This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers found that public cloud infrastructure has communicated with domains known to distribute COVID-19 themed malware. On March 24, 2020, Unit 42 published a blog discussing attack patterns used by malicious actors in relation to the novel Coronavirus (COVID-19). Taking these findings a step further, researchers attempted to uncover if there are malicious COVID-19 related events taking place within public cloud infrastructure. If indications of this activity were found, how could organizations protect themselves?
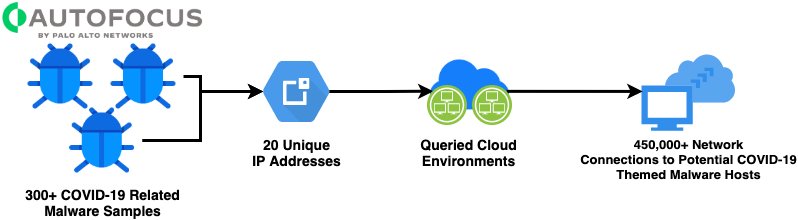
Researchers identified 300+ COVID-19 themed malware samples that communicated with 20 unique IP addresses and domain indicators of compromise (IOCs). After querying Prisma Cloud for network connections to these 20 suspicious IOCs between March 1 and April 7, 2020, researchers found a total of 453,074 unique network connections across 27 unique cloud environments (see Image 1).
-
- 450,000+ cloud-based network connections with COVID-19 themed malware IoCs
- Across 27 unique and potentially compromised cloud environments
- Clear indications of communication with nodes known to perform command and control (C2) operations related to COVID-19 themed malware
It is not clear if each of the 27 identified organizations were in fact compromised with COVID-19 themed malware, as researchers were not able to view the network traffic nor did they receive the malware samples themselves which initiated the witnessed connections. Nonetheless, these network connections should be considered highly suspicious due to the fact that the destination endpoints have a documented history of malware operations.
The Research
Using AutoFocus, a Palo Alto Networks proprietary tool for malware-based threat intelligence research, Unit 42 researchers queried for malware samples that established network connections to domains that contained at least one of the following keywords: “Corona”, “COVID”, “Pandemic”, or “Virus”. Researchers then filtered the results based upon timestamps between March 1 and April 7, 2020. The metadata of these network connections was then analyzed and compared to the network traffic Palo Alto Networks Prisma Cloud maintains.
CAVEAT: Given the nature of network traffic, the network traffic content was not available for analysis, leaving only the network connection’s metadata as a sole means to identify malware network traffic.
AutoFocus returned more than 446 malware samples fitting COVID-19 themed domain network connections. These samples provided 20 unique domains and hard-coded IP addresses that could potentially serve or maintain the malware infrastructure. By resolving the domains to the most recently known host IP address, these IP addresses were used to query cloud network traffic connections between March 1 and April 7, 2020. The query returned 453,074 unique network connections from cloud environments, which were communicating to systems directly tied to the DNS activity of known COVID-19themed malware, see Image 1 above.
Table 1 lists the 18 IP addresses, which were identified within Prisma Cloud as well as what and if they are maintained by a content delivery network (CDN) provider.
| IP Address | CDN-Provider | Count |
| 8.251.31[.]254 | Level3 | 91026 |
| 95.101.78[.]106 | Akamai International | 83624 |
| 95.101.78[.]82 | Akamai International | 81979 |
| 8.250.169[.]254 | Level3 | 51091 |
| 8.250.183[.]254 | Level3 | 49611 |
| 8.251.5[.]254 | Level3 | 46864 |
| 8.251.15[.]254 | Level3 | 40262 |
| 74.208.236[.]42 | 6742 | |
| 120.138.17[.]203 | Telstra Corp | 765 |
| 104.28.9[.]246 | Cloudflare Inc | 458 |
| 104.31.74[.]50 | Cloudflare Inc | 420 |
| 5.79.72[.]163 | 72 | |
| 31.170.167[.]123 | 66 | |
| 103.140.250[.]215 | 32 | |
| 51.77.161[.]45 | 27 | |
| 45.81.226[.]17 | 19 | |
| 91.234.99[.]234 | 12 | |
| 45.128.134[.]14 | 4 | |
| Total Result | 453074 |
Table 1. Total COVID-19 themed malware sample DNS activity samples queried through Prisma Cloud
The yellow highlighted values indicate IP addresses that resolve to CDN hosting platforms like Cloudflare, Level 3, and Akamai Hosting. CDN networks provide limited network information outside of session metadata. Given this limitation, researchers chose to exclude CDN IP addresses from this analysis no matter the likelihood of malicious content. Unit 42 also published the blog COVID-19: Cloud Threat Landscape which details CDN website hosting within cloud platforms.
