Executive Summary
Unit 42 recently shared information about a new attack surface targeting Microsoft Internet Information Services (IIS) and SQL Server at Black Hat Asia 2021. In our presentation, we introduced a previously undisclosed technique to execute SQL queries on the remote database in IIS and SQL Server under SQL injection or ad hoc scenarios. We also discussed three typical cases picked from around 100 Jet vulnerabilities that we discovered in a three-month period. Here, we cover the details of the technique, which allows threat actors to remotely attack IIS and SQL Server to gain SYSTEM privilege by using Microsoft Jet Database Engine vulnerabilities.
In response to this research, Microsoft released a complex patch to mitigate this attack surface. However, the patch is turned off by default and most Jet vulnerabilities are still not patched. We highly recommend that our customers proactively turn on mitigation to disable remote tables access in the registry and stay cautious of these kinds of attacks. Besides that, the mitigation for the attack surface in Access Connectivity Engine (ACE) still remains imperfect, and we are working with Microsoft to release a complete patch for both MS Jet and ACE.
Palo Alto Networks Next-Generation Firewall customers can help mitigate such attacks by using App-ID and the Threat Prevention security subscription.
Attack Surface
The new attack surface is caused by the remote database access supported in Microsoft Jet Database Engine, including MS Jet Red (Jet Red Database Engine) and ACE (Access Connectivity Engine). It is a practical feature, but can also bring potential security issues. When misused, the feature allows attackers to execute SQL queries on the fully controlled database file on the remote attacker’s controlled server. Once the remote legitimate database file is replaced with a malformed database file, executing SQL queries on it could break the code precondition and assumptions in Microsoft Jet/ACE, leading to vulnerabilities in many Jet components.
The overall impact and break in security boundaries from these Jet vulnerabilities depend on where the SQL query is executed. The typical attack scenarios are SQL injection and ad hoc. In these two scenarios, attackers can execute any SQL queries on the malformed databases in the IIS and SQL Server. The resulting Jet vulnerabilities will impact the IIS and SQL Server. In detail, users can assign a remote database when executing SQL queries on tables by adding a database path ahead of the table in MS Jet and using OPENDATASOURCE, OPENROWSET or addlinkedserver in ACE, as shown in Figure 1.
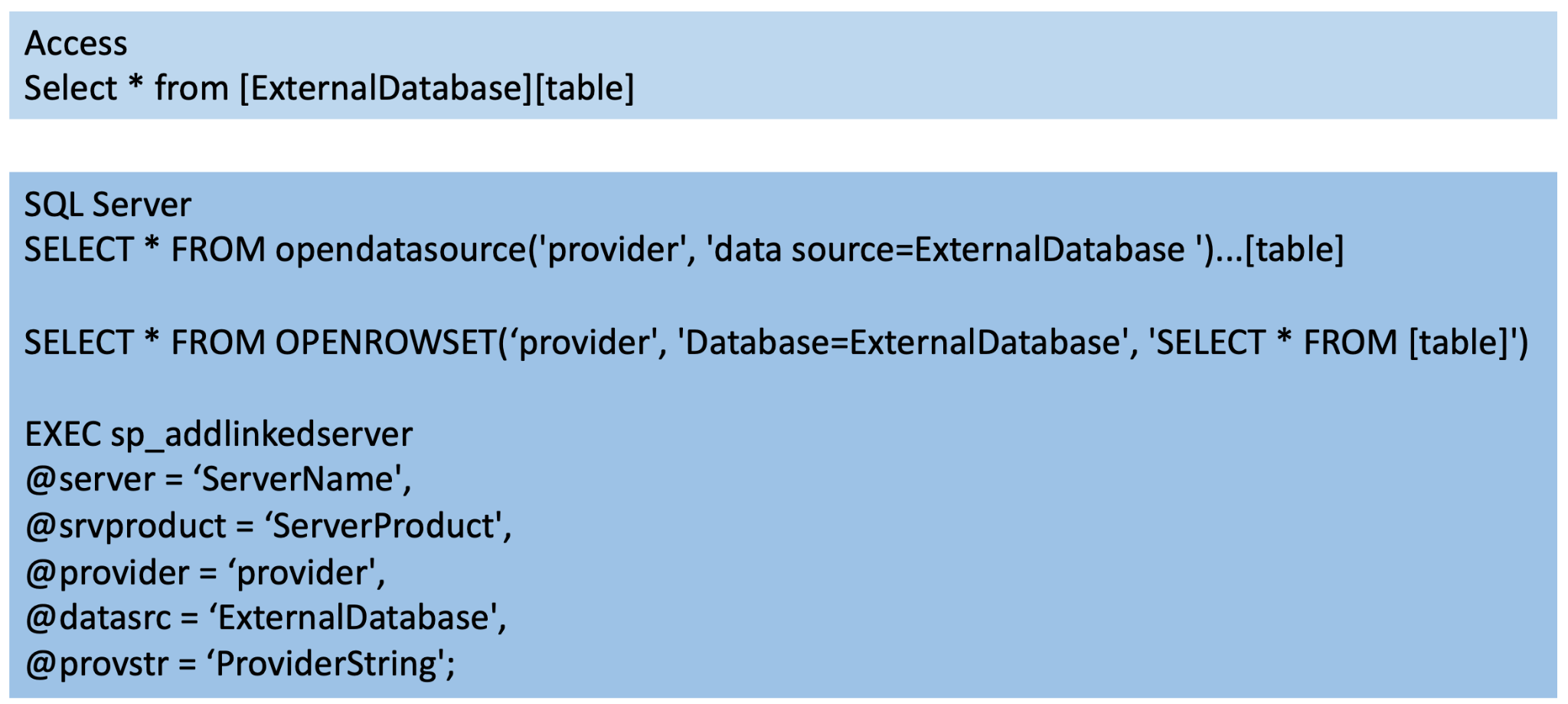
