Executive Summary
A large number of IP cameras and surveillance systems used in enterprise networks were recently discovered to be vulnerable to remote code execution and information leakage due to CVE-2021-28372, a vulnerability in the built-in ThroughTek Kalay P2P software development kit that is used by many of these devices. Many users of IP cameras and surveillance systems are unaware of the built-in software and TCP/IP stacks in their devices, and can overlook related vulnerabilities as a result.
Here, we cover how this specific vulnerability affects certain IoT devices.
In addition, this example highlights a big-picture problem for IoT devices. Vulnerabilities in built-in third-party technologies, many of which are not continuously maintained or are using legacy software, can leave IoT devices vulnerable in turn. This necessitates having proper visibility into devices in an enterprise network, as well as proper risk and vulnerability assessment.
Palo Alto Networks customers receive protections against the vulnerabilities discussed here from the IoT Security platform.
| CVE Discussed | CVE-2021-28372 |
| Related Unit 42 Topics | IoT security, supply chain |
Background on CVE-2021-28372
Cybersecurity researchers identified a vulnerability in August 2021 that affects devices using the ThroughTek Kalay P2P Software Development Kit (SDK). Attackers can exploit this vulnerability to impersonate a device running ThoughTek Kalay SDK by using a 20-bit unique identifier. This would allow a malicious attacker to hijack a victim’s connection, extract credentials from the traffic and gain unauthorized access to sensitive information on it. The ThroughTek Kalay SDK is built into various IoT devices, specifically IP cameras, video recorders and baby monitors. It is also used in various mobile and desktop applications on end-user devices.
A majority of IoT devices using the vulnerable SDK are associated with real-time video and audio feeds. A successful attack on a device can leak private video or audio and result in the device being spoofed or its certificate being hijacked. CVE-2021-28372 has been assigned to this vulnerability with a CVSS score of 9.6. For more details, read the ICS-Cert advisory.
What Is ThroughTek Kalay?
ThroughTek Kalay provides an end-to-end solutions platform for various IoT devices. The platform can be leveraged by various IoT vendors, OEM and chip manufacturers to create an efficient cloud service that can support various applications specific to the device type and industry. According to the product website, the ThroughTek Kalay 2.0 platform is specifically used for video surveillance devices and smart home products such as IP cameras, CCTV/NVR/DVR, low-power cameras, visible doorbells and security light cameras. It is also used for smart robots, routers, storage/NAS devices and household appliances. The ThroughTek Kalay client base ranges from consumer brand manufacturers to hardware manufacturers.
The ThroughTek Kalay platform uses P2P technology to create a decentralized architecture to enable IoT cloud services specifically suited for smart homes. According to ThroughTek Kalay, their SDK is in use on 86 million online devices and makes over 1.1 billion monthly connections to their cloud servers.
Who Does Your IoT Device Talk to?
The ThroughTek Kalay platform provides P2P connection functionality and allows P2P connections to the IP camera behind the Network Address Translation (NAT) table. The P2P connection is used for communication between IP cameras, sharing of APIs between IP cameras and servers and to prevent having a single point of failure by making it possible for devices to connect to multiple servers.
Many vendors, often IP camera manufacturers, produce devices that use ThroughTek Kalay’s platform. By reviewing crowdsourced data from organizations using Palo Alto Networks IoT Security, we found a number of popular IP camera vendors that use ThroughTek Kalay’s platform. However, since the Kalay platform establishes a P2P connection between devices, certain master servers are used to establish these connections. Whenever a device using ThroughTek’s services boots up, it sends call home messages to one of the many ThoughTek Kalay’s Internet of Things Cloud (IoTC) platforms using a random UDP port (between 10000 and 19999) to traverse the NAT.
The connections to these master servers can give an indication of which IoT devices are actively connecting to the ThroughTek service to establish a P2P connection. However, this does raise certain concerns. A consumer buying a product from a specific vendor does not necessarily expect or have any awareness of their traffic being sent to these types of international servers via a third party.