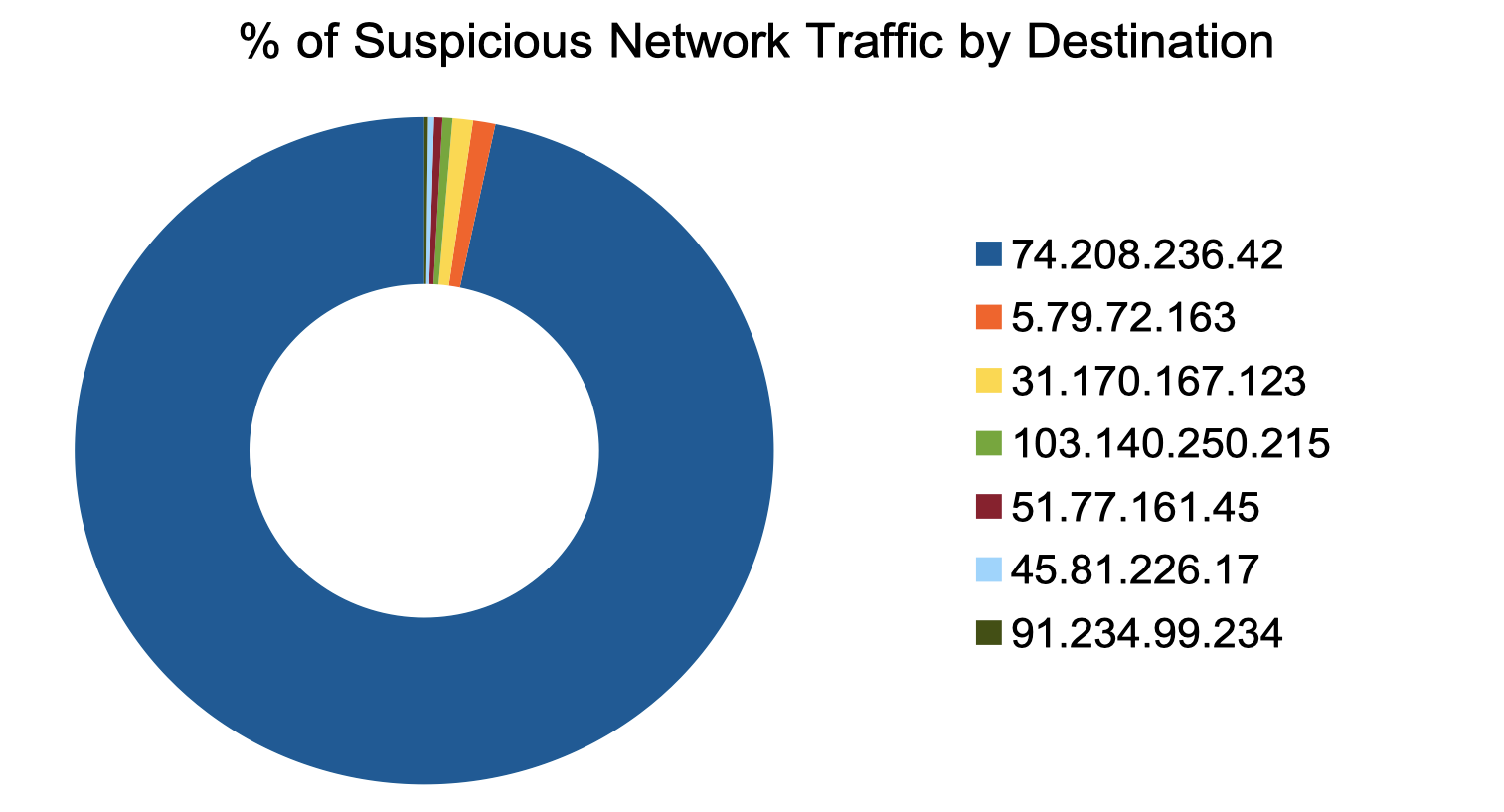
Researchers were able to positively identify seven IP addresses that were witnessed as the destination network connection from 27 unique Prisma Cloud environments. These IP addresses resolve to independently hosted, non-CDN web servers, which have a known history of malicious activity both from the perspective of Unit 42 and from other reputable third-party threat sources like RiskIQ’s PassiveTotal and Hyas Insight. These seven IP addresses, and the domains from which they resolve, significantly increase the likelihood that they serve or maintain malicious content directly associated with COVID-19 themed malware and they are actively communicating with cloud environments, see Table 2.
| IP Address | Count |
| 74.208.236.42 | 6742 |
| 5.79.72.163 | 72 |
| 31.170.167.123 | 66 |
| 103.140.250.215 | 32 |
| 51.77.161.45 | 27 |
| 45.81.226.17 | 19 |
| 91.234.99.234 | 12 |
| Total Result | 6970 |
Table 2. Non-CDN hosted domains and their associated Prisma Cloud network connections
Image 1 displays the network traffic percentages witnessed by these seven IP addresses.