Inside MS Jet and ACE, CreateFile is called to open the remote database file in IIS and SQL Server. Given that the input path of the remote database is a UNC path, both Server Message Block (SMB) and Web-based Distributed Authoring and Versioning (WebDAV) will be used to open the remote database, as shown in Figure 2.
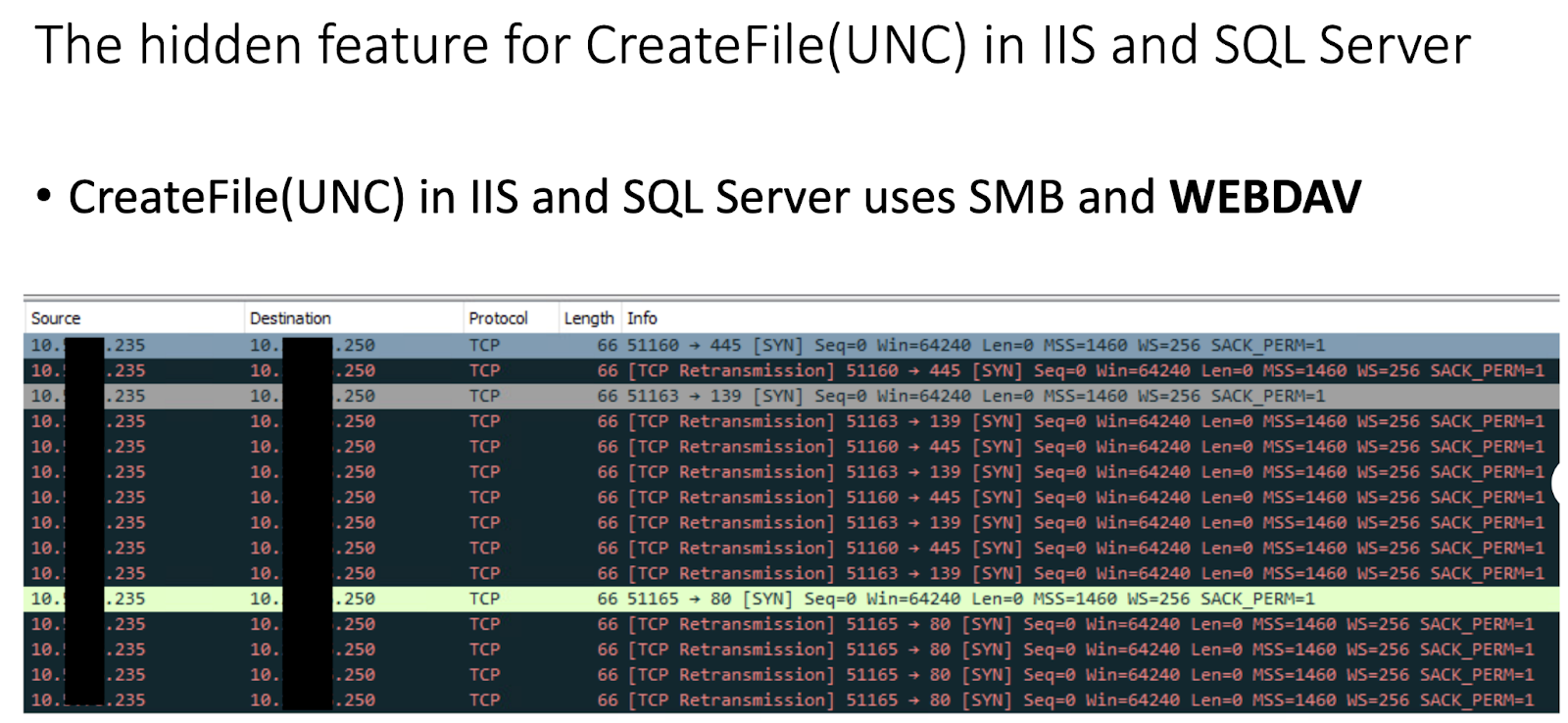
SQL injection and ad hoc are just two of the possible attack scenarios. Similarly, IIS and SQL Server are only two of the potential victims. Any components supporting MS Jet and ACE on Windows could be vulnerable, as long as the component allows users to execute any query on the controllable database with MS Jet and ACE.
Vulnerabilities in IIS and SQL Server
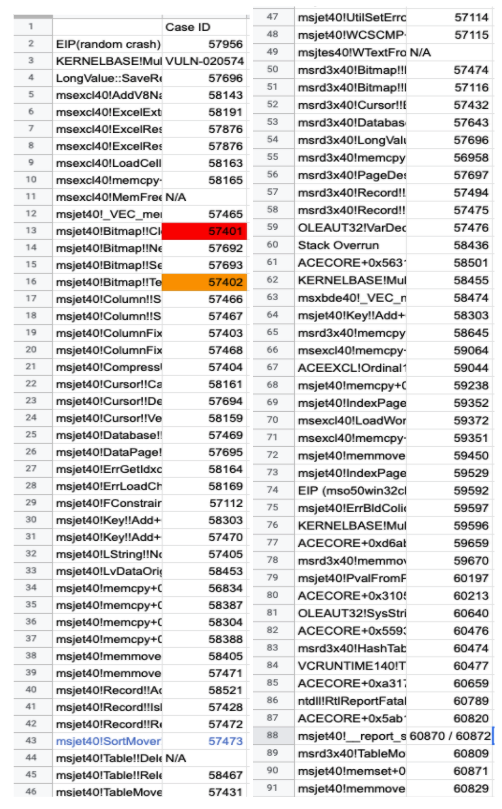
The remote database access gives attackers the capability of replacing a legitimate database with a malformed database. According to our research, replacing the database is one of the keys to finding vulnerabilities in MS Jet and ACE. Assuming that code development and testing in MS Jet and ACE might not consider the situation of the database being malformed, we had the idea of mutating both SQL queries and database files. With that fuzzing strategy, we have discovered around 100 vulnerabilities in MS Jet and ACE, as shown in Figure 3. Most of them can be used to attack IIS and SQL Server under SQL injection and ad hoc scenarios.
