Executive Summary
We recently identified a growing number of attacks targeting macOS users across multiple regions and industries. Our research has identified three particularly prevalent macOS infostealers in the wild, which we will explore in depth: Poseidon, Atomic and Cthulhu. We’ll show how they operate and how we detect their malicious activity.
Infostealers can sometimes be viewed as a less worrisome type of threat due to their more limited functionality compared to, for example, remote access Trojans. But by exfiltrating sensitive credentials, financial records and intellectual property, infostealers often lead to data breaches, financial losses and reputational damage. These are all things organizations need to take seriously. A recent analysis of these attacks shows that infostealers account for the largest group of new macOS malware in 2024. In our own telemetry, we detected a 101% increase of macOS infostealers between the last two quarters of 2024.
Palo Alto Networks customers are better protected against the infostealers presented in this research through Cortex XDR and XSIAM, and Cloud-Delivered Security Services for our Next-Generation Firewall, such as Advanced WildFire, Advanced DNS Security and Advanced URL Filtering.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | macOS, Infostealers |
macOS Infostealers Surge
Infostealers are a type of malware that is primarily designed to steal a wide range of sensitive information. This information ranges from financial details to the credentials of various services to sensitive files stored on the compromised hosts. Financial details can include payment card details, banking information and crypto wallets.
Most infostealers are indiscriminate, aiming to maximize data collection for impact and monetization. This broad range of information stealing capabilities exposes organizations to significant risks, including data leaks and providing initial access for further attacks, such as ransomware deployment.