Historic Malware Activity
Researchers returned to AutoFocus to refine the malware sample results of these IP addresses. Researchers specifically targeted any malware sample that contains DNS activity with any IP address that is listed in Table 2. The results returned a total of 185 unique malware samples with an assortment of connections to known malware families and exploits like LokiBot, NanoCoreRAT, vulnerability exploits CVE-2017-11882, CVE-2017-0199, and CVE-2012-0158, as well as having several connections to malware operations like Windows Word phishing documents and RTF_ASLR bypass.
While these malware families and exploits appear to have DNS activity linking them to these seven IP addresses, researchers are not suggesting that there exists any link with COVID-19 themed malware and these malware families or exploits outside of their IP infrastructure or DNS activity. For example, it is possible these particular systems could host and provide several variants of malware and it is also possible that more than one malicious group hosts and maintains their own C2 operations on one or more of the systems using the IP addresses in Table 2.
Additionally, each of these seven IP addresses was flagged as “Blacklisted by Third Parties” within PassiveTotal’s RiskIQ based upon the grounds of phishing, spam, C2 infrastructure, and malware distribution. With the AutoFocus evidence paired with the evidence gathered from RiskIQ’s PassiveTotal and Hyas Insight, researchers feel highly confident in determining these IP addresses as malicious and recommend that no cloud or traditional environment maintain any network communication with them.
Port Analysis
Researchers also analyzed the network sessions to determine the protocols most commonly used by the IP addresses listed in Table 2. As can be seen from the network traffic metadata, shown in Table 3, TCP Port 80 and TCP Port 443 make up 97% of the network traffic to and from these malicious IP addresses, although there are suspicious connections present on ports 25, 110, and 445.
| Destination Port | Destination IP | Count |
| 25 | 5.79.72.163 | 8 |
| 53 | 51.77.161.45 | 2 |
| 80 | 103.140.250.215 | 20 |
| 31.170.167.123 | 39 | |
| 45.128.134.14 | 4 | |
| 5.79.72.163 | 4 | |
| 51.77.161.45 | 14 | |
| 74.208.236.42 | 4086 | |
| 110 | 51.77.161.45 | 3 |
| 443 | 103.140.250.215 | 12 |
| 31.170.167.123 | 27 | |
| 5.79.72.163 | 56 | |
| 51.77.161.45 | 8 | |
| 74.208.236.42 | 2655 | |
| 445 | 45.81.226.17 | 11 |
| 74.208.236.42 | 1 | |
| 3389 | 45.81.226.17 | 8 |
| 5.79.72.163 | 4 | |
| Total Result | 6962 |
Table 3. Destination port analysis of suspicious COVID-19themed network communications
Drill Down
For the remainder of this blog, the following four IP addresses will be specifically isolated as they hold the highest likelihood for serving or maintaining malicious COVID-19 themed content to cloud infrastructure, 74.208.236[.]42, 31.170.167[.]123, 5.79.72[.]163, and 51.77.161[.]45.
74.208.236[.]42
The IP address 74.208.236[.]42 comprised the majority of the network connections with 97% of the non-CDN traffic originating from cloud environments. This IP address is the sole resolution for the domain unlimitedimportandexport[.]com, which is flagged for malicious content regarding command and control infrastructure, malware distribution, and phishing operations using COVID-19 themed attacks.
AutoFocus contained 15 malware samples that perform network connections to the domain unlimitedimportandexport[.]com and it's resolving IP address 74.208.236[.]42, with a first seen date between March 1 and April 7, 2020. AutoFocus had tagged each of these malware samples as either ExcelLaunchPowerShell (12) or WinwordLaunchPowershell (7). No other domain was identified resolving to this IP address from any other AutoFocus samples. While the domain is not the only site hosted upon the system residing at 74.208.236[.]42, this IP address is to be considered highly suspicious and likely delivers malicious content to cloud environments.
31.170.167[.]123
Unit 42 released a blog on April 12, 2020, detailing Malicious Attackers Target Government and Medical Organizations With COVID-19 Themed Phishing Campaigns. Within that report, the IP address 31.170.167[.]123, which resolves from the domain www.tempinfo[.]96[.]it, was identified as the C2 node used to receive the username and hostname from the victim organization, which was then used to generate an AES encryption key. This encryption key is then returned to the victim by means of an HTTP POST from the URL www.tempinfo[.]96[.]lt/wras/savekey.php, and the encryption process is initiated.
This IP address was found to have network communications with three organizations within the Prisma Cloud network metadata. However, the organizations involved were not government or medical organizations, as they were detailed within the previous Unit 42 blog, but rather included a US-based business data and analytics firm, a US-based market analysis firm, and a US-based network analytic company. This IP indicator should be considered highly suspicious and all network communications with it should initiate an incident investigation.