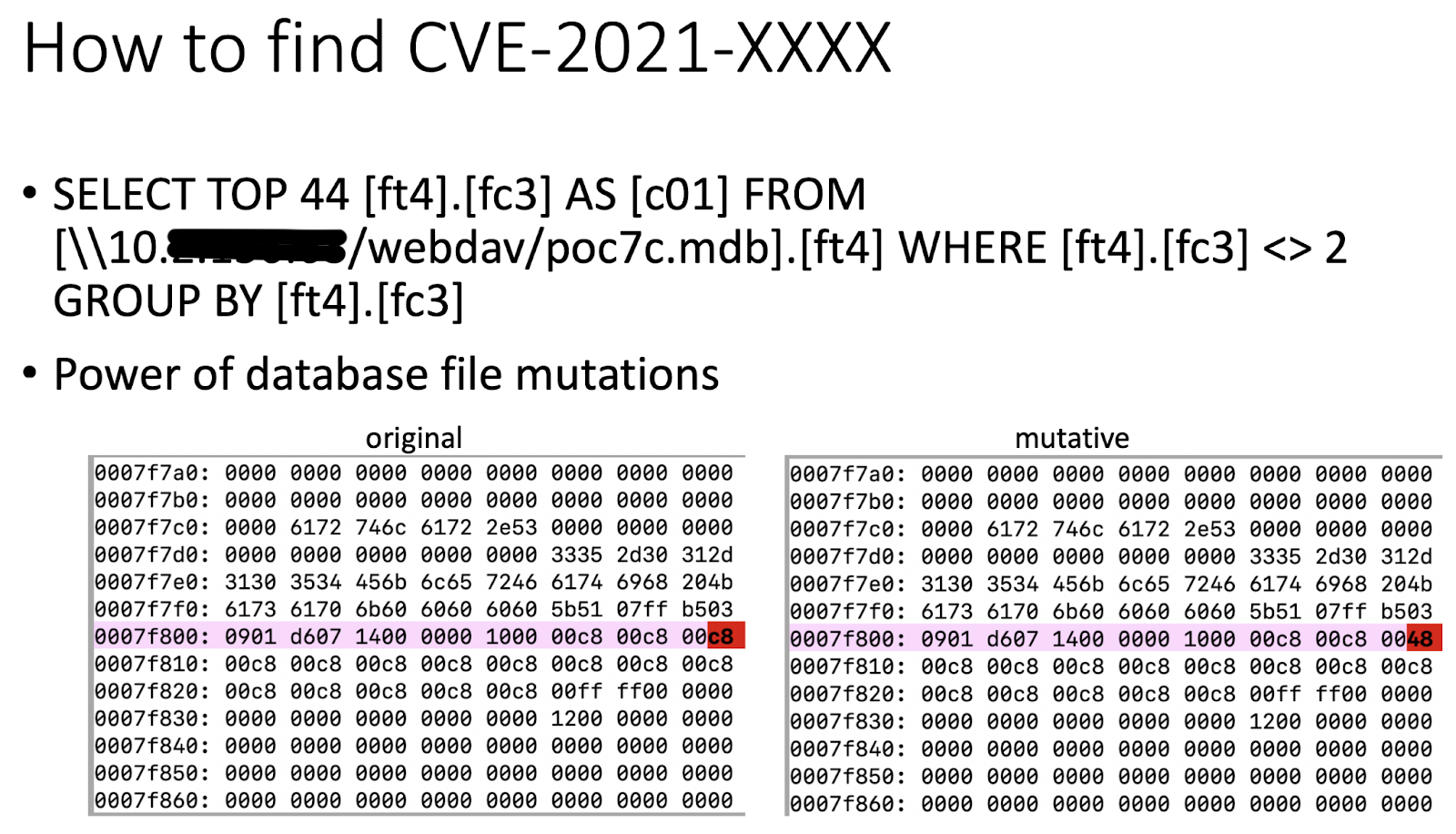
In our presentation, we proved that just one byte change in the database file can lead to an MS Jet vulnerability, as shown in Figure 4.
Microsoft Patch
With the Patch Tuesday update for Windows released in May 2021, Microsoft assigned CVE-2021-28455 to our discovery and patched the new attack surface we reported. The patch introduces an option for users to disable remote database access in the MS Jet component and ACE component. Instead of patching every single JET vulnerability, it mitigated the whole attack surface disclosed in our presentation in multiple applications that use MS Jet, such as IIS and Access.
As we can see in Figure 5, there is a new field at offset 904h in the rgtib structure (represented by ebx register) for remote database access. It is set to 1 by default in the _ltibAllocate function, which means it is enabled by default.
