Executive Summary
Tens of thousands of vulnerabilities are reported every year, but not all are used by threat actors in real-world attacks. There are many reasons for this: a proof of concept (PoC) may not be available for attackers to weaponize, it may be too difficult to exploit the vulnerability, there may be a lack of accessible vulnerable software on the internet, or attackers may simply deem a vulnerability not worth exploiting due to low impact. Real-world defenders need real-world data on which vulnerabilities attackers are choosing to exploit – and where to focus protections.
In the 2022 Unit 42 Network Threat Trends Research Report, we’ve used data captured by the Palo Alto Networks Advanced Threat Prevention security service on Next-Generation Firewall and Prisma SASE from regions including the United States, Singapore, Japan, Australia, Canada and Europe to observe and analyze exploits in the wild. Our data includes attacks on organizations including universities, hospitals, e-commerce vendors, financial institutions and tech companies. It includes 262 million attack traffic sessions from 2021, excluding internal traffic.
We’ve used this information to identify which vulnerabilities attackers exploited most commonly in 2021, and to predict which vulnerabilities they are likely to focus on in 2022 and 2023. We recommend that organizations patch the vulnerabilities listed below.
Palo Alto Networks customers receive protections against the vulnerabilities discussed here through our Cloud-Delivered Security Services, namely Advanced Threat Prevention. We also offer coverage across the attack lifecycle with complementary protection from WildFire, Advanced URL Filtering and DNS Security. These services can be deployed across the entire enterprise via Next-Generation Firewall physical and virtual appliances, and Prisma Access.
| CVEs discussed | CVE-2017-5638, CVE-2017-9841, CVE-2018-19986, CVE-2019-02320, CVE-2019-19597, CVE-2019-2725, CVE-2019-2729, CVE-2019-9082, CVE-2020-5902, CVE-2020-14882, CVE-2020-14883, CVE-2020-15505, CVE-2020-15506, CVE-2020-25078, CVE-2021-21315, CVE-2021-22986, CVE-2021-26855, CVE-2021-31805, CVE-2021-34473, CVE-2021-35464, CVE-2021-38647, CVE-2021-40438, CVE-2021-40539, CVE-2021-41773, CVE-2021-42013, CVE-2021-44228, CVE-2021-45046, CVE-2022-22963, CVE-2022-22965 |
Most Exploited Vulnerabilities of 2021
