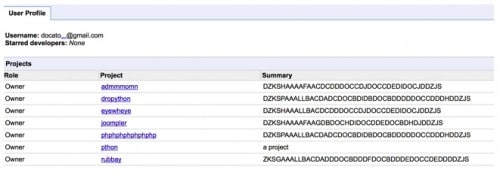
The encoded commands decode to the below IP addresses. Interestingly, “/p/pthon”, which is the project page used by some of the newly discovered samples detailed later in this blog, is the only page with the encoded command not included in the summary and is instead in text only on the page itself. The three pages created since we discovered this user are admmmomn, eyewheye, and joompler.
Table 1
| Google Code Project | Decoded C2 server |
| admmmomn | 223.29.248.9 |
| dropython | 202.181.133.237 |
| eyewheye | 223.29.248.9 |
| joompler | 61.78.34.179 |
| phphphphphphphp | 202.181.133.237 |
| pthon | 211.233.89.182 |
| rubbay | 203.135.134.243 |
We discovered a total of seven samples, five of which were not in VirusTotal prior to our submission. Table 2 contains details of a PlugX sample using the PixelPlus Co., Ltd certificate that is currently only detected by four AV vendors. It has been in use in the wild since at least early June and is the earliest sample related to this activity our team has so far found. It was targeted against a major university. It uses one of the Google Code pages noted in FireEye’s blog, “/p/updata-server”, but had a different C2 redirect, noted below. Interestingly, the IP resolved by the initial website hosting the PlugX malware also served as a C2 server for different malware in mid-December 2013 (MD5: ddd46ce5e5eaaa8e61ce11a121a79266). At that time the C2 server was qq7712409.3322[.]org.
Table 2
| SHA256 | 4d894492c10ddaaae6924744cd21d8115e8b1d72bceb7df6393a8d2cf9130a49 | |
| MD5 | 50af349c69ae4dec74bc41c581b82459 | |
| File Name | 1.dll | |
| File Size | 180600 | |
| Create Date | 2014-06-04 01:38:28 | |
| Digital Signer | PIXELPLUS CO., LTD. | |
| Download Site Resolution |
lthly[.]com113.10.149.142 | |
| Google CodeC2 Redirect | /p/updata-server210.180.33.33 | |
The PlugX sample in Table 3 also uses the legitimate PixelPlus Co., Ltd certificate and was also targeted against the university. This sample was not represented in VirusTotal. It is correctly identified by eleven AV vendors as PlugX malware. In addition, it also used the same Google Code page and redirect as the previous sample. The registrant information associated with the website hosting the malware is a domain reseller.
Table 3
| SHA256 | 935c9652a0d5427a0205062431fd1db9ccafa68d55313504f76206026b84b2f4 |
| MD5 | f92e9e3e86856b5c0ee465f77a440abb |
| File Name | 1.exe |
| File Size | 249720 |
| Create Date | 2014-06-03 21:25:27 |
| Digital Signer | PIXELPLUS CO., LTD. |
| Download Site Resolution | www.tiptoptours.com[.]hk/UploadFiles/58.64.139.39 |
| Google Code Redirect | /p/updata-server210.180.33.33 |
We were able to uncover an additional two samples using the QTI International Inc certificate and Google Code pages. The first sample in the below table was not in VirusTotal and targeted the same university as the previous samples. Only three AV vendors correctly identified it as PlugX malware.
Table 4
| SHA256 | 2ab4953d2e2b38a918e1a1c74741e1de6111b1ce59878a82768990a339318cd2 |
| MD5 | e8277240392ce218f9ec9d4ec3d00655 |
| File Name | k.dll |
| File Size | 180448 |
| Create Date | 2014-06-12 04:15:33 |
| Digital Signer | QTI International Inc |
| Google Code Redirect | /p/pthon211.233.89.182 |
The second sample using the QTI International Inc certificate also uses IP 211.233.89.182 for C2 but does not first connect to a Google Code page and is not PlugX. Instead it contained two separate Trojans; one known as Cudofows.A by Microsoft, and one only detected by two AV vendors in VirusTotal known as Backdoor.Win32.Miancha.f by Kaspersky. This malware also targeted the university. Of note, the PlugX sample in Table 8 uses a different certificate but was downloaded from the same website. It also uses the Google Code page “/p/tempzz” for C2, which was also listed in FireEye’s blog.