Infostealers leveraging macOS often exploit the native AppleScript framework. This framework provides extensive OS access, and it also simplifies execution with its natural language syntax. Since these prompts can look like legitimate system prompts, threat actors use this framework to trick victims via social engineering. For example, they can prompt them to enter credentials or trick them into disabling security controls.
Our research, using Cortex XDR telemetry from macOS environments, identified three particularly prevalent infostealers: Atomic Stealer, Poseidon Stealer and Cthulhu Stealer.
This article focuses on these stealers, their interaction with the macOS operating system, and how our products detect their tactics, techniques and procedures (TTPs).
Atomic Stealer (AMOS)
Also known as AMOS, Atomic Stealer was discovered in April 2023. The developers of Atomic Stealer sell it as malware as a service (MaaS) in hacker forums and on Telegram.
The threat intelligence community has observed several different versions of this infostealer. Earlier versions were written in Go, and the more recent versions are written in C++. Some versions of Atomic Stealer drop a Python script, and other versions use Mach-O binaries.
The Atomic Stealer operators usually distribute their malware via malvertising. It is capable of stealing the following information:
- Notes and documents
- Browser data (e.g., passwords, cookies and more)
- Cryptocurrency wallets
- Instant messaging data (e.g., Discord, Telegram)
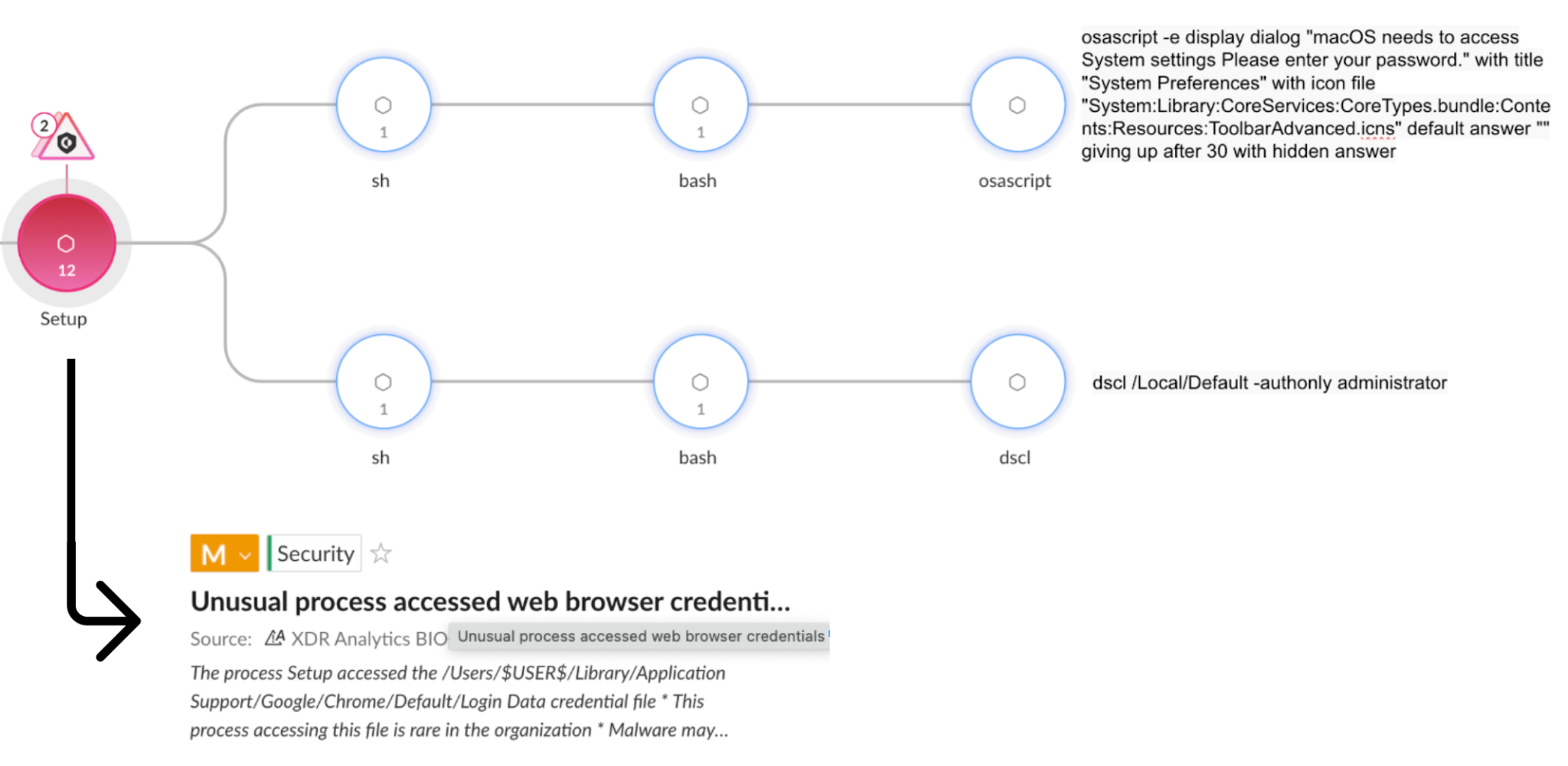
Figure 1 shows the execution flow of Atomic Stealer, during one of its operations disguised as a legitimate installation file. This threat attempted to access the file at /Users/$USER$/Library/Application Support/Google/Chrome/Default/Login Data, which stores Google Chrome login credentials.
Poseidon Stealer
Someone using the alias “Rodrigo4” has advertised Poseidon Stealer in hacker forums, as shown in Figure 2. Rodrigo4 is allegedly a former coder for Atomic Stealer, and Poseidon Stealer is considered a fork or direct competitor of Atomic Stealer.
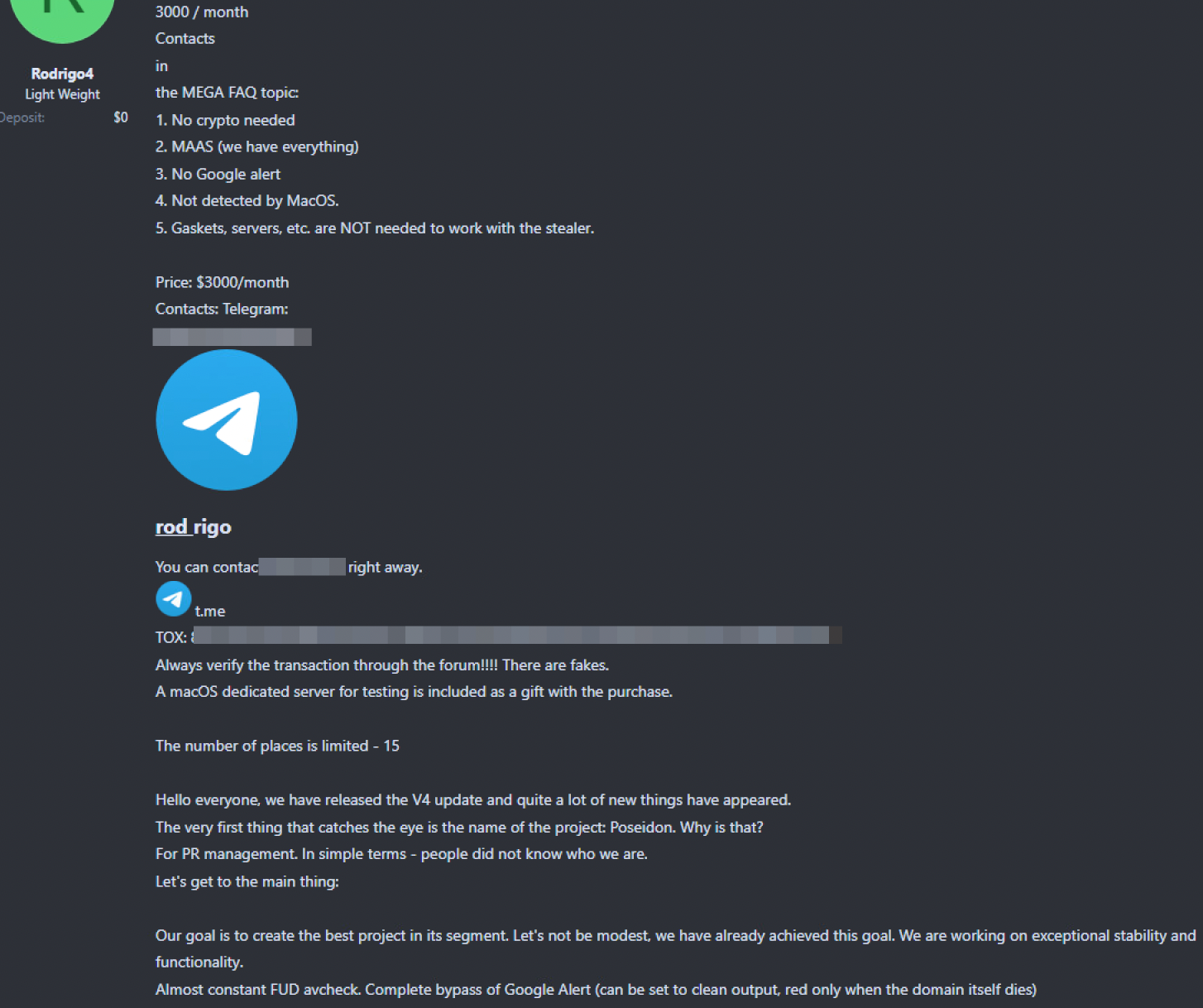
By August 2024, Rodrigo4 sold the Poseidon Stealer MaaS to an unknown source. However, the malware has apparently remained active since then.
