In February 2016, Unit 42 published detailed analysis of Locky ransomware. We certainly weren’t the only ones who saw this malware, and many others have also reported on it. Since that time, Locky has been frequently noted in various campaigns using malicious spam (malspam) to spread this relatively new strain of ransomware.
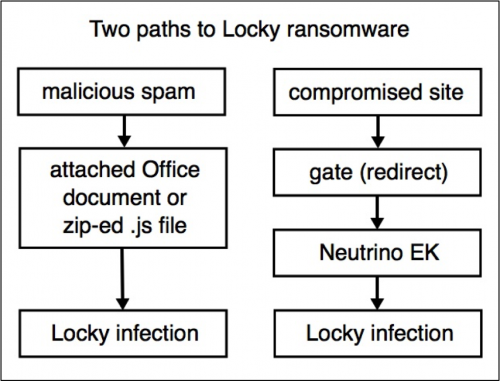
When we initially reported on Locky, attackers were distributing the malware using Microsoft Office documents with malicious macros to download and execute the ransomware. Attackers quickly added another tactic, sending e-mails with zip attachments containing malicious Javascript files to accomplish the same goal. However, exploit kits (EKs) have also been used to infect users with Locky from casual web browsing. This activity suggests that there are effectively two paths to Locky: one through malspam and another through EK traffic.
Figure 1: An example of two paths to Locky from February 2016.
The EK path is rarely mentioned. So far, we have seen very little reporting on Locky's propagation through EK traffic. Some sources noted Neutrino EK was used to send this malware, but no more has been publicly announced on the subject.
In recent days we have noticed Locky attempting to infect systems using the Nuclear EK.
Details
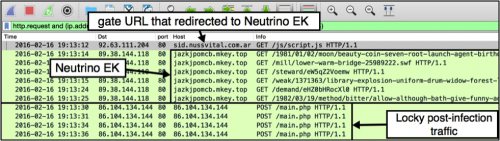
In February 2016 when Neutrino EK was first reported delivering Locky, we found a pcap of the traffic and saw the following pattern:
Figure 2: Wireshark display of Locky sent by Neutrino EK on 2016-02-16.
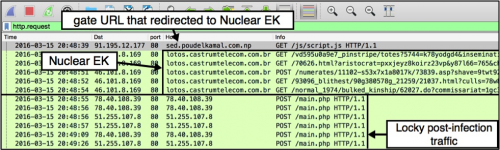
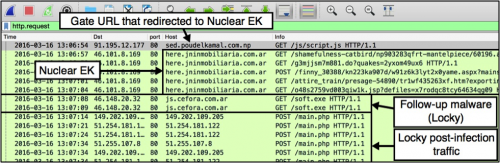
Proofpoint reported similar traffic and stated it was Locky distributed by a Neutrino EK thread known for spreading Necurs. This month, we ran across the same type of gate. This time, traffic patterns after the gate were similar to what we've seen for Nuclear EK. The payload was either Locky, or it was a downloader that retrieved Locky from another domain.
Figure 3: Wireshark display of Locky sent by Nuclear EK on 2016-03-15.
Figure 4: Wireshark display of Nuclear EK on 2016-03-16 sending a payload that downloaded Locky.
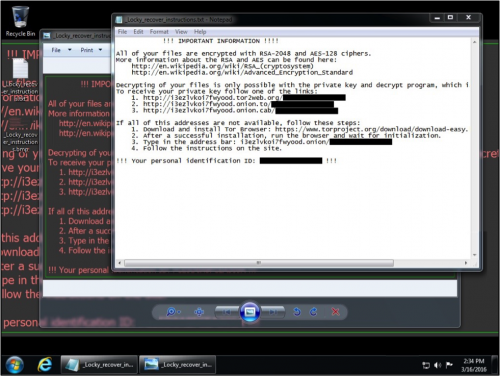
A Windows host infected with these Locky samples looks similar to previously-infected hosts when we first reported about the ransomware in February 2016.
Figure 5: A Windows host after being infected with Locky on 2016-03-16.
Conclusion
As noted in our previous blog post about Locky, Palo Alto Networks customers are protected from Locky through our next-generation security platform. WildFire continues to detect Locky, and AutoFocus identifies this threat under the Unit 42 "Locky" tag.
We continue to investigate Locky and EK traffic for applicable indicators to inform the community and further enhance our threat prevention platform.
Indicators of Compromise
Date/time range: 2016-03-15 and 2016-03-16
Gate IP address: 91.195.12.177
Gate domain: sed.poudelkamal.com.np
Nuclear EK IP address: 46.101.8.169
Nuclear EK domains: lotos.castrumtelcom.com.br , here.jninmobilaria.com.ar
Follow-up malware IP address: 46.148.20.32
Follow-up malware domain: js.cefora.com.ar
IP addresses from post-infection traffic caused by Locky ransomware:
- 51.254.181.122
- 51.255.107.8
- 78.40.108.39
- 149.202.109.205
Exploits and malware noted:
- Description: 2016-03-15 Nuclear EK Flash exploit
- SHA256 hash: 94bd74514cc9e579edf55dd1bac653ceca1837d930d109c6e701afe309b23310
- Description: 2016-03-16 Nuclear EK Flash exploit
- SHA256 hash: 4228036684f4f519704a102cd9322ac9edb1bfb5b20558a7a6873818f0e6a7b4
- Description: 2016-03-15 Nuclear EK payload - Locky ransomware
- SHA256 hash: faf4f689683f3347738ef0a8370a78d504b513d44f3a70f833c50de3d138c3b2
- Description: 2016-03-16 Nuclear EK payload - file that downloaded Locky ransomware
- SHA256 hash: a9dac0a0389c463b063cb30f647b3d1610e6052570efe2dfb1fca749d8f039fc
- Description: Locky ransomware downloaded by Nuclear EK payload (soft.exe)
- SHA256 hash: cc2355cc6d265cd90b71282980abcf0a7f3dcb3a608a5c98e7697598696481af












 Get updates from Unit 42
Get updates from Unit 42