Executive Summary
When launching and persisting attacks at scale, threat actors can inadvertently leave behind traces of information. They often reuse, rotate and share portions of their infrastructure when automating their campaign’s setup before launching an attack. Defenders can leverage this behavior by pivoting on a few known indicators to uncover newer infrastructure.
This article describes the benefits of automated pivoting and uses three case studies to show how we can discover new indicators. Using a network crawler leveraging relationships among domains, we discovered network artifacts around known indicators and trained a graph neural network (GNN) to detect additional malicious domains.
These three case studies show that defenders can proactively discover attack infrastructure by continuously monitoring a threat actor's evolving indicators. The three case studies covered in this article are:
- A postal services phishing campaign
- A credit card skimmer campaign
- A financial services phishing campaign
Palo Alto Networks customers are better protected from the threats discussed in this article via Advanced URL Filtering and Advanced DNS Security, which deploy proactive threat hunting capabilities to discover malicious URL infrastructure. Advanced WildFire also provides coverage for the associated samples and other indicators discussed in this post.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Malicious Domains, Deep Learning, Phishing |
Proactive Detection Through Automation
One of the best ways to defend against cyberattacks is to proactively discover a threat actor's new infrastructure based on known indicators. We can then block the associated infrastructure before they can weaponize it. Using automated detection through a GNN model can reveal hidden connections and allow earlier detection of new indicators.
Figure 1 shows an example of domains reportedly used by FIN7, a Russian threat actor we track as Squeamish Libra.
![Timeline diagram showing the registration and detection dates of various domains including myscannapp[.]com, thepjscanner[.]com, and advanced-p-scanner[.]com, spanning from August 16, 2023, to September 20, 2023.](https://unit42.paloaltonetworks.com/wp-content/uploads/2025/01/word-image-636207-138057-1.png)
The initial three fake vendor domains shown in Figure 1 are:
- advanced-ip-sccanner[.]com
- myipscanner[.]com
- myscannappo[.]com
Based on our in-house content analyzers and third-party intelligence, these domains all hosted a malicious binary named Advanced_Ip_Scanner_setup.exe posing as an installer for Advanced IP Scanner. However, it was an installer for Aranuk/Carbanak malware.
Threat actors often abuse, take advantage of or subvert legitimate products for malicious purposes. This does not imply that the legitimate product is flawed or malicious.
This threat actor also registered other domains to weaponize later. However, we pivoted on the hosting infrastructure and mapped additional domains.
Figure 2 shows a diagram mapping the infrastructure of this phishing campaign.
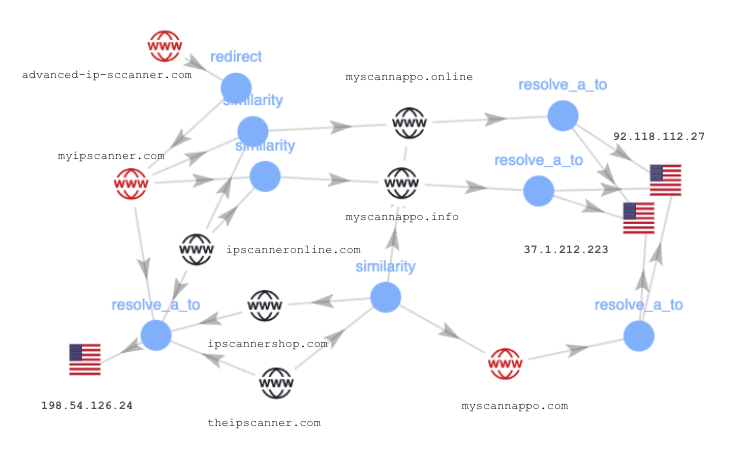
The domains with the red symbol shown in Figure 2 are the known malicious domains before we expanded the infrastructure map for this campaign. Note that we have omitted some of the nodes and edges in this diagram to more clearly show the relationships between the known domains and newly discovered domains.
We can identify new indicators through automated pivoting on known infrastructure based on:
- The relationships between different types of indicators
- Pivoting on these relationships using GNN
Relationships Between Different Types of Indicators
We can pivot on existing infrastructure based on the relationship between different types of indicators. These indicators are:
- Co-hosted domains
- Malware delivery URLs
- Command-and-control (C2) domains
- HTTPS certificates for domains
- HTTPS certificates for IP addresses
- Phishing kits
Co-Hosted domains: To orchestrate large-scale attacks, threat actors often register numerous domains and rotate through them over time, typically using similar hosting infrastructure. For example, the group behind a malicious link shortening service nicknamed Prolific Puma has registered thousands of domains to evade detection. This group further obscured its activity by abusing shared hosting services. Despite these evasion tactics, strong connections remained between older and newer Prolific Puma domains because they were simultaneously hosted on multiple IP addresses.
Malware delivery URLs: Threat actors occasionally use different URLs to distribute the same malware file. Pivoting on a malware file can reveal new delivery URLs from a different source.
C2 domains: Malware binaries can connect to multiple C2 domains, either simultaneously or rotating over time. Investigating these domains can reveal a history of IP addresses hosting the servers using these domains.
HTTPS certificates for domains: SSL or TLS certificates are used by web servers for identity validation and establishing secure HTTPS connections. All modern web browsers require a valid certificate for HTTP traffic, and phishing websites must have a valid certificate to successfully impersonate a legitimate brand. To automate and scale a campaign, threat actors often acquire these certificates in bulk. Therefore, we can pivot on the fingerprints (sometimes called thumbprints) of these certificates to find other domains from the same campaign or threat actor.