Poseidon Stealer infects machines via the download of Trojanized installers pretending to be legitimate applications. Its operators usually distribute it via Google ads and malicious spam emails.
The malicious installer contains an encoded AppleScript file. During the installation process, the malicious installer decodes and executes the AppleScript.
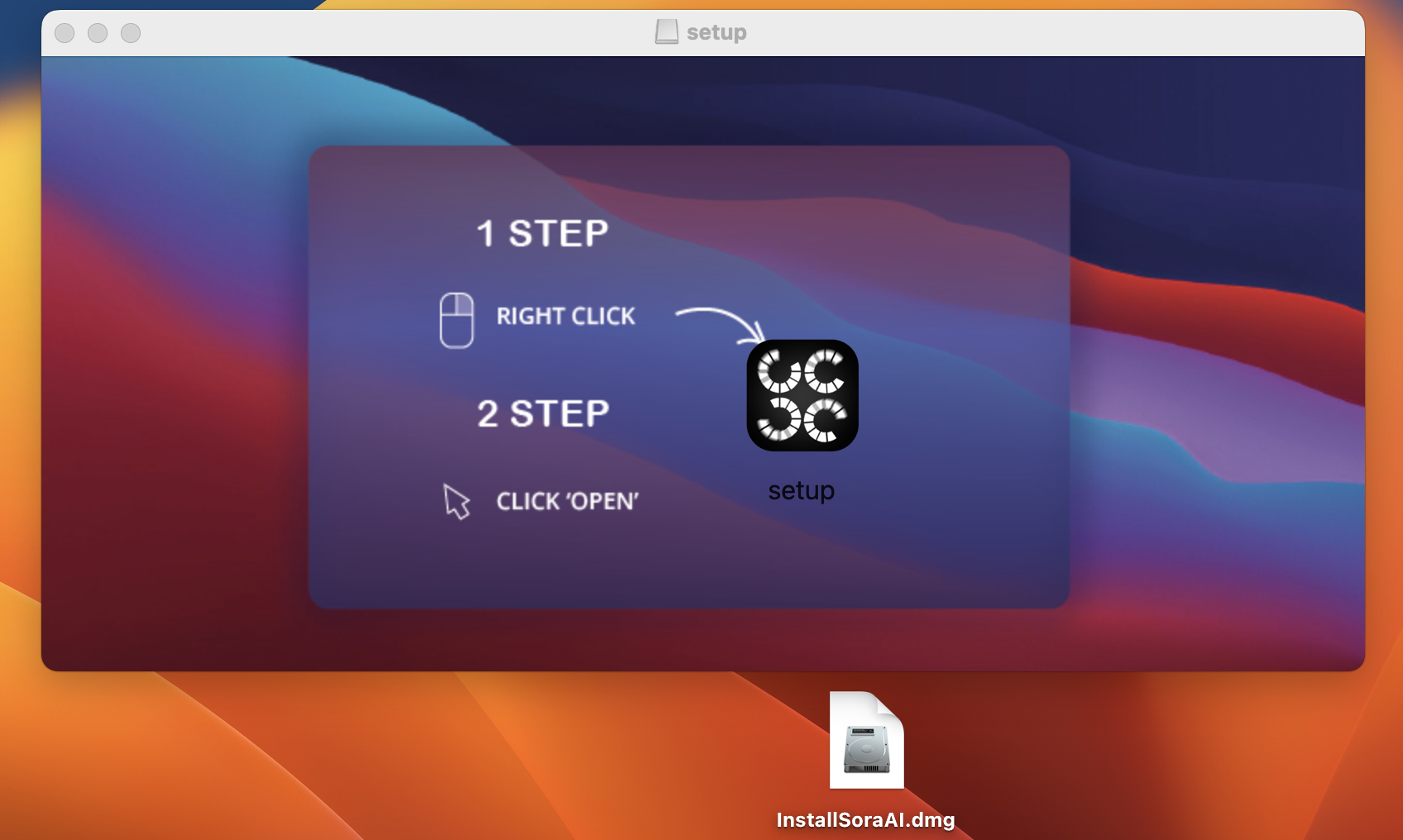
Figure 3 shows an example of a Trojanized application installer in a macOS environment that will install Poseidon Stealer.