5.79.72[.]163
The IP address 5.79.72[.]163 was witnessed interacting with six of the 27 disparate cloud environments. The IP address resolves to the domain teknik[.]io, which maintains a firm history of malicious actions including malware distribution operations. No other domain has been seen resolving to this IP address and any connections to this IP address should be considered suspicious.
AutoFocus contains 143 malware samples, associated with this domain and the resolving IP address, with a first seen date between March 1 and April 7, 2020. The vast majority of these malware samples were tagged as exploiting CVE-2017-11882 (130) or CVE-2017-0199 (21), with a couple of samples also tagged as LokiBot (10) and NanoCoreRAT (4). The malware appears to center around Windows operating systems and focuses on Rich Text File documents to infect systems. All network traffic to or from this domain and its resolving IP address should be considered highly suspicious and efforts should be made to terminate future network connections.
51.77.161[.]45
The IP address 51.77.161[.]45 has been linked to COVID-19themed malicious content via the domain kplico[.]com. This domain has been put on third-party denylists due to malware distribution and phishing attempts, and the system only appears to host-specific domains at specific times. These domains appear to rotate across 16 predominately Iranian-based domains
Analysis of the malware samples gathered from AutoFocus only consisted of three positive malware samples first seen during the March 1 through April 7, 2020 timeframe used for this research, tagged as CVE-2017-11882, CVE-2017-0199, and WinwordLaunchPowershell, however, there have been a total of 11 confirmed malware samples since January 27, 2020. All known malware samples make DNS requests to the domain kplico[.]com and Autofocus tags the majority of the older samples as NanoCoreRAT (6).
Conclusion
Of the 300+ malware samples identified to communicate with known COVID-19 related malware, 20 unique IP addresses and domains were identified. Network traffic from all known Prisma Cloud environments was queried using these 20 suspicious IP addresses and domains and a total of 453,074 unique network connections were identified between March 1 and April 7, 2020, see Image 1 above.
Of these network connections, seven IP addresses were identified, which gave a high likelihood of positive malware communications with cloud infrastructure. These communications are highly likely to contain malicious transmissions to and from infrastructure known to host COVID-19 related operations.
It is not clear if each of the 27 identified organizations was in fact compromised with COVID-19 themed malware, as researchers were not able to view the network traffic nor did they receive the malware samples themselves which initiated the witnessed connections. It is critical that every organization monitor their cloud infrastructure network communications to ensure that these types of malicious communications are identified and blocked. CNSP methodologies must be integrated into cloud infrastructure, development, and production environments to ensure these COVID-19themed attacks cannot be maintained within a cloud infrastructure.
Mitigation
Palo Alto Network Next-Generation Firewalls
Each of the IOCs listed within the following IOC section were added to the PAN-DB, which will allow each next-generation firewall, both hardware and VM-Series, to block network traffic to the identified IP addresses and domains, as well as block any of the malware samples listed within the report.
Prisma Cloud
Prisma Cloud has taken its first steps into integrating AutoFocus Indicators of Compromise (IoCs) into its operation base to ensure that cloud organizations can quickly identify when their cloud infrastructure communicates with known malicious malware. Now that Prisma Cloud combines AutoFocus with its ability to monitor cloud endpoints, detect malicious actions, and alert upon critical vulnerabilities, Prisma Cloud is able to monitor and protect single, hybrid, and multi-cloud environments using proven threat intelligence.
Cloud Native Security Platforms
Integrate Cloud Native Security Platforms (CNSP) into the CI/CD pipeline to ensure that cloud infrastructure is properly vetted for security risks. CNSPs share context about infrastructure, PaaS, users, development platforms, data and application workloads across platform components to enhance security. CNSP offers organizations the ability to deliver secure cloud infrastructure while simultaneously using the hallmarks of cloud, security automation, secure scalability, manageability, and secure on-demand resourcing.
IaC Scanning
Every Infrastructure-as-Code (IaC) template used within both development and production environments should be scanned for misconfigurations and vulnerabilities prior to its use. According to the Unit 42 Cloud Threat Report: Spring 2020, more than 42% of all IaC templates pulled from GitHub contain at least one misconfiguration or vulnerability.