HTTPS certificates for IP addresses: Since domains are used by servers hosted on IP addresses, these SSL/TLS certificates also apply to the associated IP address. In some cases, a web server or URL might not have a domain name and will use an IP address directly. Either way, we can search for fingerprints of HTTPS certificates across different IP addresses to discover additional infrastructure. For example, since the Russian invasion of Ukraine, multiple IP addresses hosting content from Russian threat actor Trident Ursa had the same fingerprint for self-signed certificates used during HTTPS traffic.
Phishing kits: Phishing kits are often discovered in the wild as ZIP archives that contain templates used to create phishing sites that impersonate login pages of a famous company or brand. Criminals often purchase these through phishing-as-a-service operations like 16shop. They can then deploy the same phishing kit to multiple domains and their associated servers. We can identify these by searching for all domains associated with a particular phishing kit.
For an ongoing campaign, we can examine the relationships between these different types of indicators to discover new infrastructure. This is a time-consuming process if done manually, but we can automate the analysis through methods like GNN.
Pivoting Through GNN
A single correlation or association between two malicious domains does not necessarily mean these are part of the same campaign. For example, domains hosted on servers using the same IP address could be an example of shared hosting, where hundreds of domains use the same IP address.
However, multiple associations between two malicious domains indicate a shared infrastructure. For example, two domains having the following qualities indicate they are most likely part of the same campaign:
- Shared same hosting provider
- Distribution of the same malware file
- Registration through the same registrar on the same day
The more associations, the stronger the relationship between the domains.
We can leverage this insight to gather as many correlations as possible between different domains and determine which are part of the same campaign. In addition to the indicators we've already discussed, further attributes like lexical patterns, hosting duration and content structure can also solidify the relationships between domains.