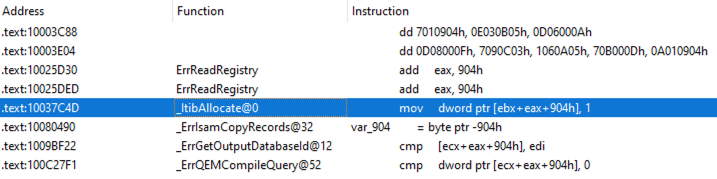
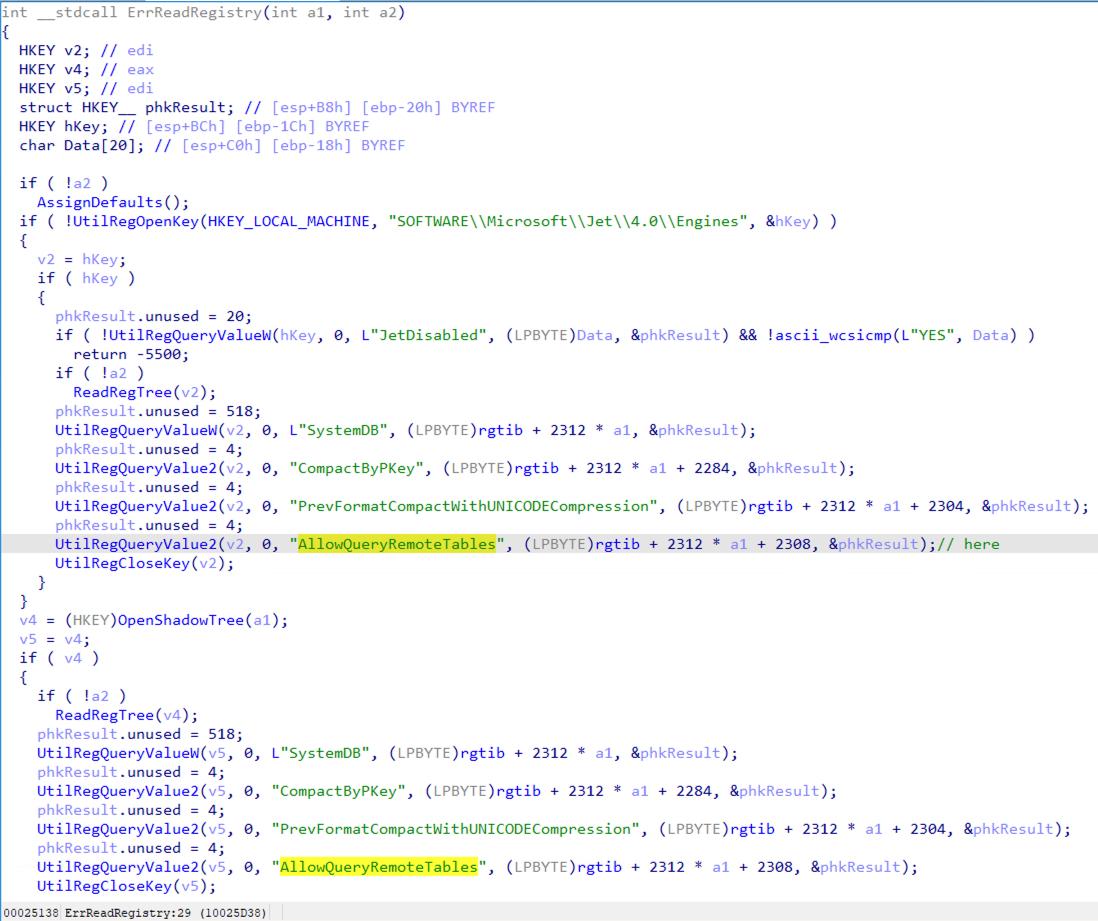
Then the UtilRegQueryValue2 function is called in the ErrReadRegistry function to get the value of the registry key – AllowQueryRemoteTables – under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Jet\4.0\engines registry entry. After that, it stores the value to the AllowQueryRemoteTables field of the rgtib structure shown in Figure 6.
After that, two functions ( _ErrGetOutputDatabaseId and _ErrQEMCompileQuery) check the AllowQueryRemoteTables field in the rgtib structure (represented by ecx register), as figure 7 depicts.