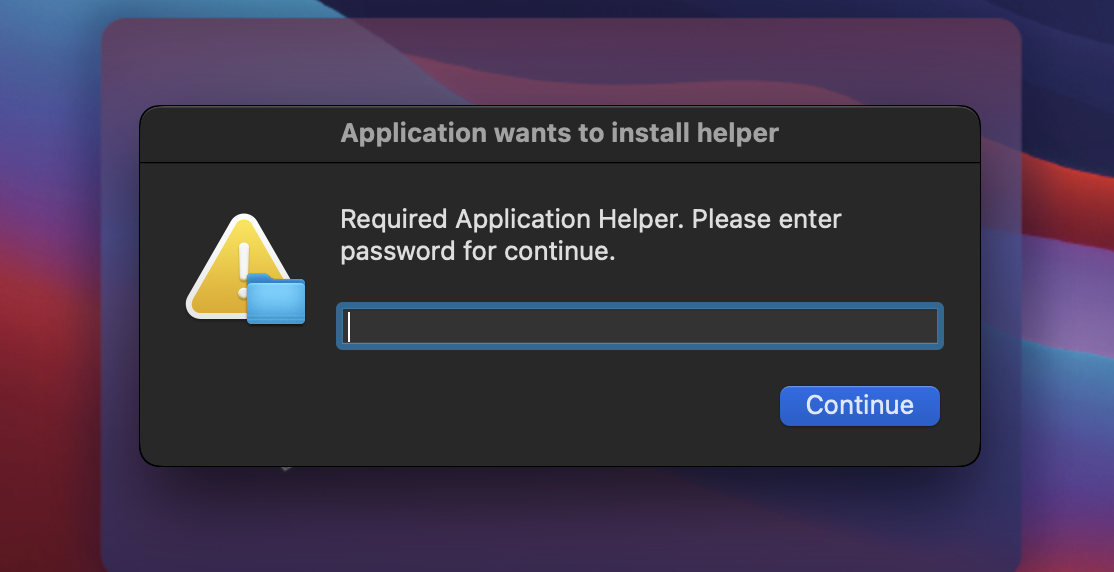
After the victim tries to install the application, Poseidon Stealer prompts them with a dialog box to get their password, as shown in Figure 4.
Poseidon Stealer sends its stolen information to a web server controlled by the attackers. Figure 5 shows the login page of the Poseidon Stealer control panel from one of these web servers.

Poseidon Stealer executes the main logic of the malware through malicious AppleScript. Figure 6 shows the execution of Poseidon Stealer as detected by Cortex XDR.

Poseidon Stealer uses the AppleScript to perform the following activities:
- Gathering system information
- Stealing browser passwords and cookies
- Stealing cryptocurrency wallets
