This post is also available in: 日本語 (Japanese)
Executive Summary
In October 2020, during Microsoft’s Patch Tuesday, a security update (CVE-2020-16898) addressed a critical vulnerability discovered in IPv6 Router Advertisement Options (called “DNS RA options”). This vulnerability resides within the Windows TCP/IP stack that is responsible for handling RA packets. Current exploitation leads to a Denial of Service (DoS) with the possibility of remote code execution.
This vulnerability affects multiple Windows versions that support IPv6 RDNSS, which was added to Windows starting with Windows 10, version 1709.
Mitigation Actions for CVE-2020-16898
As always, we recommend that our customers patch their system as soon as possible. Until a patch can be applied, Microsoft has published guidance that can be used to mitigate this vulnerability. To help clarify the guidance Microsoft has published, we have outlined the steps that should be taken to disable IPv6 RDNSS.
From an elevated privilege command prompt (such as Administrator), run the following command:
a. Netsh int ipv6 sh int
This command will provide a list of all network IPv6 interfaces with the corresponding index numbers. Example output:
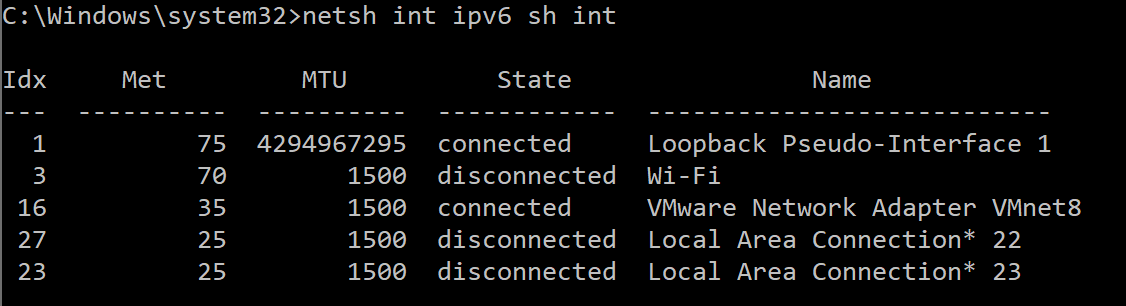
b. For each Idx number, run the command netsh int ipv6 set int Idx number rabaseddnsconfig=disable replacing Idx number with the Idx number listed from step a. This will disable the RDNSS feature for each interface, mitigating the vulnerability.
c. To verify that RDNSS is disabled, issue the following command for each of the listed Idx numbers: netsh int ipv6 sh int Idx number. This command will output the parameters for the desired interface. Example output:
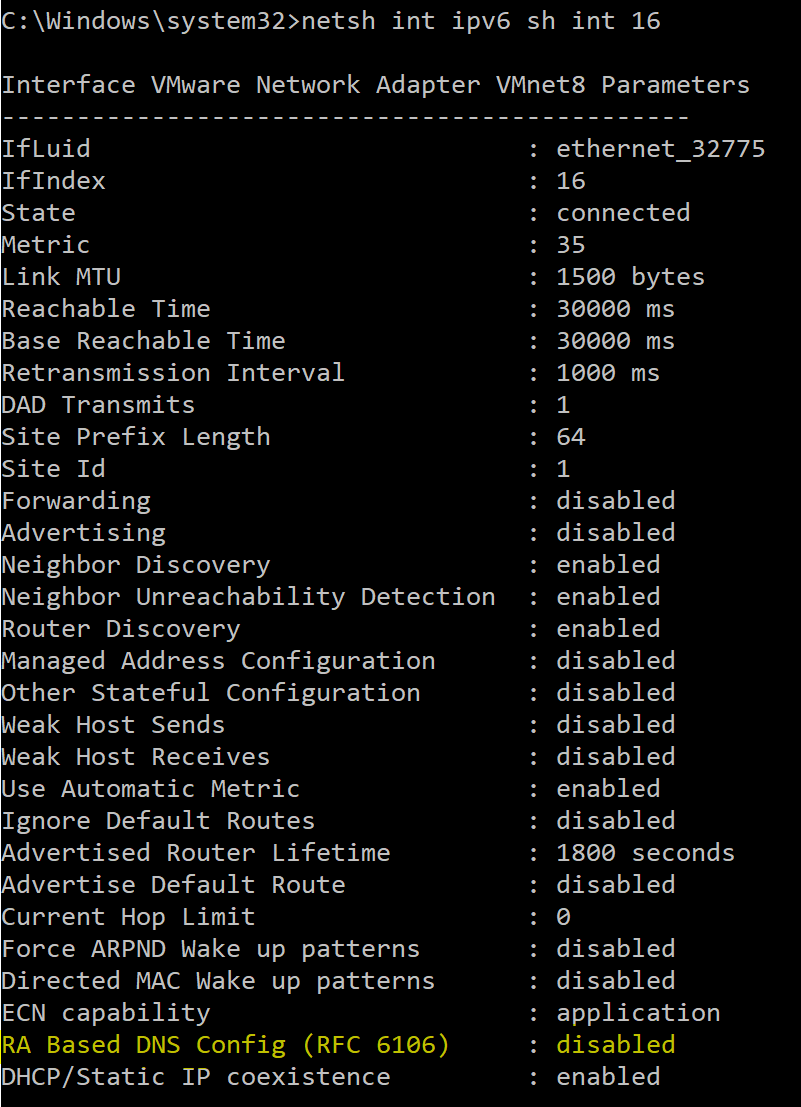
*RA Based DNS Config (RFC 6106) should be disabled for each interface.
Conclusion
The Palo Alto Networks Threat Prevention cloud-delivered security subscription provides protection against the exploitation of this vulnerability:
- Next-Generation Firewall customers with a Threat Prevention subscription and following best practices are protected against the exploitation of this vulnerability. The relevant Threat ID is 59240, and it was released with Applications and Threat content update version 8330.
Cortex XDR Pro customers can leverage the script execution capability to deploy the workaround published by Microsoft in their managed environments.
Palo Alto Networks will update this Threat Brief with new information and recommendations as they become available.












 Get updates from Unit 42
Get updates from Unit 42