Using this insight, we can pivot from a small, seed set of known indicators to discover additional network artifacts. We do this for our internal detection by training a GNN classifier. Figure 3 shows a high-level flow chart of our pipeline.

From the seed domains, we construct a graph that expands the information to include other known network artifacts. This enriches each graph node with discriminating features.
We extract these features to train a GNN classifier to detect new domains with high confidence. You can learn more about our approach in our recent Virus Bulletin 2024 talk and recent research publication [PDF] for the RAID 2024 International Conference.
Case Studies
We have used our GNN approach for detection during the past several months. The results indicate that threat actors tend to progressively register new domains over time. The attackers often reuse hosting infrastructure and domains, often using many domains during a short time window.
The following three case studies provide examples of this threat actor behavior.
Postal Service Phishing
We have tracked a large network of malicious infrastructure used for phishing websites impersonating national and private postal/package delivery services worldwide. Starting with a few hundred malicious domains, we've identified nearly 4,000 domains hosted on approximately 1,200 IP addresses linked to this campaign over the past year
This campaign has impersonated postal services in many countries, including:
- The U.S.
- Canada
- Israel
- India
- Pakistan
- The UK
- Spain
- Korea
- Singapore
- Australia
- Ireland
- Dominican Republic
- Mexico
- Italy
Figures 4 and 5 show a partial infrastructure mapping of clusters from this postal-themed phishing campaign totaling 61 domains and three IP addresses.
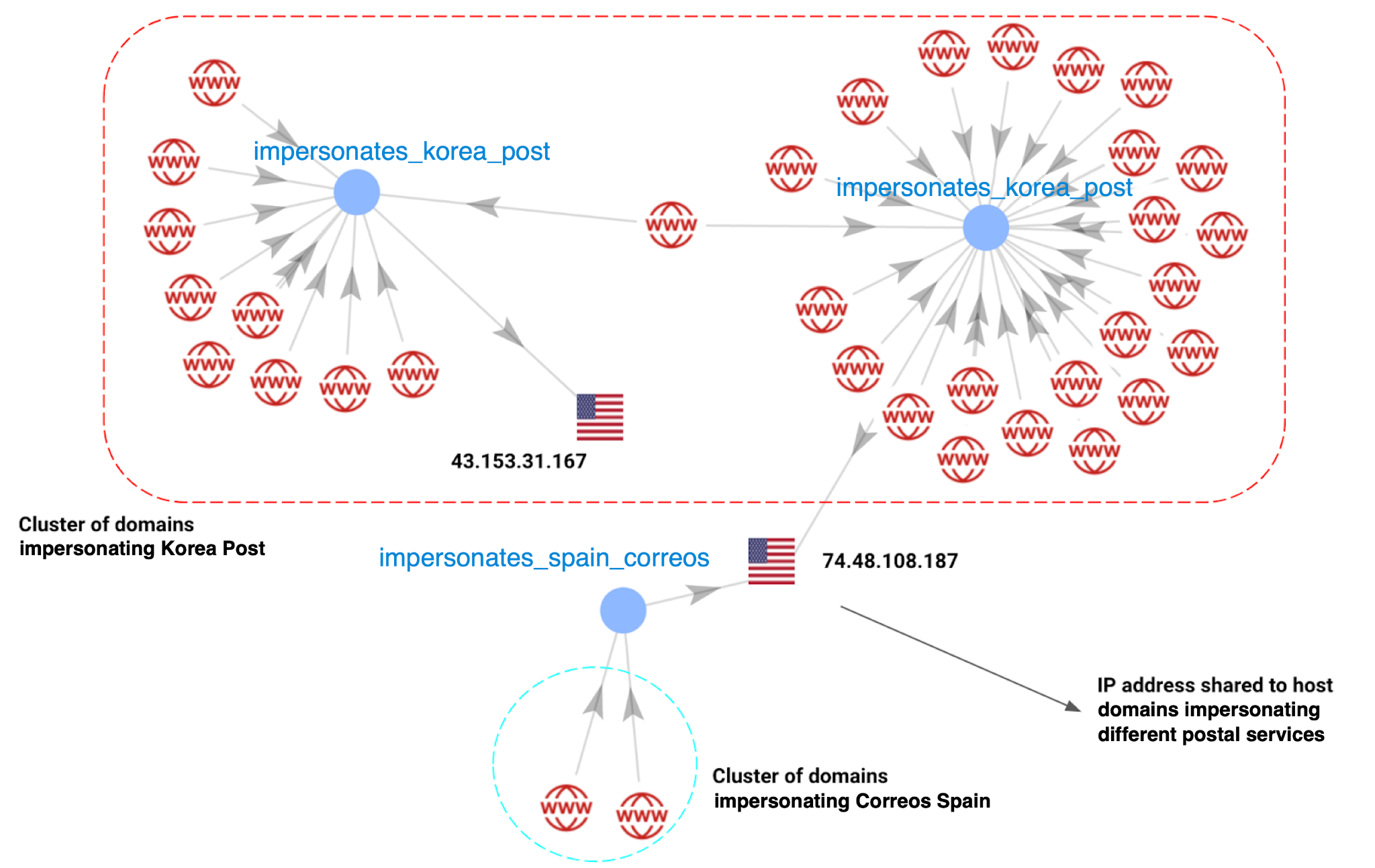
The connected components in Figure 4 highlight shared infrastructure between domains impersonating the Republic of Korea postal service (Korea Post) and Spain's state-owned postal and courier server Correos.
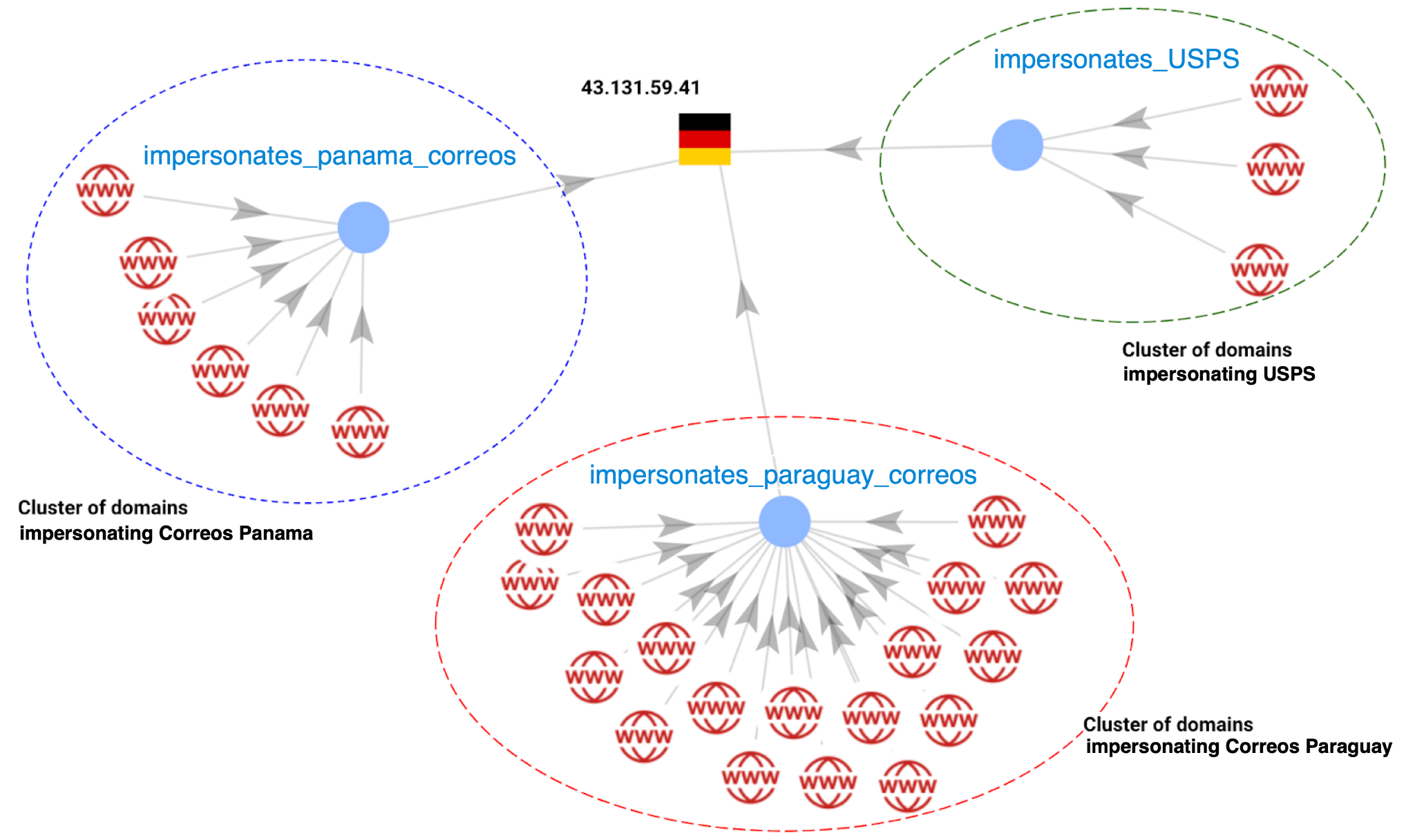
The connected components in Figure 5 show a shared infrastructure between domains targeting customers of the US Postal Service (USPS), the Panama Post Office (Panama Correos) and the Paraguay Post Office (Paraguay Correos).