This is where CVE-2021-28372 comes in. For this example, we inspect traffic from IP cameras and surveillance systems built with the ThoughTek Kalay’s IoTC platform. When the device is booting up, the first function it calls is IOTC_Initialize. This makes a UDP request to one of the ThroughTek Kalay master servers: *.iotcplatform[.]com over random UDP ports in the range 10000 to 20000.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
public int initIOTC() { if(ms_nIOTCInit!=IOTCAPIs.IOTC_ER_NoERROR) { intport=(int)(10000 + (System.currentTimeMillis()%10000)); ms_nIOTCInit=IOTC_Initialize(port,"50.19.254[.]134", "122.248.234[.]207", "m4.iotcplatform[.]com", "m5.iotcplatform[.]com"); actMainView.setLog("IOTC_Initialize(.)="+ms_nIOTCInit+", udpPort="+port); mLanSearch(); return ms_nIOTCInit; } return 0; } |
As the code snippet above shows, the initialization involves a random port generation, followed by connection to one of four different IP addresses. However, based on our research into crowdsourced data, we found there are more than 14 different IP addresses the IoT devices connect to in order to initiate the P2P connection.
![The figure shows the typical network connections made by an IP camera. On the left side, in blue, it shows IP Camera Device: 50, Internet: 40, Intranet: 10. On the right side, in gray and orange, the figure shows NTP Server: 5, DNS Server: 5, device-api.ip-camera-vendor[.]com (TCP): 15, m4.iotcplatform[.]com (UDP): 15, certificate update server (SSL): 10](https://unit42.paloaltonetworks.com/wp-content/uploads/2022/03/word-image-46.png)
- An IP camera produced and sold by a US manufacturer is set up in an enterprise network.
- The device makes a connection to the API of the device manufacturer – which is an expected traffic destination.
- device-api.ip-camera-vendor[.]com
- In addition, the same device makes UDP connections to the third-party master servers to establish a P2P connection.
- m4.iotcplatform[.]com
Investigating the underlying network traffic that makes the device vulnerable to CVE-2021-28372 highlights a bigger issue in IoT devices overall. A product bought from one specific vendor makes connections to the internet to third-party websites or international destinations – often without the consumer being aware of it.
IoT Supply Chain Increases Attack Surface of Devices
Enterprise companies and consumers procure and operate IoT devices from various vendors in their networks. However, most IoT devices have underlying third-party real-time operating systems (RTOS), TCP/IP stacks, embedded Bluetooth stacks or other SDKs that can impact the device risk and increase its attack surface. In the recent past, we have seen a slew of such vulnerabilities that affect IoT device components. This includes TCP/IP stack vulnerabilities like Amnesia:33, Ripple:20 and Infra:Halt, RTOS vulnerabilities like Nucleus:13 and Bluetooth attacks like Sweyntooth, Braktooth and Bleeding Tooth specifically target IoT devices in various industry verticals such as manufacturing, retail, healthcare and others.
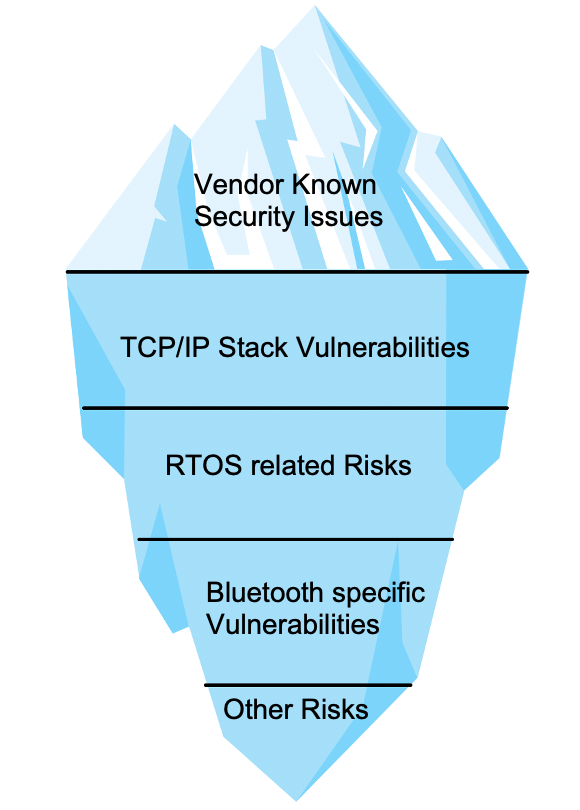
As we can see in Figure 2, the various underlying components present an hidden-iceberg problem, where the tip of the iceberg (the part above water) is known to consumers, but a large part is hidden and hence unknown to the consumer. For example, if a specific device has no known vendor vulnerabilities, many customers assume the device is safe. However, there might be deeper issues that can only be understood by monitoring the traffic and connections made by the device, as is the case with ThroughTek Kalay’s SDK-related CVE. All these components, while contributing to the overall functionality of the device, increase the chances of the device being attacked by malicious actors and expose the network to risk.