Unsurprisingly given their severity and ease of exploitation, the Apache Log4j vulnerabilities were the most exploited CVEs of 2021, with over 11 million attack sessions observed in less than one month. Though the vulnerabilities were made public in December 2021, attack sessions against them account for 4.2% of the total attack sessions observed, underscoring the profound impact these vulnerabilities had on security.
However, attackers also make heavy use of older vulnerabilities. Some of the top vulnerabilities we identified were disclosed as far back as 2017. This demonstrates the importance of understanding your organization’s attack surface and ensuring that older software is properly managed.
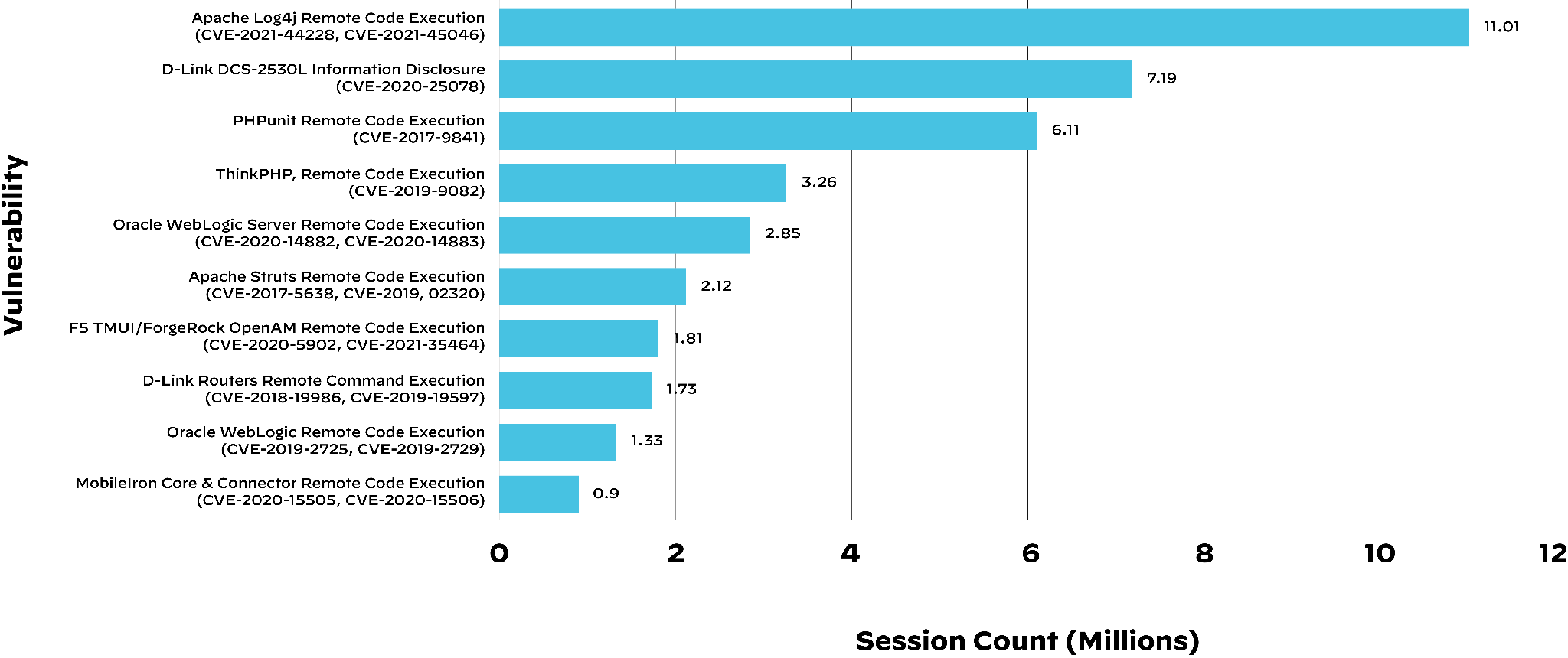
For the seventh most exploited vulnerability listed above – “F5 TMUI/ForgeRock Open AM” – we combined CVE-2020-5902 and CVE-2021-35464 as they were both logged due to the Apache path normalization issue and therefore related. Others that show two or more CVEs are similar in nature and target the same vendor. It’s important to note that intrusion prevention system (IPS) vendors, including Palo Alto Networks, can use a single threat prevention signature to detect multiple, similar CVE attacks.
CVEs to Watch in 2022 and 2023
We conducted secondary analysis of the malicious sessions observed in attack traffic to search for insights to inform defenders of the vulnerabilities that are likely to be popular with attackers in 2022 and early 2023.
To select the CVEs for this list, we evaluated vulnerabilities based on the following criteria:
- Severity: All vulnerabilities listed below are considered high or critical severity.
- Vendor: Attackers are more likely to focus on vulnerabilities that affect widely used products.
- Impact: Vulnerabilities that allow, for example, remote code execution could allow attackers to do significant damage to a targeted organization.
- Attack complexity: CVEs that don’t require a complex attack path, or for which proofs of concept are readily available are easier for attackers to exploit.
- Exploits in the wild: If attackers are already exploiting a vulnerability, they are likely to continue.
The table below lists the top 10 vulnerabilities to watch. The version in the full report also includes links to existing research and potential patches.
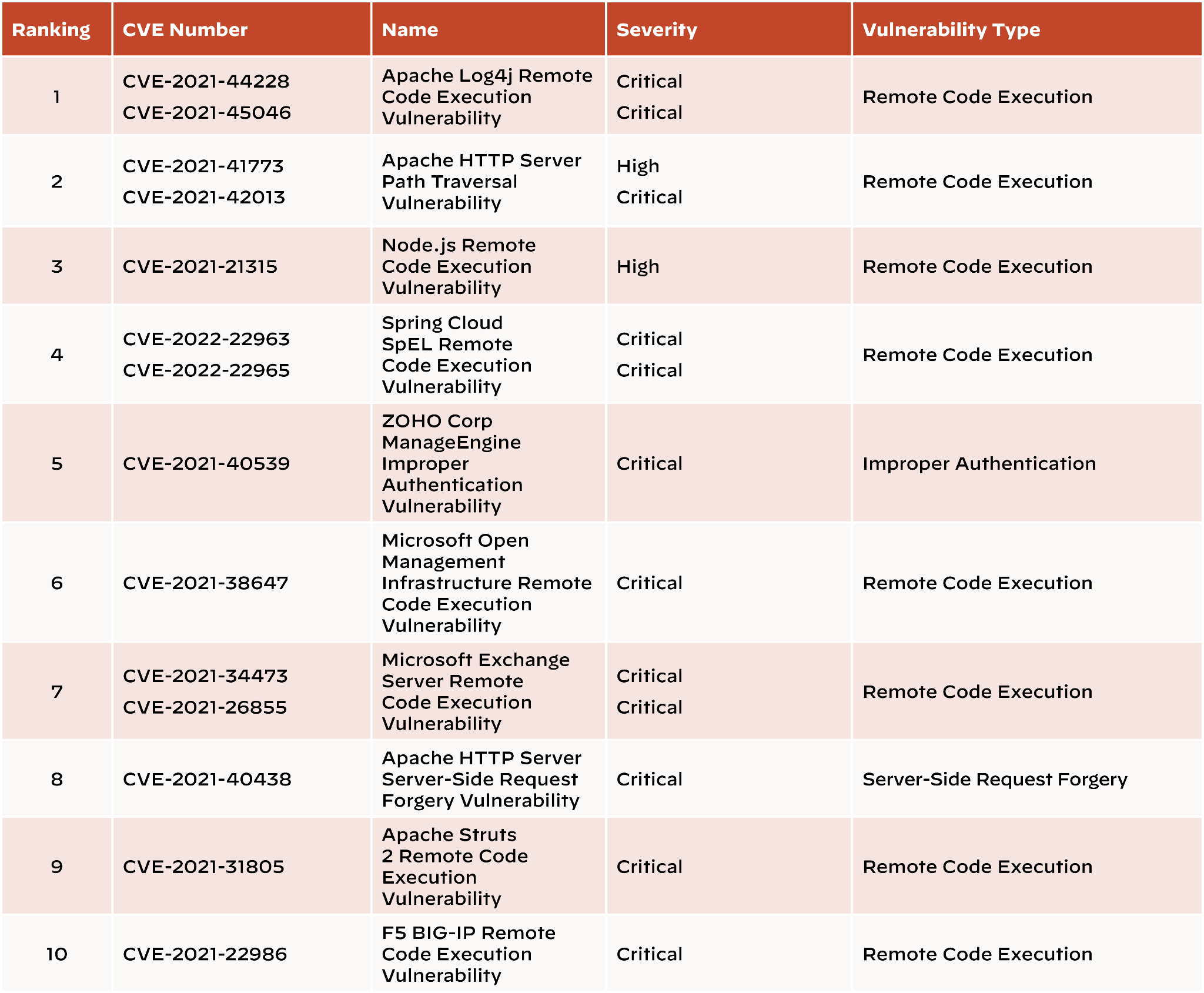