We detected these domains between August 25-Sep. 20, 2024. Out of the 61 total domains:
- 33 impersonated Korea Post
- 18 impersonated Paraguay Correos
- 6 impersonated Panama Correos
- 3 impersonated the USPS
- 2 impersonated Correos Spain
These examples show that the attackers use the same hosting infrastructure to impersonate postal services operating in different parts of the world.
In another example, an IP address at 47.251.0[.]168 hosted malicious domains in September 2024 to target customers of the following postal services:
- correosesllr[.]top - Correos Spain
- inposdomag[.]top - Dominican Postal Institute (INPOSDOM)
- inposdomak[.]top - INPOSDOM
- usps.postscy[.]top - USPS
This postal-themed phishing campaign remains active throughout the year, but we noticed a trend of increased domains and hosting IP addresses from mid to late 2024. To evade detection, most domains have short windows of live activity before attackers switch to different domains, demonstrating a fast-flux pattern.
This campaign has reused IP addresses. For instance, nine unique IP addresses within the 103.120.80[.]0/24 subnet hosted a malicious domain impersonating postal services in September 2023. These IP addresses were inactive until June 2024, when attackers used them to host 11 different malicious domains impersonating postal services.
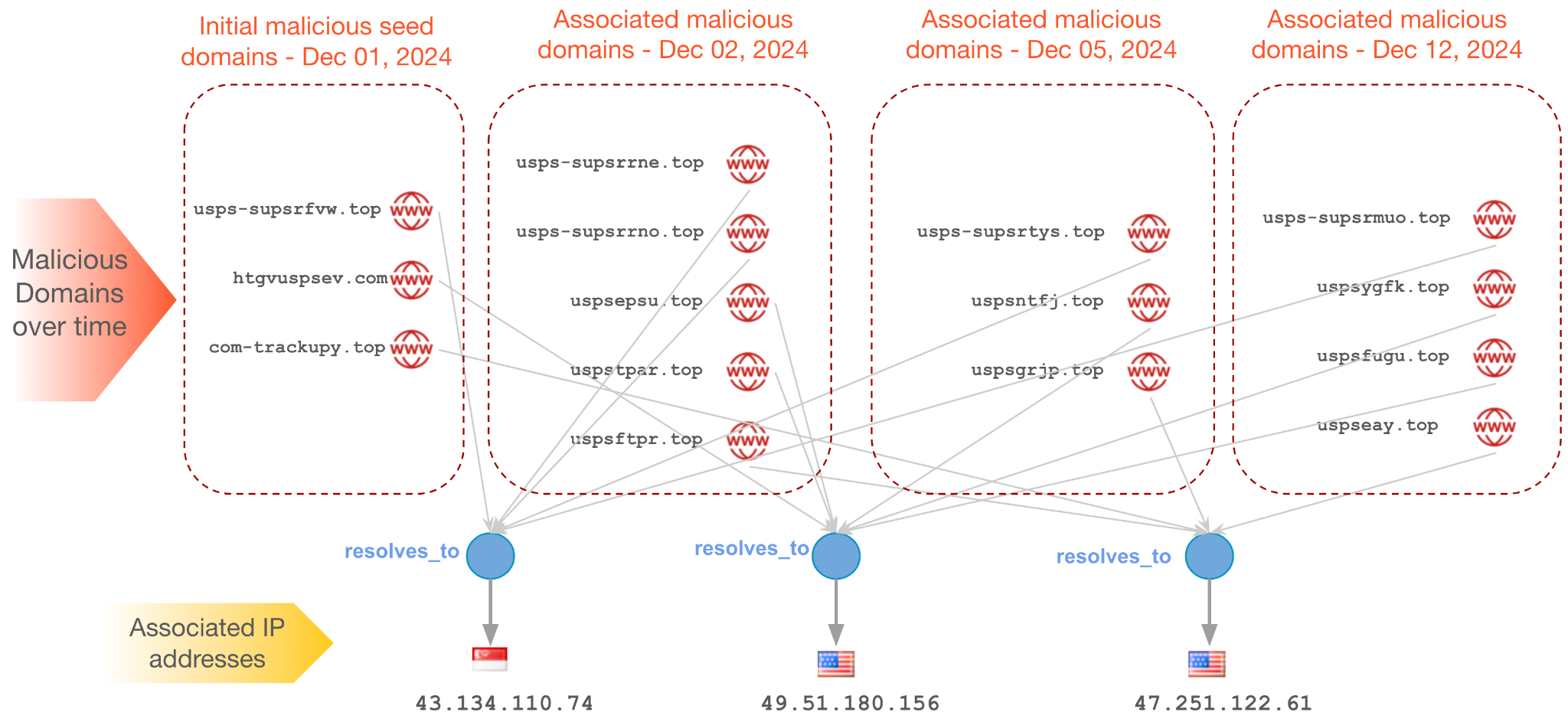
Figure 6 shows 15 malicious domains impersonating postal services discovered over a span of two weeks in December 2024. Continuous monitoring of three IP addresses associated with malicious domains detected on Dec. 1, 2024 resulted in detection of additional malicious domains as the hosting IP addresses are often reused by threat actors.