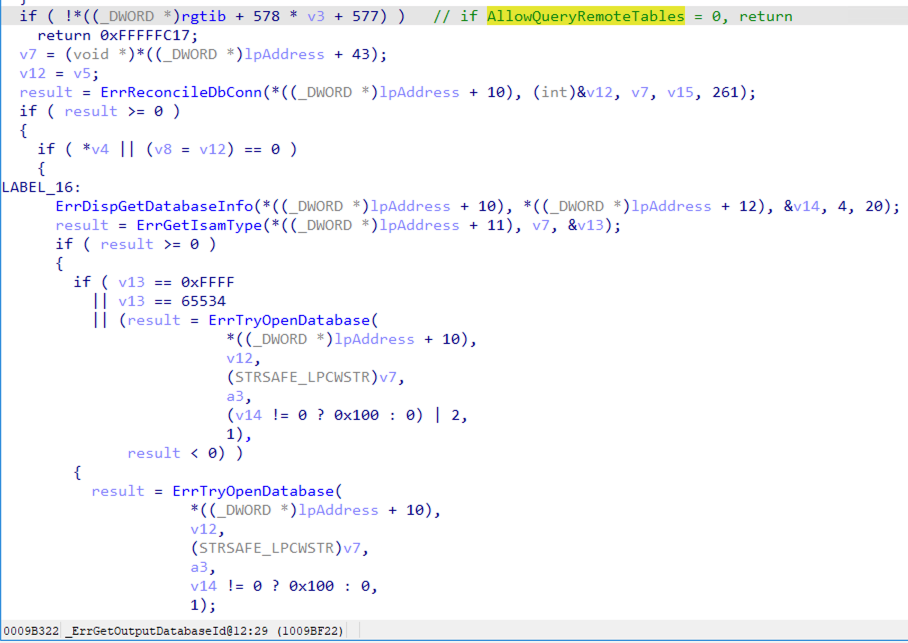
As we can see in figure 8, if the AllowQueryRemoteTables field is set to 0, then the _ErrGetOutputDatabaseId function will return an error and the ErrTryOpenDatabase function will not be invoked to open the database file, regardless of whether the database file is remote or local. This effectively mitigates the remote database access attack surface.
However, this feature is not turned on by default. To disable remote database access, users need to add a registry, named AllowQueryRemoteTables, in corresponding registries as described in this Microsoft document and set the dword value to 0.
Next-Generation Firewall Mitigations for CVE-2021-28455
Palo Alto Networks Next-Generation Firewall customers can configure their Security Policy Rule settings to protect themselves from attacks related to CVE-2021-28455 by blocking WebDAV traffic from traversing from the trusted to untrusted zones.
How to configure App-ID to drop WebDAV packets:
Step 1: Create a Security Policy Rule.