The website hosting the malware was registered 4 June 2014 via eNom, a well-known domain name registrar. The registrant address is labtestshowlong[@]outlook.com, which has not been used to register any other domains as of 14 August.
Table 5
| SHA256 | 136e709cc83cbda0cd8ca6e46fe9e57202bd2699ca063f9d1a51602394c06ef3 |
| MD5 | e2a4b96cce9de4fb126cfd5f5c73c3ed |
| File Name | 1.zip |
| File Size | 122592 |
| Create Date | 2014-06-19 01:02:52 |
| Digital Signer | QTI International Inc |
| Download Site Resolution | java-se.com210.253.101.105 |
| C2 Resolution | hk.jave-se.com211.233.89.182 |
Our team was able to further uncover three new samples using the Ssanyong Motor Co., Ltd certificate and Google Code C2 redirection. None of these were in VirusTotal. The below sample also uses the Google Code page “/p/pthon”, which was newly uncovered during this research. The PlugX sample in Table 4 used the same Google Code page and redirect, but the QTI International Inc certificate. The below PlugX sample was only detected as PlugX malware by two AV vendors.
Table 6
| SHA256 | 25a02434132c3977124dfaa7e7392a9af4d1617f3520bc04589d5e7e5aad0362 |
| MD5 | a31fe2e6bd94e6df84a091d00d27ec28 |
| File Name | rasadhlp.dll |
| File Size | 122752 |
| Create Date | 2014-06-12 05:26:46 |
| Digital Signer | Ssangyong Motor Co., Ltd. |
| Google Code Redirect | /p/pthon211.233.89.182 |
The PlugX sample in Table 7 also targeted the same university as all previous samples. Eight AV vendors correctly identified it.
Table 7
| SHA256 | 6594912a0fe3d0380af1630aa8cb6c489f014af4b37f1c99f62fe4d2806907e5 |
| MD5 | 59db9dc2bb3635a3bd94182ae68d31cb |
| File Name | BIN.EXE |
| File Size | 250752 |
| Create Date | 2014-06-12 04:08:41 |
| Digital Signer | Ssangyong Motor Co., Ltd. |
| Google Code Redirect | /p/pthon211.233.89.182 |
The final new sample using the SSanyong Motor Co., Ltd certificate is an interesting mix. It was downloaded from the same website as the sample in Table 5; however, it was targeted against an international law firm’s East Asian office, and uses a Google Code page identified in FireEye’s blog for C2, but an IP not listed in the blog post. In addition, it was only detected by two AV vendors.
Table 8
| SHA256 | bbff6295b390e3098401a43f08d95d35745e807a0dcb19a2ea4a1596aca9ef31 |
| MD5 | 835a1e33a87941c7a1cc9a741d33a5a3 |
| File Name | svchost.exe |
| File Size | 160640 |
| Create Date | 2014-06-19 23:25:52 |
| Digital Signer | Ssangyong Motor Co., Ltd. |
| Download Site Resolution | java-se.com210.253.101.105 |
| Google Code Resolution | /p/tempzz111.92.188.20 |
We see several indications this is an ongoing campaign, including:
- We were able to find several unknown samples used within the same timeframe as those in the FireEye blog;
- The limited AV detection and lack of previous VirusTotal submission of most of these samples;
- The identification of another active malicious Google Code account updated within the past several days; and,
- The identification of additional Google Code project pages that do not have corresponding reported samples.
These new methods have somewhat limited efficacy, as further C2 commands would be more obviously detectable because the C2 server no longer appears to be a legitimate website. However, it is highly likely there are still more unknowns related to this activity, as the actors conducting it have shown an understanding of basic perimeter network defense and some ability to adapt around it.
Prior to publishing this blog, we notified both Microsoft and Google of the malicious accounts using their services in an effort to help thwart this malicious activity.












 Get updates from Unit 42
Get updates from Unit 42