- Gathering user credentials and notes from the macOS Notes application
- Collecting Telegram data
- Harvesting passwords from BitWarden and KeePassXC password managers
Cthulhu Stealer
Cthulhu Stealer is another popular infostealer sold as MaaS via Telegram, by operators who call themselves “Cthulhu Team.” Cthulhu Stealer is written in Go and its operators propagate it via malicious application installers. An example of one of these installers is shown in Figure 7.
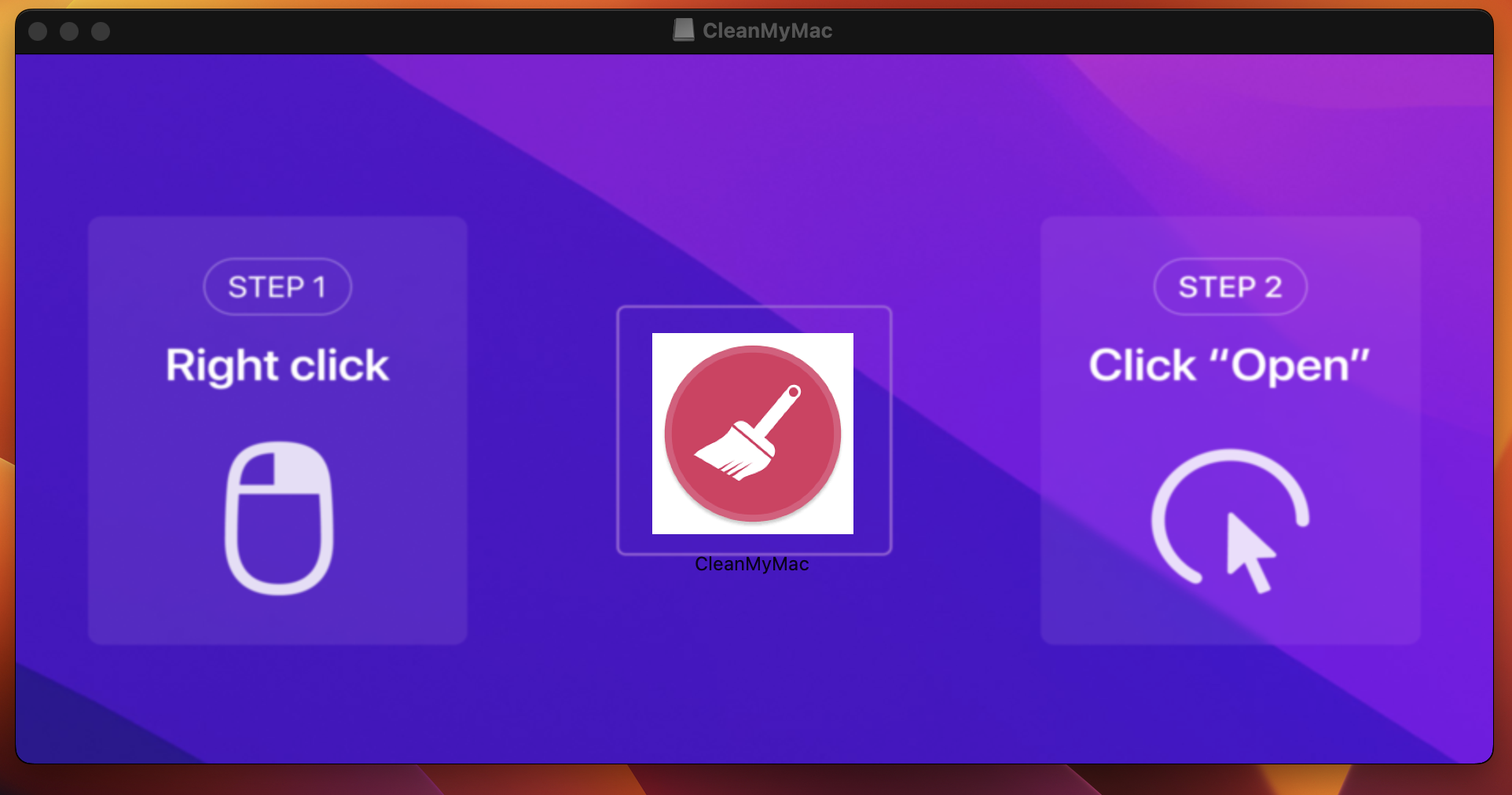
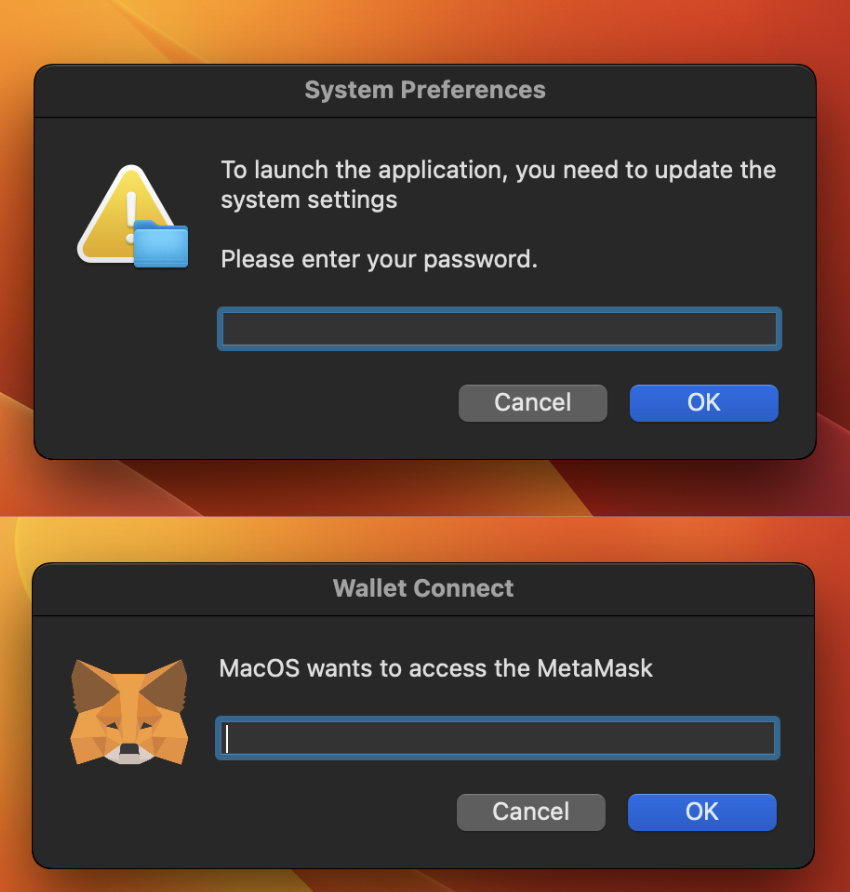
When executed, the malicious installer presents a fake dialog box claiming an update is needed for the system setting and asks for a password. Next, a second dialog box pops up, this time requesting a MetaMask password as shown in Figure 8.