Indicators of Compromise (IOCs)
IP Addresses
5.79.72[.]163
31.170.167[.]123
45.81.226[.]17
51.77.161[.]45
74.208.236[.]42
91.234.99[.]234
103.140.250[.]215
Domains
kplico[.]com
teknik[.]io
tempinfo[.]96[.]it
unlimitedimportandexport[.]com
Hashes
015d9c9a42e23532cbff50f9f65d90b7e5e53b0b8df676ee6a13f4177e3eae35
025c3d602e548ddb3bd9b640c26665d836a45dd583a4942ae9730c02f1f1a12c
0411028730acd0a55c6077ad8f58b72fa4362da33d88445ae5cb4e33a909ae92
0537f15b4051942430191340336a785f8c690a8aa29571d7a0dde843c5d9b0ed
0578e68d8770cfd9c073f44a4262666ca8114a905f95eb68dc2ce3258c7d0c1d
082ef0b013bab1fb3c9f99aa50a1c039b1c9bb25e84ee37d88b90a513c28ee05
0b56480f83dede82b7e331f82144421bf69b2009d4aead0d1c577fd6329029b3
0e3bb07880b9e2cd3da9aed3ae2e0596ceb63654766ea5b79282282a2159bf48
0fc6ceef04ce6de9ba41ea9d2651d9962bd2b7c5e092df4b71f42cad64c90a92
11bf5382ba0dc36ecaad3ce47cdc6890fbaa22d401716cd149d29741ea487120
1431e293da7a89a08a80ba63f13090050b15f4dc1d28cc752949858aa7690707
1441d6db9a2dccc8a57982f7ac4feab62f0621c8f36bebfb5971a7d7233cb309
164f917cb665c788adb9908444d90e1f9fed0ea2942e5744f5f3a72be92747c8
16a74b44f1d4ca3b850910182d2e87b2317f7aa9becb15d330416eee1fb55e07
1714b62d8d44cc289726b966be8598b5a7e416cd0c85050be9d395d36610a66d
1766f9752af45a8655f716562d0dd93714e2009fc04474c6734d5daebb95162c
19c169929dc46269b669c9c92fc0445a5057666a1e443208a57dcbf8686d9a1e
19ec071e413a88d0de44d0837486ecb6adfdbfeb85edd64db560af556effe7ee
1aaf862d0f14d85e2870503db000bec25c0952413b12f039ecc32f61cf565131
1ac34ed069159715ada83bc926d6b7d70447d6d45e382d2b8fba04ca1f7ee86b
1c935aa3a65ad9d045838f5297c1386a5a152beb12b40331459461d088c4538c
2185a33735010dcb8e22ff8301111e714596edce67fe82ec349bf8aaeab29033
21c267e76b886f9289947481999034fae58ae2575f063b78bf584ba6dd96ef0d
23f04285f6494f8670e984d559ef9d265f0e28fcb1f3636a2751bf97e89f5306
242c590d3582149d465f90063f1a64fcc29875834e667b3b2e934ab58c1a7a19
2466a4b6df523b21a2a97f5f6cfa15a14aca084e3f9e5e24aac0394d60616800
247832fc2d01c4b163372c005185cbd7d0352ceccec2a277bc968ea4da630639
253f00d16f2d35d43baeb88afba5d01c4151877c8c42e168e691e50eda87b2fb
271cdfbeace863d7fc6ad9ccb19ca74855088acbf0be761634e5f9276d5321c0
271dee34bdf71e407ea2424560be0f12f736b1a2f6c9af91aec5d1f4b9216d00
2779863a173ff975148cb3156ee593cb5719a0ab238ea7c9e0b0ca3b5a4a9326
277ca0574a1ff8cbebe3f30e59736775962135aaa5ff0f7decd2b6c247a4ae8a
28aeda6b35141c7e54b3bac3f6d5255e01db9cd4567dcfed8168da734d7c0669
2ab43f60b558d7448afe4855c8bb6d0cf8fab6e16e7848154ed0b98c72eb77e8
35184145261c318d0e348638b995b5d0d165217f0ae53067ed4c40bcc653db29
354dc02a498c1a963689f314a0bc72f36771e41b8f8798e78d0da2cb860fbec5
3599c1bcdd715ce17c8bbe2535edb4dcb4b5ab94b8a9807b2378cbabd1a13e02
3b54e98cb52fb06929e70dfedea7f6265dc522225e2eb1db149da231a5b87b2f
3c37b32cc0cf0da87c3d47545ec79cf41b8662b0354551e3217276f891f12a22
3dfb211685c0945841184e5215c37889ea180a7f454a55a80a4de7fb5cb4314e
3e168b8fb92ab777b647491dea631b06effd8b32b75d41143f266f30e146e030
3e4bbe926935e71625578822e326a501d7e268bf0a4903b279855cff9015ea0c
3ecd8af401ac56c61538c3e1bf396c3a7acba0cb89d624a29044833bd815b160
41a69c13aec8be3e1f725a73d98727447f73ab1f4c7fa2baa9bbce8618df8ca1