The IP address 146.112.61[.]108 hosted around 160 malicious domains last year and was reused for 11 more domains this year. This included hosting eight domains in September 2024, all targeting customers of various postal services.
URLs for these phishing campaigns host pages featuring the targeted brand's logo, with various messages as shown in Figure 7.

Examples of messages include:
- “Your package is on hold due to an invalid recipient address. Fill in the correct address using this link.”
- “Your package is stuck at customs due to unpaid fees. Click here to pay and avoid additional charges.”
Links in these initial phishing pages lead visitors to subsequent pages that request more personal information or payment details.
In a one month period from Sep. 10-Oct. 10, 2024, we detected 3,211 phishing domains associated with this campaign.
Web Skimmer Campaign
We detected a web skimmer campaign that continues to affect hundreds of commercial sites, some of which are in Tranco's list of the top 1 million sites. Attackers first compromised benign sites and installed client-side malicious JavaScript code called a skimmer.
Attackers then loaded this code on potential victims' machines when they visited pages from these sites. When victims logged in to the sites or entered their credit card, these skimmers stole the data and sent it to an exfiltration endpoint controlled by the attacker.
This campaign exfiltrated stolen data to domains with names impersonating well-known benign infrastructure. Examples of these exfiltration domains follow:
- apple.com-ticket[.]info
- cdn-google-tag[.]info
- chatwareopenalgroup[.]net
- establish-coinbase[.]com
- google-site-verification[.]com
- jquerylib-min[.]net
- ssl-google-analytics[.]com
- staticlitycis[.]com
After detecting these skimmers on a number of websites, we used our automated GNN approach to identify an expanded infrastructure from a group of seed indicators. The detected infrastructure included:
- Domains that attackers had not yet weaponized
- Assets active since 2022
- Many IP addresses that were assigned to hosting providers in Russia
We identified 65 domains, 815 IP addresses and other indicators associated with this campaign since October 2023. This campaign is also active year-round.
There was a noticeable increase in hosting IP addresses in early 2024 and significant activity in June and July of 2024. Figure 8 shows a map of the infrastructure used for this campaign.
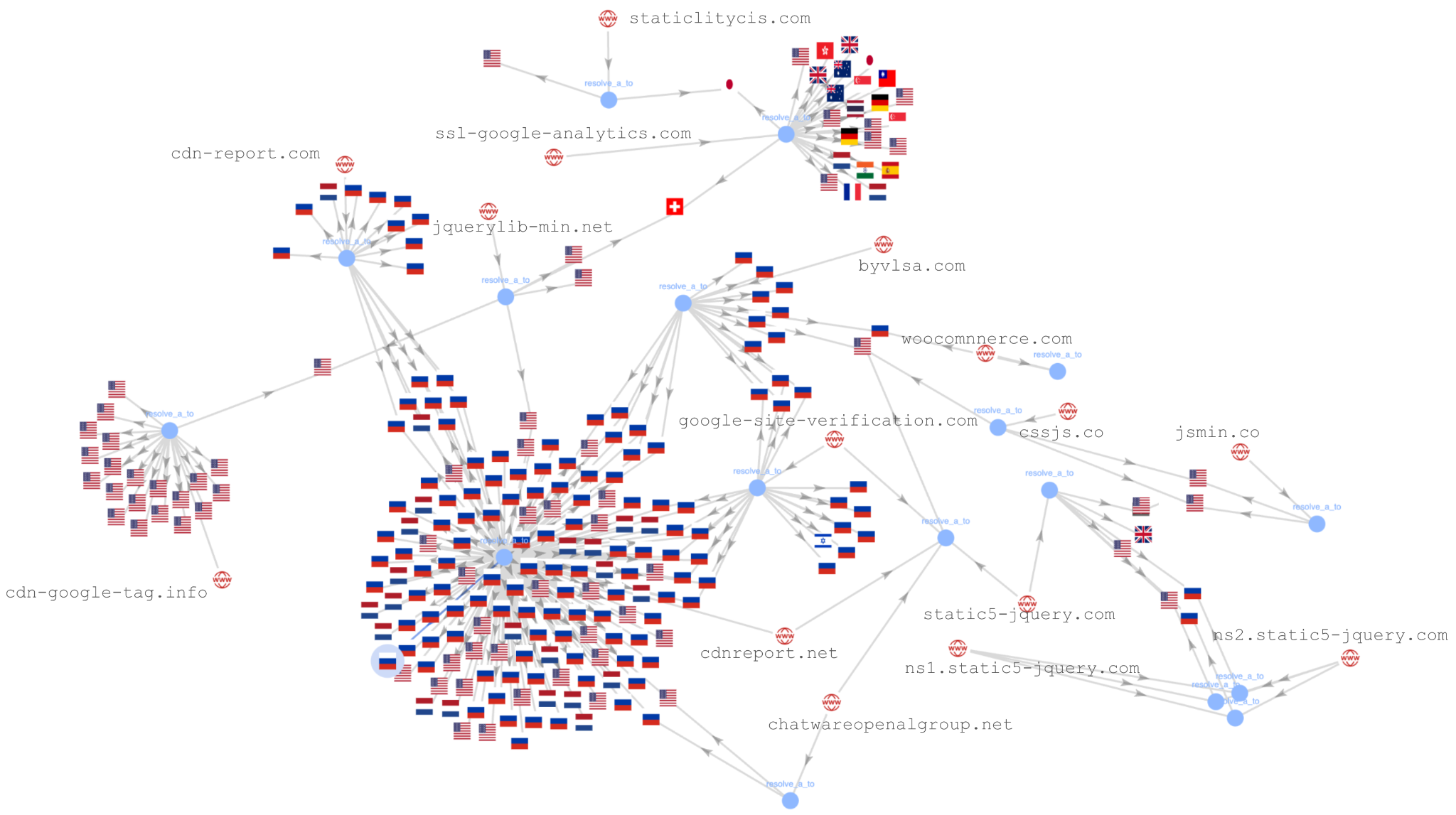
The web skimmer map in Figure 8 contains 15 domains and their hosting infrastructure consisting of 249 IP addresses predominantly operated by Russian hosting providers. Attribution is unclear at this time, but some of our current indicators overlap with those previously attributed to TA569.