Cthulhu Stealer targets a broad range of information from a compromised macOS endpoint. This information includes:
- Sensitive data (e.g., passwords, credit cards information, history, cookies) from major browsers:
- Google Chrome
- Microsoft Edge
- Firefox
- A variety of different cryptocurrency wallets
- FileZilla configuration files (which may include usernames and passwords)
- Telegram data
- Note files from the macOS Notes application
- Keychain and SafeStorage Passwords
- Files with the following extensions:
- .png
- .jpg
- .jpeg
- .icns
- .doc
- .xls
- .xlsx
- .rtf
- Data related to the gaming platform Battle[.]net and the game Minecraft (shown in Figure 9)
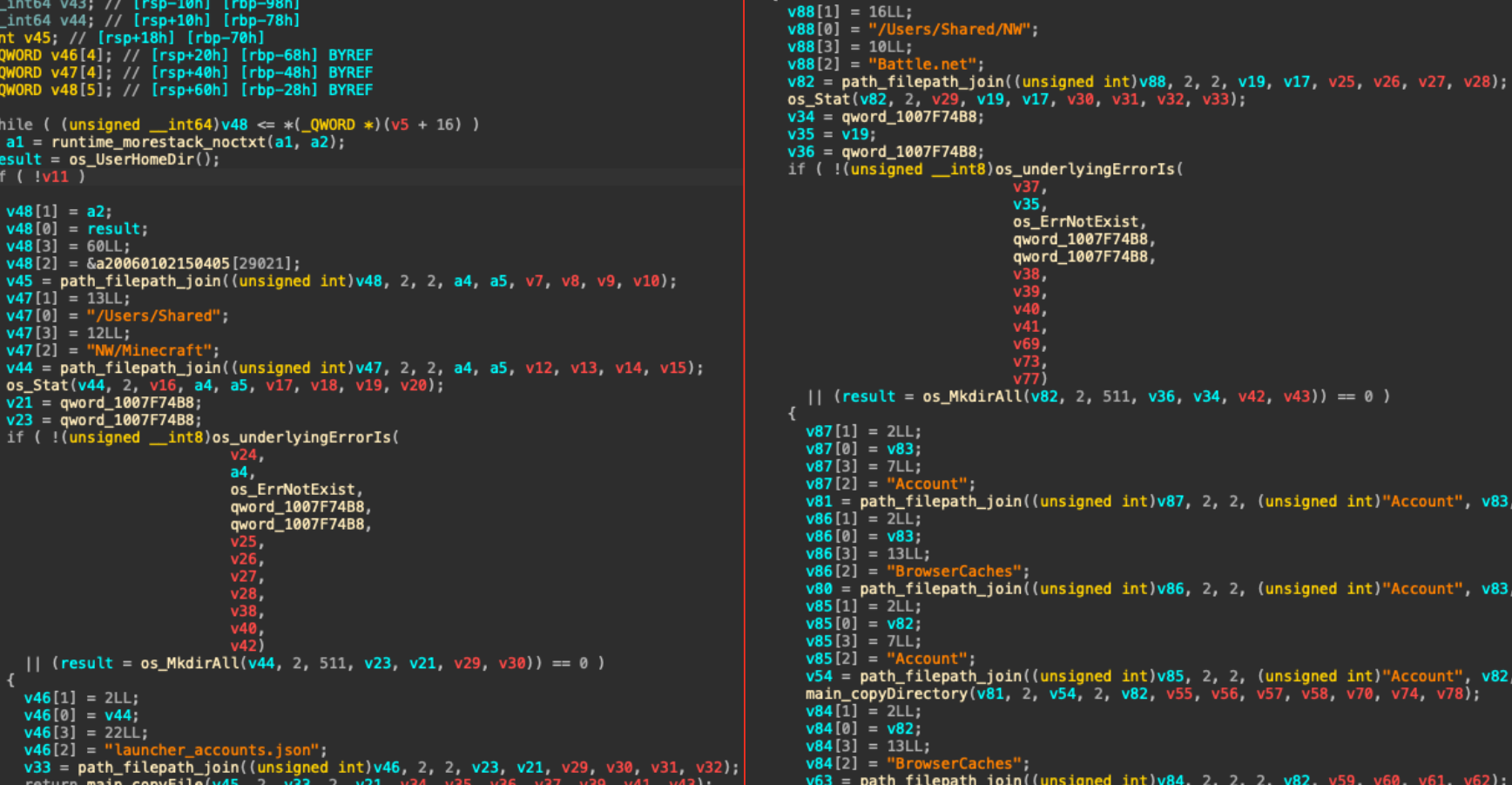
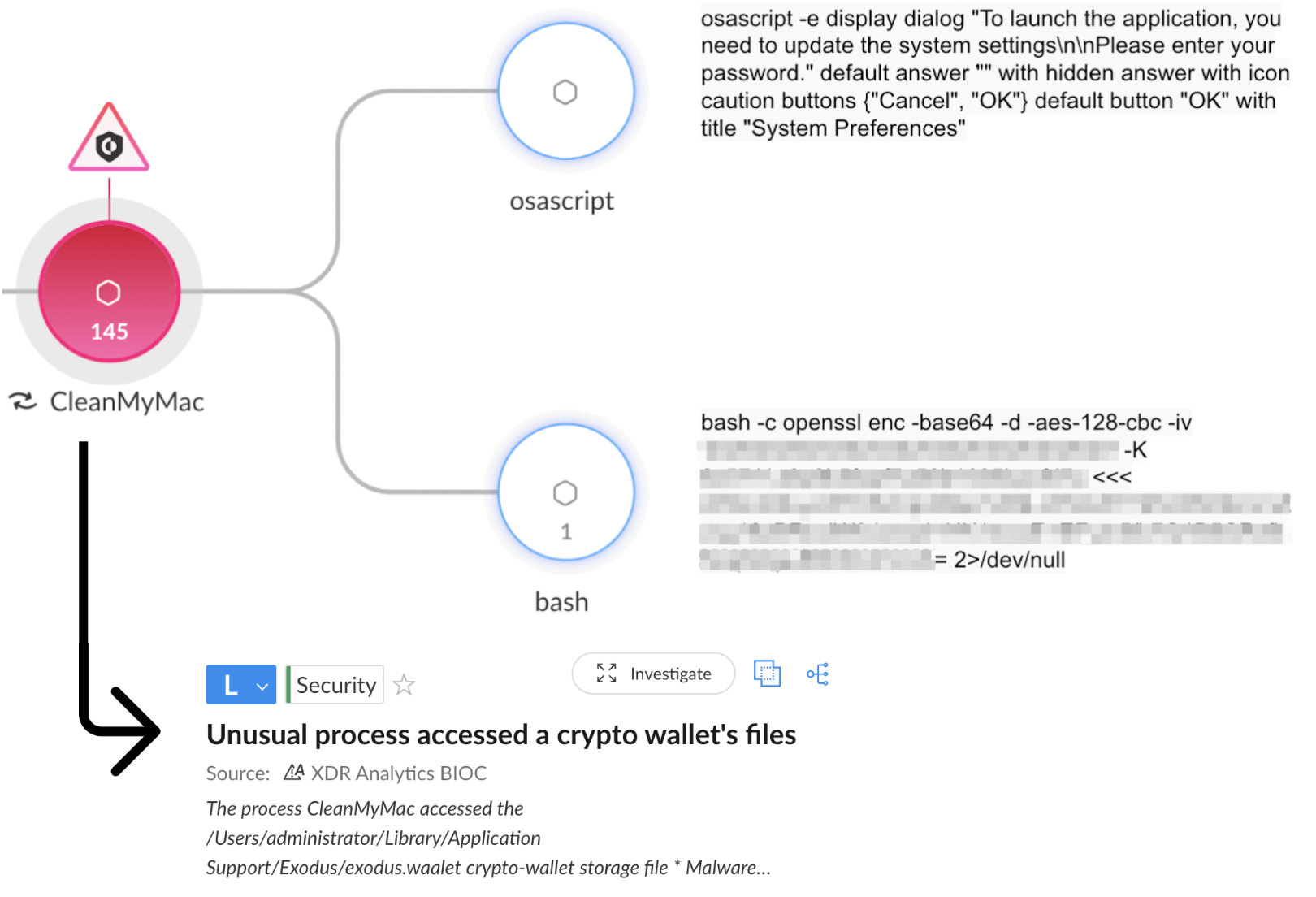
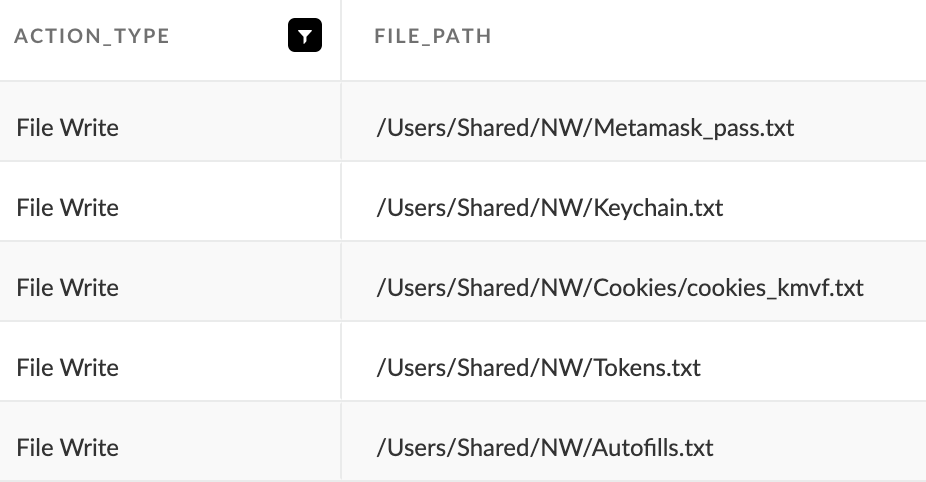
Cthulhu Stealer saves the stolen data in a directory at /Users/Shared/NW and uploads it to a command-and-control server. Figure 11 shows the different file names this threat stores data in.