What’s Next: Proactively Secure IoT Devices
Securing the ever-expanding IoT attack surface requires proper device visibility, understanding of the various networking connections being made, monitoring of device behaviors and proactively notifying customers of risks in their network.
This is where an IoT Security platform can help. Organizations should seek an approach that helps pinpoint devices in your inventory that contain vulnerabilities – whether from the vendor or from built-in third-party software. Based on traffic observed between, for example, various IP cameras and internet destinations (specifically IoTC platforms), potentially vulnerable devices should be flagged.
Here are some key capabilities that an IoT security platform should provide to tackle similar vulnerabilities in IoT devices.
- Accurate discovery and inventory: Teams must be enabled to quickly discover, locate, and assess utilization of IoT devices. Accurate detection of a device down to vendor, model and firmware is crucial for any security steps that follow.
- Holistic risk assessment: Holistic risk assessment helps security teams proactively find security threats and vulnerabilities. A system capable of delivering machine learning-driven insights can help establish a behavior baseline and provide a deep risk assessment. This could include watching for threat indicators (e.g., an abnormal connection between devices or the presence of malicious files). It could also mean monitoring for issues such as default passwords, end of life operating systems, apps or devices, and obsolete protocols. It’s also important to monitor CVEs and assess them in context. Finally, a risk assessment strategy can be strengthened by extended capabilities achieved through integrations with third-party vulnerability management systems such as Qualys, Rapid 7 and Tenable to scan for additional vulnerabilities in IoT devices.
- Apply risk reduction policies: Real-time risk monitoring, reporting and alerting are crucial for organizations to proactively reduce IoT risk. Consistent profiling of device activity and behavior yields data that can be accurately converted into risk-based Zero Trust policy recommendations. This approach enables security teams to confidently allow only trusted behavior and, if necessary, implement proper segmentation to reduce attack radius.
- Prevent Threats: Built-in prevention capabilities help block known targeted IoT malware, spyware, and exploits, preventing the use of DNS for command and control (C2), and stopping access to bad URLs or malicious websites to help prevent the loss of sensitive data.
Conclusion
A recently discovered vulnerability in the ThroughTek Kalay P2P SDK gains significance when considering how IP cameras and surveillance devices use this specific third-party SDK to provide P2P connection functionality. Network traffic analysis of affected devices reveal that major vendors use this specific SDK, making their devices vulnerable. However, due to the vulnerability being a part of an embedded component of the device, such connections and underlying vulnerabilities are often not exposed to the consumer.
This issue has been amplified in recent times through various exposed vulnerabilities that affect the supply chain for IoT devices. As a result, it is even more imperative for customers to have full visibility of the devices in their network, the traffic they generate and any underlying security risks associated with it.
Palo Alto Networks IoT Security can help secure enterprise networks in the ways described, and includes protections for CVE-2021-28372. In addition, the platform uses patented anomaly-detection mechanisms to detect when devices with known vulnerabilities deviate from their normal network behavior, which might indicate they've been exploited. For example, the platform generates alerts for aberrant behavior such as a sudden appearance of traffic from a new source, an unusually high number of connections or an inexplicable rash of new international connections.
Additional Resources
- Risks in IoT Supply Chain
- Know Your Infusion Pump Vulnerabilities and Secure Your Healthcare Organization
- 2020 Unit 42 IoT Threat Report












 Get updates from Unit 42
Get updates from Unit 42