Financial Services Phishing
Threat actors used a large network of attacker-controlled infrastructure for phishing websites targeting customers of banking and financial services worldwide. These campaigns spoofed financial organizations' webpages to steal personal and financial data.
From October 2023-2024, we identified approximately 5,000 domains hosted on more than 5,600 IP addresses linked to this campaign. These phishing attacks targeted customers of banking services in many countries including:
- The U.S.
- Canada
- India
- Germany
- Greece
- South Africa
- Kenya
- The UK
- Thailand
- Switzerland
Each day, we noticed dozens of domains impersonating not only well-known large-scale banks, but many regional and local banks, as well as platforms for trading and investment. Most of these malicious domains used shared hosting infrastructure. These campaigns were also active year-round.
Figure 9 shows the infrastructure mapping for one of these campaigns. It illustrates connected components for 16 domains targeting customers of various banking institutions across the world using eight IP addresses.
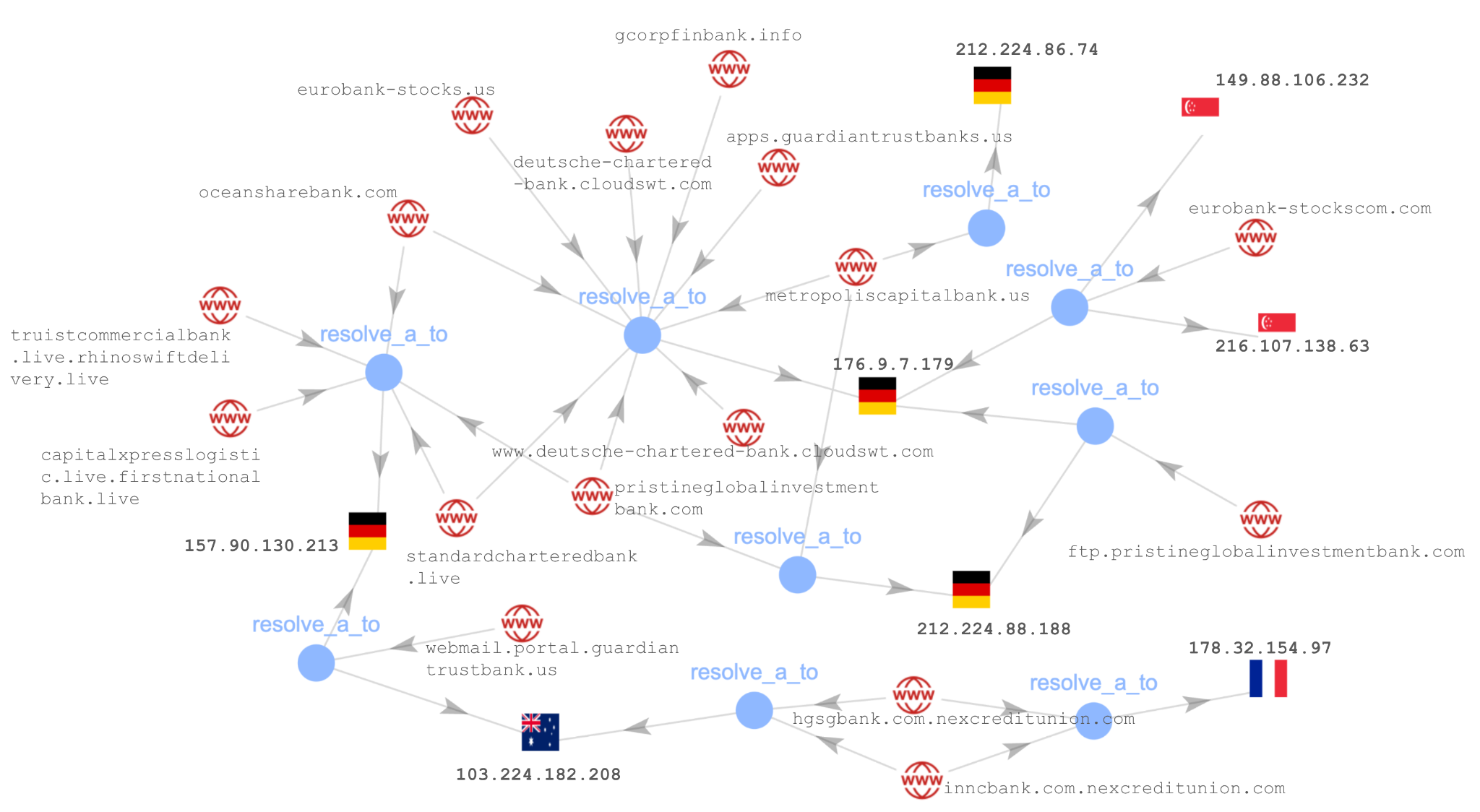
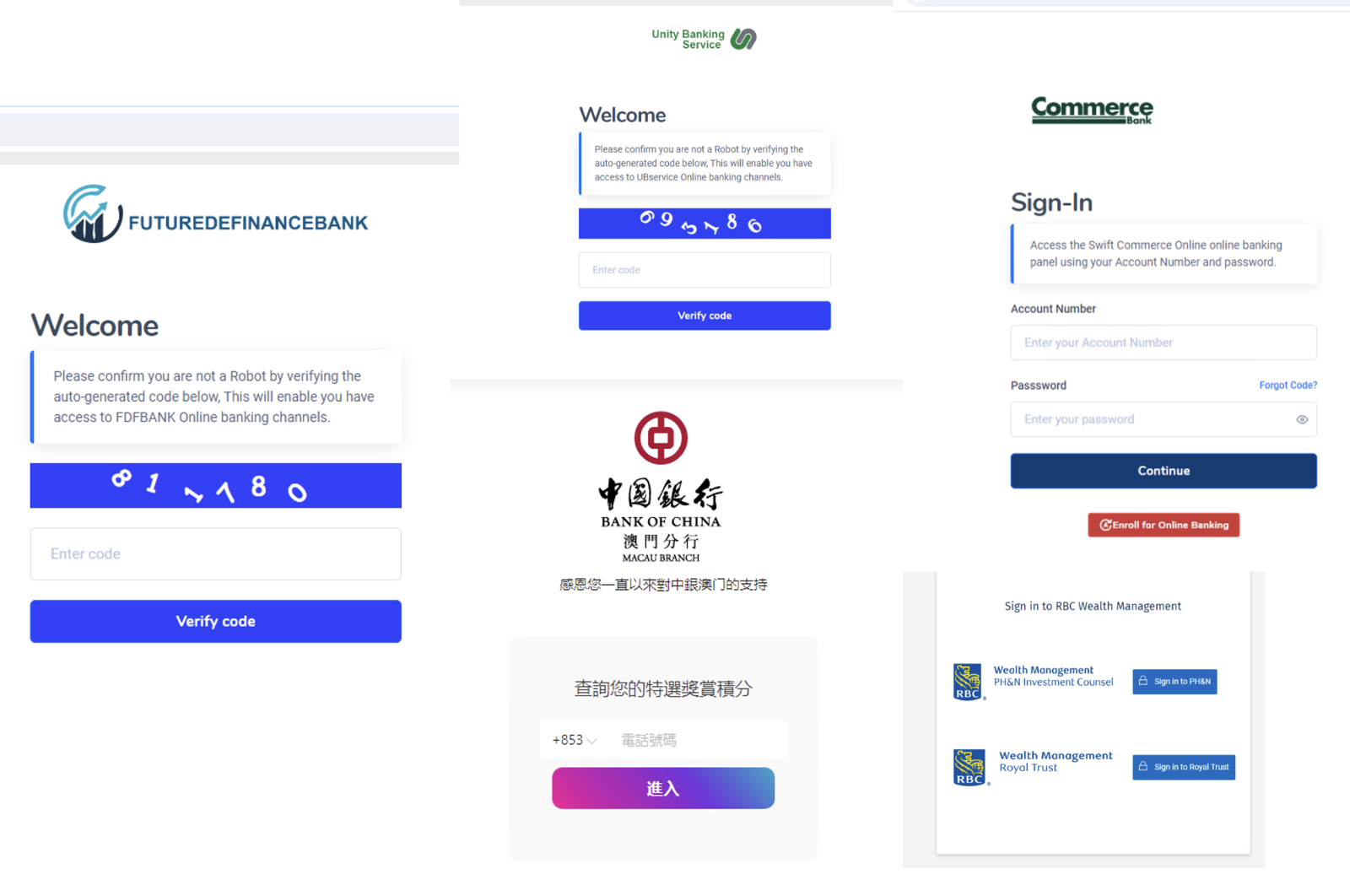
Figure 10 shows screenshots from five examples of pages for financial services phishing activity.
Conclusion
Threat actors launch large-scale attacks using extensive hosting infrastructure, but this infrastructure changes over time as the attackers attempt to evade detection. This article described our automated GNN approach to pivoting on known indicators, so we can discover new infrastructure for active campaigns before attackers weaponize it.
Our three case studies revealed that threat actors share, reuse and rotate their attack infrastructure. They likely implement these changes through an automated setup process. This process inadvertently leaves behind traces of information we can detect through proactive searching.
Palo Alto Networks customers are better protected from the threats in this article through the following products:
- Advanced URL Filtering and Advanced DNS Security deploy proactive threat hunting capabilities to discover malicious URL infrastructure
- Advanced WildFire covers the associated samples and other indicators discussed in this post
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Acknowledgments
The authors would like to thank Bradley Duncan for the thorough technical review of the article, and Doel Santos for verifying the campaigns mentioned in it. We would also like to thank the editorial team including Samantha Stallings, Lysa Myers and Erica Naone for the assistance with improving and publishing this article. The authors would also like to thank Wei Wang for her guidance in development of this work.