Conclusion
This article reviews three prominent macOS infostealer threats, Atomic Stealer, Posedion Stealer and Cthulhu Stealer. These threats are significant not only for what they can steal directly but also because they can represent an entry point for additional malicious activity. For example, a breach that deploys an infostealer may lead to ransomware deployment later.
Implementing advanced macOS detection modules is a step forward in identifying and countering these threats.
Given the pace at which attackers are evolving their methods, a proactive and multi-layered defense strategy is essential for any organization aiming to protect its assets.
Protections and Mitigations
The new Cortex XDR macOS Analytics suites include the following detection suites:
- Credentials grabbing analytics: detecting techniques infostealers use to acquire sensitive credentials
- Sensitive information stealing analytics: detecting techniques infostealers use to steal sensitive information
- AppleScript analytics: detecting malicious ways threat actors use AppleScript
These suites monitor sensitive file access and unusual AppleScript executions, and they have helped us identify malicious activities associated with threat actors trying to steal sensitive information from organizational macOS endpoints.
Additionally:
- Cortex XDR and XSIAM are designed to:
- Prevent the execution of known malicious malware and also prevent the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protect against credential gathering tools and techniques using Cortex Credential Gathering Protection.
- Detect infostealer threats by analyzing anomalous file access, AppleScript execution and user activity from multiple data sources.
- Advanced WildFire cloud-delivered malware analysis service accurately identifies the Poseidon Stealer, Atomic Stealer and Cthulhu Stealer samples mentioned in this article as malicious.
- Advanced URL Filtering and Advanced DNS Security identify domains associated with this malware as malicious.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 Hashes for Examples of Atomic Stealer
- 599e6358503a0569d998f09ccfbdeaa629d8910f410e26df0ffbd68112e77b05
- a33705df80d2a7c2deeb192c3de9e7f06c7bfd14b84f782cf86099c52a8b0178
- cfa8173e681bf6866e06b1a971dab03954b28d3626d96ac0827c5f261e7997cd
- 831f80f6e6f7be8352aba0b54b3e55ade63f8719c7e6f8cfa19ee34af5a07deb
- a9fe32498f6132b9c39ae16524bdb3d71b451017a2d3acf117416a0dc9a89ce5
- 3eac9c66a712f74d9e93e24751220a74b2c7e5320c74f1f7b4931d8181c7f26c
IP Addresses for Atomic Stealer C2 Servers
- 94.142.138[.]177
- 194.169.175[.]117
SHA256 Hashes for Examples of Poseidon Stealer
- 9f4f286e5e40b252512540cc186727abfb0ad15a76f91855b1e72efb006b854c
- 5880430d86d092ac56bfa4aec7e245e3d9084e996165d64549ccb66b626d8c56
- 0bb4ba056d64fff21d13b53b5c1bd5ccb89bed27e66e2b7ff60ddcf47c1342b4
- 1b9b929e63be771393b6a4e526930eedb78f279174711bd2f19dfa8545f6e714
- c4e7320945caf9dc4dca11f6ad0170bc6fc2148de0cdc8aa15a236b248165d39
- a8aa1d7f940f0a8ccd516e52232b103d343826e13df9e4d9567f75e996683886
- 09852c1f67939efad0f0baeead5d23dc9cd53eec0f1f6069f041dfd4e0e83c3f
- b94067535123dd236a075d54afa34fef80324f7d1375f55c29ca70393e6492b2
- 9390108ca021b5f5c8c25849c1d6903c8a30568e822ce22e01e96381ea2df3b5
IP Addresses for Poseidon Stealer C2 Servers
- 194.59.183[.]241
- 70.34.213[.]27
SHA256 Hashes for Examples of Cthulhu Stealer
- 2d232bd6a6b6140a06b3cf59343e3e2113235adcf3fb93e78fa3746d9679cfc3
- d8d29c2906145771e1c12d6520a826c238d5672f256779326ba38859dfb9cf4c
- 6483094f7784c424891644a85d5535688c8969666e16a194d397dc66779b0b12
- a772451ddd6897c00ce766949fc82e30cfb64a6b31b44bfd9068a76ab99dd188
- ad32e638216b859855f78a856f8f4e3aea66add550619a4bde08754e2c218186
- dd831c4aaaceb9f063642ae729956a716e29e0c5452526996e92959cca820914
- 57ece6ae15a8d16a24bad097b4455dc6aec4a24c139d62d05c59330620c3e90e
- 93f33e76c57240dda2b80b0270ad867a4c77ee7ad4ac135d086398e789e4dbc9
IP Address for Cthulhu Stealer C2 Server
- 89.208.103[.]185
Additional Resources
- New Cortex Detectors for macOS Address Stealers and Malicious AppleScript – Cortex Blog, Palo Alto Networks
Updated Feb. 4, 2025, at 8:55 a.m. PT to add Additional Resources section












 Get updates from Unit 42
Get updates from Unit 42