1. Select Policies > Security and Add a new rule.
2. Enter a Name for the rule and add an optional Description.
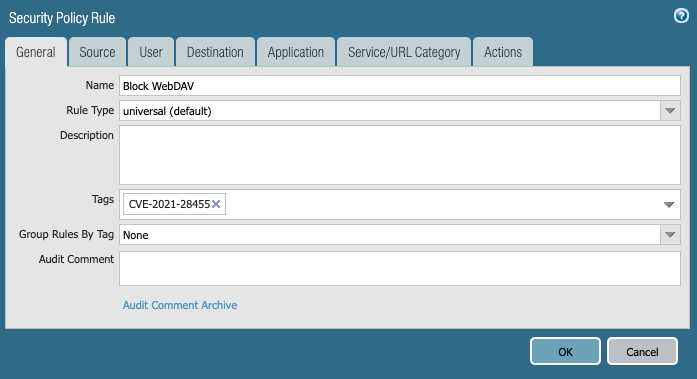
3. On the Source tab, add “trust” to the Source Zone.
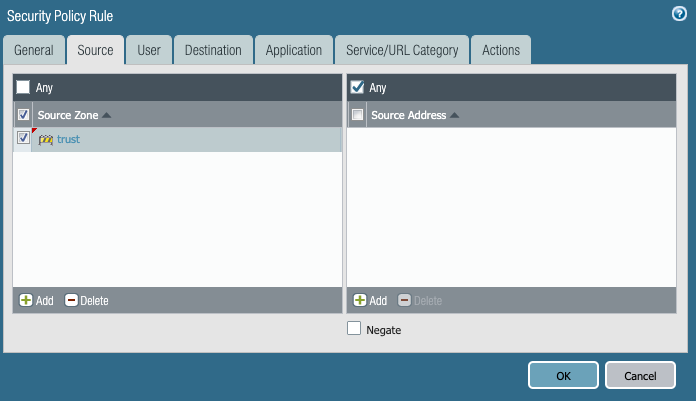
4. On the Destination tab, add “untrust” to the Destination Zone.
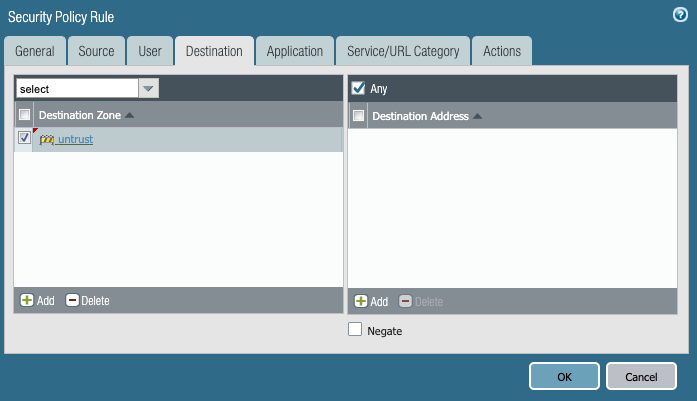
5. On the Application tab, add WebDAV to the Applications.
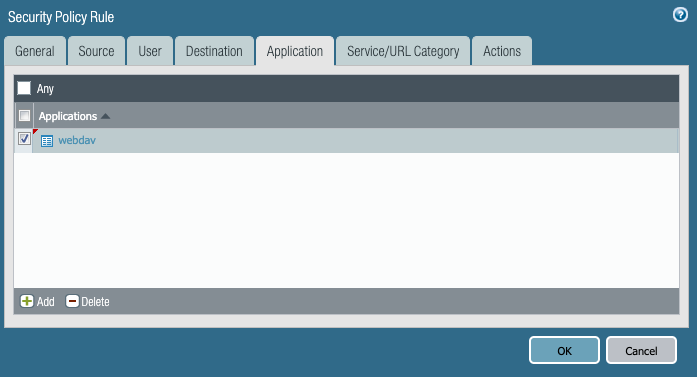
6. On the Actions tab, use Drop action in Action Setting.
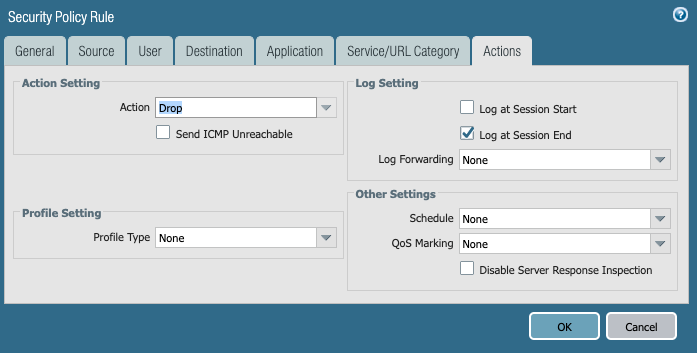
7. Click OK.
Step 2: Commit your changes.
Conclusion
IIS and SQL Server are examples of fundamental components in the Microsoft ecosystem that have been widely deployed in many production systems and services. Microsoft Jet Database Engine, including MS Jet and ACE, are over 20 years old, and a vast majority of the Jet modules have been found to be easily exploitable due to limited exploit mitigations. The remote database access feature connects the Jet vulnerabilities with IIS and SQL Server components, thereby downgrading their security to the same level as the Jet Database Engine. Attackers could potentially leverage this feature to attack IIS and SQL Server and get SYSTEM privilege remotely from a single SQL injection.
Palo Alto Networks recommends all of our customers follow the Microsoft guidance and disable remote database access to mitigate this severe attack surface. This can help prevent attackers from using Jet vulnerabilities to compromise IIS and SQL Server. Palo Alto Networks Next-Generation Firewalls can help mitigate such attacks by using App-ID and the Threat Prevention security subscription.












 Get updates from Unit 42
Get updates from Unit 42