Indicators of Compromise
Examples of domains used in Squeamish Libra (FIN7) activity:
- advanced-ip-sccanner[.]com
- ipscanneronline[.]com
- ipscannershop[.]com
- myipscanner[.]com
- myscannappo[.]com
- myscannappo[.]info
- myscannappo[.]online
- theipscanner[.]com
Examples of domains used in postal service-themed phishing:
- correoparaguayo-myposta[.]top
- correoparaguayo-mypostf[.]top
- correoparaguayo-myposth[.]top
- correoparaguayo-myposts[.]top
- correoparaguayo-mypostvsa[.]top
- correoparaguayo-mypostvsd[.]top
- correoparaguayo-mypostvse[.]top
- correoparaguayo-mypostvsf[.]top
- correoparaguayo-mypostvsg[.]top
- correoparaguayo-mypostvsh[.]top
- correoparaguayo-mypostvsi[.]top
- correoparaguayo-mypostvsl[.]top
- correoparaguayo-mypostvsp[.]top
- correoparaguayo-mypostvst[.]top
- correoparaguayo-mypostvsu[.]top
- correoparaguayo-mypostvsx[.]top
- correoparaguayo-mypostvsy[.]top
- correoparaguayo-mypostvsz[.]top
- correosespe[.]top
- correoseswe[.]top
- correospanamaagobs-csc[.]top
- correospanamaagobs-csd[.]top
- correospanamaagobs-cse[.]top
- correospanamaagobs-csr[.]top
- correospanamaagobs-css[.]top
- correospanamaagobs-csx[.]top
- koreapostge[.]shop
- koreapostma[.]shop
- koreapostmk[.]shop
- koreapostmv[.]shop
- koreapostmx[.]shop
- koreapostmz[.]shop
- koreapostni[.]shop
- koreapostnp[.]shop
- koreapostnu[.]shop
- koreapostpc[.]shop
- koreapostpe[.]shop
- koreapostpf[.]shop
- koreapostpg[.]shop
- koreapostpo[.]shop
- koreapostpt[.]shop
- koreapostpu[.]shop
- koreapostpw[.]shop
- koreapostst[.]shop
- koreapostxb[.]shop
- koreapostxn[.]shop
- koreapostxt[.]shop
- us-usos-qwtaa[.]top
- us-usos-qwtad[.]top
- us-usos-qwtaz[.]top
- usps-supsrfvw[.]top
- usps-supsrmuo[.]top
- usps-supsrrne[.]top
- usps-supsrrno[.]top
- usps-supsrtys[.]top
- uspsepsu[.]top
- uspsftpr[.]top
- uspsfugu[.]top
- uspsgrjp[.]top
- uspsntfj[.]top
- uspstpar[.]top
- uspsyeay[.]top
- uspsygfk[.]top
Examples of domains used in web skimmer campaign:
- byvlsa[.]com
- cdn-google-tag[.]info
- cdn-report[.]com
- cdnreport[.]net
- chatwareopenalgroup[.]net
- cssjs[.]co
- google-site-verification[.]com
- jquerylib-min[.]net
- jsmin[.]co
- ns1.static5-jquery[.]com
- ns2.static5-jquery[.]com
- ssl-google-analytics[.]com
- static5-jquery[.]com
- staticlitycis[.]com
- woocomnnerce[.]com
Examples of domains used in financial services phishing activity:
- apps.guardiantrustbanks[.]us
- capitalxpresslogistic.live.firstnationalbank[.]live
- deutsche-chartered-bank.cloudswt[.]com
- eurobank-stocks[.]us
- eurobank-stockscom[.]com
- ftp.pristineglobalinvestmentbank[.]com
- gcorpfinbank[.]info
- hgsgbank.com.nexcreditunion[.]com
- inncbank.com.nexcreditunion[.]com
- metropoliscapitalbank[.]us
- oceansharebank[.]com
- pristineglobalinvestmentbank[.]com
- standardcharteredbank[.]live
- truistcommercialbank.live.rhinoswiftdelivery[.]live
- webmail.portal.guardiantrustbank[.]us
- www.capitalxpresslogistic.live.firstnationalbank[.]live
- www.deutsche-chartered-bank.cloudswt[.]com
References
- A Gentle Introduction to Graph Neural Networks – Distill
- Discriminative Feature – ScienceDirect
- Domains impersonating Postal Services – Unit 42 Timely Threat Intelligence on GitHub
- Domains Spoofing Deribit Cryptocurrency Trading Platform – Unit 42 Timely Threat Intelligence on GitHub
- JavaScript-based Web Skimmers from Legitimate Web Sites – Unit 42 Timely Threat Intelligence on GitHub
- Phishers Spoof USPS, 12 Other Natl’ Postal Services – Krebs on Security
- Proactively hunting for low-reputed infrastructure used by large cybercrimes and APTs – Virus Bulletin
- Prolific Puma: Shadowy Link Shortening Service Enables Cybercrime – Infoblox
- Revisiting 16shop Phishing Kit, Trend-Interpol Partnership – Trend Micro
- TA569: SocGholish and Beyond – Proofpoint
- Threat Group FIN7 Targets the U.S. Automotive Industry – BlackBerry Research and Intelligence Team, BlackBerry Blog
Updated Jan. 14, 2025, at 6:56 a.m. PT to add to the list of acknowledgements.












 Get updates from Unit 42
Get updates from Unit 42