41b2c6afecf797ab0fa9532a9327a1f19a5c58e13635ba7bd0e9deb45dfd5170
42945e863a1e8054ca89d90759f299722a1d7ff9b9762cbac73214bda828fcf6
42f04025460e5a6fc16d6182ee264d103d9bcd03fffd782c10f0b2e82b84f768
4409d981edc3b15f5c58995200aef4609af5a32aab9da7d596f108e29e48ed61
44fb4d09a80e4afc69cac7409c23e126262b606a909dd421146aa5e06aa2d390
458f33a1dc34e0b587dda65f10238f590738abe8a453511fab0558144b919e37
46f0d3ab6b68d84847c04820d7f2e590727ce4c87e96f29dfc3e1ecac8b404f6
47123fb92a882213d89fda07f28f3d1713259d1c8842326f7bc27488d4c48155
49480dfd1f5349234b92a3ee08263071a8acecab2ff5b188c242ba84bf880e90
4a1f043432e9810242ba29a67b5b2e7e501754a06f3cadaffbbbf766a9116f8e
4c11d68b80ac96302f79f23586cb40b6d7a5235875c14ae00a8d9203fa574a65
4c73d0437cb52e082b00c5100bab779399b18548f41da43a3a127f8343bdc847
4c874ab6c0b01cba06ffa454a37e878d4c7b8cb8cc0ed00a8c410a9833eed407
4dc69e5b5aca4c147121bf37f0f659dd0976f8c75c00b942f5a095f68938702a
4dcaaa0534d2a270a5e1c9ce5464c8ce826b7767108392a2616da9a25ff267a8
4fd2d7d93ea4cb52a749c00773cae469a7054c0d99a88169e5a334e32f50f22a
508075b3374b4c3c47d257b5d794779a90418cbb1d68175c2abfa4ce5f24dd67
51e9ae4199f631c7df589bfe857568c609a6f57c43538dd27f9bb1f6932808e6
543d8be5723b82693a6f5326f435823e0b152c2d83f874b86a82f6fcbd931bc7
5529dd3374d902d4ec626f23b831cd3e4d0120d15d9a0dc16deb3d19784ab35c
55988e76af684dffd45346e4622245e5978187a2784eeb064b5bf616e80b09a0
55cfc6c24813143e41df3fd01d35e16602af309620ca45648eaf70cc257f4a2d
58a6710c62c4a11565cb66282a78356179ebf868724a89580821953e5e7b3746
58f7ca1e6626103f0274d20f590d7f693585816e00f0bd93884bc15d0a7247a2
599317272a363b0a30b2860560be79d2066d9881b66925cbc9948f3cec8397bc
59ad049d80b6e2cff529e4a26db3bcb25e5b5dfda49d87b4b031c13e62cb2288
5a4582018c5e5e90d37604f4a4e3598150919153e8b1edf4e64da392630b968d
5d9e4abeeecf4ac855880206049246abe0f49a14bfc693349a81605478dde63b
5e977b5c8d3f438e684ffe134027476dd90a4eff1bf4910d1b41f0d489f9a04d
5ea2d64f9c644433e995108afbbfa9bfc0077e45f5f96abbeba717fddfba8474
5fc201b8c6700a59586a14a8ac53165e662fee128038f204b73a3a0e795d547a
61115d27cb35e6bf9835761e1897e53182e62ecaa63c1f3533bbf24cc940e805
62d38f19e67013ce7b2a84cb17362c77e2f13134ee3f8743cbadde818483e617
6318684e58716680b882f26d8aecf04e0019ccaa31605629815c79f05a0a1838
6391e4c4a9632bce7a7f5b01a701b8e84aaf0be9f115e5daf910c41f3b5260fc
6535d0c2d59dc35f1c3951812b79e2a97b2862d4c0fe12cdc37f0ec641abf081
66f886cee2e281a481d03dfda28bbe8ada348087d24544403a23d0596ccd3753
67b268f1e4ec8cd13940eff3a442445dca813ca706993211ff32e9eda1db35b4
67e895b7e1d01ed661cf5f310da8d1f59337dffe967002728d55fffeed2bb56b
6dd31b038d84e748f8b873e31971c0fbb329f75979c5f520a8e460d0764b8370
6f9cf2d532cc8eea81df1ba495a300513fb2567d4e2dd343705b2aee698afc4d
7031315d4298f8030872ba6a4dc07903decc5a008fa01017c734c42b995f7d17
70471f7b4fa066ced7a8415d3c0219037daf4376a5af99232a714725c160046f
7172c41b8860618b6adf20a0443a7d4c2e93a6b01da97f8068d53d4194e37bbd
71cb2fdf87214765aa9af37ea331245afb6441a28eadb1f7ab35cacb8043bd61
74da88d674bf1d281e39aa18399d0f189e51dc87e9e3827b8c6182e2e0de0e7e
7512ef3971ca4d0a902342fe3b6dc465939fc7046222e7d50524eee83076e6ea