We recommend that defenders take steps to protect against the CVEs listed above, including applying patches after due diligence.
Conclusion: Why We Hope Our List of Top CVEs Is Wrong
We carefully evaluated the CVEs we highlighted above to help organizations prioritize protections – but our hope is that when we evaluate top vulnerabilities of this year in 2023, they won’t look anything like our list above.
Ideally, by drawing attention to these vulnerabilities and providing visibility into how to stop them, we’ve encouraged network security teams to increase defenses against them – forcing attackers to look elsewhere. We’ll consider it even more of a success if threat actors wind up focusing on less impactful vulnerabilities than the ones listed here. Is that win/win or a win/loss?
The information in this blog was drawn from the 2022 Unit 42 Network Threat Trends Research Report. Download the full report to gain more insights into trends in network vulnerabilities and links to research, as well as data gathered from our telemetry on malware families and file types. The report also contains case studies on Log4Shell and SiloScape, a discussion of the use of customized and encoded command and control (C2) by Cobalt Strike, and an in-depth analysis of the Apache HTTP Server Path Traversal Vulnerability listed above as a potential top vulnerability in the year to come.
Our security experts round out the report with recommendations on how to fully assess your network security posture, how to deploy preventions for unknown command and control, and how to implement Zero Trust.
Palo Alto Networks customers receive protections against the vulnerabilities discussed here through our Cloud-Delivered Security Services, namely Advanced Threat Prevention. We also offer coverage across the attack lifecycle with complementary protection from WildFire, Advanced URL Filtering and DNS Security. These services can be deployed across the entire enterprise via Next-Generation Firewall physical and virtual appliances, and Prisma Access.
Read the full 2022 Unit 42 Network Threat Trends Research Report.
Additional Resources
Announcing the First Unit 42 Network Threat Trends Research Report
Network Security Trends series
Advanced Threat Prevention
Cloud-Delivered Security Services
Other Recent Unit 42 Reports
Unit 42 Cloud Threat Report, Volume 6
2022 Unit 42 Ransomware Threat Report












 Get updates from Unit 42
Get updates from Unit 42