758594c0ffb7b7736d9705a830341da83d220a656c9651534af2c3d0ec2ecfe3
758d0addc5b5952f4367307e06b8c559376ea514286c2c56a1200cee230a790b
767cb6b6859090c2ff271e2a69a37ace6f13a98faec1608ef265d146567566bc
778c6ab3a1bdb991b6b37ec5d652b6c444a20fddb743962da34fb5302ed87728
7a23a1e1f4e13a03de911def8a14c110f18bd512bbcf2abea0bef2e3dd09cf68
7b427b656ce425376a61a0d1caea523258aa44c8e4011d66089f02658263463e
7d57545c0bc2f5d52e90be220fc224ca48b3b6b697f5ae34333122df2224a4ef
7ea775ce3d1bbec6a0956b651d6faa66c9c56c7c9fabb700cc8f4f2a972e6aa2
7ec29d0c7759e0a04b9aa24104232df451b29dbbad9951add42cd23ef3292d07
7f07f14d5ba0dcdd810db7cf047045eb306600823ca0a7dac88c0b52d3930d4d
7f1c867216e3d37b54c5e07dae0dde6712a204eab13aa464df23f14ddc968606
81e98135951b22364f0679cae1590b14463adf27f6d55659d0f3104bbec79780
8332b625d3b6280762ef9fe393da174c65d390b3834d95865904854922eeda3f
8476cc9f2ad18d2bb884e4fc70e81d2cf4cd4036085ccd9f9aaee08ef50367af
849cac7f9689229de2eb83845295d5e061fe5a35388534054b9098a0eb256e1f
865c3d5398639b15b66ded5441836610bc82d3c996e707ff8741c8b7fce482d5
89a63aeb18c87652e6c68ca582fea6e12e88b519e21f52ee9e649ab92e720c4a
8d58014569735fafade5ff971e9f19b885503f693a0f32e685b9829bd67e679f
8dcf7eba4af16338b5ac343f55176ae836214e54677db9c1d9128afb96dd05b5
8f6f6c9140a3d265363dbbd34d552eda964c5f9c042a93c86ac29dfd05896ff8
8fbc5a54150922aef7fbc914fe72cd663bc23bf0a33eb4c8659cd79d53d6cd9b
91a981113c630434212a4ed9cf0362ed514dbc2c52e235a3875cabc4cafadebc
91cc37ccdece55aa4cca2532a846126fa463927c3f10343716314f04a27c3c79
984eeddd872274e16a4a24d42a66dd99110793fe64e46db525d5c017cd5755b1
9b023002c7cdfa05d8ce487af118673563c11d98f95d095b208627d700971c74
9be3262c99cecb704a331b96d3f640f97efa094608daeddd8b9682f441faa5b1
9c28354579d2ce69df3f609cd46c6c53052c3546cd4c63205a6c88e6a229ec35
9e07f2ffae0b978cf6f36026d7a049691a43da206800bf3ad187c1bfee33928d
9eb1bd5605d05e9926a63256e6b77c2e5ea21a4b3798f0697108c4035efb3e42
9f0385a0967acc5d324628ea3f78ef86085a6ed59037bce26bcecb0d9ab5197c
9f5a60090ed1b94abc12d02ae1a43ae5a0eb37b108483ef0286d2c9f917b7476
a01c3c97b8b91ef4c69b3392fb57091546b1fb7c344d60b33dd5d778f58f6d07
a0400828ef967467fae9dc8bb83c658f8a493d05268aabc4f1fdf0f235a63d3e
a0f1cb4197fe6f18cc664ed6eacb6d2ef8597eca7723d4130f1b0ed5d5ad1669
a15a623767449a87179ca7276c16bc33825aad76c475870fcefbd62110c2120e
a4007fb26c4ac60b661a77839739f5db56b0d016c57611af013f4bbb21d672cf
a465aa7ac0dc2f7d868a6e682870f164f2738647bee1d7d337c710f0eb52bbfc
a4e2573420f85a738fe78b192e87c2f864aeaae89aa7377f2a4a11d909a0a824
a76a2c64c08cb5e96238ba19f9a038573ae6f61dd1ce2f63b8c9441b8b935990
a843b0c799c7ad34fa76f278db59da140d77af3a38295b0d74ea273013065ed4
a884b0fb2e540b4bfff1df58fb6b294ce638846b8ee6a296d3661881c570ffb1
aafb51a2fd04fbc38a549d648b7e96d62216a9a1908b0fa5c39357f88a8bf95f
ab458a1da7237fe9779357a20d2d5718bd84bfc67d121f9162f059f9deafc6dc
abe39297ce1526ff13e022ea2c68b5141a3aaf03551d9d95b260373d0bb17af3
adc9c3d9534ac4be11796a95c966840c88b69589a1a4b6b0426a996838afe4e0
ae26d3bdeaea73a75c7c3bd6c3faf9513a3fd957bba0f446d0fd4555d5428a15
ae6c08d1378963a1e602167ed9d70151769344ba77cfced1865a1643277a1319
b1a82ca1b059bd34b5c98560d7257b65c0906e518c578952c2328f3bf416bcd1
b4e585a0f192ed4fdea8909dc2c119bce45ca7e1b7a74ef45ba1c14cfa16a97e
b557edeb7c35a0545e780cfea1b057ed73a8835cbd80fc3534bf6b1da89975b1
b5d9082c42b9d649fed71d07156d65c0d8162b2adb761003b8946cc6d8c63fea
b639c0937a7b1f194bb980c7d601813c95c01c509220a153a62e9e79a53d2cda
b688f8534058c14a5a111f755f49c45ea101fa684b182039ff06958115866b81
b9728bf311577a2d9f8258296d9b6d326d0e9d32bec678c19601465e2a033fe8
ba36d885a562a6aec1dadcd654b4468e47f4b5aeb7c5b2aa642560536d74e5e6
baa31d36a1229ab1f21da18b7ef603e46a3abbf5e6163d471f1bdea8ab3a3281
bb399ed423a50afb359fbe7c769706196478c117869ebb6976aed43b3a7777a2
bf16e722984f266ed24480bbf2c796cd9cb6104324b066d6e086628c1b4d4b77
bfb5edf186a206a54b0002e4b44cfba96b6340ab3fc5654b5be662f8e7ae95ed
c0ca8040842789fd69497927dda9a1fa2813d7652467090cc88ee47a543e6085
c330346d40854e4a971cd0c6011f9dcb1484e85b6e42d8d48735312518ae4a9f
c35d1f026bc0c6a9acfbcd7959d2c781bd14059a0276a90be75b19e86433f500
c501f99a404c0866d9f8b3f9b71d4169cf07296923edeef1b2054cf1d937bef0
c5c43b340957830f5d7484ce06f9de0ef593d88f3d48c09cd2150e670661f672
c74c2bb7f954d5f3f806fd399fcec81522be1c02162a6821d31050de1dee1a92
c9440b0b18b92db64cb53c3f43e269c5906c7d13d2c2211755ae5abf253581ef
ca50c4d018bcc196bf53d3f02fafffe5045f31d17561e02fa6f4c4f2b0c7c05a
ce66f177d83b8c45367fa50e83c2378f04c4f9df88577e43879526e5b98b3c41
cf3aed798cf3d1ac93baff3a7b3b6aaf8227a356538a53c914b942ca2b689772
d15767f8ca42218de59e998a74faad26dbfc3327431be164b6aaae7a01957297
d5bb3fafb5a1ccefa682282bb3f8adb015e3296688efe0d8aeb236828af9a331
d706fe8a74682bcd7eaf301b2cd1c0f38d54ed2b10570ea463bcaad341e010fb
d7696c137969dfd65a0398ddfd5065e5de1a61be93a4680ffc1c7faa731d5b69
d88cf127211cc77685a6f61e32a19358946e1a935930ba8c020d9807a2effe21
de3e93acc847979c41267c52cc4b46b35553a4a152feeab182b6c5dbfb21a14a
df2becbce21a204e7f92467a06e6d68069330b8c21dd7342adf079b68fb9d08f
e0bd1875f37bdffcea0a0e3871220a83ffdd09ffd3b7cb770520bbf00fd7e5b8
e1238fc834747073182c964f3da49c9c6dd963acaff053c8765a6871cb740de0
e17a5ba4e146550c43766f0a76004e548c1b9e4802370d5ee3f4c54a92404b64
e9259b9278b0e081ed8f64a2fb21f82f2c33a184db39650804d53916417fac2b
eb720c30a1bfd1771925c100403833a46cc0852987f57d83168a1adcf91dc371
ec1c7bec6d8d360f9f2be44fa948f08d3144f2b7a7c6432f13ad255f00c7c9b3
ec94ac63d4d436d94d73f76a3fb6200d1597d0203a17020f55a62b381071d849
ed83615ed3193bdcb4202b5e288199d626de7884c4eeda32968a06b3c0e43ee6
ef72febd8cbe7f5d73140436e2c19a76fb4546bff6265f3d259f51171b190afa
f1b696ca941f48be904350de5727970ba05ec7443df05b89bd416ac11866a4fe
f3e1fdf3ff164f8d75486e53ce23df56c7eaa0bc8261b2106c5a1ef32eead295
f4fe33c22dbe4182406054e7bb4a3cd764a75c277c8013d4decbf30b3c9dfad8
f50686ddf8d9696bce0cde277261a7e901ec4ad3af1f57c71c3f24b1bc3fdb58
f610bfaa9d6ed6c0bddd277590e19ff6100269392fda0812ee389f5c33df2811
f70f447eb7cbc612f06537775c0084c9cde94eeb7d39e3f84e1111f8eb108426
f8132b19cba0af3c24f873a5d81ee588b3487b8db9bb12f1b317f6b1d2affcaa
fe9b7fce26d17f9e46c69a6d11e69e974f54a9aca56ef945489deae8b51199d2
fef116e4e2eaa3ef8350dfddb1f4bfd73a19738c693e647c34cbd877d9a0dcf2












 Get updates from Unit 42
Get updates from Unit 42